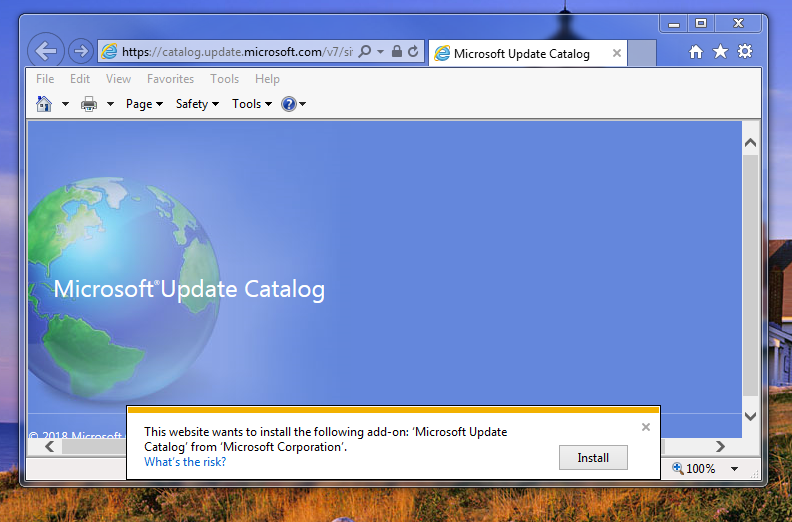
I didn’t believe it until I saw it. And you can, too. Post coming in Computerworld. Thx, Stefan Kanthak, Günter Born
[See the full post at: Microsoft using insecure HTTP links to distribute security patches through the Update Catalog]

|
Patch reliability is unclear, but widespread attacks make patching prudent. Go ahead and patch, but watch out for potential problems. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
-
Microsoft using insecure HTTP links to distribute security patches through the Update Catalog
Home » Forums » Newsletter and Homepage topics » Microsoft using insecure HTTP links to distribute security patches through the Update Catalog
- This topic has 59 replies, 24 voices, and was last updated 3 years, 1 month ago by
anonymous.
AuthorTopicViewing 24 reply threadsAuthorReplies-
zeuswoz
AskWoody LoungerFebruary 16, 2018 at 10:59 am #167825Holy c***, so they are. I just checked myself. Example below
Rgds, Zeus
-
anonymous
Guest
-
Rick59
AskWoody LoungerFebruary 16, 2018 at 11:09 am #167836It seems like MS is just stumbling from one disaster to another.
My daughter really likes her new pixelbook, but for myself I find the screen too small and I’ve never been a big fan of laptop keyboards and touchpads. It still is a very nice laptop that oozes high quality and I believe will get a fair number of buyers.
Looks like ASUS is brnging out a new chromebox some time this year
https://www.androidheadlines.com/2018/01/hands-on-with-the-new-asus-chromebox-3-ces-2018.html
Looks interesting and could be a serious option for myself. Just hoping I get a Meltdown patch soon for my Win7-32 machine and then I could wait for the new chromebox. If not and real world exploits start showing up I might have to look at an Apple product.
zero2dash
AskWoody LoungerFebruary 16, 2018 at 11:11 am #167839I’m curious what the point is in this kerfuffle, other than it’s not a great idea (which is par for the course with MS).
Short of a MITM attack/circumvention, what exactly is the paranoia over?
I don’t recall seeing mass hysteria over sites using FTP instead of SFTP, so why exactly is using HTTP instead of HTTPS any different?1 user thanked author for this post.
-
OscarCP
MemberFebruary 16, 2018 at 12:40 pm #167877Phishing? Fake, Trojan “updates” bearing viruses, worms?
Maybe the PC has to be already compromised by a preliminary infestation with malware opening the way to the one in the HTTP address?
How much of a protection really is HTTPS these days?
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV -
zero2dash
AskWoody LoungerFebruary 16, 2018 at 1:39 pm #167909I’m not disagreeing that there can be issues, but in the context of this and whether or not it will cause users issues, the odds are (and I’d say they’re favorable odds) are that it won’t.
Riddle me this: what prototypical uneducated PC owner/user is downloading Windows Updates piecemeal from somewhere other than Windows Update?
The answer of course is “no one”. Anyone capable of downloading updates from the Microsoft Catalog is going to be a novice techie (at worst). Such a person is not going to be easily fooled by any of the potential issues that you listed.
