Patch Tuesday patches are rolling out right now and there’s a bunch of them. Quick glance on the Microsoft Update Catalog shows 104 individual patches
[See the full post at: Patch Tuesday: The good, the bad, the ugly and the hopeless]

|
There are isolated problems with current patches, but they are well-known and documented on this site. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
-
Patch Tuesday: The good, the bad, the ugly and the hopeless
Home » Forums » Newsletter and Homepage topics » Patch Tuesday: The good, the bad, the ugly and the hopeless
- This topic has 119 replies, 29 voices, and was last updated 6 years, 7 months ago.
Tags: MSE Pattern
AuthorTopicViewing 39 reply threadsAuthorReplies-
abbodi86
AskWoody_MVP -
geekdom
AskWoody_MVPOctober 9, 2018 at 1:52 pm #223107Beta Test
Here and appeared in Windows Updates just now:
https://support.microsoft.com/en-us/help/3177467/servicing-stack-update-for-windows-7-sp1-and-windows-server-2008-r2-spThis update appeared after today’s other updates were installed and I checked for updates again.
On permanent hiatus {with backup and coffee}
offline▸ Win10Pro 2004.19041.572 x64 i3-3220 RAM8GB HDD Firefox83.0b3 WindowsDefender
offline▸ Acer TravelMate P215-52 RAM8GB Win11Pro 22H2.22621.1265 x64 i5-10210U SSD Firefox106.0 MicrosoftDefender
online▸ Win11Pro 22H2.22621.1992 x64 i5-9400 RAM16GB HDD Firefox116.0b3 MicrosoftDefender -
anonymous
GuestOctober 9, 2018 at 3:09 pm #223129This may be the first time you’ve cleared the deck to expose this service stack update. It was discussed by Mr.Brian (I believe) last year. And more recently was a subject of some contention over how to properly bring a system up to date.
Could there have been a system change that removed an earlier install, that is now being recognized and put on offer to your system again?
-
geekdom
AskWoody_MVPOctober 9, 2018 at 3:40 pm #223158An earlier version of KB3177467 was installed on my computeer September 20, 2016.
What has occurred in the current check for updates is all other applicable updates appeared first and KB3177467-v2 showed only after current updates had been installed.
abbodie86’s question was: does this update show alone and first. No, it doesn’t; it shows alone and last after all the other current updates have been installed.
On permanent hiatus {with backup and coffee}
offline▸ Win10Pro 2004.19041.572 x64 i3-3220 RAM8GB HDD Firefox83.0b3 WindowsDefender
offline▸ Acer TravelMate P215-52 RAM8GB Win11Pro 22H2.22621.1265 x64 i5-10210U SSD Firefox106.0 MicrosoftDefender
online▸ Win11Pro 22H2.22621.1992 x64 i5-9400 RAM16GB HDD Firefox116.0b3 MicrosoftDefender -
anonymous
GuestOctober 9, 2018 at 4:19 pm #223186
-
-
-
-
PKCano
ManagerOctober 9, 2018 at 4:29 pm #223191The original version of KB3177467 was installed on my Win7 Ult x64 in 2016
Today (10/9), I had 5 updates in the queue (Rollup, .NET Rollup, MSRT and 2 Office Viewer patches). I hid all 5, did a search for updates, and the SSU KB3177467 -v2 showed up. It is still exclusive and does not show up until the Windows Update queue is empty.
-
-
geekdom
AskWoody_MVPOctober 9, 2018 at 12:52 pm #223075Beta Test
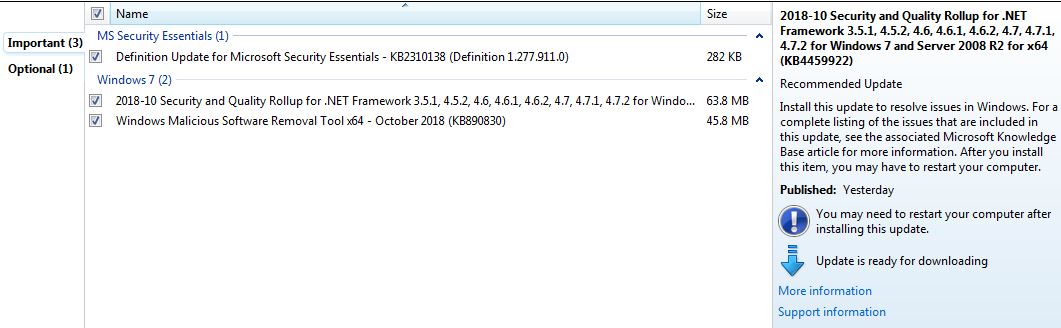
Reporting on Windows 7 x64 updates:- Windows Malicious Software Removal Tool x64 (KB890830)
- Security and Quality Rollup for .NET Framework 3.5.1, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2 for Windows 7 and Server 2008 R2 for x64 (KB4459922)
- October Security Monthly Quality Rollup Windows7 x64 (KB4462923)
All installed without error and the system rebooted without error.
Please note that I have GWX Control Panel to prohibit Windows 10 upgrade.On permanent hiatus {with backup and coffee}
offline▸ Win10Pro 2004.19041.572 x64 i3-3220 RAM8GB HDD Firefox83.0b3 WindowsDefender
offline▸ Acer TravelMate P215-52 RAM8GB Win11Pro 22H2.22621.1265 x64 i5-10210U SSD Firefox106.0 MicrosoftDefender
online▸ Win11Pro 22H2.22621.1992 x64 i5-9400 RAM16GB HDD Firefox116.0b3 MicrosoftDefender -
geekdom
AskWoody_MVPOctober 9, 2018 at 3:52 pm #223169Beta Test
Checked for updates again.- KB3177467 showed as a stand-alone update.
- KB3177467 installed without error.
No system reboot was required nor indicated as necessary.
