The times are a-changin’. Last October, Microsoft started lumping together all of its Windows 7 and 8.1 patches. Before October, we had separate patch
[See the full post at: MS-DEFCON 3: Get patched and brace yourself for a Malware-as-a-Service future]

|
Patch reliability is unclear, but widespread attacks make patching prudent. Go ahead and patch, but watch out for potential problems. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
-
MS-DEFCON 3: Get patched and brace yourself for a Malware-as-a-Service future
Home » Forums » Newsletter and Homepage topics » MS-DEFCON 3: Get patched and brace yourself for a Malware-as-a-Service future
- This topic has 136 replies, 38 voices, and was last updated 7 years, 11 months ago.
AuthorTopicViewing 53 reply threadsAuthorReplies-
Noel Carboni
AskWoody_MVPMay 21, 2017 at 6:50 pm #117325A Win 8.1 data point:
We appear well-synchronized in our judgment, Woody… I completed testing on my Win 8.1 virtual machine and chose to move my critical Win 8.1 workstation up to the May “Group A” patches today.
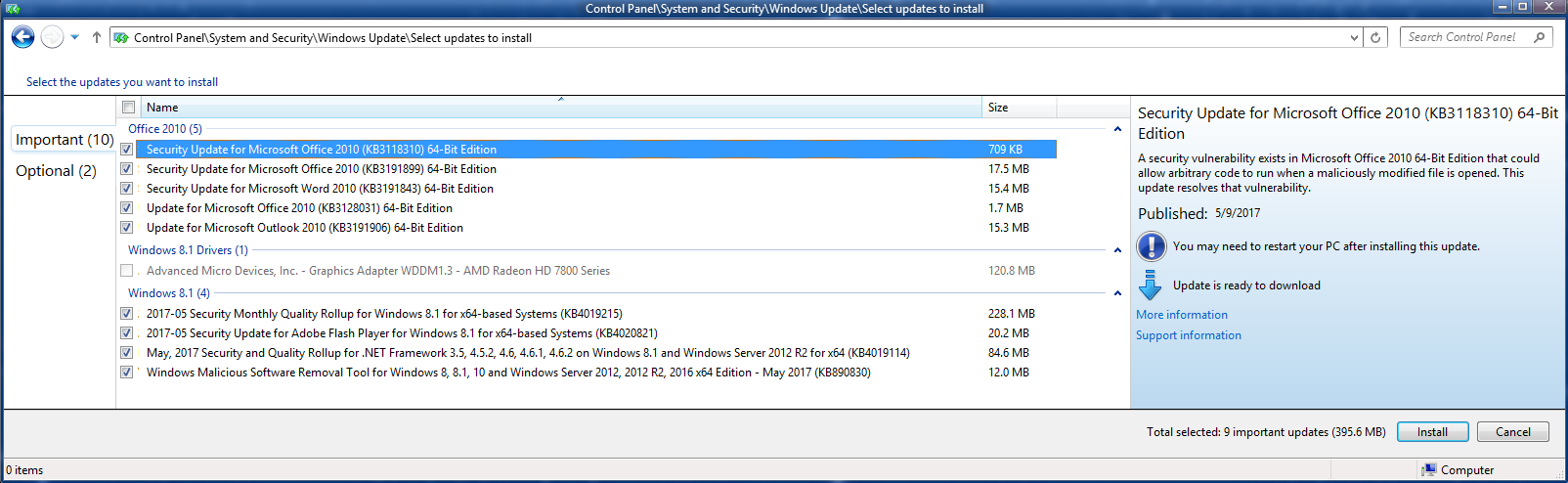
The Important updates listed as available follow. I hid the driver update (I no longer even have an ATI card) but chose to install all the others:
The optional updates that were offered are shown here. I did not install these.
After the updates went in I tested and benchmarked the hardware system and have found Win 8.1 is still apparently stable, with performance unaffected.
Miscellaneous observations after the installation:
- Several previously disabled scheduled jobs in the Microsoft Windows > NET Framework and Microsoft Windows > Windows Update areas were re-enabled by the updates and had to be disabled again.
- Service BITS was changed from DEMAND_START to AUTO_START and had to be set back to “Manual” again.
- The updates shown as installed in the output of a WMI QFE LIST command after completion didn’t precisely match the list of updates proposed to be installed by Windows Update prior to the installation. These are the ones listed as having been freshly installed:
- KB4014505
- KB4014510
- KB4019215
- KB4020821
- KB4015550 is no longer listed as installed by WMI QFE LIST. Apparently it was superseded.
- Several Office Document Cache Handler BHOs that had been removed were re-installed.
This machine, though Group A, does not send telemetry in. However, to accomplish a “Group A” Windows Update check it necessarily contacted the following servers:
- ctldl.windowsupdate.com
- sls.update.microsoft.com
- fe2.update.microsoft.com
- download.windowsupdate.com
-Noel
- Several previously disabled scheduled jobs in the Microsoft Windows > NET Framework and Microsoft Windows > Windows Update areas were re-enabled by the updates and had to be disabled again.
-
MrJimPhelps
AskWoody MVPMay 24, 2017 at 1:06 pm #118010I’ve had my Windows 8.1 laptop on fully-automatic updates ever since I bought it a couple of years ago. I have never had any problems with it.
I know that you don’t recommend fully-automatic updates, Woody; but I just wanted to share my results, nothing more.
Group "L" (Linux Mint)
with Windows 10 running in a remote session on my file server
-
MrBrian
AskWoody_MVPMay 21, 2017 at 6:56 pm #117329For those in Group A who also wish to have lesser amounts of telemetry, I recommend doing step 1 (Turn off the Customer Experience Improvement Program) of 2000007: Turning off the worst Windows 7 and 8.1 snooping before you install any Windows updates.
4 users thanked author for this post.
MrBrian
AskWoody_MVPMay 21, 2017 at 6:58 pm #117331For those who are in Group B due to wanting to reduce telemetry, I recommend also doing step 1 (Turn off the Customer Experience Improvement Program) of 2000007: Turning off the worst Windows 7 and 8.1 snooping.
TheSuffering
AskWoody Lounger-
Noel Carboni
AskWoody_MVPMay 21, 2017 at 7:54 pm #117347None have been specifically marked by Microsoft as being ones you should be aware of.
Sorry, couldn’t resist. 😉
In all seriousness Woody wouldn’t be moving the MS-DEFCON level up there were big problems, and he’d likely be mentioning them if there were significant lesser problems.
He DOES mention the “unsupported hardware” issue (if you have a new processor), and he DOES mention snooping. He also mentions the positives (patches for recently abused vulnerabilities).
-Noel
4 users thanked author for this post.
-
TheSuffering
AskWoody Lounger
-
-
Charlie
AskWoody PlusMay 22, 2017 at 4:06 pm #117717Win 7, Group B –
What about the Office Updates? There were two “newer” ones that came out after I finished the April updates. One of them appears to still be there. Are they okay now?
Also, I’ve got a Cumulative Security Update for Internet Explorer 11 which is dated 10/14/14!
Being 20 something in the 70's was far more fun than being 70 something in the insane 20's -
PKCano
ManagerMay 22, 2017 at 4:11 pm #117723If the Office updates are checked, go ahead and install them.
The old update for IE is there because the supersedence chain for it was broken when MS retired a mass of old updates recently. It will eventually disappear if you leave it alone, but if it gets installed it won’t hurt anything.
1 user thanked author for this post.
-
anonymous
GuestMay 21, 2017 at 7:57 pm #117346I have been Group W since October, with the lone exception of fixing the WannaCry problem. It wasn’t as scary as I thought it would be to install that, so I thought maybe I’d join Group B, but now I’m not so sure. I have a 5-year-old Win 7 laptop so I am in the clear on the “unsupported hardware” issue. Anyway, thanks as always for the information and clear steps. It’s just up to me to make a decision now, I guess.
-
slowdog
AskWoody LoungerMay 23, 2017 at 11:56 pm #117956#117346
That anonymous was me, for the record. I decided to join Group B and then rain into a snag with January and made an account to ask about it. I found the answer, though, and am now ready to continue installing missed updates. (My problem was that January’s kb 3212642 wouldn’t install, but I now know it’s because I had already installed March’s kb 4012212.) So far (so far!), Group B isn’t that bad.
Adul
AskWoody LoungerMay 21, 2017 at 8:57 pm #117360Group “W” should at least disable SMB v1:
This workaround was even recommended by Mocrosoft in their MS17-010
280park
AskWoody PlusMay 21, 2017 at 10:02 pm #117369RE: KB2987107 Cumulative Security Update for Internet Explorer 11 for Windows 7 for x64-based Systems
I have been in Group A since its inception. After installation of the April rollup the ancient KB2987107 mysteriously appeared on one of the two old Windows 7 computers that I maintain. Windows 7 was completely reinstalled on that computer on August 24, 2015. Windows Update history lists 12 cumulative security updates for Internet Explorer 11 subsequent to August 24, 2015 so it seems odd that an old cumulative update would now be needed.
There was some previous discussion here about the reappearance of KB2987107 but I do not recall if there was a consensus opinion regarding whether to install it. Any thoughts?
-
PKCano
ManagerMay 22, 2017 at 5:07 am #117534Microsoft retired a mass of old updates recently. In doing so, the supersedence chain waa broken for some of them. For that reason KB2987107 showed up. It will eventually disappear as MS cleans up the rest of the old updates. You can install it, or not. There are no adverse effects either way.