This seems very much like a clickbait article to me. Mission accomplished, I guess.
1 user thanked author for this post.
-
woody
Manager -
lurks about
AskWoody LoungerFebruary 17, 2018 at 9:41 am #168060HTTP connections are vulnerable to MTM attacks and I would think someone who is trying one might find Windows updates via HTTP an interesting way to try one.
HTTPS connections are encrypted and rely on a handshake between the browser and server. Once established MTM attacks become almost impossible if the proper protocols are used. About the only reliable to attack an HTTPS connection is to fool the user into initially connecting to a rogue site; more of a social engineering problem than a technical one.
-
-
gborn
AskWoody_MVPFebruary 16, 2018 at 11:16 am #167841A few more details may be read within my blog post Microsoft delivers updates via HTTP & more security obscurity
Ex Microsoft Windows (Insider) MVP, Microsoft Answers Community Moderator, Blogger, Book author
https://www.borncity.com/win/
-
abbodi86
AskWoody_MVP
The Surfing Pensioner
AskWoody Plus-
gborn
AskWoody_MVPFebruary 17, 2018 at 12:51 am #168020I guess, the risk for private user is minimal. But it’s probably an attack vector, that should be discussed at least.
Ex Microsoft Windows (Insider) MVP, Microsoft Answers Community Moderator, Blogger, Book author
https://www.borncity.com/win/
1 user thanked author for this post.
-
MrJimPhelps
AskWoody MVPFebruary 17, 2018 at 9:20 am #168051I’m in Group L – Linux Mint!
Group "L" (Linux Mint)
with Windows 10 running in a remote session on my file server2 users thanked author for this post.
-
Jan K.
AskWoody Lounger
-
anonymous
Guestanonymous
GuestFebruary 16, 2018 at 12:35 pm #167872Where is this Mass Hysteria?
There is the expectation that a tech company would choose HTTPS for a website that is regularly accessed by their customers for downloads, especially MSIs. It has taken many people by surprise that Microsoft has chosen not to. You may recall that it was just a year ago that they had to remove Active X from this site.
in 2018, Google and Firefox are issuing ‘insecure’ notices for sites that are not HTTPS, whereas Edge and IE do not. Considering that the vast majority of users do not use Microsoft’s browsers, the HTTP designation for the MS Catalog site is a major inconvenience for MS users. This is an immature game that results in zero winners.
-
WildBill
AskWoody PlusFebruary 16, 2018 at 5:33 pm #167962in 2018, Google and Firefox are issuing ‘insecure’ notices for sites that are not HTTPS, whereas Edge and IE do not. Considering that the vast majority of users do not use Microsoft’s browsers, the HTTP designation for the MS Catalog site is a major inconvenience for MS users. This is an immature game that results in zero winners.
I’m using Firefox & haven’t gotten any ‘insecure’ notices for http sites… Yet. Maybe Firefox will start about the same time Chrome does later this year. Some people may call this clickbait & promoting hysteria, but Woody & others are right; a popular http patch could be hacked & Who Would Know? Methinks Google will be doing this to troll Microsoft; still, not best practices at work in Redmond, IMO.
Bought a refurbished Windows 10 64-bit, currently updated to 22H2. Have broke the AC adapter cord going to the 8.1 machine, but before that, coaxed it into charging. Need to buy new adapter if wish to continue using it.
Wild Bill Rides Again...
geekdom
AskWoody_MVPFebruary 16, 2018 at 12:54 pm #167885Isn’t that an oxymoron?
On permanent hiatus {with backup and coffee}
offline▸ Win10Pro 2004.19041.572 x64 i3-3220 RAM8GB HDD Firefox83.0b3 WindowsDefender
offline▸ Acer TravelMate P215-52 RAM8GB Win11Pro 22H2.22621.1265 x64 i5-10210U SSD Firefox106.0 MicrosoftDefender
online▸ Win11Pro 22H2.22621.1992 x64 i5-9400 RAM16GB HDD Firefox116.0b3 MicrosoftDefenderMrBrian
AskWoody_MVPFebruary 16, 2018 at 1:00 pm #167888If anyone is curious if using Windows Update itself is secure, here are some links:
Are Windows Updates susceptible to tampering, eg. using a MiTM attack
There have been Windows updates that address the security of using Windows Update:
Researchers reveal how Flame fakes Windows Update
Unauthorized digital certificates could allow spoofing
-
MrBrian
AskWoody_MVPFebruary 20, 2018 at 12:05 am #168746In response to the Flame malware, Microsoft also did this: From Update to Windows Update, WSUS Coming This Week (2012): “Our hardening introduces two defense-in-depth changes. First, we have further hardened the Windows Update infrastructure so that the Windows Update client will only trust files signed by a new certificate that is used solely to protect updates to the Windows Update client. Second, we are strengthening the communication channel used by Windows Update in a similar way.”