On permanent hiatus {with backup and coffee}
offline▸ Win10Pro 2004.19041.572 x64 i3-3220 RAM8GB HDD Firefox83.0b3 WindowsDefender
offline▸ Acer TravelMate P215-52 RAM8GB Win11Pro 22H2.22621.1265 x64 i5-10210U SSD Firefox106.0 MicrosoftDefender
online▸ Win11Pro 22H2.22621.1992 x64 i5-9400 RAM16GB HDD Firefox116.0b3 MicrosoftDefender1 user thanked author for this post.
-
-
PKCano
ManagerOctober 9, 2018 at 12:53 pm #223077Group B Security-only patches have been updated on AKB2000003 as of Oct. 9, 2018.
The links provided are direct download to the MS Update Catalog, thus are always up to date.
-
PKCano
ManagerOctober 10, 2018 at 12:25 am #223368How to get the Servicing Stack KB3177467 -v2 if you are in Group B
The SSU KB3177467 will not appear in Windows Update as long as there are any other pending updates in the “important” update queue.
In Windows Update:
+ Hide the Security Quality Monthly Rollup.
+ Hide whatever other updates you do not want to install (including unchecked).
+Install the remaining checked updates – this should clear the WU queue.
+Reboot if required, wait 15 minutes, search for updates
+Install the Servicing Stack KB3177467
+Reboot if required, wait 10 minutes
+ Install the Security-only Update and the IE11 Cumulative Update
+ Reboot, wait 15 minutesEDIT: Alternate method………….
In Windows Update:
+ Hide all pending updates in the important update queue (checked and unchecked)
+ Search for updates
+ Install the Servicing Stack KB3177467
+ Reboot if required, wait 10 minutes
+ Install the Security-only Update and the IE11 Cumulative Update
+ Reboot, wait 15 minutes
+ Unhide any updates you want to install (.NET, MSRT, Office, etc)
+ Install the remaining updates
+ Reboot if required, wait 15 minutesGroup B is a little more difficult this month!
8 users thanked author for this post.
-
DrBonzo
AskWoody PlusOctober 10, 2018 at 12:44 am #223370Thanks for those very clear instructions. I’m curious, though, if it’s OK to just get the SSU update from the catalog as a stand alone package and install it, reboot if required, and then install the Security Only and IE 11 updates.
While I’m sure your way will work, it seems that MS is using some very convoluted logic (you need the SSU before installing the Rollup, Security Only, or IE 11 updates, but you’re not offered the SSU until after you’ve either installed those updates – that’s the convoluted part – or gone to the trouble of hiding them – which is not quite so convoluted but is certainly devious/obtuse/obfuscated/etc.) Or perhaps I’m missing something?
-
PKCano
ManagerOctober 10, 2018 at 6:16 am #223411It is certainly OK to download the SSU from the Catalogue and install it manually. But it can be had from Windows Update with a little effort while the Security-only patches cannot.
MS should present the SSU first in Windows Update and not allow the Rollup to show up unless it is install first. That would be logical.
But this is MS we are talking about.
-
-
RTEsysadmin
AskWoody LoungerOctober 10, 2018 at 6:20 pm #223638Thanks for those instructions. Still, it seems easier to install the update manually. Also, if you have a lot of machines on an AD domain that need it, you can probably plan on losing at least a night’s sleep. For our servers, I’m planning to deploy it through Group Policy, as we do with all updates (we don’t Windows Update or WSUS) with a start-up script:
wusa.exe \\server\Share\Windows6.1-KBxxxxxx-….msu /quiet /norestart
shutdown /rThis avoids having to repackage the .msu file as an .msi, as you’d normally have to do to run a program at startup.
Group K(ill me now)
-
-
-
Susan Bradley
Manager -
woody
Manager -
GreatAndPowerfulTech
AskWoody Lounger
-
-
-
OscarCP
MemberOctober 9, 2018 at 1:08 pm #223087As I have every month and for several years now, and being Group B, I am going to wait for at least three weeks before even considering patching my Windows 7 PC this time — unless something like the Meltdown/Specter scare happens — and while keeping an eye most particularly on the comments here and elsewhere about problems people may encounter and, of course, also on the Master Patch List.
Group B, Windows 7 Pro, Sp1, x64.
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV -
anonymous
Guest -
Geo
AskWoody Plus -
Zaphyrus
AskWoody Lounger -
Karlston
AskWoody LoungerOctober 9, 2018 at 2:23 pm #223118It’s interesting that “the most secure version of Windows ever” AKA Windows 10, has more vulnerabilities being patched than the “older less secure” versions.
Another Microsoft Windows 10
lieclaim bites the dust?Hanlon's Razor: Never attribute to malice that which can be adequately explained by stupidity.
-
Zaphyrus
AskWoody LoungerOctober 9, 2018 at 2:54 pm #223125I think it has to do that the people that creates virus and stuff, moves to newer OS since they are more widely used
That’s why I have a personal theory that under that logic, IT MAY be safe to use older systems like XP.
for example, if I was someone that want to mess up with people computers, I wouldn’t create a virus that target an OS that only 1 or 2 persons use. I would target the lastest OS.
YES I know, all of us should be in supported systems.
Just someone who don't want Windows to mess with its computer. -
Karlston
AskWoody Lounger -
anonymous
GuestOctober 9, 2018 at 3:52 pm #223161Karlston – The amount of vulnerability patches don’t necessarily relate to how vulnerable the system actually is. Things like the Zero Day Initiative didn’t really exist back in the day of (say) XP. Many exploits existed that were never patched because they were never reported nor found. Many of the vulnerability patches fix vulnerabilities that exist but are non-trivial to exploit. Many of the exploits from XP’s era were quite trivial.
Zaphyrus – Picking an old OS may protect you from some of the mass exploits, however if you’re ever targeted you’d be toast. Most kits still have exploits for older systems, or they’re still common enough to find. Also if the phishing email you clicked on contained a link to an automated downloader server, it may have exploits for many different systems.
