There are still some well-known (even acknowledged) bugs, and the inanities performed in the name of Meltdown and Spectre continue to boggle my mind.
[See the full post at: Microsoft Patch Alert: August is much, much better than July]

|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
-
Microsoft Patch Alert: August is much, much better than July
Home » Forums » Newsletter and Homepage topics » Microsoft Patch Alert: August is much, much better than July
- This topic has 76 replies, 25 voices, and was last updated 6 years, 6 months ago.
AuthorTopicViewing 19 reply threadsAuthorReplies-
OscarCP
MemberAugust 23, 2018 at 2:33 pm #212777Thanks, Woody for this very good news.
But there is no great need to hurry up and install any updates. For my part, I’ll wait, as usual, another two weeks, in case some problems are discovered in the meantime. After that, and already three weeks after Patch Tuesday, we’ll see.
Group B, Windows 7 SP1, x64.
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV4 users thanked author for this post.
-
Demeter
AskWoody Lounger -
woody
ManagerAugust 23, 2018 at 4:24 pm #212805there is no great need to hurry up and install any updates
Well, unless you’re a member of a Chinese organization that uses IE 11 with VBScript enabled and you’re a juicy target for North Korea…..
4 users thanked author for this post.
-
OscarCP
MemberAugust 23, 2018 at 4:26 pm #212806Lucky me, then.
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV -
walker
AskWoody LoungerAugust 23, 2018 at 5:42 pm #212830@Woody: I don’t recall the last time we had a month which there was a Defcon 3, so I’m afraid to attempt to install “anything”. I only have a few pending anyway, however they go back to July and August…. Some users are installing and some aren’t apparently. Thank you for keeping us up to date on the messes we’ve been getting with the “update process”. Great work, Woody! Thank you for your wonderful website!! 🙂
1 user thanked author for this post.
-
woody
ManagerAugust 23, 2018 at 6:13 pm #212838 -
MrJimPhelps
AskWoody MVP
-
-
-
-
Klaas Vaak
AskWoody LoungerAugust 23, 2018 at 9:58 pm #212866@OscarCP: l asked Woody the question in another thread but he did not answer, so let me ask you: does the MS Defcon level at the top of this page refer to the current month only? My feeling is that it does, but I would like it confirmed.
Another question is: is it OK now to implement the July patches?
I am in group B – security only patches – on 1 computer, and in Group A – monthly roll-up – on another computer.
1x Linux Mint 19.1 | 1x Linux antiX
-
Kirsty
ManagerAugust 23, 2018 at 11:49 pm #212873Your response was within an hour of your posting.
Woody has since posted this, just below the other (non-threaded) reply to you:
That’s exactly correct.
Look for a change in MS-DEFCON level late this week – unless something weird pops up.

3 users thanked author for this post.
-
Klaas Vaak
AskWoody LoungerAugust 26, 2018 at 4:28 am #213167@Kirsty: when Woody says “that’s exactly correct” I am still unclear as to what he means. I assume it is in answer to my question what the MS-Defcon numbers at the top of this page refer to.
My felling was that they refer, or should refer, to the current month, i.e. August in this case.
But from an earlier response it is clear that they still refer to July and that we have to wait till level 3 or 4 is reached.
So I repeat my request: to have a remark next to the MS-Defcon numbers showing which month the refer to.
1x Linux Mint 19.1 | 1x Linux antiX
-
Kirsty
ManagerAugust 26, 2018 at 2:27 pm #213263@kirsty: when Woody says “that’s exactly correct” I am still unclear as to what he means.
There’s no way I’m brave enough to speak for Woody! However, the threaded conversation went:
The status is real time, not patch month related. Currently it’s 2 so if you’re unsure, don’t patch yet.
That’s exactly correct.
I read that to mean that Woody was endorsing Paul’s response.

-
Klaas Vaak
AskWoody LoungerAugust 27, 2018 at 3:08 am #213366@Kirsty: the mere fact that you and I are discussing back and forth, referring to different threads, different responses and different people, proves incontrovertibly that there is confusion about which month the Defcon shield refers to.
Now, I don’t take myself for a particularly brilliant person, but I feel confident that I am not more retarded than the average person here. So my request remains: add a flag next to the shield indicating the month in order to avoid confusion. Why is there consistent refusal to implement something simple that will avoid confusion and carries no risk?