MrBrian
AskWoody_MVPAJNorth
AskWoody Plusanonymous
GuestFebruary 16, 2018 at 3:34 pm #167935-
anonymous
GuestFebruary 16, 2018 at 4:09 pm #167943Agreed, and also with the click bait comment above.
Since all Microsoft updates are signed, they are tamper-proof and thus secure regardless of whether the transport is secure. What additional benefit would using HTTPS offer? Absolutely nothing, it would just waste CPU performance.
WSUS also requires both HTTP and HTTPS ports, this is well documented:
“WSUS also uses SSL to encrypt metadata passed between clients and downstream WSUS servers. Note that WSUS only uses SSL for metadata. This is also the way Microsoft Update distributes updates.
As discussed earlier in this guide, updates consist of two parts: metadata that describes what an update is useful for, and the files to install the update on a computer. Microsoft mitigates the risk of sending update files over an unencrypted channel by signing each update. In addition to signing each update, a hash is computed and sent with the metadata for each update. When an update is downloaded, WSUS checks the digital signature and hash. If the update has been tampered with, it is not installed.”Edit to remove HTML
Please convert to plain text (.txt) before cut/paste -
MrBrian
AskWoody_MVPFebruary 16, 2018 at 6:07 pm #167965From New Paper Released: WSUSpect – Compromising the Windows Enterprise via Windows Update (2015):
“Today, we released a paper titled ‘WSUSpect – Compromising the Windows Enterprise via Windows Update’ which accompanies the talk presented by two of our senior researchers at Black Hat USA 2015.
The presentation demonstrates how Windows Update can be abused for internal attacks on corporate networks by exploiting insecurely configured enterprise implementations of Windows Server Update Services (WSUS).”
-
OscarCP
MemberFebruary 16, 2018 at 8:37 pm #167978That is on Enterprise; would this proof of vulnerability have, as a corollary, that it is also true, across the board, for all extant versions of Windows X (with X= 7, or 8, or 8.1, or 10)?
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV -
MrBrian
AskWoody_MVPFebruary 17, 2018 at 12:59 pm #168114That is on Enterprise; would this proof of vulnerability have, as a corollary, that it is also true, across the board, for all extant versions of Windows X (with X= 7, or 8, or 8.1, or 10)?
I’m not sure, but here is another related work: WSUSpendu. English version of this paper (pdf): https://www.blackhat.com/docs/us-17/wednesday/us-17-Coltel-WSUSpendu-Use-WSUS-To-Hang-Its-Clients-wp.pdf.
-
-
-
-
gborn
AskWoody_MVPFebruary 17, 2018 at 12:23 am #168013Since all Microsoft updates are signed, they are tamper-proof and thus secure regardless of whether the transport is secure.
That was my first thought. But did you read my addendum here?
Tested: Windows accepts altered updates …
Within my German blog post, a reader did a simple test. He downloaded an update package via Microsoft Update Catalog. Then he used Notepad++ to edit some strings within the update package. The saved package is flagged ‘as modified’ on digital signature property page. But Windows accept this update and install it.
I guess (haven’t tested it), the digitale signatur proof check will be executed for .cabs included. The post from Mr. Brian below indicates, that some parts are checked and others not.
So: Overall I guess, it’s a ‘non optimal’ solution, Microsoft decides to use (nicely spoken). Well, we can discuss about http versus https. But then explain, why they offer kb articles via https, while downloads from http download links are redirected to https pages – and Update Catalog downloads still shipped via http.
Ex Microsoft Windows (Insider) MVP, Microsoft Answers Community Moderator, Blogger, Book author
https://www.borncity.com/win/
3 users thanked author for this post.
-
Noel Carboni
AskWoody_MVPFebruary 17, 2018 at 3:26 am #168024Why?