-
280park
AskWoody Plus
-
ch100
AskWoody_MVPMay 22, 2017 at 5:32 am #117539I see that there is not enough interest in your issue which is actually more interesting than most people realise and there is nothing occult about it. It is only an inoffensive bug.
Few weeks ago, Microsoft did maintenance and removed a large number of superseded (obsolete) updates for IE 11. They did not do it carefully enough and broke a certain supersedence chain. In fact they removed the most recent (11 in total if I remember well, but the exact number does not really matter) cumulative updates, while the oldest 3 have been neglected. After the fact, they removed the most recent 2 of those neglected, but still left one outstanding which is KB2987107.
You are not required to know all those details and in fact none of it would affect you or anyone else if you just run Windows Update and install everything that comes up there as it is the recommendation. I can explain it to you and everyone else, but for most of us outside of Microsoft it takes many years of experience and tests performed at night, outside the regular business hours to be able to understand all those issues. Telemetry is not one of those issues and you can safely ignore it. Just use your own judgement about it. If the law enforcement agencies are interested in monitoring anyone, they can do it regardless.
If you decide to “install” KB2987107, it would actually not install, but flag WU as being installed. It is harmless in fact, but useless at the same time. It is your option what to do with it. Both ways are correct. If it is annoying to you, “install” it, if not, leave it alone. At some stage, Microsoft people will figure out and remove it from the picture.
I am more on the practical side and a professional and not quite a hobbyist and I actually recommend to follow the manufacturer’s instructions and install everything that comes on Windows Update EXCEPT what is obviously not intended to be installed by end-users and named as “Preview”.
If one does not like Windows or corporations or believe they are sold to the dark side, then the same one should mind their own business and not use Windows. Nuff said.-
woody
ManagerMay 22, 2017 at 5:50 am #117541Telemetry is not one of those issues and you can safely ignore it. Just use your own judgement about it. If the law enforcement agencies are interested in monitoring anyone, they can do it regardless.
Peoples’ sensitivity to privacy, telemetry, and snooping, varies. That’s as it should be – what’s right for me may not be right for the guy down the street.
I have two big concerns:
> Companies that collect and use data about me should (a) tell me what data they’re collecting, (b) let me look at it and (c) give me a chance to either delete or at least challenge anything on file. That’s exactly how things stand with credit data in the US. I don’t like the credit laws, but they’re better than nothing.
> Law enforcement and other governmental organizations should have a high bar to clear before collecting any information.
Neither of those appear to be in the cards.
Microsoft’s Security-Only “Group B” approach is turning into something that requires near-full-time diligence to implement. That may be intentional, maybe not, but for most people it just doesn’t work.
You’re absolutely right about the “use it or change to something else” approach to Windows. In the past we didn’t have much choice. In the future we’ll have lots and lots of choices, each with its own benefits and drawbacks.
I keep coming back to Dr Watson and how it would ask, politely, before sending information to Microsoft. Times have certainly changed!
-
Geo
AskWoody Plus -
PKCano
ManagerMay 22, 2017 at 11:41 am #117630It depends it you are in Group A or group B.
For Group A the “Give me Recommended” box is checked.
For Group B the “Give me Recommended” box is unchecked.
See the instructions for patching Group A AKB2000004 and Group B AKB2000003 -
ch100
AskWoody_MVPMay 22, 2017 at 4:09 pm #117722@PKCano
That one is one of the views about the Recommended updates.
In fact there are variations in the interpretation of that setting.
We have Group B people asking if they have to install KB3125574, the May 2016 Convenience Rollup, which is essentially a collection of most Recommended Updates and very few others.
Strictly speaking, Group B users should not install any Recommended updates and install only Important and after October 2016 only Security updates. This can be managed only by using a custom solution and not by using Windows Update after October 2016 due to complexities of supersedence involved. Only few people on this forum and from my experience even professionals really understand all the complexities involved to do this correctly.There is a second Group A- approach in which none of the Recommended Updates is installed intentionally by selecting the checkbox, but it is expected that they will come regardless as part of the Cumulative Update model which is expected to follow in the next few months. Those users would still be secure in the mean time, but they are not taking benefit of the many enhancements which have been implemented since Windows 7 Service Pack 1 was released in early 2011. The functional enhancements come usually with Recommended Updates and in few cases were they are Critical they come under Important non-security.
There is no quality difference among Critical Important, Recommended and Optional. The classification is artificial and made by Microsoft as intended to represent the priority given to those updates.
The full Group A approach is to include Recommended and my personal recommendation is to include the Recommended and all Optional, except for those named Preview.
There are few exceptions which I consider that should not be installed regardless:
KB971033
KB3021917I am currently of the opinion that KB2952664 and its companion KB3150513 should be installed, but those 2 patches are everyone’s pet patches and everyone is entitled to an opinion about them.
-
-
280park
AskWoody PlusMay 22, 2017 at 8:28 pm #117777My principal concern was whether the reappearance of KB2987107 on one of my Windows 7 computers and not the other was an indication that Windows Update on the computer where it appeared had gone haywire.
I installed both KB2987107 and the May security rollup today and so far everything seems to be working fine.
Thanks.anonymous
GuestMay 21, 2017 at 11:00 pm #117364On my Win 7 Pro x64, in the Group A approach which I’ve been following since past October there are 4 patches checked and marked for install, those being the monthly rollup, .net rollup, MSRT and of course, the unwanted IE KB3008923…
So, for group A instructions I should install all of the first three right?
And what about the latter? Should I just leave it there or hide it?
-
PKCano
Manager -
ch100
AskWoody_MVP -
woody
ManagerMay 22, 2017 at 5:53 am #117543Since the “Get Windows 10” campaign, people have come to challenge what Microsoft’s doing to their machines. I think they have a right to ask – and get answers. Now that we’ve seen what MS can and will do to customers’ computers, it’s right to be inquisitive and skeptical.
-
ch100
AskWoody_MVP -
MrJimPhelps
AskWoody MVPMay 24, 2017 at 1:19 pm #118018This is easier than most people think.
When you first bought Windows and installed it, did you question what came with it?
Why do you question it now?When I first bought Windows (I assume you mean Windows 7 and Windows 8.1), Microsoft had a different way of doing things, a different implicit understanding with their customers — They did their best to accommodate the customer. Now, however, that has changed — they now force the customer to do things the Microsoft way.
One example: a good friend of mine who is about 70 years old and not very computer-savvy had Windows 7 on his computer. I installed GWX Control Panel to block the install of Windows 10. Soon after I did that, he got upgraded to Windows 10 without his consent.
That’s why I question it now.
Group "L" (Linux Mint)
with Windows 10 running in a remote session on my file server
-
-
-
Noel Carboni
AskWoody_MVPMay 22, 2017 at 11:41 am #117631When you first bought Windows and installed it, did you question what came with it?
Why do you question it now?Thank you for asking a GREAT leading question!
I have to start out by saying that they seem to be making a pretty good effort to keep updates of high quality so far. Assuming they haven’t built time bombs into them, that is. And yes, that used to be unthinkable!
Since you asked, I for one actually DID question it. Since the time of XP I have been following a 100+ page guide with every new system to tweak and augment Windows into a state where it’s reasonable and powerful to use. But beyond that…
Microsoft has in the past few years crossed a line of trust that’s not possible to uncross.
They pushed what was a few short years ago considered adware (malware?) through Windows Update. Windows Defender was once “anti-spyware”, and now they spy and it can’t be turned off without hacking. They’re undoing people’s choices during updates, and removing key choices in new systems, all the while claiming: It’s the best ever!
If they had failed at doing it the way they did it before (supporting user choice) maybe I could be a bit sympathetic to their changing their approach. But no, they took over the world by providing an OS that people could control!
They’re changing their business model now to be more predatory and it is clearly not motivated by a desire to make things better for we users.
At this point we could ask: How many years (decades) would it take for people to love Microsoft again, if they were to start respecting their users again now, and stop trying to act like a company they’re not?
-Noel
anonymous
Guest-
PKCano
ManagerMay 22, 2017 at 5:13 am #117536Being in Group B, you need to go back and install all the Security only updates you have not already installed as well as the latest Cumulative Update for IE11. See the instructions in AKB2000003
You may have trouble with the January update, if so, skip it.
-
anonymous
GuestMay 25, 2017 at 7:12 am #118096So, what will happen if I only patch the latest May 9, 2017—KB4019264 (Monthly Rollup)? The list on akb2000003, why is it so all of the patches is so important now when it was not for a half a year… What security patches is so much more important now to install that I cant miss anyone? Shouldn’t all the important security patches be in the latest update?
This is madness if Microsoft just dont give a **** about a group A person as it seems like if they had there computer turned off for a few months. That they have to go back in catalog.update.microsoft.com to find all the previous updates.
Yes I have KB4012212 separatly, and the .net quality rollup(kb4019112) failed installing because I only have Framework 4.6.1 installed on my computer. But somehow i got kb4014504 and kb4014511 from the rollup?
I only got more confused now and this makes me want to go Group W.
Edited for content.
Please follow the –Lounge Rules– no personal attacks, no swearing, and politics/religion are relegated to the Rants forum. -
PKCano
ManagerMay 25, 2017 at 7:44 am #118104So, what will happen if I only patch the latest May 9, 2017—KB4019264 (Monthly Rollup)?