1x Linux Mint 19.1 | 1x Linux antiX
-
woody
ManagerAugust 27, 2018 at 8:09 am #213411Sorry I’ve been remiss in posting here.
The MS-DEFCON number refers to the current state of patching. It doesn’t refer to a specific set of patches. It’s an on-off switch: If we’re at 3-4-5, go ahead and install outstanding patches. If we’re at 1-2, do not install patches. Think of it as a go/no-go flag, not limited to a single patch or group of patches, spanning all of the stuff that Microsoft offers.
(There’s one exception: If you have a new machine, or you just installed a new version of Windows or Office, you should go ahead and install everything — even if we’re going through a rough month.)
In all cases, read the fine print, which appears in Computerworld.
If you’re concerned about individual patches, or groups of patches, or months of patches, or groups of months of patches, you should refer to Susan’s Master Patch List, which goes into great detail. Susan’s comprehensive list is for people who are concerned about installing individual patches. MS-DEFCON is meant for folks who don’t want to be bothered with the details — they only want a “go ahead” when the coast is clear, when the benefits of patching in general outweigh the risks.
The MS-DEFCON level of 2 right now means you shouldn’t install patches. Since we never got out of the MS-DEFCON 1-2 realm in July, that means you shouldn’t install either July or August patches. Just don’t install any patches. Simple.
There aren’t any imminent threats, and there are no improvements embodied in the patches, that (in my mind) justify installing either the July or August patches.
If we get a fairly clean round on Tuesday, I’ll release the kraken. Until then, relax. There’s no reason at all right now for installing July or August patches.
5 users thanked author for this post.
-
-
-
-
MrJimPhelps
AskWoody MVPAugust 24, 2018 at 10:45 am #212940does the MS Defcon level at the top of this page refer to the current month only? My feeling is that it does, but I would like it confirmed.
I’ve always thought of it as a continual notice. In other words, as soon as things change, Woody changes the Defcon level.
Since patches generally are issued monthly, the Defcon level is generally a monthly thing; but that isn’t a hard and fast rule. It could change at anytime; or, it might not change in more than a month.
Group "L" (Linux Mint)
with Windows 10 running in a remote session on my file server2 users thanked author for this post.
-
Klaas Vaak
AskWoody LoungerAugust 26, 2018 at 11:18 am #213246@Mr.JimPhelps: you are right about there not being a hard & fast rule, because right now it refers to both – https://www.askwoody.com/2018/staying-the-course-at-ms-defcon-2/
And that is why I think it would be useful to have a flag attached to the Defcon shield to take away doubt & confusion.
1x Linux Mint 19.1 | 1x Linux antiX
-
DrBonzo
AskWoody PlusAugust 26, 2018 at 1:07 pm #213252I’ve been hanging out at AskWoody for roughly 2 years now, and this is the first time the DEFCON number has applied to more than one month, at least according to my memory. All the other times the DEFCON number has gone up to 3 or higher before the next months patches have come out.
So, if my memory is serving correctly, we’re in a highly unusual situation now.
2 users thanked author for this post.
-
Microfix
AskWoody MVPAugust 26, 2018 at 1:30 pm #213256I actually think it’s no more unusual that the first three or four months at the start of the year with meltdown etc.. IIRC there were only a few days between catching up and new patches being issued for the next month over that period of time.
As long as your antivirus security, browser and extensions are being updated, there’s absolutely nothing to be worrying about.If debian is good enough for NASA... -
Klaas Vaak
AskWoody LoungerAugust 27, 2018 at 3:03 am #213365@Microfix: forgive my simplicity, but I fail to see the relevance of the antivirus, browser and extensions in this context.
What’s more, you are contradicting yourself: if this type situation occurs in the 1st 3-4 months of the year (BTW I find that already far too long), and it happens again in the 7th month, then, in view of MS’s deteriorating track record, I maintain that a flag indicating the month next to the Defcon shield is not too much to ask for. We already have enough confusion caused by MS, we don’t need more added to that here, esp. since adding a flag is no major undertaking, surely?