A reason might be that it takes computer power to encrypt large blocks of data. That translates to money when running a network that’s tasked with delivering an unprecedented amount of data. Let’s not forget, with concepts like “cumulative” and “6 month major release cycles” dawning, updates are working out to hundreds of megabytes to gigabytes apiece. We’re all becoming numb to mega/giga/tera but it’s an unprecedented large network and server load – by a lot.
Many folks have more computer power than they need, and they might prefer an https: connection vs. http: on general principles but it comes at a price, however intangible.
And lo and behold right when content delivery networks could use more capacity, now servers are becoming less efficient than ever, with their mitigations for newly “discovered” vulnerabilities going in.
Why invite / create problems on purpose? It’s not hard to imagine there are those who benefit from people throwing money at their problems.
But even if it’s not planned, insecure computing and networking are where we came from. The only thing people thought https: was good for just a few scant years ago was specific important transactions. Who worried about such things as “Man In The Middle” attacks when it seemed ridiculously expensive/difficult to do, and backups were smaller and easier to restore? Now the data we use to manage our lives is becoming huge, and more valuable than ever – and the bad guys share their software via the same web…
-Noel
1 user thanked author for this post.
-
MrBrian
AskWoody_MVPFebruary 16, 2018 at 6:04 pm #167963SkipH
AskWoody PlusFebruary 16, 2018 at 5:09 pm #167955Just did a Google search for “Microsoft Update Catalog” using Chrome.
Clicked on the 1st site found, “Microsoft Update Catalog” (https://catalog.update.microsoft.com), get the following ‘web page’:
I made a shortcut a long time ago to the MS Update Catalog site using:
https://www.catalog.update.microsoft.com/home.aspx
and it works fine, brings up the non-ActiveX web site in IE 11 or Chrome. (more on that in a following post)
3 users thanked author for this post.
SkipH
AskWoody PlusFebruary 16, 2018 at 5:26 pm #167959@”anonymous’ in post # 167872:
Then did a Google search for “Microsoft update catalog” in IE 11 (brings up the same results as in Chrome).
Click on the 1st result “Microsoft Update Catalog” and get the following web site:
The URL of the above web page is:
https://catalog.update.microsoft.com/v7/site/Install.aspx
So, there’s multiple ways to kind of get to the MS Update Catalog site, and at least one of them still wants to install ActiveX in IE 11. Seems ActiveX is still alive on the above web page. I’ve never installed it, so use the ‘other’ way to get to the Update catalog site.
Very confusing.
anonymous
GuestFebruary 16, 2018 at 7:25 pm #167971anonymous
GuestFebruary 16, 2018 at 11:14 pm #1679971) Microsoft Update Catalog: https://www.catalog.update.microsoft.com
All file download links at the above are served via HTTP, ever since the catalog was launched. If we manually switch the download link from HTTP to HTTPS, the download will fail. The browser would warn about an untrusted connection, with details such as “download.windowsupdate.com uses an invalid security certificate“.
2) Microsoft Download Center: https://download.windowsupdate.com
From what I noticed, numerous file download links posted since years ago at the above are randomly served via HTTP. That is, some download links are in HTTPS, but some are in HTTP. But we can manually switch the download link from HTTP to HTTPS, & still fetch the file.
As such, if Microsoft has any intention of making its file downloads more secure for users, it needs to not only fix portal (1), but also the random HTTP download links at portal (2).
1 user thanked author for this post.
anonymous
GuestFebruary 17, 2018 at 4:28 am #168022In the Computerworld article, it says: “Now flip over to the KB 4087256 article” but the link is https://support.microsoft.com/en-us/help/4074588
I guess that KB 4087256 is renamed to KB 4074588?
-
woody
Manager
abbodi86
AskWoody_MVPFebruary 17, 2018 at 7:31 am #168041This sudden hysteria would more understandable if it was directed towards Windows Update, which have been and still and will continue to deliver all updates via HTTP
the MU catalog links are just a mirror of WU linksthe sha1 hash appended to each file name will prevent any tampering
https://www.askwoody.com/forums/topic/ms-defcon-4-time-to-get-november-windows-and-office-patches-applied/#post-22192even the new Windows 10 UUP and Delivery Optimization links are HTTP
with all due respect, HTTPS is overrated in this context
BTW, i pointed that long time ago, although not very clear 😀
https://www.askwoody.com/forums/topic/ms-defcon-4-time-to-get-november-windows-and-office-patches-applied/#post-22239gborn
AskWoody_MVPFebruary 17, 2018 at 9:27 am #168054Microsoft Update Catalog is not broken catalog.update.microsoft.com is the IE-activex front-end http://www.catalog.update.microsoft.com is the non-activex front-end (for IE and other browsers)
That’s what also some German users told me, but …
I mentioned it within my German comment – just try the two tests below.
http://www.catalog.update.microsoft.com
catalog.update.microsoft.comThe last link shows ‘Server negotiated HTTP/2 with blacklisted suite’ (btw also for IE 11 and Edge under Windows 10). I would say, it’s some misconfigured servers, probably.