KB4019264 is the May cumulative Monthly Rollup. It contains three parts: security patches, non-security patches and the cumulative patch for IE11 since Oct 2016. The patches listed in AKB2000003 are security-only patches only for the month of issue. If you install the cumulative Monthly Rollup, the security patches are included, so you don’t need both.
Yes I have KB4012212 separatly
If you have been offline and installed KB4012212, the March Security Only Update, that protected you from the WannaCry exploit. That was the least you could install for protection. If you had installed the March Monthly Rollup, KB4012215, you would have also had the security-only part.
People in Group A, who install the “Security Monthly Quality Rollup for Windows” through Windows Update, do not need to download and manually install the patches listed in AKB2000003 because those patches are included in the Monthly Rollup.
People in Group B do not install the Monthly Rollup. But they still need the security-only and the IE11 updates. Those are not available through Windows Update, so the people in Group B have to download and install them separately.he .net quality rollup(kb4019112) failed installing because I only have Framework 4.6.1 installed on my computer. But somehow i got kb4014504 and kb4014511 from the rollup?
KB4019112 is the Rollup for all the different versions of .NET. It contains four different patches, one for each version. KB4014504 and KB4014511 are the patches for the versions of .NET you have installed on your computer. Say “thank you” to Windows Update for picking the right ones for your computer (so you didn’t have to figure out which ones you needed). 🙂
-
anonymous
GuestMay 25, 2017 at 9:36 am #118108Thank you @PKCano for the kind response 🙂 and I am sorry for the bad words. My mind seems to anger up on so little things today. I think i try the links on akb2000003, there is only 7 of them i think.
And I have never updated my IE from IE8, because i use firefox for everything. Does that matter at all when i never use IE?
-
PKCano
ManagerMay 25, 2017 at 9:36 am #118118Yes, keeping IE up to date is important because, even if you are not using it, it is part of the operating system and other processes use it. IE8 is vulnerable to many exploits. You should upgrade it to IE11. If you are not installing the Security Monthly Quality Rollups through Windows Update, then you should install the Cumulative Update for IE11 for May found in AKB200003.
I use Firefox also. Keep it up to date too.
-
-
-
jshthng
AskWoody LoungerMay 22, 2017 at 12:53 am #117393Hi, I just have a question to ask. I have a computer that’s running on windows 7, and on i7-3630QM. I checked and found out that this processor is 3rd-Gen and belongs to the Ivy Bridge group. Do you think it’s safe to install the windows updates for my computer? Will it block future updates? Thanks!
-
anonymous
Guest -
PKCano
Manager
anonymous
GuestMay 22, 2017 at 12:53 am #117394morat
AskWoody LoungerMay 22, 2017 at 1:39 am #117409I’m using Windows 7 SP1 32-bit. I’m in Group B. I’ve been installing DotNet rollups via Windows Update. And security only updates & IE updates via Microsoft Update Catalog.
Everything worked well until this month.
After patching for May 2017, Windows Update says I should install KB2813347 (from 2013) and KB2987107 (from 2014). Belarc Advisor says I should install KB3126446 (from 2016), KB3212642 and KB4019108.
KB3212642 is the January 2017 security only update that I installed in February. I tried reinstalling KB3212642, but I get a “update is not applicable to your computer” message.
KB4019108 is the May 2017 DotNet security only update, but I already installed the May 2017 DotNet rollup.
I read about the “supersedence chain” issue in another thread. Very confusing.
-
PKCano
ManagerMay 22, 2017 at 5:26 am #117538KB2987107 (from 2014)
You can skip this one. It shows up because the supersedence chain was broken when MS retired the mass of patches recently.
KB2813347 (from 2013)
This fixes MS13-029. Go ahead and install. If it’s there because of broken supersedence, it won’t hurt anything.
KB3212642 is the January 2017 security only update
If it shows already installed, don’t worry about this one.
KB4019108 is the May 2017 DotNet security only update
You can try to install this if you want to. But it probably won’t install since you have the May Rollup already installed. It may be showing up because of incomplete supersedence.
samak
AskWoody PlusMay 22, 2017 at 4:12 am #117514Group B – just updated without any issues. Probably worth mentioning that the .NET patch took about 10 minutes to install, so be patient and don’t worry if it seems to be taking a while longer than usual.
Windows 10 Home 22H2, Acer Aspire TC-1660 desktop + LibreOffice, non-techie
AlexN
AskWoody LoungerMay 22, 2017 at 4:58 am #117532Some of us consider Windows10 to be “Malware-as-a-service” so the future is inevitable either way 🙂
Fortran, C++, R, Python, Java, Matlab, HTML, CSS, etc.... coding is fun!
A weatherman that can code1 user thanked author for this post.
TonyS
AskWoody PlusMay 22, 2017 at 7:09 am #117552Group B here – at least until this month, but in the light of the very helpful discussions on here, and the probable impending proliferation of malware, I am now considering swallowing hard, holding my breath, shutting my eyes and jumping to Group A, at least on one laptop.
Currently I’m up to date with Group B processes and patches to April 2017, all router ports are stealthed, antivirus is up to date and I’m running Malwarebytes premium. I can’t do anything about SMB1 as it appears to be necessary for accessing my NAS box.
No problems with processor as the machine is at least five years old. It’s an HP, running Win7 Home Premium x64. Currently WinUpdate is set to ‘never check’ and both ‘give me recommended updates in the same way’ and ‘software notifications’ are unticked, so I’ve got the old KB’s (2952664, 3021917, 3068708 and 3080149) all sitting as ‘Optional’ and uninstalled.
My question is, if I decide to move to Group A, should I leave settings as is and not install the old KB’s, or should I tick both ‘recommended’ and ‘software’ and install all Important updates if they are checked?
Many thanks to Woody and the usual trusty (and trusted) contributors.
Win10 22H2 Pro, MBAM Premium, Firefox, OpenOffice, Sumatra PDF.1 user thanked author for this post.
-
PKCano
ManagerMay 22, 2017 at 7:33 am #117558Instructions for Group A are in AKB2000004
To make it short:
Check the box “give me recommended like I get Important”
Check “Give me updates for other MS products”
Search for updates, do not check anything that is unchecked by default in the important updates.Please read the full instructions in AKB2000004.
-
TonyS
AskWoody PlusMay 22, 2017 at 8:00 am #117569Yes, read that, thanks. But that means 3 of the 4 old KB’s would be installed, leaving just 3021907 unchecked. I guess what I’m really asking is, is it necessary to install those three patches which are related to GWX compatability and/or telemetry? Before you ask, I have disabled Windows CEIP.
Win10 22H2 Pro, MBAM Premium, Firefox, OpenOffice, Sumatra PDF. -
PKCano
ManagerMay 22, 2017 at 8:09 am #117572You should not install anything that is unchecked by default.
You should avoid the telemtry related patches as listed in AKB2000003. If they show up in the important updates as checked, whether you hide them or uncheck them is immaterial as they won’t get installed either way. It is not recommended to hide any other updates – simply uncheck them prior to installing. -
TonyS
AskWoody Plus -
anonymous
GuestMay 22, 2017 at 9:57 am #117592 -
PKCano
ManagerMay 22, 2017 at 9:53 am #117599The instructions for Group A are in AKB2000004
-
-
-
abbodi86
AskWoody_MVP-
woody
ManagerMay 22, 2017 at 7:56 am #117568Excellent question. Best I can tell, the EternalBlue code was meant to infect Win XP and 8.1, in addition to 7, but somehow the code in WannaCry didn’t hook into either. The Metasploit version, I hear, did infect XP and 8.1, but WannaCry (which is based on the Metasploit implementation) did not.
I think.
-
abbodi86
AskWoody_MVP
-
ch100
AskWoody_MVPJan K.
AskWoody LoungerMay 22, 2017 at 8:28 am #117578Kinda “strange” update here… last update for this win7 was back on 26. March and expected a never-ending list, but got just 3?! One security quality, one .net and the usual “removal of bad sw”, in all 300 Mb.
The IE 11 update must have been included in the security, as IE 11 to my surprise is now up-to-date?
Everything’s smooth and no problems. As usual with .net it took longer than I bothered to wait for…
Faith in microSoft semi-restored…
-
PKCano
Manager
CraigS26
AskWoody PlusMay 22, 2017 at 8:44 am #117581While Listing my Successful Group A – Win 7-64 – Updates below …. In Updating Group A we are to Chk: “Give me recommended updates the same way I receive important updates”. Woody’s Step A4. “Install Patches” doesn’t mention “Recommended’s” as things we’ll see …. Is anyone actually Reading about / Installing Any Recommended’s?