1x Linux Mint 19.1 | 1x Linux antiX
-
Microfix
AskWoody MVPAugust 27, 2018 at 3:33 am #213367So reminding people to update their AV, browsers and extensions is inappropriate?
This is all relative to skipped patches for July and August and good practice regardless.
If you wish to put forward your idea of a flag, I suggest you contact Woody directly, instead of posting it all around the blog/ forum. please refer to Lounge rules on repetition.If debian is good enough for NASA... -
Klaas Vaak
AskWoody LoungerAugust 27, 2018 at 4:57 am #2133781. Please explain what AV, browsers and extensions have to do with Windows.
2. I did ask Woody directly in another thread but he did not answer. Instead, Kirsty answered, so I replied to her. Other people also answered but none addressed the issue I raised, which is why I returned to my request to keep the focus. It was certainly not my intention to spam the thread.
3. I did not mean to ruffle your feathers either, which must be clear from my posts. Your virtual kick in my butt seems a bit over the top.
1x Linux Mint 19.1 | 1x Linux antiX
-
Elly
AskWoody MVPAugust 27, 2018 at 11:28 am #2134681. Please explain what AV, browsers and extensions have to do with Windows.
Here is an article talking about how the Meltdown exploit could happen through your browser… basically by using a timing attack to trigger buffer overflow and allowing private data on your Windows (or Linux) operating system to be read by the attacker. All the major browsers took steps to prevent this kind of attack, so you would be protected from that particular direction, as long as you have an up to date browser.

Non-techy Win 10 Pro and Linux Mint experimenter
-
Klaas Vaak
AskWoody LoungerAugust 27, 2018 at 2:57 am #213364 -
OscarCP
MemberAugust 27, 2018 at 6:45 pm #213549DrBonzo #213252 : ” So, if my memory is serving correctly, we’re in a highly unusual situation now.”
It looks to me like the DEFCON, out of necessity, is increasingly determined by the repeated rafts of problems with Windows 10, Surface, etc. I have Windows 7 and the situation has been pretty good, comparatively, this month, and not that bad in July, either. Pretty much, in fact, as it used to be before Windows 10 and other changes in MS policies concerning or affecting Windows got started some three years ago. (Only 3 years? It feels more like an eternity!) So for myself, I now pay more attention to the Master Patch List and the chatter here and elsewhere.
Group B. Windows 10 Pro, SP1 x64.
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV -
Kirsty
ManagerAugust 27, 2018 at 7:21 pm #213554I have Windows 7 and the situation has been pretty good, comparatively, this month, and not that bad in July, either.
Ah, excuse me. That is July 2018?! That isn’t how I would interpret what Woody had to say on the subject (Aug 10th):
The Win7 and 8.1 bugs are so bad that Microsoft took the unprecedented step of changing Monthly Rollup Previews to “recommended” so they’re installed automatically.

-
OscarCP
MemberAugust 27, 2018 at 8:14 pm #213558I was speaking from, by now, considerable experience with Win 7 patching as Group B. I think that opinion of Woody was about Win 7 S&Q rollups and Group A patching. In my own just one-man opinion and, admittedly, the opinion of a one man not gifted with a panoptical observation of events, those are second only to Windows 10 as causes of grief, with the consequent hair pulling, cloth rendering and lamentation. Which is one reason I am Group B for ever (or for as long as I continue to run a machine with Windows as its OS…)
I probably should also have mentioned Win 7 rollups and not just Windows 10 in my post further up, to roundup all the usual suspects.
And from what I’ve heard, Windows 8.1 (with non-Rollup patches) has not being doing that bad either.
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV -
woody
ManagerAugust 28, 2018 at 2:17 am #213597It’s a question of degree, but Win7 patches (and associated .NET, IE, and other patches) in July were pretty dismal.
If you’re at the Master Patch List level of enlightenment, the view’s a bit different, but no matter how you slice it, July was execrable.
Win8.1 has been pretty good.
5 users thanked author for this post.
-
-
anonymous
GuestAugust 23, 2018 at 11:43 pm #212871OscarCP, haven’t you already stated here that you have!