Ex Microsoft Windows (Insider) MVP, Microsoft Answers Community Moderator, Blogger, Book author
https://www.borncity.com/win/
woody
ManagerFebruary 17, 2018 at 12:05 pm #168101I received this email from Stefan Kanthak (whom I hope will join us here), slightly edited:
My point is NOT with Windows Update/Automatic Update, but with a MitM attacker who serves bogus updates. Yes, WU/AU will reject the altered updates. But an administrator who notices the WU/AU failure might be tempted to fetch the failed updates manually … and fall prey to a bogus one.
An especially trivial example is the Security Update for CAPICOM (KB931906) The EXE file is a properly signed but vulnerable executable (there are of course quite some more of this kind), which may be served by a MitM attacked instead of the requested update.Executables are not fed to WUSA.exe, DISM.exe, CBS or the Windows Microsoft Installer which will check their signature and deny to process bogus updates. A double-click on this .EXE will come up with an UAC prompt which
says “I’m from Microsoft”. To go from there, look at my FD and BugTraq posts about IExpress or 931906 or CAPICOM on how to proceed.Yes, this is an INDIRECT exploit; but it’s an exploit. And then there are updates which are NOT distributed through WU/AU, but only via Microsoft Update Catalog, for example KB3127754.
-
woody
ManagerFebruary 17, 2018 at 12:13 pm #168103I don’t claim to be an expert at Windows Update internals, but here’s my concerned-layman’s take:
Both the “HTTPS should be there” and the “HTTP is good enough” factions have points in their favor. There doesn’t appear to be a direct attack vector the way things stand, but the potential is there for an unfortunate admin (or user) to shoot themselves in the foot.
I think MS should be moving to use HTTPS links exclusively for all of their security patches, even if there’s a performance hit. Not because there’s a known threat. But because the threat’s potentially very large — and the rewards potentially huge.
2 users thanked author for this post.
-
anonymous
GuestFebruary 17, 2018 at 12:46 pm #168109Raymond Chen discusses this category of ‘security hole’ frequently on his blog.
It goes “it rather consists of being on the other side of this airtight hatchway,” which is his way of saying that if your admin(or user) is such a clueless chap that he downloads and installs malware, THAT is your problem. You can not claim a security defect when everything is working exactly as designed.
The default arrangement is that the downloaded executable is going to require UAC approval, and when it does, it will indicate the program is signed by XYZ or not signed. If it doesn’t say Microsoft, you don’t run it! Any steps beyond that are social engineering, and are not fixable by the software. Microsoft issues these certificates, so they are presumably on the lookout for any attempts to fool people, and they can revoke certificates also.
-
anonymous
GuestFebruary 18, 2018 at 3:27 pm #168513Anon #168109 said:
The default arrangement is that the downloaded executable is going to require UAC approval, and when it does, it will indicate the program is signed by XYZ or not signed. If it doesn’t say Microsoft, you don’t run it!The above strategy is not foolproof. Even if the program is signed with a genuine Microsoft signature, it doesn’t necessarily imply that it is safe to run. Genuine software vendor digital signatures can be created from stolen private keys, such as in the following example.
https://www.symantec.com/connect/blogs/stux-be-you
21 Sep 2010
Back in July we saw the Stuxnet worm targeting industrial control systems. The Stuxnet authors stole the digital signatures of two Taiwanese chip makers and used them on the rootkit employed by the worm. Just how they were getting their hands on the private keys needed to steal the signatures remains a missing piece of the Stuxnet puzzle.In order to digitally sign a binary, you must have a private key. If attackers can gain possession of the key they can steal the key owner’s signature; therefore, the owner of the private key should ensure that it remains private. Somehow, these private keys were stolen and used by the Stuxnet authors to sign the rootkit in order to ensure that it would be loaded by Windows Vista and Windows 7.
