Lots of activity this month in the wonderful world of wacky Windows patches. Post coming in Computerworld.
[See the full post at: Microsoft Patch Alert: Lots of bugs introduced, most fixed, but Win7 is still tied up in NIC knots, and Microsoft hasn’t increased the pay for its 1803 beta testers]

|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
-
Microsoft Patch Alert: Lots of bugs introduced, most fixed, but Win7 is still tied up in NIC knots, and Microsoft hasn’t increased the pay for its 1803 beta testers
Home » Forums » Newsletter and Homepage topics » Microsoft Patch Alert: Lots of bugs introduced, most fixed, but Win7 is still tied up in NIC knots, and Microsoft hasn’t increased the pay for its 1803 beta testers
- This topic has 47 replies, 22 voices, and was last updated 6 years, 10 months ago.
AuthorTopicwoody
ManagerMay 29, 2018 at 10:28 pm #195097Viewing 17 reply threadsAuthorRepliesMrToad28
AskWoody LoungerMay 30, 2018 at 10:32 am #195163I rolled back to Dec 2017 on most used win 7 PC’s and will skip May patches…maybe June will bring stability…or perhaps July. Bad patches are far greater risk to PC health than hacking threats for those that employ multi-layer anti-malware and practice safe computing. These patches are trojan horses.
-
anonymous
GuestMay 31, 2018 at 11:11 am #195379I’ve given up on Windows 7 (and so has Microsoft).
It’s hard to stay on a platform that has very obviously been abandoned and sabotaged by the developer. As amraybt commented, the bigger issue is system instability and general bugs, courtesy of Microsoft, rather than malware. Yes, the risk of infection increases over time on unpatched systems. For now, I’m using Malwarebytes to reduce the risk of the latter, and skipping patches released after December 2017 to mitigate the former.
If nothing changes over the next few months, I’ll use the Win7 boxes offline and migrate to other patched systems instead.
I used to give Microsoft the benefit of the doubt, but now I absolutely believe this is intentional based on the amount of time these things have festered. Microsoft knows that Windows 7 is the biggest threat to Windows 10 adoption.
2 users thanked author for this post.
-
Charlie
AskWoody PlusMay 31, 2018 at 1:07 pm #195393In that case it would be good for you to get familiar with Linux or Mac. Linux has easy to use versions like Mint which you could use for web surfing and email. Keep your Win 7 for playing great games and other things. I’ve tried Linux Mint and I like it. It’s not as flashy as Win 7, but it gets the job done without all the headaches MS gives us.
Being 20 something in the 70's was far more fun than being 70 something in the insane 20's4 users thanked author for this post.
-
EP
AskWoody_MVPMay 30, 2018 at 11:09 am #195170well woody it looks like the windows update “supersedence” chain is partially broken again for Win7.
Doing recent scans of Windows Update on most of my Windows 7 computers seem to offer past IE11 security updates like KB3185319 and KB3175443, even though I already have the KB4103718 update installed. if I hide KB3185319, then the next WU scan will offer me KB3175443 instead.
anonymous
Guest-
PKCano
Manager -
anonymous
Guest
-
b
AskWoody_MVPMay 30, 2018 at 12:40 pm #195193which finally made 1803 installable on most common PCs.
Installable, mind you. Not stable. For example, there are many reports of 1803 driving batteries nuts.Seven out of 350,000,000 is many?
-
MrJimPhelps
AskWoody MVP -
b
AskWoody_MVP -
MrJimPhelps
AskWoody MVP -
anonymous
GuestJune 3, 2018 at 10:00 am #195720b wrote:
given the 350 million computers now running version 1803
Not sure that’s true. Seems pretty unlikely. And I’m not the only one with doubts…
https://www.zdnet.com/article/has-microsoft-accelerated-its-latest-windows-10-rollout-not-so-fast/
-
-
WildBill
AskWoody PlusMay 30, 2018 at 12:46 pm #195195Windows 8.1 / Server 2012 R2 continues to look good. By any objective measure, 8.1 is Microsoft’s most stable version of Windows. By a long shot.