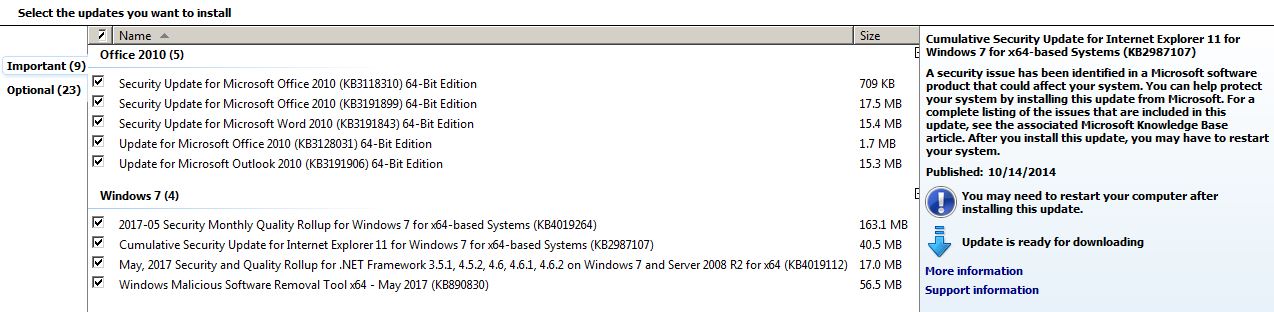
Group A: Omitted Silverlight on Purpose ….. KB4019264 May Security Monthly Quality Rollup W7-64 ….. . KB4019112 NET Framework 4.6.2, etc ….. KB890830 MSRT …. KB3118310 Office 2010 ….. KB3128031 Office 2010 …. KB3191899 Office 2010 ….KB3191843 WORD 2010 …. KB3191906 Outlook (my W7 Ver not active) …..
W10 Pro 22H2 / Hm-Stdnt Ofce '16 C2R / Macrium Pd vX / GP=2 + FtrU=Semi-Annual + Feature Defer = 1 + QU = 0
-
PKCano
ManagerMay 22, 2017 at 8:53 am #117582See the instructions for Group A patching in AKB2000004
Group A has “Give me Recommended updates the same way I get Important Updates” checked. Therefore the recommended updates appear under the “Important Update” list.
CraigS26
AskWoody PlusMay 22, 2017 at 9:28 am #117587See the instructions for Group A patching in AKB2000004 Group A has “Give me Recommended updates the same way I get Important Updates” checked. Therefore the recommended updates appear under the “Important Update” list.
Thanks, PK. I know I had checked that box long before but what happened was, like just now, the page went below my bottom border & I did NOT SEE the OK box to chk …. So the Chk mark disappeared when I exited Change Settings. I was sure we once agreed that “Importants Only” would be Installed, so my mind just rationalized that Give me Recommended’s like Importants was for some other reason than to install All of them, TOO.
Revisiting the New List opens a can of worms full of “Do Not Install” KB’s I kept list on KBs 3179573 (AUG Rollup), 2952664 (Cust Experience we turned-off) , 3021917, 3068708, 3137061 about VM machines I don’t use, ETC., KB313397 (not on list) makes me Disable Secure Boot in W7-64, which I’m scared to try.
Re-Reading the Instructions doesn’t Clarify WHAT people are doing with the Non-Important Updates populating the Important List… Some are installed ?….. All seems Crazy ???
Thanks for any clarification….
W10 Pro 22H2 / Hm-Stdnt Ofce '16 C2R / Macrium Pd vX / GP=2 + FtrU=Semi-Annual + Feature Defer = 1 + QU = 0
-
PKCano
ManagerMay 23, 2017 at 9:05 am #117864See #117861 below
anonymous
Guest-
PKCano
Manager
MrJimPhelps
AskWoody MVPMay 22, 2017 at 9:52 am #117597Group B isn’t dead, but it’s no longer within the grasp of typical Windows customers. Many of you reading this post are fully capable of sticking with Group B. Most Windows customers are not.
I have Windows 7-64. My technical knowledge and decades of IT experience makes me fully capable of sticking with Group B. However, I switched to Group A a few months ago, because I got a huge headache just thinking about what I had to do to keep up with Group B, and in fact, I wasn’t keeping up with it for that reason.
I have a Haswell CPU, and so I am unlikely to get bit with the “update bug”.
So far, no problems whatsoever that I am aware of.
Group "L" (Linux Mint)
with Windows 10 running in a remote session on my file server1 user thanked author for this post.
fl
AskWoody LoungerMay 22, 2017 at 10:54 am #117617I am in Group B, running Windows 7 SP1 on two Bookcamped Macs, 64 bit on one machine, 32 on the other. I just finished manually applying KB4019263 (the Security Only update) and KB4018271 (the IE11 Security update).
I then went to Windows Update where I installed KB4019112 the Security and Quality update for .NET, as well as the May version of the MSRT (KB890830).
When I rebooted my system and checked the Installed Updates, there is no trace of KP4019112, but instead I’m shown that KB4014511 and KB4014504 were just installed. I’m assuming that the former installed the two latter – am I correct?
A second question, for my own edification: The latest instructions for Group B recommends that the Windows Update Service be Stopped prior to applying the two Manual Updates mentioned at the top of this post. Is this simply to avoid any possible interference from any background update scanning which may be taking place, and could interfere with the smooth manual installations?
Thirdly, when all the dust had settled, I noticed that in Windows Update > Optional updates, KB 3181988 is listed, which purports to fix an error where a consistent error is shown whenever the UFC scans USBHUB.sys. I run software that requires the use of a USB dongle, so I’ve been reluctant to install this, in case it interferes with my otherwise functioning USB ports. Is this safe to install, or should I continue to ignore it?
Last of all, I’m guessing that if I was meticulous during all the GWX debacle, and have none of the telemetry patches listed in topic AK2000003, that I do not need to install and run KB3184143, which is supposed to remove all the GWX stuff from last year. Can I continue to ignore this one as well?
Mac Mini v. 6.2 (2012) with Win10 Pro 64 bit v. 1809
MacBook Pro v. 3.1 (2007) with Win7 32 bit - Group B Updater2 users thanked author for this post.
anonymous
GuestMay 22, 2017 at 11:05 am #117620You sounds way too afraid than you should from the article.
Yes, for some time ahead zero day state of art hacks are going to be released in the wild.
Yes, they may have the potential to make WannaCry repeat again.
But, I think very few people stopped to reason about the other side of the coin that allowed it to make the headlines? It attached unpatched systems, yes.
But unpatched systems with an already extremely sensible port naked to the internet (and indeed afaik it mostly targeted business; home-users, stupid or not, have firewalls and closed ports 99% of times)
https://blog.malwarebytes.com/cybercrime/2017/05/how-did-wannacry-ransomworm-spread/ (thanks ars for the tip!)
Very honestly, this seems the worst of the sins and problems. And for as much I’m expecting local escalations like it was raining, that really doesn’t seem as bad and worrisome as what happened this month.
I’m not advocating for group W (live 5 years unpatched), but as a happy group B user I’d urge you not to live in haste and take your usual time to be sure.
Alice
AskWoody LoungerMay 22, 2017 at 11:42 am #117633Woody-
You wrote
We’ve seen security patches released outside the monthly Security-only stream. There have been bugs in Security-only patches that were fixed outside of the Security-only stream.
Would you please provide more information on the security patches which were released outside the monthly Security-only stream and the bugs in Security-only patches which were fixed outside of the Security-only stream?
Thank you.
-Alice
anonymous
GuestMay 22, 2017 at 12:02 pm #117639? says:
thanx again for the group b update smoothness. you guys make it easy peezy compared to my slow lookup of it all. took a little more than an hour to do 3 win7 pro machines, last evening after i noticed the yellow 3. now for the clean up game. dism is always interesting with the removed kb’s…
i did notice on the one office ’10 machine it swallowed KB3118310 which seemed old however on a quick look it was released on 05\09’2017. i could not remember your notice about kb3128031 so in it went. i will let you know if it isn’t quite kosher. i’m also taking the KB4019112 instead of the security only version and it showed as kb4014504 as installed. they are probably just messin’ wit my Alzheimer’s?
love & kisses
-
PKCano
Manager -
anonymous
GuestMay 22, 2017 at 10:47 pm #117787? says:
thank you for the info on the # difference PKCano, after i cleaned up with DISM these were removed from the side-by-side: KB2913431-“causes windows to crash” WPF (antivirus) hotfix, Tcpip.sys, Netio.sys, Fwpkclnt.sys
KB2957189-MS14-031, TCP 06/10 2014, Netio.sys, Tcpip.sys, Fwpkclnt.sys
KB2972211-MS14-053, .Net 3.5.1, 09/09/2014 (DOS)
KB3092601-MS15-119, Winsock (EOP), 09/10/2017, Tdx.sys, Afd.sys
KB3135983-MS16-035, .Net 3.5.1 (signed XML’s) 03/08/2016, system.security.dllEdit html to text (from copy>paste?)
-
zero2dash
AskWoody LoungerMay 22, 2017 at 12:43 pm #117649I’ve been in Group B since October.
* WU/AU (automatic updates) disabled – don’t even check automatically. Completely disabled.
* My “method” was, use WU to check for updates, then find the security-only varieties and install (once the DEFCON was at 3 or better). Win and IE at least; the .NET, I grab the rollup because I don’t have any fear there of something being snuck in.
* “Give me recommended updates the same way I receive important updates” unchecked.
* CEIP disabled/opted-out.I’m starting to consider changing things…starting to consider switching to more of an “AB”…using WU to install the rollups, with CEIP disabled, but, only after the typical “incubation” period and DEFCON 3 or better rating. However, that has me thinking: what about that method is any different than what is baked in to Win10 – assuming you do something to defer your updates in 10?
I’m starting to think that I’m fighting a battle that I’ll never win, for nothing. I’m starting to wonder if I’m just “wasting my time”.