-
Zaphyrus
AskWoody Lounger
-
-
-
krzemien
AskWoody Lounger -
b
AskWoody_MVP -
EstherD
AskWoody Lounger -
b
AskWoody_MVP -
AlexEiffel
AskWoody_MVPOctober 9, 2018 at 10:21 pm #223351I think she might refer to Total Meltdown.
-
b
AskWoody_MVP
-
-
-
-
-
anonymous
Guest -
anonymous
GuestOctober 9, 2018 at 3:03 pm #223124There was a last minute change on daylight saving time here on Brazil – as discussed here: https://social.technet.microsoft.com/Forums/pt-BR/2e144152-c2c1-48cf-a22b-023d094e30ef/horrio-de-vero-20182019-nova-alterao?forum=w8serverpt
As far as I can see none of those updates will fix it, right?
-
PKCano
Manager
-
-
anonymous
GuestOctober 9, 2018 at 3:16 pm #223136Win 10 1809 home user. Have a question maybe someone could help with.
I just updated my computer, and strange….In the update history, the cumulative update (KB4464330) shows twice. Once it shows it successively installed on 10/9/2018. However, below that it shows the same KB4464330 Failed to install on 10/9/2018 – 0x8024200d.
I checked my Windows version, and I am on build 17763.55 (which I believe is what build I should be on).
Computer appears to be working fine.
In two years of owning this computer, I have never seen an install error message in the update history.
The actual update process seemed to go fine.
Is this something to be concerned about?
Many many thanks….
-
Mr. Natural
AskWoody LoungerOctober 9, 2018 at 3:19 pm #223142It’s like a runaway train. Despite all the obstacles, derailing’s and catastrophe’s that have occurred there is no stopping this train. Total disregard and oblivious to the past. Moving full steam ahead regardless. Absolutely no stopping or slowing down.
Hmmmmm… kind of like some sort of A.I. making the decisions and following the prescribed schedule regardless. Calling the shots with no consideration for the lowly human “element”.
Red Ruffnsore
-
anonymous
Guest -
samak
AskWoody PlusOctober 9, 2018 at 3:45 pm #223160Interesting to see that the W7 monthly roll-up patch KB4462923 has the NIC issue but the Security-only patch KB4462915 doesn’t. Yay for Group B
Windows 10 Home 22H2, Acer Aspire TC-1660 desktop + LibreOffice, non-techie
1 user thanked author for this post.
-
Bill C.
AskWoody PlusOctober 9, 2018 at 3:52 pm #223172And just in time for Halloween, IIRC, this is the month that the Win7 telemetry updates are to be included in the Monthly Rollups (Group A), correct. I think that was discussed last month.
If so, I suspect someone will reference it and refresh my mind.
1 user thanked author for this post.
-
ViperJohn
AskWoody LoungerOctober 9, 2018 at 4:04 pm #223179Group B Security-only patches have been updated on AKB2000003 as of Oct. 9, 2018. The links provided are direct download to the MS Update Catalog, thus are always up to date.
PKCano the Group B’ers also have the KB3177467-v2 Servicing Stack Update to manually install this month.
Viper
-
PKCano
Manager
-
-
Geo
AskWoody PlusOctober 9, 2018 at 4:17 pm #223187Group A, Win 7X64, Home Premium, AMD, MS security essentials, Office 10. No problems, no slowdown after installation.
2 users thanked author for this post.
-
Geo
AskWoody Plus -
Microfix
AskWoody MVP
-
-
anonymous
GuestOctober 9, 2018 at 4:54 pm #223199I’d say it’s pretty important to make a note of it. Doubt I’m the only one who doesn’t hide everything…
— Cavalary
1 user thanked author for this post.
-
ViperJohn
AskWoody LoungerOctober 9, 2018 at 5:40 pm #223235The SSU is available through Windows Update after they hide the other update(s). No need for a Catalogue link.
The SSU should be installed before Octobers Security Only updates shouldn’t it??? That is normally how SSU’s are applied. Without at least a reference to it the risk of out of order updates goes through the roof. I always install the Security Only updates from the catalog before I even run WU to get the .NET updates and hide the other junk in WU. I bet I am not alone in doing that.
1 user thanked author for this post.
-
anonymous
Guest
-
-
Carl D
AskWoody LoungerOctober 9, 2018 at 5:42 pm #223237Wait… WHY would Microsoft need telemetry from a Win 7 system? Are they trying to discover what people need with real computer operating systems? Or just slow them down and make them less secure? -Noel
Noel, I’ve asked that question myself a few times. Never really received any sort of satisfactory answer apart from “oh, it helps MS improve Windows” or words to that effect.
What sort of ‘improvements’ is MS planning for W7 between now and January 2020, I wonder? Unless they’re slowly laying the foundations for all remaining Windows 7 computers worldwide to automatically ‘upgrade’ themselves to Windows 10 immediately following W7 EOL.
I’ll have my popcorn ready when January 2020 arrives, just in case.
1 user thanked author for this post.
-
TheOwner
AskWoody LoungerOctober 9, 2018 at 5:43 pm #223238 -
PKCano
Manager -
Carl D
AskWoody LoungerOctober 9, 2018 at 6:03 pm #223251Someone recently posted a link to a batch file which disables/removes the added telemetry to Windows 7.
Because the telemetry isn’t ‘baked’ into the OS like Windows 10 it is easier the defeat/remove apparently.
Can’t remember which thread it was in but I have the batch file saved here. The creator recommended running it after installing Windows Updates every month from now on.
-
anonymous
Guest
-
-
anonymous
Guest -
anonymous
GuestOctober 9, 2018 at 6:12 pm #223254My notes show that KB3150513 follows on from KB2952664, a well documented item to avoid. I intended to write that you should look for, and remove that item. But now understand that may be what is now bundled into the October Cumulative Update. Please someone say if this is correct or no.