It seems you have an unanswered question also.
https://www.askwoody.com/forums/topic/patch-lady-report-on-the-august-updates/#post-212636columbia2011
AskWoody LoungerAugust 23, 2018 at 2:37 pm #212778In KB4343900 (Monthly Rollup) was published known issue with IE 11 (a blank page may appear for some redirects. Additionally, if you open a site that uses Active Directory Federation Services (AD FS) or Single sign-on (SSO), the site may be unresponsive).
Full info – https://support.microsoft.com/en-us/help/4343900/windows-7-update-kb4343900-
DrBonzo
AskWoody PlusAugust 23, 2018 at 2:44 pm #212779The same issue is reported on the MS support page for the IE11 cumulative update, KB4343205. The issue is not reported for the security only update, KB4343899.
So, both Groups A and B are affected by this issue (assuming the Rollup for A and the SO and IE11 updates for B).
Geo
AskWoody Plusfernlady
AskWoody LoungerAugust 23, 2018 at 5:39 pm #212828-
Microfix
AskWoody MVP
anonymous
GuestAugust 23, 2018 at 6:05 pm #212825WARNING! Windows Updates for Windows 10 1803 spits out 2018-05 Update for Windows 10 Version 1803 for x64-based Systems (KB4100347) but this microcode update is already replaced by 2018-08 Update for Windows 10 Version 1803 for x64-based Systems (KB4346084)!
See
https://www.catalog.update.microsoft.com/ScopedViewInline.aspx?updateid=e13a1770-08b4-4f08-9f83-d8ed662fb474
and
https://www.catalog.update.microsoft.com/ScopedViewInline.aspx?updateid=818b74db-252b-415b-895b-f055fc6254b4
for details.Best of all, this update is offered even if the CPU is not listed, and the BIOS is up-to-date serving the latest microcode from Intel…
anonymous
GuestAugust 23, 2018 at 6:06 pm #212826There was a thought that some human would publish benchmarks regardless of that agreement, it is a ridiculous demand that could cause worse feelings throughout the technology and computer user communities.
Who knows what Intel’s marketing department would begin to claim about their processors? Yet another reminder to stay alert, ’cause they are trying anything to catch us unaware.
BobbyB
AskWoody LoungerAugust 23, 2018 at 6:13 pm #212839May just wait a couple of weeks here I am not seeing a lot of fuss around here or elsewhere on the Web after July and Aug’s patch frenzy, “quiet before the storm” perhaps?
Win’s 10 x64 Pro (Partition) and Home both 1709 (VHD) July’s still hidden, July’s came out of the defer 30 days after on Pro and was hidden with WUMT, 1803 Home (VHD) Aug’s hidden WUMT. Office 2010/16 first batch 1st patch Tuesday for July office 2010/16 installed. Aug’s still hidden WUMT
Win8.1 x64 Julys installed no problem, never is, and Aug’s just waiting.
Win’s7 x86 and x64 July’s Office (early batch 1st Office patch Tuesday) installed no worries, Julys (real) patch Tuesday rolled over to this month inc. 2nd Patch Tuesday Office 2010/16 hence still waiting. Probably give it a go if nothing untoward turns up in the next couple of weeks.
Sorry no relevant KB Numbers the machines are all over the place work and Home and an immense amount of KB’s to note. So far so good and nothing untoward to report “fingers crossed” 🙂Ascaris
AskWoody MVPAugust 23, 2018 at 6:24 pm #212841You know, back when it seemed that the microcode updates were finished and the performance hit had already been taken, I took the approach of avoiding the update in firmware and letting the OS handle it (Linux, for the most part, so I got them even though I don’t use 10). I thought that once I was certain I liked how it behaved with the new microcode, I would then consider doing it in firmware.
Now, it just seems like a never-ending series of patches that harm performance (and probably are not optimized as well as they could be, given the pace at which they were coming) to protect against threats that don’t even exist yet in any meaningful sense. What’s the point of going halfway, though? If I am not going to accept all of the microcode changes, I might as well just go back to the one that performed the best (while still allowing the updates in software, as long as the performance is acceptable), at least until there is something out there that actually presents a credible threat to me.
