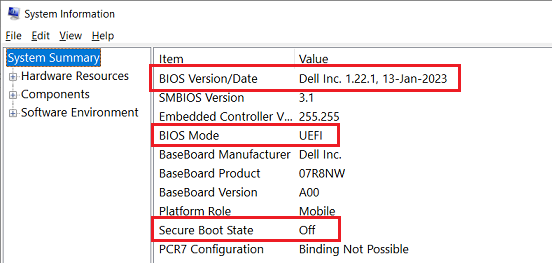
ISSUE 20.21.1 • 2023-05-23 By Susan Bradley Deploy May updates — and nothing but the updates. I’m lowering the MS-DEFCON level to 4 to encourage you t
[See the full post at: MS-DEFCON 4: Skip those Secure Boot scripts]
Susan Bradley Patch Lady/Prudent patcher