This may be more help, https://www.askwoody.com/forums/topic/neutralize-telemetry-and-sustain-windows-7-and-8-1-monthly-rollup-model/
-
abbodi86
AskWoody_MVP
-
-
TheOwner
AskWoody Lounger -
PKCano
ManagerOctober 9, 2018 at 7:09 pm #223292We are still at DEFCON-1. The patches just came out today and DEFCON-1 means WAIT to 1nstall. I think you should wait until Woody has had time to sort all this out and make recommendations for patching safely. A DEFCON number of 3 or above will signify that.
-
-
b
AskWoody_MVPOctober 9, 2018 at 7:54 pm #223301There’s a bumper crop of Office security patches, for Office 2010, 2013, 2016, several viewers, SharePoint Server 2010, 2013 and 2016.
150 million users of Office 365 ProPlus (Click to Run) also had updates made available:
-
anonymous
Guest -
b
AskWoody_MVP
-
-
-
Geo
AskWoody Plus -
GoneToPlaid
AskWoody LoungerOctober 9, 2018 at 11:38 pm #223363Win7 SSU KB3177467-v2 still exclusive i’m interesting to know if it will get offered alone first on WU, since it’s now Security Update i don’t have deployed Win7 currently to check
I am pretty sure that KB3177467 is simply a re-release of this update which was originally released on or about 2016-09-19.
What? There is a KB3177467-v2? And this is not simply a re-release of the original KB?
I am Group B, and I have had KB3177467 installed on all of my Windows 7 computers since around 2016-10-02 with no issues aside from the Stage 3 of 3 hang. I encountered the Stage 3 of 3 hang when I inadvertently installed this update at the same time as other updates on one of my Windows 7 computers.
Think about it. This is a Servicing Stack Update (SSU) for Windows Update. You really should install any SSU by itself (as in not installing any other updates at the same time) and reboot your computer before proceeding to install any other updates.
For all Windows 7 users, installing this update is important since it fixes some critical timing issues which could occur when installing other updates. KB3177467 does not contain telemetry, does not alter Windows Update settings, and has nothing to do with either Windows 10 or GWX.
The upshot is that KB3177467 is now flagged as a Security Update in order to hopefully get all Windows 7 users to install it, which they should if it is not already installed even though this update has nothing to do with security.
-
DrBonzo
AskWoody PlusOctober 10, 2018 at 12:51 am #223371This version 2 thing seems pretty fishy to me. I installed the original SSU in October 2016 with no problems at all (no hanging on ‘2 of 3’ or ‘3 of 3’, nor any other problems). My September 2018 group B Win 7 Security only and IE 11 patches installed with no problems at all. So now all of the sudden, MS has come up with a new version of the SSU!!!??? I’m thinking the likelihood of there being hidden nasty tricks in this new SSU is very high.
-
abbodi86
AskWoody_MVPOctober 10, 2018 at 2:32 am #223389Yes, KB3177467-v2 do not contain any new files, just new package with higher version and “Security Update” classification
but how WU users can handle “possible” Monthly Rollup issue if KB3177467-v2 only show up after installing the rollup (and clear other updates)?
IMHO, they should treat the rollup just like Windows 8.1 KB2919355, it won’t show up in WU until the proper SSU is installedi’m pretty sure the “exclusive” attribute is the cause of “Stage 3 of 3 hang”
previous SSU KB3020369 does not have it, and i didn’t hear any issue with installing it -
GoneToPlaid
AskWoody LoungerOctober 10, 2018 at 11:06 am #223497Correct. I just installed the v2 and noted that KB3177467 is now listed as “Security Update for Microsoft Windows (KB3177467)” under Installed Updates, whereas v1 was listed as “Update for Microsoft Windows (KB3177467)” under Installed Updates.
abboi86 is also correct that v2 contains no new files nor anything fishy. I also agree with him about the exclusive nature of SSUs as the cause of any Stage 3 of 3 hangs.
-
-
Ed
AskWoody LoungerOctober 10, 2018 at 5:51 am #223408“Think about it. This is a Servicing Stack Update (SSU) for Windows Update. You really should install any SSU by itself (as in not installing any other updates at the same time) and reboot your computer before proceeding to install any other updates.”
OK, I thought about it, and once again I’m posing the same question. You’re telling people they should restart their computers after installing this update and it should be installed by itself… I’d like an explanation as to WHY we need to do this? Unless you’re seeing a “Restart Now” prompt after installing KB3177467 why should we do a restart? Are YOU seeing a “Restart Now” prompt after installing only KB3177467?
For the third time now I’m asking you to explain why anybody would need to restart their computer after installing an update that does NOT require a restart! If my most recent unanswered request for clarification on this is a bit foggy see here……
-
GoneToPlaid
AskWoody Lounger -
anonymous
GuestOctober 26, 2018 at 11:48 am #227412“I stand corrected. If you installed KB3177467
exclusively, you do not have to restart your computer.”I fixed your comment for you GoneToPlaid, in the link Ed provided he clearly stated he installed the SSU (KB3177467) and then two Security Only updates directly afterwards without a restart between any of them.
I’d have to think Ed’s 100% success rate on 16 individual computers would be pretty stealth proof that a restart is not needed regardless if the SSU is installed “exclusively” or not.
-
anonymous
GuestOctober 26, 2018 at 12:31 pm #227431
-
-
-
-
-
Microfix
AskWoody MVPOctober 10, 2018 at 4:08 am #223394NOTE: For those of a ‘nervous telemetry disposition’
Just installed SQMR kb4462926 on W8.1 without issue but, found 2 nodes of telemetry had appeared to the system due to telemetry being integrated in the SQMR patch, now neutered until next SMQR.<sigh>W7 will be much the same on SQMR kb4462923 patch (with integrated KB2952664)
I would suggest reading neutralize-telemetry-and-sustain-windows-7-and-8-1-monthly-rollup-model
by @abbodi86What, no integrated Adobe Flash update for W8.1 this month!
