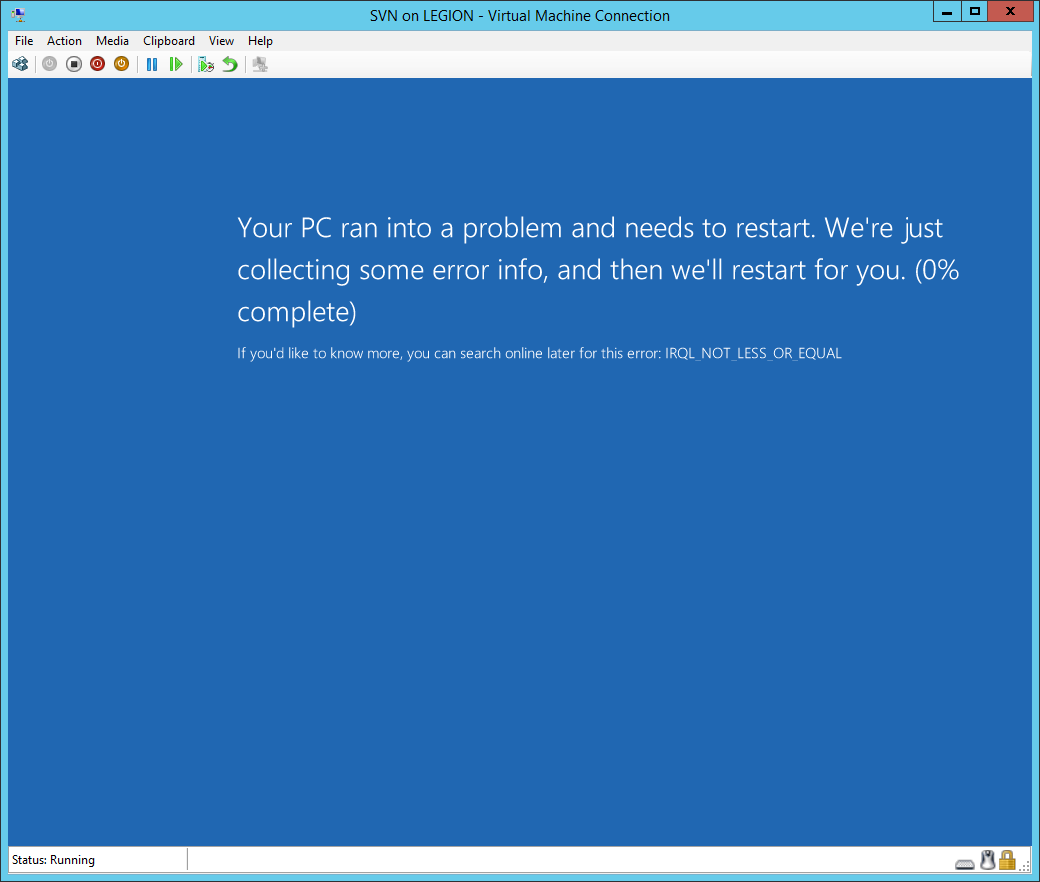
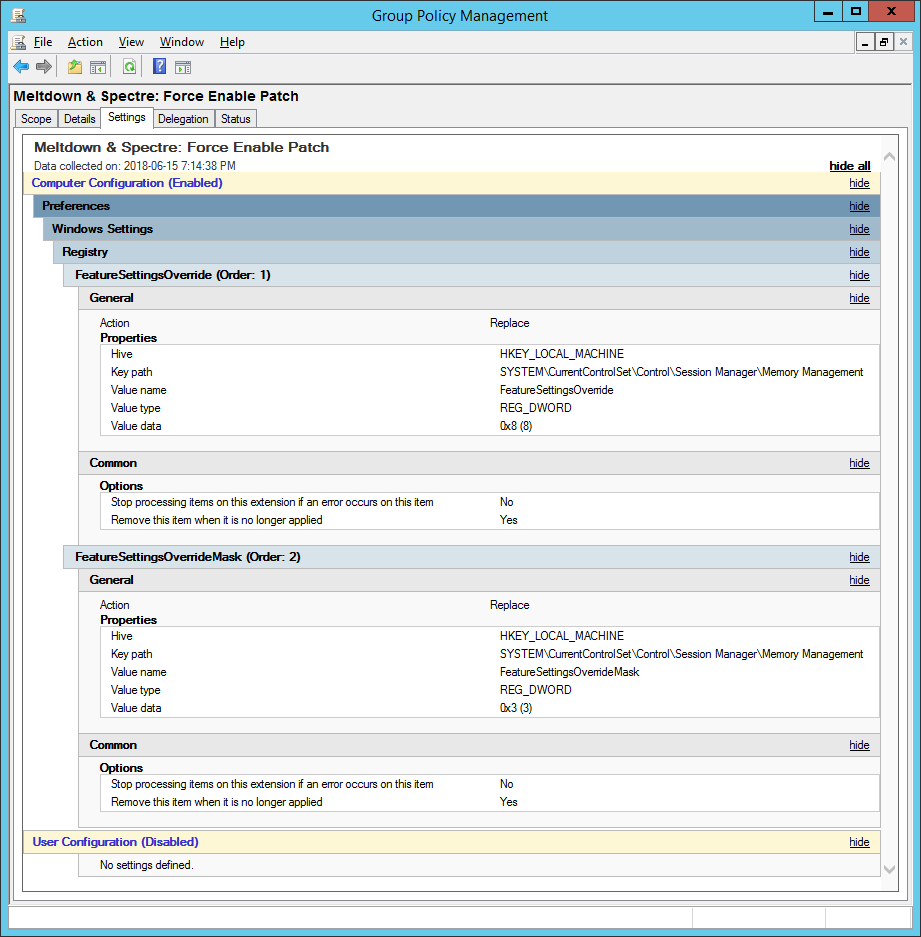
For those of you that like to dig a bit deeper into the details of patching, I highly recommend the Zero Day blog. For those who remember the detaile
[See the full post at: Patch Lady – light reading for the evening]
Susan Bradley Patch Lady/Prudent patcher