I want a secure system, but I also want a reliable system.
The lines in the sand are so blurred now, I don’t even know where they are anymore.
If CEIP is disabled anyway, Mr.Brian mentions that you’re not transmitting much telemetry anyway. So why am I banging my head against the wall several times a month every month to be in group B? On top of that, why not just go ahead and upgrade my machines to 10 using the ‘assistive technologies’ upgrade?Am I the only one?
wdburt1
AskWoody PlusMay 22, 2017 at 12:55 pm #117650“Group B isn’t dead, but it’s no longer within the grasp of typical Windows customers. Many of you reading this post are fully capable of sticking with Group B. Most Windows customers are not.”
I just finished downloading the April and May Security-only updates on two Win 7 computers and ran Windows Update and installed the .NET update as well. Total time invested: less than a hour.
It seems to me that you have identified an opportunity for someone. It’s inconvenient to have to manually download and install updates, but not a killer. The hard part is identifying what to install, the pitfalls, and how the game keeps changing. Right now you and PKCano are addressing the need. But so are those IT consultants (both for-pay and volunteer) who follow the subject. People pay for convenience, especially when it is provided by someone offering specialized knowledge.
How about updates-as-a-service? At its simplest, a monthly email that contains the links, advises when (and when not to) install them, etc.
Even better: A little piece of software that would do the job automatically, replacing Windows Update. Perhaps one or more of the antivirus products could take on this task.
Better yet, but won’t happen: Somebody other than M$ comes up with a way to provide security-only patches for Win 7 and/or other versions.
All this presumes that Group B is a viable strategy if the right updates are regularly installed. The theory that all updates must be accepted because Windows is a completely integrated, cohesive piece of engineering, and as such the instructions from the wizards who tend it must be obeyed at all times, is, well, a theory–and one contradicted by the patching screwups of the last year.
1 user thanked author for this post.
-
The Surfing Pensioner
AskWoody PlusMay 22, 2017 at 6:19 pm #117752I also have updated my two Windows 7 machines Group B-style in less than an hour this afternoon. I was sorting paperwork at the same time, and intermittently answering the phone. Where’s the problem? Falling off a log would have been harder – in reality, I imagine falling off a log on purpose is quite difficult.
Cybertooth
AskWoody PlusMay 22, 2017 at 1:53 pm #117665Woody, in your post you wrote that
That neat (if controversial and not really so neat) version of the world changed forever when, earlier this month, Shadow Brokers not only released the NSA’s trove which gave rise to the WannaCry worm, it also set up an auction for the “Shadow Brokers Monthly Data Dump” — what I’ve called Malware as a Service. You can bet that there are some very nasty malware surprises coming, all lovingly crafted by the US National Security Agency, stolen, then spread by Shadow Brokers.
Is it possible that the threat posed by these things has been (way, way) overstated? Three points on the example of WannaCry:
- I read that the total estimated ransom paid by victims is about $60K. (The amount could have grown since I read that.) At $300 per paying victim, that comes out to 200 who paid. Even if the real or current number is two orders of magnitude greater, that’s 20,000 paying “customers” out of the hundreds of millions of PCs in operation.
- Somewhere along the line, I also read estimates of the number of affected PCs (as opposed to people who paid the ransom) which were at around 200,000. That’s out of how many Windows PCs out there — 1.5 billion? Even if we stipulate that only Windows 7 computers are threatened, that’s still less than 1 in 3500 computers worldwide.
- I also read that most if not all AV vendors came up with protection against WannaCry within days or even hours of the initial attack. The developer of the anti-ransomware program HitmanPro.Alert says that even a 3-year-old version of their software stops WannaCry.
I dunno, sounds to me that in order to get this infection you almost have to want to get attacked. Bottom line: if we’re not in Group A, we don’t need to rush headlong into it. Keep an up-to-date AV and set up a multi-layered defense (e.g. anti-virus + anti-exploit). I’m not Group W (I’m in Group B), but I don’t think I’d be losing any sleep over this one if I were in W.
I could look up the figures given above. And updated stats are welcome.
Constructive comments also welcome.
1 user thanked author for this post.
-
PKCano
Manager -
ch100
AskWoody_MVPMay 22, 2017 at 7:41 pm #117772As an individual you can have your own strategy for patching and assess your own situation for what is acceptable, but this is not to be seen as advice for other users.
Woody and the MVPs here advise readers to have their systems secure and functional as much as possible and available.
Group W is not part of that advise and there are reservations about Group B of patching because people following it on this forum in general do not have the technical ability and instruments (Enterprise software) to follow it correctly.
People following Group B should have that level of understanding that they do not need list of patches and are able to devise their own patching strategy and method.
On the other hand, Group A is mainstream and suitable for everyone, end users and any enterprise.
Hummer4
AskWoody LoungerMay 22, 2017 at 1:54 pm #117666Excellent review of Woody’s recommendations for updating. (Win7 here). But shouldn’t there be an added (cautionary) note about installing “Preview” vs. “Quality” Monthly Rollups? For Groups A etc., trying to update window machines w/o downloading Preview (beta?) versions unnecessarily would avoid time-consuming backchecking. Or is this not much of a problem? I’m conscientious about leaving the Preview Rollups unchecked.
-
PKCano
ManagerMay 22, 2017 at 2:19 pm #117672You can read the patching instructions for Group A in AKB2000004
You can read the patching instructions for Group B in AKB2000003
Neither Group installs the “Preview” patch.
In fact, neither Group installs updates that are UNCHECKED by default.
anonymous
GuestMay 22, 2017 at 2:54 pm #117688I have been following Askwoody.com for a while when I researched GWX and found a discussion about the control panel and other discussions about patches to avoid. I installed the panel and stayed because here was a one-stop-shop for info on Windows 7. I didn’t have to search the net for info on bad patches.
When the group a, b, etc, system was implemented I joined Group B and had no problems with it. In the last few months I have found it more of a pain to sort out all of the extras like net patches and so on. I keep aware of my system but I am not an IT type so I decided to the Group A route.
—
Before I make the full transition to A can anyone give a definitive answer on:
Update for Windows 7 for x64-based Systems (KB3177467)
This pops up after WU is finished and several people have asked about it in the past but the only answer from the group at the time was “hold off installing it”. So… hide it or install it?
-firemind
Btw, thanks to everyone for helping out with computer stuff.
1 user thanked author for this post.
-
PKCano
Manager -
anonymous
Guest
-
SueW
AskWoody PlusMay 22, 2017 at 3:01 pm #117694I just completed Group B instructions: from the initial downloads of the 2 May updates for Windows 7 and IE, until the final restart, took 44 minutes.
There were 8 Important and 2 Optional Updates, of which 7 Important and 0 Optional were installed.
Thank you very much, once again, for such clear and easy-to-follow instructions — making this such a painless process.
Win 7 SP1 Home Premium 64-bit; Office 2010; Group B (SaS); Former 'Tech Weenie'anonymous
GuestMay 22, 2017 at 5:33 pm #117730Woody
I have been with Group B since it started back in Fall 2016. Today I decided it was getting to much for a non-techie to stay in group B, so I decided to move to Group A for ALL 3 computers. I have 3 computers, 2 Toshiba laptops win7-Pro and 1 HP desktop win8. I also decided to move to 8.1 on the desktop and started there first. I upgraded to 8.1 and all seems to have gone well. I upgraded and then checked for updates and it took 3 times to get them all. My concern is now every time I start the computer I get this message box when I go to the desktop screen: Run DLL c:\windows\system32\LogiLDA.dll module could not be found OK
I click ok and the box goes away. I am not sure what this is and I am not sure what I am to do. I did not get any error messages while upgrading or switching over to group A. Got any ideas? Thanks Dianne
-
PKCano
Manager
nospamboz
AskWoody LoungerMay 22, 2017 at 5:35 pm #117733So Win 7 Group B patching will be like it was for patching Win XP x64 (remember that?) during the year after Win XP patches stopped being released, but Server 2003 x64 patches (valid for XP x64) could be downloaded and installed manually.
Been there, done that, lost the T-shirt, more of the same.
1 user thanked author for this post.
Cybertooth
AskWoody PlusMay 22, 2017 at 5:38 pm #117735I believe you are missing the seriousness of the situation. WannaCry was just the first (we heard a lot about). There are more to come and the Shadow Brokers release more of the hacking tools.
Time will tell how serious these others really are.
anonymous
GuestMay 22, 2017 at 5:49 pm #117736After installing the updates today, after a search it was offered me a May MSRT again, probably a rerun, since it had the date of publishing of today… Which I’m installing right now… Did it happen to anyone?
1 user thanked author for this post.
-
Mcmacladdie
AskWoody LoungerMay 22, 2017 at 6:08 pm #117742It’s not just you… I’ve had this happen as well. Installed all but the old IE11 patch, rebooted, and after checking for updates again, it was there. The May MSRT shows as installed as well, and I did a check for updates right before installing, yet this one shows a publish date of today.
1 user thanked author for this post.
-
280park
AskWoody PlusMay 23, 2017 at 1:15 am #117826
anonymous
GuestMay 22, 2017 at 6:58 pm #117759I’m confused. Doesn’t Microsoft have a copyright on the phrase “malware-as-a-service”?