EDIT: Another method is to use WPD which claims to work on versions of Windows 7-10
Windows - commercial by definition and now function... -
Noel Carboni
AskWoody_MVPOctober 10, 2018 at 6:06 am #223409I’m always curious how others take control of such things, on the chance that there is an even deeper disablement process I don’t know about that could lead to even better performance…
What did you do (if anything) beyond changing the Customer Experience Improvement Program settings and configuring the scheduled tasks to Disabled?
I’ve been wondering whether disabling some of the underlying trace logging will reclaim a few percent of computer power, to be put to better use on actual work. Not long ago I followed some advice (I’m sorry to say I forgot the source) to disable tracing for something on my Win 8.1 system, and I do believe I picked up a few percent in software build speed (which a new version of Visual Studio promptly ate up again).
-Noel
-
Microfix
AskWoody MVPOctober 10, 2018 at 7:43 am #223427Noel, for me it’s not about performance, it’s more to do with MS and their intrusive hidden agendas, aka snooping in W7 and W8.1
What I did was re-check the system with Spybot Anti-Beacon to discover 2 nodes had been re-activated. Then using the script abbodi86 posted, checked all the settings within the script manually (in the registry) to ensure that they hadn’t changed and if so, revert them back – without actually using the script batch file at all, I don’t like the idea of not being able to revert back
I’ve been following ‘Crazyws’ (WindowsSpyBlocker author) who generated the firewall rules to circumvent MS snooping for a good while now, who continuously updates the firewall rulesets to reflect updated MS evolving methods for snooping. WPD utilizes the updated rulesets as well as implements useful switches to prevent further background data transfer.
When I discovered WPD, the plus was for me, being able to revert back to defaults (Important) should something go haywire online, it hasn’t, tested on both W7 and W8.1: WU works as intended and that’s all I need from MS, nothing more and nothing less. (QA Patches might help)
WPD is portable and satisfies what I wish to achieve. From within the portable app, one can export the blocked IP’s and check the IP addresses online. The internal switches within WPD all retain default values which is hard to find these days as a failsafe.
It’s not about performance for me, more peace of mind and an OS under my control..YMMV
Note: I have no association with WPD, Crazyws etc..and like what they are doing and producing to help others from the transparency at MS.
Windows - commercial by definition and now function...
-
-
-
anonymous
GuestOctober 10, 2018 at 7:57 am #223424Oops. I installed the updates from patch Tuesday today on a 1709 machine. Since then, a worrying text appears in Settings/Windows update. It says that Microsoft started distributing a new version of Windows and that from now on I should regularly check when I can get this wonderful piece of software on my systems. Mind you: I am on Semi Annual, 365 days deferral. Doesn’t sound good at all :-(((
-
anonymous
Guest -
geekdom
AskWoody_MVPOctober 10, 2018 at 8:07 am #223441Group A, B, W explanations are here:
https://www.askwoody.com/forums/topic/2000011-group-a-group-b-and-group-w-whats-the-difference/———
Please check the MS-DEFCON number in the upper-left corner.
When MS-DEFCON is at 3 or greater, it’s safer to patch.MS-DEFCON explanation is here:
https://www.askwoody.com/ms-defcon-system/On permanent hiatus {with backup and coffee}
offline▸ Win10Pro 2004.19041.572 x64 i3-3220 RAM8GB HDD Firefox83.0b3 WindowsDefender
offline▸ Acer TravelMate P215-52 RAM8GB Win11Pro 22H2.22621.1265 x64 i5-10210U SSD Firefox106.0 MicrosoftDefender
online▸ Win11Pro 22H2.22621.1992 x64 i5-9400 RAM16GB HDD Firefox116.0b3 MicrosoftDefender
-
-
anonymous
Guest -
anonymous
Guest -
PKCano
Manager -
anonymous
GuestOctober 10, 2018 at 1:47 pm #223568I am the anonymous that replied to @geekdom further up the page yesterday. I happen to be Group A, but not sure that affects this point. This is where I misunderstood geekdom when I read his result. (-v1 installed long ago, -v2 offered after cleared deck following October 2018 install)
This brought me to the temporary theory that October 2018 update itself causes a change that results in the new offer of -v2. Since geekdom already had -v1 onboard.
I’m not overly concerned, as one way or another this will resolve itself. I’m just noting what seems inconsistent to me.
-
-
-
anonymous
Guest -
dgreen
AskWoody LoungerOctober 10, 2018 at 10:14 pm #223685Just did a windows update check for October updates (I have it do not check)
FYI
KB3177467 was installed after new hard drive installed last fall (2017) when I deceided to go to Group A at that time.
September updates installed 10/2 (defcon 3) with no issuesToday’s update offerings
Important:
Kb4459922 (.net rollup)
MSRTNOTE: Rollup not offered. Has it been pulled?
Optional:
Kb4457139 2018-09 previewDell Inspiron 660 (new hard drive installed and Windows 7 reloaded Nov. 2017)
Windows 7 Home Premium 64 bit SP 1 GROUP A
Processor: Intel i3-3240 (ivy bridge 3rd generation)
chipset Intel (R) 7 series/C216
chipset family SATA AHCI Controller -1 E02
NIC Realtek PCLE GBE Family ControllerMSE antivirus
Chrome browserAttached Important updates, Optional updates, Hidden updates.
-
bsfinkel
AskWoody LoungerOctober 11, 2018 at 9:31 am #223808I run Windows 7 Professional 32-bit, and I have not experienced the Windows Update problem. On Tuesday, WU told me that there two updates:
KB4462923 2018-10 Security Monthly Quality Rollup Win 7
KB4459922 2018-10 Security and Quality Rollup for .NETI usually wait one day, per Woody, before I install them, but I installed both as soon as they were available. No problems and a reboot. Then I did another WU, and
KB3177467 Upd Win 7 (Servicing stack update)
appeared. I was curious as to why this did not appear with the first batch (now I know why), so I checked my manual install log. I had installed this previously on 22-Sep-2016. I then installed the new version, and a reboot was not required. I do not like MS’s re-use of patch IDs.