Geez, boss, don’t jinx us! It’s just a matter of time before Redmond remembers people still use 8.1/Server 2012 R2…
Bought a refurbished Windows 10 64-bit, currently updated to 22H2. Have broke the AC adapter cord going to the 8.1 machine, but before that, coaxed it into charging. Need to buy new adapter if wish to continue using it.
Wild Bill Rides Again...4 users thanked author for this post.
-
Cascadian
AskWoody LoungerMay 30, 2018 at 7:49 pm #195271My first thought on reading that line was on the selective nature of ‘bugs’ involved. Since Microsoft is a responsible corporation that keeps a tight lip concerning its flaws, we resort to Occam and his friends to deduce likely causes.
Win10’s relative ‘youth’ and hypercycling redesign are easy first explanations for a bugcount. Not a complete explanation, because it is so much more complex with a realignment of business goals and all that, but enough to wave away initial concerns.
Win7 is just ancient, out of date, so pervasive that is makes an easy target. Think barn door in terms of vulnerability. Again, not a fair assessment, but it is variations on this theme that get the endless criticism.
One common description of Win8 is as a dual purpose bridge from Win7 to the wonderful world of touchscreens and associated GUI full of tiles. Another oversimplification. But I cannot find a reasonable explanation for this platform’s immunity to Microsoft’s ‘bugs’.
You jest, and I enjoy it. But it really does reflect the feeling that once Win7’s eulogy is read and the last shovel tamps done the dirt, Win8.1 will begin to receive the full Microsoft attention it deserves. Not a friendly feeling.
1 user thanked author for this post.
Bill C.
AskWoody PlusMay 30, 2018 at 12:47 pm #195197OK, let me be the one to ask the question:
If all the previous Group B monthly security only patches installed and worked OK with the NIC issue, are the odds in favor of the May Security Only KB4103712 also working vis-a-vis the NIC issue?
Not that I am jumping now at DefCon 2, but I was just throwing it out. I do understand that any number of issues could happen, but if the NIC issue spans multiple months and updates and they went OK, I am hoping…
-
pmcjr6142
AskWoody PlusMay 30, 2018 at 1:26 pm #195207Bill C….makes sense to me. I don’t believe MS has crashed the world’s Win 7 PCs with these patches. We would have heard about that. While it’s still a crap shoot, I believe the odds are in the favor of those that update. I’ll still give Woody until early next week to see what he thinks is wise, ie. forget May updates or go ahead. I don’t think much new info is going to come out in the next week.
iPhone 13, 2019 iMac(SSD)
-
anonymous
GuestMay 30, 2018 at 2:49 pm #195225I am group B, security only. kb4103712 caused my usb ‘wired’ HP 1210 printer to not be recognized. I have Win7 home premium 64bit AMD athlonII SP1. No ‘spectre’ updates. I uninstalled said security update ONLY, and printer is online again.
-
Bill C.
AskWoody Plus -
Geo
AskWoody PlusMay 31, 2018 at 10:15 am #195378I have the same printer and problem. I go in to see what’s printing and it’s been checked to print offline even though I did’t check it. I uncheck it and cancel print then redo the print anew. Other times I unplug the USB plug in and reinsert it. Finally after all the monkeying around after the updates I reinstalled the printer and it’s been working ever since.
1 user thanked author for this post.
-
Charlie
AskWoody PlusMay 30, 2018 at 12:54 pm #195202Twelve days left until the June Black Tuesday. It certainly seems like MS doesn’t give a …… about fixing the NIC problem. Mine is built into my ASUS motherboard. Is a list of affected NI Cards available?
Being 20 something in the 70's was far more fun than being 70 something in the insane 20's-
PKCano
Manager
anonymous
GuestMay 30, 2018 at 2:03 pm #195212Master patch list says no issues tracked for KB4103727, but the article on ComputerWorld says there were install and bluescreen issues. I haven’t been able to sync KB4103714 into SCCM either. Has 4103727 really been marked superceded yet? Trying to determine which patch we should/shouldn’t apply!
As always, thanks for the amazing site!