On my Sandy Bridge desktop PC, there hasn’t been a firmware update in ~6 years, but I could have added the newest microcode to my existing firmware image, had I wanted to. My Core 2 Duo laptop never got an update, even though Intel initially planned for a Penryn update, and my Dell Inspiron 11 “Chromebook-but-it-came-with-Windows” (Braswell SoC) laptop allowed me to roll back the firmware to the older, pre-Spectre microcode without issue. The new microcode had been the only thing changed, according to the changelog, so I’m not missing anything else by rolling back.
Then there is my Acer Swift (Apollo Lake SoC). It does not allow reverting to older firmware versions, and because of the buggy firmware it had (and has), I had updated it to the newest firmware release in the hopes for an improvement (which didn’t happen). At the time, I thought it was odd that there was no mention of microcode changes in the firmware changelog, but I presumed they were in there anyway.
I decided to check the microcode revision in use on the Swift last night, and it revealed a version that was released in March of 2017, which is definitely pre-Spectre. I had the latest Linux patch for Intel microcode and the latest (post-Spectre) firmware installed, yet this was the result? It was good news, by my way of thinking, but unexpected.
I searched my microcode revision to verify the date, and I found a page where someone was saying that the Apollo Lake was a strange case. There was no revised microcode for the Apollo Lake from Intel, and apparently the talk is that Apollo Lake does not need it, as it is somehow already immune to Spectre.
Well how do you like that!
I don’t know if it is true or not that Apollo Lake is immune to Spectre as-is, but the part about Intel not releasing any new microcodes for it does appear to be true. The good news is that this means that I have the pre-Spectre version in my firmware. If Intel eventually releases one, I will get it through the Linux update channel, and I can evaluate it from there to see if I will accept the performance hit before I go flashing anything.
And Acer, booooo to you for (1) not having a flash utility built into the firmware, (2) not allowing flashing older firmware, and (3) releasing such a buggy firmware in the first place (and after 8 revisions, it’s still buggy). If this laptop wasn’t such a deal for the price, I would think differently, but I still like it a lot and would buy it again, despite its firmware flaws.
Dell XPS 13/9310, i5-1135G7/16GB, KDE Neon 6.2
XPG Xenia 15, i7-9750H/32GB & GTX1660ti, Kubuntu 24.04
Acer Swift Go 14, i5-1335U/16GB, Kubuntu 24.04 (and Win 11)1 user thanked author for this post.
-
OscarCP
MemberAugust 23, 2018 at 6:55 pm #212847Ascaris: ” On my Sandy Bridge desktop PC, there hasn’t been a firmware update in ~6 years, but I could have added the newest microcode to my existing firmware image, had I wanted to ”
I am curious, because I also have an approx. six years old I-7 “sandy bridge” running Win 7 Pro x64 (mine has four cores and eight virtual processors, which I mention here in case that mattered.) And I have read somewhere that there are no firmware updates for machines that old. Not that I have any intention of installing a firmware update. As regardless of whether it is installed permanently as firmware or gets installed again and again at each and every bootstrapping of the OS, if something goes wrong with the install and the machine cannot go through with the booting process, I suspect that the only way to ever use the machine again would entail performing the kind of major surgery that (this being me) I am loath to even think of. So I might just as well remove the hard disk and send the rest of the PC to recycling.
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV -
Ascaris
AskWoody MVPAugust 23, 2018 at 7:45 pm #212853Linux reports that the microcode in use by my Sandy CPU has a release date of February 7, 2018. Ubuntu pushed it out on March 13.
If a microcode update from the OS borks your PC to the point that it cannot even boot, just turn it off and go to recovery mode (whatever your particular OS has) and remove the update, or restore from backup. It’s no different than any other bad update in terms of how you deal with it.
If your PC is borked by a firmware update released by your PC OEM, there’s a good chance the PC is still under warranty (sadly, most of them forget a PC even exists after the replacement model is introduced, which happens really quickly), and you can send it in and let them take care of it.
Dell XPS 13/9310, i5-1135G7/16GB, KDE Neon 6.2
XPG Xenia 15, i7-9750H/32GB & GTX1660ti, Kubuntu 24.04
Acer Swift Go 14, i5-1335U/16GB, Kubuntu 24.04 (and Win 11) -
OscarCP
MemberAugust 23, 2018 at 8:33 pm #212855Ascaris: ” If a microcode update from the OS borks your PC to the point that it cannot even boot, just turn it off and go to recovery mode (whatever your particular OS has) and remove the update, or restore from backup ”
Thanks for your answer, and particularly this bit of information: I had thought that if the machine could not be booted up, then it was impossible to do anything with it, including a login in recovery mode. Good to know that, even then, this is still possible.