-
anonymous
GuestOctober 15, 2018 at 8:30 am #224750Hi all, I don’t know if you guys/girls have thought about this view, but I think if you must go through one installation of
windows6.1-kb3177467-v2-x86_abd69a188878d93212486213990c8caab4d6ae57.msu, [one],
then you will probably, [?], whitout your knowledge install KB 302 03 69.Instead of doing it in your mind that you have installed only one file, which have the valid name KB 317 74 67.
Why I think this is becauce I don’t have this file KB 302 03 69 installed on my system, and I have also compared this file KB 317 74 67
which I tried to install on the september installation, but I couldn’t do it. Becauce it was already installed on my system.Thouse two files are NOT same of the amount in the data.
[one]
windows6.1-kb3177467-v2-x86_abd69a188878d93212486213990c8caab4d6ae57.msu
have 4,214,830 kb.[Two]
Windows6.1-KB3177467-x86.msu
have 4,212,488 kb.Link:
http://support.microsoft.com/help/3177467If you read on the page you will find this text:
Update replacement information
This update replaces the previously released update 3020369.Best regards
ChristerDs. I’m within the group B and I have installed september without mars, april, may, june, july, augusty.
And when I check my logs all things are reported as normal within the information of my files. Ps. -
bsfinkel
AskWoody Lounger -
anonymous
GuestOctober 21, 2018 at 5:29 am #225927Hi @bsfinkel
I looked at “microsoft KB3020369 fixes KB2819745” through google and I found out that Microsoft decided to change it with this:
Source: https://www.google.ca/search?q=microsoft+KB3020369+fixes+KB2819745&hl=en-SE&source=hp&gbv=1&btnG=Search22 Apr 2015 … Update for Windows 7 (KB3020369). Important! Selecting a language below will
dynamically change the complete page content to that…
Source: https://www.microsoft.com/en-us/download/details.aspx?id=46827Details:
/Version: 3020369
/File Name: Windows6.1-KB3020369-x86.msu
/Date Published: 4/22/2015
/File Size: 4.0 MBRelated Resources:
Knowledge Base Article —> link
https://support.microsoft.com/en-ca/help/3020369/april-2015-servicing-stack-update-for-windows-7-and-windows-server-200Answer from the link… Issues that are fixed in this update:
Update 2819745 installation fails when you try to upgrade to Windows Management Framework (WMF) 4.0 by installing update 2819745 on a read-only domain controller (RODC) in Windows 7 Service Pack 1 (SP1) or Windows Server 2008 R2 SP1.Best regards
Christer
-
-
-
geekdom
AskWoody_MVPOctober 16, 2018 at 1:07 pm #225101Bleeping Computer reports on October Windows 10 updates:
https://www.bleepingcomputer.com/news/microsoft/known-problems-and-fixes-for-october-2018-windows-10-updates/On permanent hiatus {with backup and coffee}
offline▸ Win10Pro 2004.19041.572 x64 i3-3220 RAM8GB HDD Firefox83.0b3 WindowsDefender
offline▸ Acer TravelMate P215-52 RAM8GB Win11Pro 22H2.22621.1265 x64 i5-10210U SSD Firefox106.0 MicrosoftDefender
online▸ Win11Pro 22H2.22621.1992 x64 i5-9400 RAM16GB HDD Firefox116.0b3 MicrosoftDefender -
woody
Manager
-
-
bsfinkel
AskWoody LoungerOctober 26, 2018 at 3:01 pm #227471Another problem with Windows Update that I currently have on my Windows 7 Professional system – MSE updates. My MS Security Essentials icon is brown, not green. It tells me that my definitions are out-of-date. I ran Windows Update, and it told me that I needed to install update 1.279.572.0 . I try to install it, and it did not install. I checked the log (which I process with an awk script), and that 572 update was installed at 11:53 this morning. I did another “check for updates”, and it still told me that I needed to install 572 (along with two preview updates that I will not install).
And there was a case earlier (Oct 21) when WU told me to install definition update 102, when I had installed 102 on Oct 19, and the last pattern update I had installed was 247.
-
anonymous
GuestOctober 26, 2018 at 3:40 pm #227473@bsfinkel , there were similar posts regarding Defender earlier this month that resolved without corrective action. MSE and Defender update definitions from the same pool so I am jumping to conclude this may be similar. I am curious of three things:
Do you have KB3177467 installed?
Is it -v1 from 2016, or -v2 from 2018?
Does your WU setting ask to recieve updates for Microsoft products along with Windows Updates?
I’m sure the answer to the last is yes, because of what you have written. But I hope to learn if cutting that tie and updating through the MSE user interface would give a different result. I do not know that the Service Stack Update is responsible for this. I am noticing the coincidence of Microsoft AV’s showing failures during this same timeframe. The KB number is specific to Windows 7.
-
DrBonzo
AskWoody PlusOctober 26, 2018 at 5:44 pm #227487For what it’s worth:
Win 7 Pro x64, sp1, running MSE as the only AV program. I have MSE set to automatically update definitions every day at a set time. I usually also update it through the MSE interface once a day, and sometimes it will update itself automatically at some other time. I NEVER update MSE through the Windows Update interface. Occasionally I find that WU and MSE don’t ‘communicate’ correctly regarding the definition update numbers. Sometimes WU will say an update failed and sometimes it will show the latest update as being a slightly earlier version than MSE reports. If there is a discrepancy or a ‘failed’ entry in WU, I can almost always fix it by doing a manual update through MSE. Alternatively, if I just wait for MSE to auto update again, things almost always get back in sync.