OscarCP
MemberMay 30, 2018 at 4:09 pm #195236As I have already explained somewhere and quite recently, giving full details as how I did it, here in Woody’s ( #194767 ), as of three days ago, I have patched my Win 7, Pro, Sp1, x64, “sandy bridge” 7-years old PC quite fully, Group-B style, through May. And have had no problems whatsoever (at least that I’ve noticed). Also many others have reported here the very same thing. Maybe one or two poor souls have reported problems, but when explaining what they did, it turned out in at least one case (of those who bother to explain) that they did something wrong.
Furthermore, if memory servers, the Patch Lady has already explained in a thread she started here some days ago that the connectivity issues apparently affects only a few types of networking card, and explained how to check to see if one has a problematic one. Another connectivity issue she also has posted about is about a different problem, having to do with servers, that (if, again, memory serves and I have understood her correctly) there could be a connectivity problem after patching Win 7 with either the rollup or the security only updates when one is trying to log in remotely to a server, for example when checking on one’s email (at the ISP’ or some other email site server) which involves an usually implicit, automated login the user does not see after having set up the account, or to some place where one logs in explicitly, as is the case here at Woody’s.
According to her, there will be a problem when either the user’s computer or the server are not both patched through May while the other one is.
So now I’m patched to the gills and I understand the situation this way, and please, correct me if I am wrong: if my networking card is one of those from the wrong side of the tracks, or those in charge of a server I am trying to log in are not patched as well, I won’t be able to connect to that or (if I have card’s trouble) any server to do whatever there. And there is nothing much I can do about it, because I have no way to fix the networking card myself or have a say on what the keepers of the server choose to about patches. Either than, maybe, complain. Or buy and install a different card (if my computer is not one of those weird laptops welded shut I’ve heard about).
Same as about taxes, same as about death. Not a nice thought, but why should one worry any more about this than about those two inevitable things? (Which I do not seriously worry about, because “Life is too short to make it miserable”, as Winston Churchill allegedly once said or wrote somewhere.)
And there you have it.
Group B, Win 7, SP1, x64, Intel I-7 “sandy bridge”
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV-
OscarCP
MemberMay 30, 2018 at 6:00 pm #195253I forgot to add, making my italicized comment a bit less fatalistic: if one patches and ends up with either connectivity issue, one can always roll back the OS to its state before the problematic patches were installed, if one had taken sensible precautions before patching (as one always should) by, at the very least, creating a restore point before patching.
So there is always something one can do, by undoing the patching, but at the price of remaining unprotected against whatever evils the patches are meant to take care of.
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV -
b
AskWoody_MVPMay 30, 2018 at 11:01 pm #195307Another connectivity issue she also has posted about is about a different problem, having to do with servers, that (if, again, memory serves and I have understood her correctly) there could be a connectivity problem after patching Win 7 with either the rollup or the security only updates when one is trying to log in remotely to a server, for example when checking on one’s email (at the ISP’ or some other email site server) which involves an usually implicit, automated login the user does not see after having set up the account, or to some place where one logs in explicitly, as is the case here at Woody’s.
It doesn’t apply to email or forums, only Remote Desktop Protocol sessions.
-
OscarCP
MemberMay 31, 2018 at 8:51 am #195368b,
If I connect via remote SSH login (as I often do) to a non-Windows server, and I am fully patched up through May, including the security only update for my Win 7, x64 machine, would I run into this kind of trouble?
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV
-
anonymous
GuestMay 30, 2018 at 6:20 pm #195251Again – I AM SKIPPING this month and waiting until the end of June/Beginning of July to install updates. This month has BEEN CRA-ZY.
2 users thanked author for this post.
Cascadian
AskWoody LoungerMay 30, 2018 at 8:37 pm #195282I have to admit, a peculiar funny bone is tickled whenever you take a deep dive into geek culture references. Stretched my memory a bit on Mentat, yes I cheated with Wikipedia. I enjoy when you sprinkle these into your articles. Adding a smile at the end does make a biter pill easier take and reduces the bad reaction. Thanks for the extra service.
James Bond 007
AskWoody LoungerMay 30, 2018 at 10:23 pm #195301Windows 8.1 / Server 2012 R2 continues to look good. By any objective measure, 8.1 is Microsoft’s most stable version of Windows. By a long shot.
For now, Woody, I completely agree. Actually, I have already converted some of the systems I have from Windows 7 to 8.1, and I am planning to do other conversions on my main systems in due course.