Obtaining a private key for a digital certificate may not be as difficult as one imagines. Infostealer.Nimkey is an example of a threat that steals PKCS#12 public key certificate files. PKCS#12 certificates are different from ordinary public key certificates—they can contain not only public keys but private keys, too.
And there are precedences for forged Microsoft certificates, such as the following incident:
Unauthentic “Microsoft Corporation” Certificates (22 Mar 2001)
https://www.cert.org/historical/advisories/CA-2001-04.cfmOn January 29 and 30, 2001, VeriSign, Inc. issued 2 certificates to an individual fraudulently claiming to be an employee of Microsoft Corporation. Any code signed by these certificates will appear to be legitimately signed by Microsoft when, in fact, it is not.
Although users who try to run code signed with these certificates will generally be presented with a warning dialog, there will not be any obvious reason to believe that the certificate is not authentic.
This issue presents a security risk because even a reasonably cautious user could be deceived into trusting the bogus certificates, since they appear to be from Microsoft. Once accepted, these certificates may allow an attacker to execute malicious code on the user’s system.
Competent blackhats can probably create their own certificate & label it “Microsoft” to deceive users who don’t go to the trouble of checking the certificate’s signature against the known Microsoft signature. And many (if not most) end-users do not have the habit, patience or know-how to conduct proper signature checks by cross-checking serial numbers & validity dates for every executable file.
1 user thanked author for this post.
-
-
ch100
AskWoody_MVPFebruary 17, 2018 at 1:21 pm #168117Woody, this in theory is accurate and well-known for many years.
But let’s take a more practical view here and also see Noel’s post for this.
A significant number of patches are released due to public hysteria in relation to this sort of vulnerabilities which have little practical relevance. For a limited number of organisations they are relevant though. 🙂
A man in the middle attack inside of an organisation require an attacker with elevated access inside of the organisation. As per the post, in this specific situation, it also require an unsuspecting administrator who would install cracked software manually bypassing the safeguards built into the software.
How secure is that organisation’s internal network in such a situation? Are there bigger problems there than the possibility of installing cracked updates?MrBrian
AskWoody_MVPFebruary 20, 2018 at 9:51 am #168892“Executables are not fed to WUSA.exe, DISM.exe, CBS or the Windows Microsoft Installer which will check their signature and deny to process bogus updates.”
If the type of file downloaded from the Catalog is a .exe file, I believe that it’s safer to install the update via Windows Update (if available) than to download and install it manually, due to the additional Windows Update infrastructure changes that Microsoft introduced in 2012. Feedback on my assertion is welcome :).
MrBrian
AskWoody_MVPFebruary 17, 2018 at 1:09 pm #168116This is related info that might be worth its own topic: From OEM Updaters put PCs at risk (2016): “A study by Duo Security, Inc suggests that OEM Updaters, programs designed by PC manufacturers to update vendor-specific software, do more harm than good as they put PCs at risk.”
-
Noel Carboni
AskWoody_MVPFebruary 17, 2018 at 2:59 pm #168135Manufacturers have struggled for a long time to find good that could be delivered from “the cloud”.
Hard looks at all cloud or network-contacting services are warranted.
Sure, with the cloud “sharing” is easy, getting a weather report is seamless, getting more software than you can possibly want is a given – yet amazingly along with that comes the increased probability of “being violated”.
It long been said that if you use Windows long enough, it will slow down more and more over time until it becomes unusable. That’s not an inherent issue with Windows or its registry or whatever. It’s because almost every software package almost invariably tries to install some extra helpful services or scheduled jobs – and I’m not even talking about big stuff like Adobe’s Creative Cloud which practically takes over your entire system with dozens of components. Run of the mill programs often want to install their services that will watch for updates, for example. Eliminate all that and lo and behold Windows can actually be run forever and maintain efficiency. I’ve done it.
I just looked at the first page of my Autoruns display, “Everything” tab, and much more stuff is unchecked than is checked (not to mention the amount of unchecked boxes in the Scheduled Tasks section).