I’ve also found that sometimes the update version reported in MSE doesn’t quite match up with the latest version found at https://www.microsoft.com/en-us/wdsi/definitions (scroll about half way down to see the latest version number)
I have v1 KB3177467 installed (no v2 yet).
I consider this to basically be a non-issue; mildly annoying that MS can’t get it right, but then I’m at the point where I’m more surprised when MS DOES get something right than when they don’t.
-
anonymous
GuestOctober 26, 2018 at 8:17 pm #227497I am the anonymous from #post-227473 above. A non-issue minor annoyance can still be an opportunity to learn rather than ignore. Even issues of unusual size (ht to The Princess Bride) can be discussed without stress.
My thought was that while we can easily receive definitions with the ‘optional’ SSU, there may be a condition where improving the engine might require the new ‘security’ SSU. If such an event were attempted, that could cause failure. My first questions were to establish which condition was already present.
I thought the response may be either, “never mind, all better now” or “still failing”; and could learn more from there.
Honestly, I haven’t even checked Microsoft information yet to see what the current engine version number should be, because it may change again before bsfinkel responds. DrBonzo, is your engine current when compared to documentation?
I ask because the one system that I look at already has -v2, and so would be expected to be current either way. It shows Engine Version: 1.1.15400.4
-
DrBonzo
AskWoody PlusOctober 26, 2018 at 9:39 pm #227501Yep, everything is current/up to date on my MSE.
In regards to your comment “… opportunity to learn rather than ignore.”, I’m running Win 7 now because for a variety of reasons, I must. In 14 months at EOL for Win 7 I will be out the door and using Mac and Linux exclusively. Since on my Win 7 machines the MSE “issue” has always resolved itself after the next one or two definition updates, I have chosen to ignore it. For me, learning more about Windows is a lost cause for my situation. Everyone makes ‘learn or ignore’ decisions every day about a wide variety of things, and in regards to computers I have chosen to learn more about Mac and Linux and less about Windows.
-
anonymous
GuestOctober 26, 2018 at 10:34 pm #227506That would seem to indicate my theory is busted. Thanks for saying -v1 yields same result. I’m near certain @bsfinkel has that already, but has not said. It is also possible the engine has not updated this month anyway. It is not a frequent event. May still be interesting to know if their experience is better updating through MSE directly.
On your lost cause and better plan for the future, it is a good plan. But it might not be bsfinkel’s plan.
-
DrBonzo
AskWoody PlusOctober 26, 2018 at 11:55 pm #227511Whatever bsfinkel’s plan is, I hope it works out for the best.
I understand someone being concerned about whether definition updates are or are not current, but given that the log shows a successful update, I would think the definitions are in fact current.
I consider Windows Update to be essentially worthless now and would put much more trust in a log file than in WU. And, I would suggest doing definition updates only through the MSE interface. I never do ANY updating through WU; I install ALL updates/patches manually from the MS Catalog.
-
-
-
-
-
bsfinkel
AskWoody LoungerOctober 28, 2018 at 9:28 am #227672Here is an update. This morning, after my weekly MSE full scan, the MSE icon in the system tray was brown. So I opened it, and it said that my definitions were out-of-date. So I told MSE to update. It sat for a long time (20-30 minutes) searching for updates. I was watching the network graph in Task Manager, and nothing was being updated. Then I open Windows Update to see what it told me. It said that pattern 691 was available, so I tried the installation from WU. Just before I had WU do the download, I saw that MSE was doing a download. Wu told me that 691 failed with error code 80070714 at 08:42. I wish that Microsoft would give a real error message instead of a hex code that requires an Internet search to investigate. I know from experience that that error code means that the update has already been installed. The log (via my awk script) said that the update had occurred at 08:40 (probably via the MSE window). But when I got the error code, MSE said that the update (number not given) was being installed. Eventually the MSE window told me that the (unknown) update failed at 9:01 due to Internet or network connectivity problem. And MSE tells me that my definitions are at version 140, installed 10/19 at 7:09PM.
I do not care how the MSE patterns are updated; I usually check via WU a few times each day. When I see a pattern update that I have not installed via WU, I really do not care if it was installed via WU automatically (these pattern updates are the ONLY updates I have WU install automatically) or via MSE. I am assuming that the updates are installed in the same place in the operating system, independent of how they were installed. MSE should not tell me that the update it download was not installed (due to a network problem), when it DID download and install an update. And why does MSE sit and think for 30 minutes, when WU thinks and downloads within a few minutes?
To answer previous questions:
> Do you have KB3177467 installed?
> Is it -v1 from 2016, or -v2 from 2018?Yes. #1 on 09/22/2016 and #2 on 10/09/2018.
> Does your WU setting ask to recieve updates for Microsoft products along with Windows Updates?
I think so. I am not sure what is meant by “Microsoft products”. I am not sure what WU setting I can check.
-
PKCano
Manager -
bsfinkel
AskWoody LoungerOctober 28, 2018 at 10:02 am #227677My settings:
Important updates: download but let me choose when to install
Recommended updates: checked
Who can install: Any user (I am the only user on this computer.)
Microsoft Update: checked (Give me updates for MS products.)
Software Notifications: checked (Show me about updates MS software.)
-
-
anonymous
GuestOctober 28, 2018 at 1:46 pm #227707bsfinkel, I am the anonymous #post-227497 from above. I see this continues for you. There are sources for better information available to you, but the reading is quite dry and tedious. Some may suggest third party solutions, or a clean uninstall and reinstall of MSE direct from Microsoft sources only.
I want to suggest consulting two .log files that are created and appended by MSE during activity. They can be found through Windows Explorer, as it is still called in my Windows 7, by following these branches: C:\Windows\Temp\MpCmdRun.log, and C:\Windows\Temp\MpSigStub.log
These are text files that will open in Notepad for review, and may be quite lengthy. Consult datestamps on entries separated by hyphen lines to get your bearings. New entries are appended at the bottom of the document. There is no need to edit changes. When you exit the document later, do not save any changes that may have occurred from an errant keystroke.