1 user thanked author for this post.
anonymous
Guestgrams
AskWoody Lounger-
grams
AskWoody Lounger
CraigS26
AskWoody PlusMay 23, 2017 at 6:36 am #117853My “Give me Recommended’s like Important’s” Box came UN-checked, and I asked above IF anyone read about / Installed Recommended’s. Was told to Re-Read AKB2000004.
Revisiting the New List opens a can of worms full of “Do Not Install” KB’s I kept a list on …. KBs 3179573 (AUG ’16 Rollup), 2952664 (Cust Experience we turned-off) , 3021917 (W10 Upgrade “appraiser“, 3068708 (Spy Patch), 3137061 about VM machines I don’t use, ETC., KB313397 (not on list) makes me Disable Secure Boot in W7-64, which I’m scared to try.
May I ask again since I don’t see anything from Re-Checking the R Box that I want to Install …. Are you guys Installing Everything in Importants , which Includes (in my W7-64 case) the Don’t Install Recommended’s listed above??
Defies my logic and limited IQ. Thanks for any clarification….
W10 Pro 22H2 / Hm-Stdnt Ofce '16 C2R / Macrium Pd vX / GP=2 + FtrU=Semi-Annual + Feature Defer = 1 + QU = 0
-
PKCano
ManagerMay 23, 2017 at 7:51 am #117861More information:
1. About the telemetry related patches, please see AKB2000007
2. I don’t find KB313397 listed in the Catalog. Typo(?)
3. AKB2000004 suggests not installing known problematic patches (see Step A3)My Personal experience:
>I don’t want telemetry. The ONLY patches I have hidden are KB2952664, KB3021917,KB3068708, and KB3080149.
>I have ALWAYS had “Give me Recommended” and “Give me updates for other products” checked. I have had no major problems because of it.
>I DO NOT check anything that is not checked by default.
>I have followed Group B type patching since Nov 2016 (avoiding Monthly Rollups). Basically the only thing I uncheck from WU is the Rollup.
>Under present circumstances, and except for the telemetry patches which will remain uninstalled, I am very much considering moving to Group A. I don’t want Win10 EVER, although I have three VMs with AU1607 and an Insider VM with CU1703. I want to be able to continue to feel (somewhat) safe with my Win7/8.1 computers until EOL. And I think that Group A may be the best way to do it. -
MrBrian
AskWoody_MVP -
PKCano
ManagerMay 26, 2017 at 6:06 pm #118274I saw the list of files that were changed/updated by the installation of KB 3068708 and KB3080149 in the “snooping test” thread.
Both KBs are related to CEIP and diagnostic telemetry.
What is your reasoning behind updating these functions (other than just later versions of the files).
Is there a possibility the later versions give MS more avenues for data collection than the ones you found in your earlier tests with the earlier versions? -
MrBrian
AskWoody_MVPMay 26, 2017 at 7:13 pm #118282@PKCano: I answered at https://www.askwoody.com/forums/topic/care-to-join-a-win7-snooping-test/#post-118281.
“Is there a possibility the later versions give MS more avenues for data collection than the ones you found in your earlier tests with the earlier versions?”
I tested the same versions of KB3068708 and KB3080149 for Windows 7 x64 in a number of tests at https://www.askwoody.com/forums/topic/care-to-join-a-win7-snooping-test/. Since KB3068708 and KB3080149 are related to Diagnostics Tracking Service, which is also installed by most of the Windows monthly rollups, I believe that your question reduces to whether Diagnostics Tracking Service can ever gather telemetry (other than telemetry related to the functioning of the Diagnostics Tracking Service itself). I believe that the answer to this question is “no” but I would welcome any further evidence on this.
-
-
-
ch100
AskWoody_MVP -
PKCano
Manager
-
-
-
PKCano
ManagerMay 27, 2017 at 7:46 am #118311
Morty
AskWoody LoungerMay 23, 2017 at 9:20 am #117865The times are a-changin’. Last October, Microsoft started lumping together all of its Windows 7 and 8.1 patches. Before October, we had separate patch[See the full post at: MS-DEFCON 3: Get patched and brace yourself for a Malware-as-a-Service future]
Thanks, Woody. I just checked for updates and there were six available. Two were unchecked.
These were checked:
2017-05 Security Monthly Quality Rollup for Windows 7 for x64-based Systems (KB4019264)
Cumulative Security Update for Internet Explorer 11 for Windows 7 for x64-based Systems (KB2987107)
May, 2017 Security and Quality Rollup for .NET Framework 3.5.1, 4.5.2, 4.6, 4.6.1, 4.6.2 on Windows 7 and Server 2008 R2 for x64 (KB4019112)
And Windows Malicious Software Removal Tool x64 – May 2017 (KB890830)These 2 were unchecked:
Microsoft .NET Framework 4.6.1 for Windows 7 for x64 (KB3102433)
and
Update for Windows 7 for x64-based Systems (KB3021917)Does that look right?
Morty
-
PKCano
Manager
Morty
AskWoody LoungerMay 23, 2017 at 9:35 am #117868Leave the unchecked updates unchecked. The update for IE is old. you can uncheck it and not install – it will eventually go away. But if it gets installed it won’t hurt anything. Get patched.
Will do. Much appreciated.
Morty
Noel Carboni
AskWoody_MVPMay 23, 2017 at 11:16 am #117879A data point:
I have updated a critical Win 7 system Group B style successfully:
Updates applied by direct download of .msu files from the catalog:
- KB4019263 – Security Only Update
- KB4018271 – Internet Explorer Rollup
I rebooted after each.
Unlike with my Win 8.1 system, which I updated “Group A” style, comparisons of detailed reports before and after revealed no disabled services or scheduled tasks that had been re-enabled.
-Noel
anonymous
GuestMay 23, 2017 at 12:58 pm #117884patched both computers today (win7, win8.1), both group b (security only & ie sec only). also installed all office 2010 related patches, .net security/quality rollup and flash player security update. so far so good.
on windows 8.1 last month i had the problem, that malicious software removal tool for april (kb890830) failed to install. and it never ever showed up again when searching for updates. today msrt for may got installed. but no april tool. kb890830 is still missing…
and fun fact: both msrt for april and may have the same number: kb890830…
-
PKCano
Manager -
anonymous
GuestMay 24, 2017 at 1:24 am #117957are msrt cumulative? is april version redundant / included in may version?
another quesion: after doing windows drive cleanup in “C:\Windows\Downloaded Program Files” i found some old files remaining:
swdir.inf (1 kb, january 29 2014), sysreqlab.osd (1 kb, april 2 2009), sysrequlab_nvd.dll (347kb, april 3 2009, signature: Husdawg, LLC).
can i delete these files?further i found old flashplayer installer (fp_ax_cab_installer) from 2009 in this folder which i deleted right off the bat.
-
PKCano
ManagerMay 24, 2017 at 4:48 am #117964are msrt cumulative? is april version redundant / included in may version?
MSRT is a malware removing tool. As such, it has new definitions with each new version just like your anti-virus. So in a way, it’s cumulative, as it keeps adding to the list of malware it can remove. Saying that, you should install each new version when it’s offered.
“C:\Windows\Downloaded Program Files” i found some old files remaining:
You can delete these, but if they are not taking up a huge amount of space leaving them will not hurt anything.
further i found old flashplayer installer (fp_ax_cab_installer) from 2009 in this folder which i deleted right off the bat.
You DEFINITELY do not want to install old versions of FlashPlayer.
-
HiFlyer
AskWoody LoungerMay 27, 2017 at 5:31 am #118306are msrt cumulative? is april version redundant / included in may version?
https://en.wikipedia.org/wiki/Malicious_Software_Removal_Tool
https://www.microsoft.com/en-us/download/malicious-software-removal-tool-details.aspx
-
-
CraigS26
AskWoody PlusMay 23, 2017 at 1:31 pm #117890More information: 1. About the telemetry related patches, please see AKB2000007 2. I don’t find KB313397 listed in the Catalog. Typo(?) 3. AKB2000004 suggests not installing known problematic patches (see Step A3) My Personal experience: >I don’t want telemetry. The ONLY patches I have hidden are KB2952664, KB3021917,KB3068708, and KB3080149. >I have ALWAYS had “Give me Recommended” and “Give me updates for other products” checked. I have had no major problems because of it. >I DO NOT check anything that is not checked by default. >I have followed Group B type patching since Nov 2016 (avoiding Monthly Rollups). Basically the only thing I uncheck from WU is the Rollup. >Under present circumstances, and except for the telemetry patches which will remain uninstalled, I am very much considering moving to Group A. I don’t want Win10 EVER, although I have three VMs with AU1607 and an Insider VM with CU1703. I want to be able to continue to feel (somewhat) safe with my Win7/8.1 computers until EOL. And I think that Group A may be the best way to do it.
I don’t find KB313397 listed in the Catalog … 2nd “7” omitted …Should have been 3133977.
Thanks for clarifying Hiddens you have. THEY were 4 of the reasons I couldn’t understand Installing the whole May List via Give Me Rec with Importants. Other than KB3133977 wanting me to DISable W7 Secure Boot, I’ll likely be comfortable with future Recommended’s UNTIL the Forum warns of a New One to HIDE.
Thanks for all that you contribute!!