-Noel
Fred
AskWoody LoungerKirsty
ManagerFebruary 17, 2018 at 9:29 pm #168422An interesting page on MSI malware has just been published on isc.scan.edu:
Malware Delivered via Windows Installer Files
Published: 2018-02-17
Last Updated: 2018-02-17 09:06:35 UTC
by Xavier Mertens (Version: 1)For some days, I collected a few samples of malicious MSI files. MSI files are Windows installer files that users can execute to install software on a Microsoft Windows system. Of course, you can replace “software” with “malware”. MSI files look less suspicious and they could bypass simple filters based on file extensions like “(com|exe|dll|js|vbs|…)”. They also look less dangerous because they are Composite Document Files…
Read the full article here
4 users thanked author for this post.
woody
ManagerFebruary 21, 2018 at 9:18 am #169233Microsoft engineer extraordinaire Michael Niehaus sent me this synopsis privately. It’s reprinted here with permission:
The updates are Authenticode-signed and validated by the OS, so a man-in-the-middle attack is impossible – any tampering done to the payload will be detected by the OS, causing the entire payload to be rejected.
That’s kind of like saying “Kerberos is insecure because it doesn’t use HTTPS” – nope, it signed the payload and validated the signature…
So you’re making a big fuss over nothing.
So I asked him about the attack vector raised by Kanthak, earlier in this thread. His response:
All Windows updates are Authenticode-signed; they can’t be tampered with. WU/WUSA/DISM will reject them. Even if you manually download them, they are still signed and can’t be tampered with.
As for executables, they are also Authenticode-signed. Windows will tell you that they are untrusted at worst, and in many cases reject them due to an invalid signature, although if you try hard enough you can probably bypass all the warnings. But these aren’t Windows updates.
There are many easier ways than a MitM attack to get people to download bad things ?
He certainly has a point!
4 users thanked author for this post.
-
MrBrian
AskWoody_MVPFebruary 21, 2018 at 11:51 am #169251“But these aren’t Windows updates”
Some updates in the Catalog are available as executables.
2 users thanked author for this post.
-
anonymous
GuestApril 2, 2022 at 10:55 pm #2436315From Ghacks :
Microsoft Update Catalog downloads are now using HTTPS
——————————————————-
https://www.ghacks.net/2022/04/02/microsoft-update-catalog-downloads-are-now-using-https/The https link provided in the article works : https://www.catalog.update.microsoft.com/Home.aspx.
Cheers.
1 user thanked author for this post.
EP
AskWoody_MVPApril 2, 2022 at 2:52 pm #2436206sorry for commenting on this 4 years late but it looks like Microsoft has recently “resolved” this problem as any actual downloads posted on MS Catalog are now found on https://catalog.s.download.windowsupdate.com instead of just http://download.windowsupdate.com
don’t ask why MS took so long in putting their MS Update Catalog downloads on their HTTPS site in 2022 but better late than never
3 users thanked author for this post.
-
Bob99
AskWoody MVPApril 2, 2022 at 6:41 pm #2436272OK, but I just got a cert warning from Firefox 98.0.2 about the site fe2.update.microsoft.com that the link catalog.s.download.windowsupdate.com redirects to.
Here’s the text:
…Firefox does not trust fe2.update.microsoft.com because its certificate issuer is unknown, the certificate is self-signed, or the server is not sending the correct intermediate certificates.
Error code: SEC_ERROR_UNKNOWN_ISSUER
I’m guessing that, for now, FF doesn’t trust the root cert because of it being “self-signed”.
Would be great if one of the MVPs here or someone with good knowledge of the inner working of certs could take a dive into the cert chain to see just why FF might not like it. That way the rest of us can decide if the cert is worth permanently accepting.
Meanwhile, I’m off to ssllabs to see what they think of the site redirection and its cert.
…And, I’m back. Didn’t take too long. SSLLabs was fine with the cert belonging to the site in the actual link mentioned by @EP above, but they didn’t like the cert from the site that the link forwards to, fe2.update,microsoft.com.
According to their tests, fe2.update.microsoft.com’s cert isn’t trusted by the Mozilla, Apple, Android, nor Java trust stores, but is trusted by Windows and is in the Windows trust store.
So, where do we go from here? Add an exception to allow FF (and, perhaps, other browsers) to trust the site anyway until the cert makes it into the other trust stores?
Yet another edit: I just tried the site in Edge 100.0.1185.29, and IT didn’t like the site’s certificate either. Gave what it called a Privacy error with a white exclamation point inside a red triangle. Here’s the exact wording:
The server presented a certificate that wasn’t publicly disclosed using the Certificate Transparency policy. This is required for some certificates to make sure they are trustworthy and to protect against attackers.