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV -
Ascaris
AskWoody MVPAugust 24, 2018 at 1:56 am #212879Well, mostly, Oscar, but it depends on what you mean by the terms. “Could not be booted up” can mean the PC is deader than a doornail, with no signs of function at all, or it could mean that it POSTs properly and tries to boot, but that there is something wrong with the OS installation on the hard drive/SSD. A failed or faulty firmware microcode update could possibly cause the first kind of issue (probably not, but it is possible), while an update to the microcode delivered as a Windows or Linux update would only cause the second kind of problem.
Dell XPS 13/9310, i5-1135G7/16GB, KDE Neon 6.2
XPG Xenia 15, i7-9750H/32GB & GTX1660ti, Kubuntu 24.04
Acer Swift Go 14, i5-1335U/16GB, Kubuntu 24.04 (and Win 11) -
OscarCP
MemberAugust 24, 2018 at 9:19 pm #213029Thanks, Ascaris.
Either way, not something to look forward to.
I’ll keep doing frequent backups, and if the Big Bad Hack ever gets my not-microcode updated machine, the data and software (reusable, maybe) will still be where I can get it, and I’ll let go of the PC, sent on its way where all good PCs in the end must go (recycling) and then will go and get myself something else (sigh).
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV
-
-
-
-
GoneToPlaid
AskWoody Lounger
rc primak
AskWoody_MVPAugust 24, 2018 at 11:33 am #212951Gentlemen, let’s not mix Penguins with Windows with Chrome Eyes!
Chrome OS is a special case. It uses hardware and firmware lockdowns to prevent issues like Meltdown and Spectre. The OS itself and the processors in Chromebooks are seldom if ever patched with microcode updates. Hence, no slowdowns can occur in Chromebooks due to these patches.
Creaking Chromebooks getting Meltdown protection soon
Chrome OS 66 to protect older Intel units, still working on ARM
https://www.theregister.co.uk/2018/03/21/chrome_os_66_meltdown_fix/
https://www.chromium.org/chromium-os/meltdown-spectre-vulnerability-status
In Linux, the kernel has several mitigations, but some of these are turned off by default. You would have to recompile a special kernel to turn on these mitigations, as they would impact system performance significantly in some systems. In Ubuntu, you can see just what is turned on or off, both OS and firmware (hardware, or BIOS) by running Spectre-Meltdown Checker (a downloadable script — please verify this script before running it!):
https://github.com/speed47/spectre-meltdown-checker
How to check Linux for Spectre and Meltdown vulnerability
https://www.cyberciti.biz/faq/check-linux-server-for-spectre-meltdown-vulnerability/
(discussion and sample output)
Coffee Lake, Apollo Lake and Kaby Lake do have Spectre-Meltdown BIOS Updates (microcode patches):
Microsoft expands Spectre, Meltdown patches to include Windows 7/8.1, more Intel chips
Microsoft now supports a broader range of operating systems and Intel processors in its fight against Spectre and Meltdown.
(Some of this article deals with Windows OS patches, but the processors themselves are also covered.)
Finally, we come to Microsoft and the Windows OS patches. These are turned on by default, but some of the MS patches undo the BIOS Update protections. There is a way to control this from within the Gibson Research InSpectre applet:
https://www.grc.com/inspectre.htm
Clear enough? Not to me either.
-- rc primak
8 users thanked author for this post.
-
OscarCP
MemberAugust 24, 2018 at 1:38 pm #212964Thank you for a great and helpful post shading some clarity on these, to me at least, confusing issues!
Unfortunately (or is it fortunately?), this new clarity shows that some of us — myself for example, with an early vintage “sandy bridge” CPU — are now (permanently?) left out of the newly announced microcode patches… On the bright side: probably this is not the most worrisome problem for most of us. At least not for now.
Group B patcher. Windows 7 SP1 x64, I-7 “sandy bridge” CPU.