W10 Pro 22H2 / Hm-Stdnt Ofce '16 C2R / Macrium Pd vX / GP=2 + FtrU=Semi-Annual + Feature Defer = 1 + QU = 0
The Surfing Pensioner
AskWoody PlusMay 24, 2017 at 7:48 am #117971Have just received this in an e-mail today:-
“Action Fraud has received the first reports of Tech-Support scammers claiming to be from Microsoft who are taking advantage of the global Wanna Cry ransomware attack.
One victim fell for the scam after calling a ‘help’ number advertised on a pop up window. The window which wouldn’t close said the victim had been affected by WannaCry Ransomware.
The victim granted the fraudsters remote access to their PC after being convinced there wasn’t sufficient anti-virus protection. The fraudsters then installed Windows Malicious Software Removal Tool,which is actually free, and took £320 as payment.
It is important to remember that Microsoft’s error and warning messages on your PC will never include a phone number. Additionally Microsoft will never proactively reach out to you to provide unsolicited PC or technical support.
Any communication they have with you must be initiated by you.PROTECTION / PREVENTION ADVICE
How to protect yourself:
• Don’t call numbers from pop-up messages.
• Never allow remote access to your computer.
• Always be wary of unsolicited calls. If you’re unsure of a caller’s identity, hang up.
• Never divulge passwords or pin numbers.
• Microsoft or someone on their behalf will never call you.
If you believe you have already been a victim• Get your computer checked for any additional programmes or software that may have been installed.
• Contact your bank to stop any further payments being taken
If you have been a victim of fraud or cyber crime, please report it to Action Fraud at http://www.actionfraud.police.ukThank you for subscribing to our alerts, to see a list of previously sent messages please visit Essex Community Messaging.”
– Looks like there’s a whole industry springing up around WannaCry!
anonymous
GuestMay 24, 2017 at 3:59 pm #118045? says:
i opened a second browser window on ie 11 last night and had lots of new content appear. it asked me if i liked it or wanted to go back to the way i had it set (hide frequent). i asked it to go back and it complied. i’m wondering if anyone else has had this behavior since installing KB4018271?
thank you
James Bond 007
AskWoody LoungerMay 25, 2017 at 12:31 am #118076Group B isn’t dead, but it’s no longer within the grasp of typical Windows customers. Many of you reading this post are fully capable of sticking with Group B. Most Windows customers are not.
In my opinion, the difficult part of staying with B is that you need to find, and then download yourself, the necessary updates each month from the Catalog. Installing them is easy once you got them.
I can understand why many people can find it difficult, especially compared to A. I don’t find it difficult at all personally, and I believe I have the “full time diligence” necessary to deal with it. In fact, I don’t really need to spend much time to search and download the updates myself as I know where to look for the necessary KB numbers.
Actually, I go further to “Full B”, which means that besides the IE and Security Only updates, I don’t get the .NET Rollup but instead get the necessary .NET security only updates (if they are available) from the Catalog and install them myself. For example for this month I get and install KB4014579 and KB4014599, the .NET 3.5 and 4.5.2 security only updates from the Catalog instead of getting the Rollup KB4019112 from Windows Update.
I have had no problems with this approach so far, and I am going to stay with it as long as possible.
This is just my preferred way of updating going forward. I am fine if any of you don’t agree with me. Let’s agree to disagree in that case.
Hope for the best. Prepare for the worst.
1 user thanked author for this post.
-
ch100
AskWoody_MVPMay 25, 2017 at 3:51 am #118088It is all good with Group B, only that you would never know exactly if you are fully patched only by using lists of released patches because of complex supersedence relationships, unless you use additional software, enterprise grade or some third-party good applications, not designed for enterprise.
This is the main problem with the complexity involved and I think Woody and anyone else responsible does not wish to assume responsibility for malware infecting user computers who are not patched consistently for the reasons above. -
The Surfing Pensioner
AskWoody Plus -
ch100
AskWoody_MVP
-
-
James Bond 007
AskWoody LoungerMay 25, 2017 at 12:47 am #118079Woody, I just observe something interesting in the description of KB4019217, the Preview Rollup for Windows 8.1 and Windows Server 2012 R2, just released:
https://support.microsoft.com/en-sg/help/4019217/windows-8-update-kb4019217
If a Server 2012 R2 system uses an Intel Xeon (E3 v6) family of processors, installing this update will block downloading and installing future Windows updates.
In my understanding, the Xeon E3 v6 family of processors (e.g. Xeon E3 1230 v6) is based on the Kaby Lake family of processors. And yet, Microsoft considers that “A Windows Server 2012 R2 system using such a processor will have Windows Update blocked after installing this update” as an “issue” that needs to be fixed.
I wonder why that is. Microsoft’s policy, it seems to me, is to block Windows Update for all people attempting to run Windows 7 or Windows 8.1 on Kaby Lake and Ryzen systems (and Windows Server 2008 R2 and Windows Server 2012 R2 are apparently also included in the block according to my tests on the VMware spoofed Kaby Lake virtual machine).
So why does Microsoft consider this “issue” to be a problem that needs to be fixed? Does this mean that if I get a system with a Xeon E3 1230 v6 CPU, say, and then install Windows Server 2012 R2 on it, then Windows Update should not be blocked and further updates should be available?
And by the way, the AMD Carrizo DDR4 “wrongly blocked” problem is still not fixed in this Preview Rollup, according to the description.
Hope for the best. Prepare for the worst.
1 user thanked author for this post.
CraigS26
AskWoody PlusMay 25, 2017 at 8:53 am #118110I ran WU again today and BOTH the KB4019264 May Rollup and MSRT, Successful 5/22 in WU History, Show again CHK’d for Dnload … + 6 New Files (a Security issue has been identified, etc, etc) ranging from 2014 – ’15 to Feb ’16.
For the May Rollup, particularly, advice is appreciated. Posted in Win 7 Update Forum but that’s been real “iffy” for me.
W10 Pro 22H2 / Hm-Stdnt Ofce '16 C2R / Macrium Pd vX / GP=2 + FtrU=Semi-Annual + Feature Defer = 1 + QU = 0
-
PKCano
ManagerMay 25, 2017 at 9:11 am #118113If one of the old patches is KB3177467 dated in 2016, that is the latest servicing stack. It has to be installed by itself and won’t show up in Windows Update until all other updates are installed. When/if it shows up, you need to install it.
Otherwise, the old patches (there was one for IE11 from 2014, may be more today but I haven’t looked, are the result of Microsoft’s retirement of a mass of old updates not too long ago. The supersedence chain for them was broken, hence they show up again. You can ignore them and eventually they will go away, but it does no harm if they get installed.MSRT was re-released a few days ago with the ability to remove WannaCry, so you will need to go ahead and install it.
The May Security Monthly Quality Rollup – did you look in the Update History to see if it failed. If so, it will keep showing up until it’s successful.
1 user thanked author for this post.
CraigS26
AskWoody PlusMay 25, 2017 at 9:22 am #118115If one of the old patches is KB3177467 dated in 2016, that is the latest servicing stack. It has to be installed by itself and won’t show up in Windows Update until all other updates are installed. When/if it shows up, you need to install it. Otherwise, the old patches (there was one for IE11 from 2014, may be more today but I haven’t looked, are the result of Microsoft’s retirement of a mass of old updates not too long ago. The supersedence chain for them was broken, hence they show up again. You can ignore them and eventually they will go away, but it does no harm if they get installed. MSRT was re-released a few days ago with the ability to remove WannaCry, so you will need to go ahead and install it. The May Security Monthly Quality Rollup – did you look in the Update History to see if it failed. If so, it will keep showing up until it’s successful.
BOTH the KB4019264 May Rollup and MSRT, —–Successful 5/22 in WU History —–, Show again CHK’d for Dnload. That’s my issue. I’ve read Forums prior where the same Update keeps Re-appearing BUT I haven’t experienced it with Rollups. Install again or Wait & see IF it disappears?
KB3177467 is Not on the list. The other older ones All just start with “A security issue has been identified … but No specifics.
W10 Pro 22H2 / Hm-Stdnt Ofce '16 C2R / Macrium Pd vX / GP=2 + FtrU=Semi-Annual + Feature Defer = 1 + QU = 0
-
PKCano
ManagerMay 25, 2017 at 9:27 am #118116You can try to install the May Rollup again. It may give you a message that it’s already installed. I wouldn’t try a third time – it will disappear at the latest when the June Rollup comes out.
I think MS is still working on retiring the old updates, so they may break more supersedence chains in the process before they’re done.
CraigS26
AskWoody PlusMay 25, 2017 at 10:13 am #118121You can try to install the May Rollup again. It may give you a message that it’s already installed. I wouldn’t try a third time – it will disappear at the latest when the June Rollup comes out. I think MS is still working on retiring the old updates, so they may break more supersedence chains in the process before they’re done.
The Rollup Installed and the MSRT Failed but Neither Returned on the next Check for Updates. (4) of the (6) new files from ’14 – ’16 disappeared on their own, so I’m posting this Only to show anyone reading here that WU remains a moving target and don’t panic when WU gets creative. Persevere………….
W10 Pro 22H2 / Hm-Stdnt Ofce '16 C2R / Macrium Pd vX / GP=2 + FtrU=Semi-Annual + Feature Defer = 1 + QU = 0
3 users thanked author for this post.
-
PKCano
Manager -
Noel Carboni
AskWoody_MVPMay 25, 2017 at 11:14 am #118126WU remains a moving target and don’t panic when WU gets creative.
