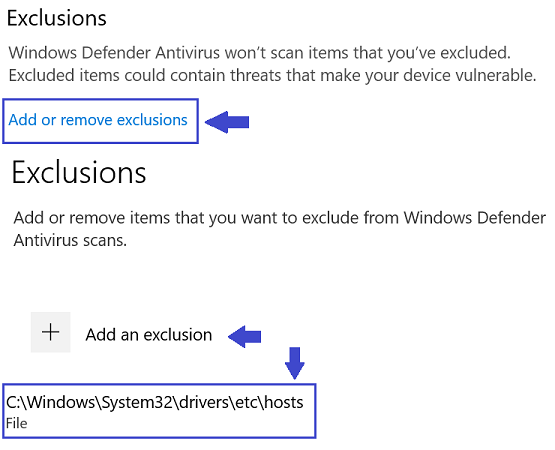
So the other day we had folks reporting issues with Defender and Western Digital drivers. Today Citrix Broker service was flagged as malicious and wel
[See the full post at: Patch Lady – Defender not having a good week]
Susan Bradley Patch Lady/Prudent patcher