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV
GoneToPlaid
AskWoody Loungeranonymous
Guest-
Susan Bradley
Manager -
Noel Carboni
AskWoody_MVPAugust 24, 2018 at 6:34 am #212910Yes, please share the specifics of what you’re seeing go wrong.
Like Susan, I have experienced no problems on my test systems nor on a production system I chose to bring up to date yesterday morning.
-Noel
6 users thanked author for this post.
-
Mr. Natural
AskWoody Lounger
-
sldc88
AskWoody LoungerAugust 23, 2018 at 10:51 pm #212868Thank you Woody for the information.
It is my understanding that we need to manually install both the July and the August updates. Am I right or can the July patches be skipped?
If the answer is no, is it necessary to install KB 4338823 prior to to KB 4345459 or will the latter only suffice?
Thanks.
Group B, Windows 7 SP1, 64 bit.
-
Noel Carboni
AskWoody_MVPAugust 24, 2018 at 6:20 am #212905If you’re doing Windows 7 Update the typical way, i.e., starting the Windows Update user interface and choosing [Check for updates] there, you should just be offered the latest cumulative patch, KB4343900. You should need to do nothing special w/regard to sitting the process out for July.
Note this wording from the Microsoft description page for KB4343900:
This security update includes improvements and fixes that were a part of update KB4338821 (released July 18, 2018)…:
This is what you should see:
-Noel
-
Microfix
AskWoody MVPAugust 24, 2018 at 6:45 am #212913Thank you Woody for the information.
It is my understanding that we need to manually install both the July and the August updates. Am I right or can the July patches be skipped?
If the answer is no, is it necessary to install KB 4338823 prior to to KB 4345459 or will the latter only suffice?
Thanks.
Group B, Windows 7 SP1, 64 bit.@Noel has posted the Group A style of patching but, as you are Group B it’s different;
In answer to your first question: Yes the July patch needs to be installed prior to the August patch as these patches are non-cumulative.
It’s best to wait for DEFCON 3 then there will be instructions given on the methodology for Group B patchers, just in case there are any pitfalls.If debian is good enough for NASA...5 users thanked author for this post.
radosuaf
AskWoody LoungerAugust 24, 2018 at 2:11 am #212882I updated fully yesterday (semi-annual not targeted) + installed latest BIOS for MSI website for the mainboard (contains C6 microcode update from Intel). Nothing exploded, but I think the whole system is a tad slower.
Fractal Design Pop Air * Thermaltake Toughpower GF3 750W * ASUS TUF GAMING B560M-PLUS * Intel Core i9-11900K * 4 x 8 GB G.Skill Aegis DDR4 3600 MHz CL16 * ASRock RX 6800 XT Phantom Gaming 16GB OC * XPG GAMMIX S70 BLADE 1TB * SanDisk Ultra 3D 1TB * Samsung EVO 840 250GB * DVD RW Lite-ON iHAS 124 * Windows 10 Pro 22H2 64-bit Insider * Windows 11 Pro Beta Insider4 users thanked author for this post.
-
Noel Carboni
AskWoody_MVPAugust 24, 2018 at 6:26 am #212909Have you timed any Disk I/O-intensive operations before the update, that could be compared with your current system state? My greatest concern with the recent patches is that they seem to affect I/O throughput, especially for jobs where a lot of multitasking is involved, like software builds from sources. The other thing that benchmarking showed me was that display I/O speed was affected, and depending on the power of your graphics card that’s something you can often sense.
-Noel
-
OscarCP
MemberAugust 24, 2018 at 1:26 pm #212962Noel, Have you noticed if this slowdown also happens: (1) after recent updates of Windows 7 as well; (2) for both Group A and B? Thanks.
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV -
Noel Carboni
AskWoody_MVPAugust 25, 2018 at 6:00 am #213052I benchmark my systems after every important change. I have NOT measured nor felt an additional significant slowdown on my Win 7 system after the initial Spectre/Meltdown updates introduced their overhead.
Summary of my observations for this small 2-core Haswell system (Dell PowerEdge T20) functioning in a small business server role:
- Significant loss of disk and display performance measured when Spectre/Meltdown mitigation updates first installed, especially where multi-threading is involved.