But we don’t know how long this stability will last. At least we do know we still have more than 4 years of patch support with Windows 8.1.
Hope for the best. Prepare for the worst.
TJ
AskWoody PlusJune 1, 2018 at 8:41 am #195510Just installed KBs 4103712 (Sec.only May) and 4103768 (IE May). Didn’t want to wait any longer.
No problemos. No NIC issues, nothing.All seems well.
LMDE is my daily driver now. Old friend Win10 keeps spinning in the background-
OscarCP
MemberJune 3, 2018 at 11:57 am #195742LeaningTowardsLinux,
Problemas, Linux, problemas. It is “los problemas”, no “los problemos”, because “the problem” translates as “el problema”, and the plural, as usual, is formed by adding an “s”. Which means Spanish is just as weird as any other language I can think of, and I can think of a few.
Nothing to do with anything in particular. Just seen this mangling of a perfectly OK word from a normally weird tongue way too often and still have not had breakfast (because it is Sunday!)
And, since we are at it: I did patch completely through May a few days ago, security only, because I am died in the wool Group B.
And: sin problemas! (So far…)
(“sin problemas”, that means “without problems.”)
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV
anonymous
GuestJune 2, 2018 at 9:13 am #195585@YP Group B and I want control on my system
I also installed KB 4103712 and KB 4103768 on 3 Win7 computers:
Netbook Win7 starter 32 bit; Dell Win7 home & pro 64 bits. It has been running with no issues for the last 3 days. I was hoping that with no connectivity issues from previous March & April updates that I was relatively safe with May updates. As always, I image my system before any Windows updates. We know Microsoft is reliable.
BTW, anybody know what computer Bill Gates uses? I’ll be willing to bet that he uses a Chromebook. As I mentioned before, I picked up a refurbish 14 in about 3 years ago for $140 with tax. No BS updates, great for surfing.
Edited for HTML. Please use text tab for copy/paste.
1 user thanked author for this post.
twbartender
AskWoody LoungerJune 2, 2018 at 10:05 am #195590Windows 7, X64, group B.
I just got finished installing all of the following May updates. All installed successfully and appear to be without issues.
Windows Malicious Software Removal Tool x64 (KB890830)
Security Update for Microsoft Excel 2010 (KB4022146) 32-Bit Edition
Security Update for Microsoft Office 2010 (KB4022137) 32-Bit Edition
Security Update for Microsoft Office 2010 (KB4011275) 32-Bit Edition
Security Update for Microsoft Office 2010 (KB2899590) 32-Bit Edition
Security Update for Microsoft Office 2010 (KB4011274) 32-Bit Edition
Security Update for Microsoft Word 2010 (KB4022141) 32-Bit Edition
Security and Quality Rollup for .NET Framework (KB4099633)
Security Update for Windows 7 (KB4103712)
Security Update for Windows IE 11 (KB4103768)4 users thanked author for this post.
TJ
AskWoody PlusJune 2, 2018 at 10:12 am #195591Well, I thought I was protected by installing May’s security updates, but another unpatched ZeroDay has been publicized (0Day) Microsoft Windows JScript Error Object Use-After-Free Remote Code Execution Vulnerability ZDI-18-534 ZDI-CAN-5613
🙁
LMDE is my daily driver now. Old friend Win10 keeps spinning in the background-
Jan K.
AskWoody Lounger
bruce.chaser
AskWoody LoungerJune 6, 2018 at 3:06 am #196312Hy all,
Can you please answer me one question.
So I have a production environment with about 150 windows 7 x64 machines.
We have a WSUS server and have not updated any machine since 12.12. 2017.My question is this.
In WSUS i have meny Security Only Quality Updates.
Do I have to install/approve those as well or are the cumulative and Monthly Quality Rollups enaugh?I we don’t need those Security Only Quality Updates i would decline them?
Please give me some insight or best practices on this.Thank in advance.
-
ch100
AskWoody_MVPJune 6, 2018 at 4:24 am #196318Strictly speaking, you have to approve only the Monthly Roll-up Updates.