The CmdRun log tracks each instance the MsMpEng.exe filename is run as a command, either by you manually or automatically by a scheduled task. The SigStub log tracks specific details exchanged during those executiona. These may give you more questions than answers, but you will have a more reliable source behind your discussion.
For instance I myself found that the engine 1.1.15400.4 mentioned before was in fact updated on the 18th of October. It has been reported that -v1 of the SSU is sufficient to install that upgrade. That date is different than your reported hiccough, so may still be unrelated. But may be worth verifying for yourself using these sources.
It is a deeper dive than most users wish to endure. Certainly too tedious to waste time on daily. But if you want to look into repair rather than starting over with a new install, I hope this guidance helps you along the way.
Should you need to post more on this troubleshoot, may I further suggest starting a question topic separate from this long Patch Tuesday topic. May all your computing be fruitful.
-
-
OscarCP
MemberOctober 28, 2018 at 9:03 pm #227778To whom it might concern:
After waiting for nearly three weeks after Patch Tuesday and not seeing any signs of serious problems experienced by those already doing so, as is my invariable practice, I have installed today all the October patches for my OS: those offered through Windows Update, as well as KB3177467, that appeared afterwards, plus the Security Only and the one for IE11, both from the Catalogue, for Windows 7, SP1, x64 on my Win 7 Pro PC. And, again as usual, installing all patches as Group B. Restore points were created before the Windows-Update offered patches (by WU itself) and by myself before installing the rest of them.
As in most other months this year (and many previous ones over the years), no issues after doing that, so far. If anything bad happens later, I’ll be sure to let you know.
Group B, Windows 7 Pro, SP1 x64, CPU I-7 Sandy Bridge.
(Seriously less painful than updating as Group A; immensely less hurtful than Windows 10, any group, at least in my own experience.)
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV1 user thanked author for this post.
-
DrBonzo
AskWoody PlusOctober 28, 2018 at 10:25 pm #227786Thanks for the update OscarCP.
I’m assuming that when you say you first installed the updates offered by Windows Update you mean you installed everything you wanted but hid the October Rollup (KB4462923) and any others you didn’t want. After doing that was when the SSU (KB3177467 version 2 from 2018) showed up in Windows Update. You then installed the SSU and then the IE 11 and Security only patches from the MS Catalog.
-
Viewing 39 reply threads -

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Who knows what?
by
Will Fastie
15 minutes ago -
My top ten underappreciated features in Office
by
Peter Deegan
8 minutes ago -
WAU Manager — It’s your computer, you are in charge!
by
Deanna McElveen
5 hours, 9 minutes ago -
Misbehaving devices
by
Susan Bradley
18 minutes ago -
.NET 8.0 Desktop Runtime (v8.0.16) – Windows x86 Installer
by
WSmeyerbos
22 hours, 47 minutes ago -
Neowin poll : What do you plan to do on Windows 10 EOS
by
Alex5723
19 minutes ago -
May 31, 2025—KB5062170 (OS Builds 22621.5415 and 22631.5415 Out-of-band
by
Alex5723
21 hours, 21 minutes ago -
Discover the Best AI Tools for Everything
by
Alex5723
21 hours, 30 minutes ago -
Edge Seems To Be Gaining Weight
by
bbearren
11 hours, 39 minutes ago -
Rufus is available from the MSFT Store
by
PL1
19 hours, 42 minutes ago -
Microsoft : Ending USB-C® Port Confusion
by
Alex5723
1 day, 22 hours ago -
KB5061768 update for Intel vPro processor
by
drmark
1 day, 4 hours ago -
Outlook 365 classic has exhausted all shared resources
by
drmark
40 minutes ago -
My Simple Word 2010 Macro Is Not Working
by
mbennett555
1 day, 18 hours ago -
Office gets current release
by
Susan Bradley
1 day, 20 hours ago -
FBI: Still Using One of These Old Routers? It’s Vulnerable to Hackers
by
Alex5723
3 days, 11 hours ago -
Windows AI Local Only no NPU required!
by
RetiredGeek
2 days, 19 hours ago -
Stop the OneDrive defaults
by
CWBillow
3 days, 11 hours ago -
Windows 11 Insider Preview build 27868 released to Canary
by
joep517
3 days, 21 hours ago -
X Suspends Encrypted DMs
by
Alex5723
3 days, 23 hours ago -
WSJ : My Robot and Me AI generated movie
by
Alex5723
4 days ago -
Botnet hacks 9,000+ ASUS routers to add persistent SSH backdoor
by
Alex5723
4 days ago -
OpenAI model sabotages shutdown code
by
Cybertooth
4 days, 1 hour ago -
Backup and access old e-mails after company e-mail address is terminated
by
M W Leijendekker
3 days, 13 hours ago -
Enabling Secureboot
by
ITguy
3 days, 20 hours ago -
Windows hosting exposes additional bugs
by
Susan Bradley
4 days, 9 hours ago -
No more rounded corners??
by
CWBillow
4 days, 5 hours ago -
Android 15 and IPV6
by
Win7and10
3 days, 18 hours ago -
KB5058405 might fail to install with recovery error 0xc0000098 in ACPI.sys
by
Susan Bradley
4 days, 21 hours ago -
T-Mobile’s T-Life App has a “Screen Recording Tool” Turned on
by
Alex5723
5 days ago
Recent blog posts
Key Links
| S | M | T | W | T | F | S |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | 6 | 7 |
| 8 | 9 | 10 | 11 | 12 | 13 | 14 |
| 15 | 16 | 17 | 18 | 19 | 20 | 21 |
| 22 | 23 | 24 | 25 | 26 | 27 | 28 |
| 29 | 30 | |||||
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.