The warning also had a little reason in all caps but in small type saying “NET::ERR_CERTIFICATE_TRANSPARENCY_REQUIRED”. So, even though the certificate is in the Windows trusted cert store, MS’s own browser, Edge, doesn’t like it. All I gotta say about that is WOW.
In all fairness, on the error page there was a way to continue to the site, but is was a blue clickable link in a VERY small font. The link said “Continue to fe2.update.microsoft.com (unsafe)”.
-
This reply was modified 3 years, 1 month ago by
Bob99. Reason: added cert testing results
-
This reply was modified 3 years, 1 month ago by
Bob99. Reason: added info about attempting to access the site with Edge
-
This reply was modified 3 years, 1 month ago by
Bob99.
1 user thanked author for this post.
-
This reply was modified 3 years, 1 month ago by
-
abbodi86
AskWoody_MVP -
Bob99
AskWoody MVPApril 2, 2022 at 7:16 pm #2436279you need to find a way to import it manually to firfox
From what I recall, this can easily be done by first clicking the grey colored button labeled “Advanced” that’s in the warning page, and then clicking the grey colored button labeled “Accept the Risk and Continue”. I haven’t done that in a very long time, but that’s what used to work to get FF to import and accept what it thought of as a questionable certificate from a web site.
Probably similar procedure(s) for Chrome, Brave, Safari and others.
-
-
Viewing 24 reply threads - This topic has 59 replies, 24 voices, and was last updated 3 years, 1 month ago by
-

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Downloads folder location
by
CWBillow
5 hours, 27 minutes ago -
Remove a User from Login screen
by
CWBillow
7 hours, 59 minutes ago -
TikTok fined €530 million for sending European user data to China
by
Nibbled To Death By Ducks
9 hours, 8 minutes ago -
Microsoft Speech Recognition Service Error Code 1002
by
stanhutchings
15 hours, 13 minutes ago -
Is it a bug or is it expected?
by
Susan Bradley
1 hour, 13 minutes ago -
Image for Windows TBwinRE image not enough space on target location
by
bobolink
11 hours, 46 minutes ago -
Start menu jump lists for some apps might not work as expected on Windows 10
by
Susan Bradley
19 hours, 46 minutes ago -
Malicious Go Modules disk-wiping malware
by
Alex5723
9 hours, 22 minutes ago -
Multiple Partitions?
by
CWBillow
10 hours, 2 minutes ago -
World Passkey Day 2025
by
Alex5723
1 day, 3 hours ago -
Add serial device in Windows 11
by
Theodore Dawson
1 day, 18 hours ago -
Windows 11 users reportedly losing data due forced BitLocker encryption
by
Alex5723
2 hours, 3 minutes ago -
Cached credentials is not a new bug
by
Susan Bradley
1 day, 23 hours ago -
Win11 24H4 Slow!
by
Bob Bible
1 day, 23 hours ago -
Microsoft hiking XBox prices starting today due to Trump’s tariffs
by
Alex5723
1 day, 20 hours ago -
Asus adds “movement sensor” to their Graphics cards
by
n0ads
2 days, 1 hour ago -
‘Minority Report’ coming to NYC
by
Alex5723
1 day, 21 hours ago -
Apple notifies new victims of spyware attacks across the world
by
Alex5723
2 days, 10 hours ago -
Tracking content block list GONE in Firefox 138
by
Bob99
2 days, 9 hours ago -
How do I migrate Password Managers
by
Rush2112
1 day, 17 hours ago -
Orb : how fast is my Internet connection
by
Alex5723
1 day, 19 hours ago -
Solid color background slows Windows 7 login
by
Alex5723
2 days, 21 hours ago -
Windows 11, version 24H2 might not download via Windows Server Updates Services
by
Alex5723
2 days, 20 hours ago -
Security fixes for Firefox
by
Susan Bradley
1 day, 20 hours ago -
Notice on termination of services of LG Mobile Phone Software Updates
by
Alex5723
3 days, 8 hours ago -
Update your Apple Devices Wormable Zero-Click Remote Code Execution in AirPlay..
by
Alex5723
3 days, 17 hours ago -
Amazon denies it had plans to be clear about consumer tariff costs
by
Alex5723
3 days, 8 hours ago -
Return of the brain dead FF sidebar
by
EricB
2 days, 19 hours ago -
Windows Settings Managed by your Organization
by
WSDavidO61
1 day, 22 hours ago -
Securing Laptop for Trustee Administrattor
by
PeachesP
1 day ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.