After their installation and your machines reporting back to WSUS, the Security Only updates will not show as required any more, except for the rare instance when Microsoft messes up the metadata supersedence, which is normally corrected in few days, up to few weeks.
I have also seen as common practice the approval of ALL updates at the same time, Monthly Roll-ups and Security Only each month, for avoiding compliance issues I suppose. This is redundant practice, but would simplify the administrative and research work and let Microsoft CBS (the so-called servicing stack) sort everything out, which it always does correctly.
At the end of the day, it is your choice, but after 1 year and a half of working and researching those aspects, my current recommendation is to approve both categories in WSUS and not to decline or not approve any. This is safest practice and you cannot fail any compliance test if this is important to you.
You never decline non-superseded updates in WSUS.
You can see the supersedence column by enabling it, which is not default configuration, but highly useful.2 users thanked author for this post.
-
columbia2011
AskWoody Lounger -
bruce.chaser
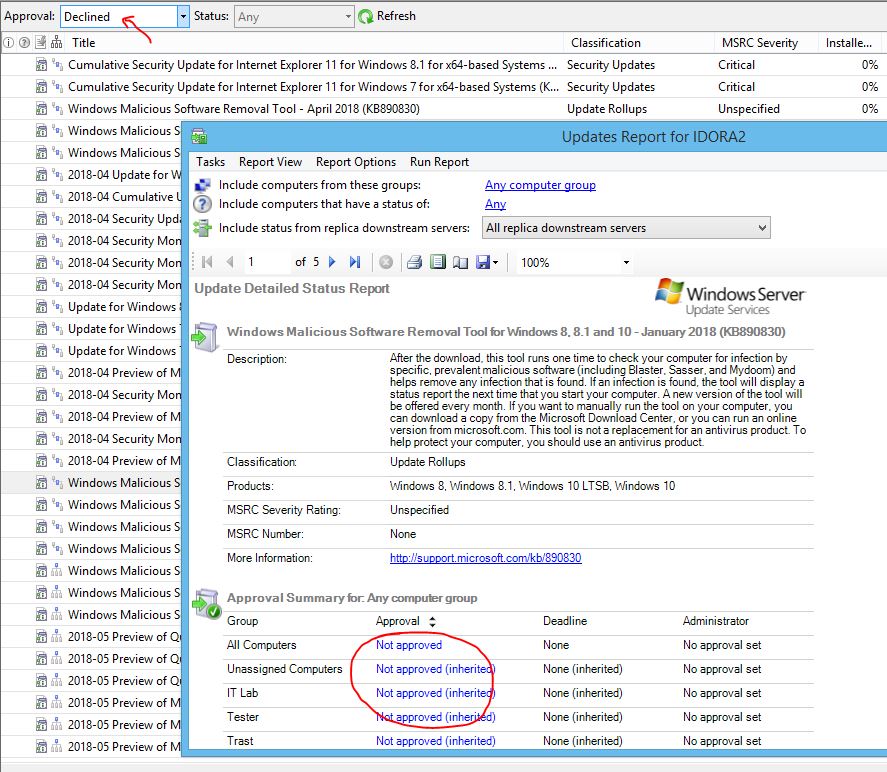
AskWoody LoungerJune 6, 2018 at 7:05 am #196332I have a question that is a little off topic but maybe someone know the answer.
I tried looking it up on google but no go.The problem is that all updated that i have declined show up as Not Approved when i open them after Declining them.
So when i set the list to show all declined updated it does show all declined updates but if I double click any of them it states Not approved.
Check the image attached.
Edit to insert attachment
1 user thanked author for this post.
-
ch100
AskWoody_MVP
-
-
-
ch100
AskWoody_MVPJune 6, 2018 at 7:42 am #196340See @bruce-chaser screenshot 4th column.
You enable various columns by right clicking on the top bar and by selecting various options.
-
bruce.chaser
AskWoody LoungerJune 6, 2018 at 7:48 am #196341One last question.
Do I approve the updates from the newest to the oldest or vice versa?
To to clear, do i approve the latest updates first, say from may 17th and then proceed to the previous months or do I start from 12.12.2017 and finish with the may 17th updates?
Thanks everyone in advance.