That’s one of the legitimate reasons some folks go “Group B” and take over control of what updates are installed directly from the catalog.
It’s all about wanting the outcome of updating activities to be that the system “just works” afterward. 🙂
-Noel
ozbadcat
AskWoody LoungerMay 28, 2017 at 7:25 pm #118485To PKCano – PK, when I do May Security only for NET – kb4019108 – it only shows one option – Windows Server 2008 R2 . So I click on the title – then more information – and then it comes up with 4 options.
The one I want is – 4014579 Description of the Security Only update for the .NET Framework 3.5.1 for Windows 7 Service Pack 1 and Windows Server 2008 R2 Service Pack 1: May 9, 2017
However when I put kb4014579 into the Update Catalog – it says ‘we did not find any result for 4014579’
Has that update been pulled or whatever ????? …… what do I do ???
THANKS, Rick in Oz 🙂
-
PKCano
ManagerMay 28, 2017 at 7:53 pm #118487You can’t search the Catalog for the four parts of KB4019108 separately. You can only search for the Rollup
If you go to more information and click on KB4014579 link, it takes you to this pageI don’t see a download specific for Win7 .NET 3.5.1, only a warning and some Registry or gpedit edits.
My advice would be to install the .NET Rollup through Windows Update and let it install whatever is necessary for v3.5.1 instead of trying to outguess MS..
I use the Rollup myself.
ozbadcat
AskWoody LoungerMay 28, 2017 at 11:19 pm #118507Hi again PKCano – I am transferring a whole portion from the knowledge base as it was from another contributor asking about the SAME question I had asked you previously today – related to SECURITY ONLY NET patches : …… and my experience in earlier in the week downloading INDIVIDUAL patches from kb4019108 …… so I thought I would elaborate to you that they now appear to have been removed from the Windows Update Catalogue
anonymous wrote:
Has MS dropped the security only patches for .net framework 4.6.1 for win7 sp1 x64? as I’m only seeing the security and quality ones in their ms catalogue there was an April security only patch
Says that it’s for Win7 sp1 but the catalogue says it’s for 2008 server ???
THANKS Anonymous – I did write to PKCano earler today about the EXACT same issue – from kb4019108 earlier this week I was able to download NET Security Only patches 4014599 ( Net 4.5.2 ) and also 4014579 ( Net 3.5.1 ) and install them on my 3 computers – I then deleted them from downloads as I no longer needed them. Then a friend wanted me to install them on his machines but when I went to the Windows Update Catalogue they were NO LONGER THERE as individual downloads…… so I asked PKCano – if those individual patches had been pulled ????? …… something has happened ….
He advised to then use the Security ROUNDUP version …. something I was trying to avoid ….preferring the Group B Security ONLY versions
Rick in Oz 🙂
-
Kirsty
ManagerMay 28, 2017 at 11:56 pm #118508Says that it’s for Win7 sp1 but the catalogue says it’s for 2008 server ???
It does say it applies to Win7 SP1, but it does not want to download the proper file from the MS catalog. I wonder if this is a temporary glitch? The catalog downloads for some of this month’s security .net rollups are quite large (170+mb).

1 user thanked author for this post.
-
HiFlyer
AskWoody LoungerMay 29, 2017 at 7:48 am #118543It does say it applies to Win7 SP1, but it does not want to download the proper file from the MS catalog. I wonder if this is a temporary glitch? The catalog downloads for some of this month’s security .net rollups are quite large (170+mb).
Highly doubtful! IMHO more likely another MS “improvement in customer experience” and/or another herding method.
Re: ozbadcat/kirsty/pkcano posts on this matter on this forum, AKB20000003, and on the Security-only .NET Updates: May 2017 forum.
My experience for May updates. Group B, 3 laptops (2xWin7SP1, 1Win8.1, all x64)
No problems all 3 machines with SOQU 4019263/40192113 and IEll4018271 updates.
Both Win7 machines have .net 4.6.1 installed. Win8.1 has 2.0, 3.0, 3.5, 4.5. (sez Speccy)
——————-
Win8.1 laptop; .net rollup KB4019114 offered by WU installed o.k.
——————–
#1Win7SP1Pro; .net rollup KB4019112 offered by WU installed o.k.
It took about 45minutes.
——————
#2Win7SP1HP; .net KB4019112 offered by WU I cancelled the installation after one hour (it was very late). WU updates show it failed. It is not installed.
WU would not offer anything for .net thereafter on repeated tries with this laptop.
I c0uld not find any ‘.net updates-only’ on the MS update catalog as others have reported.
Finally I went to MUC and brought up KB4019112 and tried to download it. I was shown the included kbs.
I downloaded and installed: “ndp4014511 for NET 4.6.1 win7sp1x64”
Q: Was that o.k. or a mistake?
Just found this site which seems to indicate xxx4511 is the right one.
https://blogs.msdn.microsoft.com/dotnet/2017/05/09/net-framework-may-2017-monthly-rollup/
HF
-
anonymous
Guest -
PKCano
ManagerMay 29, 2017 at 8:18 am #118547That shouldn’t be a problem.
In fact, for those aspiring to be in Group B, You will find the instructions advise installing the “Security and Quality Rollup for .NET Framework.” See step B4 in AKB20000031 user thanked author for this post.
-
Volume Z
AskWoody LoungerMay 29, 2017 at 8:33 am #118549Definitely OK, but it may not be enough. Always add the .msu offering. It’s an update to the .NET Framework version that shipped with Windows and always applies. Applicability of the .exe files depends on optional versions installed. If in doubt, just try.
Regards, VZ
1 user thanked author for this post.
-
-
ozbadcat
AskWoody LoungerMay 29, 2017 at 5:03 pm #118601There appears to even be issues with the NET Security and Quality Rollup version – kb 4019112 – as over in Seven Help forum – quite a few complaints about problems downloading – as well as installing it ( taking ages , if at all )
Yesterday, from Windows Update Catalog, I was able to download 1 of the individual files from it – kb4014504 ( NET 3.5.1 ) – this morning it says ” We did not find any results for “kb4014504” – so it looks like that has been pulled as well
Something is up with it …… anyone else had problems with it ?????
Rick in Oz 🙂
-
Volume Z
AskWoody Lounger
Viewing 53 reply threads -

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Return of the brain dead FF sidebar
by
EricB
4 minutes ago -
windows settings managed by your organization
by
WSDavidO61
1 hour ago -
Securing Laptop for Trustee Administrattor
by
PeachesP
3 hours, 48 minutes ago -
The local account tax
by
Susan Bradley
3 hours ago -
Recall is back with KB5055627(OS Build 26100.3915) Preview
by
Alex5723
6 hours, 21 minutes ago -
Digital TV Antenna Recommendation
by
Win7and10
5 hours, 56 minutes ago -
Server 2019 Domain Controllers broken by updates
by
MP Support
18 hours, 13 minutes ago -
Google won’t remove 3rd party cookies in Chrome as promised
by
Alex5723
19 hours, 52 minutes ago -
Microsoft Manager Says macOS Is Better Than Windows 11
by
Alex5723
23 hours, 4 minutes ago -
Outlook (NEW) Getting really Pushy
by
RetiredGeek
1 hour, 30 minutes ago -
Steps to take before updating to 24H2
by
Susan Bradley
1 hour ago -
Which Web browser is the most secure for 2025?
by
B. Livingston
5 hours, 56 minutes ago -
Replacing Skype
by
Peter Deegan
13 hours, 26 minutes ago -
FileOptimizer — Over 90 tools working together to squish your files
by
Deanna McElveen
16 hours, 56 minutes ago -
Excel Macro — ask for filename to be saved
by
nhsj
1 day, 1 hour ago -
Trying to backup Win 10 computer to iCloud
by
SheltieMom
4 hours, 21 minutes ago -
Windows 11 Insider Preview build 26200.5570 released to DEV
by
joep517
2 days, 23 hours ago -
Windows 11 Insider Preview build 26120.3941 (24H2) released to BETA
by
joep517
3 days ago -
Windows 11 Insider Preview Build 22635.5305 (23H2) released to BETA
by
joep517
3 days ago -
No April cumulative update for Win 11 23H2?
by
Peobody
1 day, 12 hours ago -
AugLoop.All (TEST Augmentation Loop MSIT)
by
LarryK
3 days, 1 hour ago -
Boot Sequence for Dell Optiplex 7070 Tower
by
Serge Carniol
3 days, 16 hours ago -
OTT Upgrade Windows 11 to 24H2 on Unsupported Hardware
by
bbearren
3 days, 19 hours ago -
Inetpub can be tricked
by
Susan Bradley
2 days, 3 hours ago -
How merge Outlook 2016 .pst file w/into newly created Outlook 2024 install .pst?
by
Tex265
2 days, 13 hours ago -
FBI 2024 Internet Crime Report
by
Alex5723
3 days, 23 hours ago -
Perplexity CEO says its browser will track everything users do online
by
Alex5723
1 day, 8 hours ago -
Login issues with Windows Hello
by
CWBillow
4 days, 10 hours ago -
How to get into a manual setup screen in 2024 Outlook classic?
by
Tex265
3 days, 22 hours ago -
Linux : ARMO rootkit “Curing”
by
Alex5723
4 days, 22 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.