Really appreciate everyone’s help.-
ch100
AskWoody_MVPJune 6, 2018 at 9:03 am #196355… and one last answer…
Enable most columns which you find useful, but in this matter what counts is the Needed Count column.
Approve everything that is needed and you have reasons to approve – i.e. do not approve any Preview or if you don’t want do not approve KB2952664 (for Windows 7/2008 R2).
Do not approve any superseded update to save your space on hard-disk and some amount of time. Otherwise it is not a mistake to approve even the superseded updates which are needed. Windows CBS and the supersedence metadata will sort out what is actually needed.
In extremely rare cases you may find that 1-2 superseded updates are offered even after installing all non-superseded updates, but this is so subtle that it is the subject for another discussion. For most purposes you can ignore this issue.
Lastly, when you think you are done with all updates, go to Windows Update online with one of the machines which are updated and scan to see if you missed anything. Obviously the last one can be done and is recommended only if your company’s policies allow you to do that or if the Windows Update access is not blocked by firewalls. -
bruce.chaser
AskWoody LoungerJune 6, 2018 at 10:07 am #196358
-
Demeter
AskWoody LoungerViewing 17 reply threads -

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Android 15 require minimum 32GB of storage
by
Alex5723
2 hours, 45 minutes ago -
Mac Mini 2018, iPhone 6s 2015 Are Now Vintage
by
Alex5723
2 hours, 55 minutes ago -
Hertz says hackers stole customer credit card and driver’s license data
by
Alex5723
3 hours, 25 minutes ago -
advice for setting up a new windows computer (Awaiting moderation)
by
routtco1001
3 hours, 46 minutes ago -
Firefox became sluggish
by
Rick Corbett
20 minutes ago -
Windows 10 Build 19045.5794 (22H2) to Release Preview Channel
by
joep517
7 hours, 24 minutes ago -
Windows 11 Insider Preview Build 22635.5235 (23H2) released to BETA
by
joep517
7 hours, 53 minutes ago -
A Funny Thing Happened on the Way to the Forum
by
bbearren
3 hours, 24 minutes ago -
Download speeds only 0.3Mbps after 24H2 upgrade on WiFi and Ethernet
by
John
4 hours, 47 minutes ago -
T-Mobile 5G Wireless Internet
by
WSmmi16
9 hours, 48 minutes ago -
Clock missing above calendar in Windows 10
by
WSCape Sand
56 minutes ago -
Formula to Calculate Q1, Q2, Q3, or Q4 of the Year?
by
WSJon5
22 hours, 39 minutes ago -
The time has come for AI-generated art
by
Catherine Barrett
2 hours, 42 minutes ago -
Hackers are using two-factor authentication to infect you
by
B. Livingston
12 hours, 22 minutes ago -
23 and you
by
Max Stul Oppenheimer
19 hours, 37 minutes ago -
April’s deluge of patches
by
Susan Bradley
57 minutes ago -
Windows 11 Windows Updater question
by
Tex265
22 seconds ago -
Key, Key, my kingdom for a Key!
by
RetiredGeek
2 days, 4 hours ago -
Registry Patches for Windows 10
by
Drcard:))
2 days, 8 hours ago -
Cannot get line length to NOT wrap in Outlining in Word 365
by
CWBillow
1 day, 15 hours ago -
DDU (Display Driver Uninstaller) updates
by
Alex5723
1 day ago -
Align objects on a OneNote page
by
CWBillow
2 days, 14 hours ago -
OneNote Send To button?
by
CWBillow
2 days, 15 hours ago -
WU help needed with “Some settings are managed by your organization”
by
Peobody
2 days, 23 hours ago -
No Newsletters since 27 January
by
rog7
1 day, 4 hours ago -
Linux Mint Debian Edition 7 gets OEM support, death of Ubuntu-based Mint ?
by
Alex5723
2 days ago -
Windows Update “Areca Technology Corporation – System – 6.20.0.41”
by
Bruce
1 day, 22 hours ago -
Google One Storage Questions
by
LHiggins
1 day, 6 hours ago -
Button Missing for Automatic Apps Updates
by
pmcjr6142
1 day, 14 hours ago -
Ancient SSD thinks it’s new
by
WSila
2 days, 4 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.