- Most, but not all, of that lost performance was recovered by disabling the mitigations with GRC InSpectre. Specific changes were noted in both display responsiveness and maximum disk I/O verified depending only on the InSpectre settings. Remaining loss of performance (with Spectre/Meltdown mitigations disabled) as compared to December 2017 patch level was somewhere between 5% and 8%.
- This system is kept up to date Group A style (i.e., all updates applied via Windows Update after manual initiation). Unwanted communications are mitigated through configuration and policy changes.
- Several BIOS updates from Dell have been made available and applied so far.
- No significant additional reductions in performance noted since the initial Spectre/Meltdown update, including tests I just ran after August updates. However, note that these results could be skewed by the next item…
- I added an SSD to the RAID 5 array at the heart of this system a month ago, and disk performance improved as expected (with mitigations remaining disabled by InSpectre).
- I have not yet found time (nor the desire) to test with the new disk and Meltdown/Spectre mitigations enabled again.
- The system is utterly stable and runs 24/7 without faults between reboots mandated by updates.
-Noel
- Significant loss of disk and display performance measured when Spectre/Meltdown mitigation updates first installed, especially where multi-threading is involved.
-
-
-
radosuaf
AskWoody LoungerSeptember 3, 2018 at 6:33 am #214901I did some testing yesterday (3D graphics performance) and it seems that W10 1803 is quite a bit faster than 8.1, both unpatched and fully patched. So, taking potential hit from BIOS aside (this I won’t be able to measure now), seems that the OS itself is not slowing things down.
Fractal Design Pop Air * Thermaltake Toughpower GF3 750W * ASUS TUF GAMING B560M-PLUS * Intel Core i9-11900K * 4 x 8 GB G.Skill Aegis DDR4 3600 MHz CL16 * ASRock RX 6800 XT Phantom Gaming 16GB OC * XPG GAMMIX S70 BLADE 1TB * SanDisk Ultra 3D 1TB * Samsung EVO 840 250GB * DVD RW Lite-ON iHAS 124 * Windows 10 Pro 22H2 64-bit Insider * Windows 11 Pro Beta Insider
zero2dash
AskWoody Loungeranonymous
GuestAugust 24, 2018 at 12:22 pm #212954Hello, I’ve looked at the master patch list for the patches review and status for installation. As a result, I have a couple of questions:
1) I have KB4022136, released 7-3-18, on my Windows update but it is not listed in the master patch list for July 2018. Is is safe to install this update for Powerpoint 2010?
2) I see that the Mater Patch list shows that KB4345590 Security/Quality for .net 3.5.1, 4.5.2, 4.6…4.7.1 for Win 7 SP1 is safe to install. I also have KB4054530 for .Net 4.7.2 on my windows update. Is this patch safe to install?
Thank you very much to Ask Woody and all the people that make it work. You help in navigating the maze of patches is much appreciated.
1 user thanked author for this post.
-
Microfix
AskWoody MVPAugust 24, 2018 at 12:43 pm #212956You may have missed this but it’s on the list for July 2018:
07/03/2018 – KB4022136 – PowerPoint 2010 – No issues – Help message for equation editor.
This is safe to install 🙂
08/14/2018 – KB4345590 – Security and Quality Rollup updates for .NET Framework 3.5.1, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, and 4.7.2 for Windows 7 SP1 and Server 2008 R2 SP1 – Ok to install – None at this time – Various
This is pending Woody’s go-ahead as we are still on DEFCON 2
KB4054530 for .Net 4.7.2: Is this in
optionalimportant updates being offered via WU un-ticked? If you don’t have .net 4.7.2 installed on your system and everything works, you don’t need it.If debian is good enough for NASA...1 user thanked author for this post.
-
jburk07
AskWoody PlusAugust 25, 2018 at 12:07 pm #213085@anonymous #212954 and @Microfix,
KB4054530 appears to be the update that *installs* .NET 4.7.2. On my Windows 7 SP1 X64 system, it is listed under Important updates but is unchecked, so I won’t be installing it.
Linux Mint Cinnamon 21.1
Group A:
Win 10 Pro x64 v22H2 Ivy Bridge, dual boot with Linux
Win l0 Pro x64 v22H2 Haswell, dual boot with Linux
Win7 Pro x64 SP1 Haswell, 0patch Pro, dual boot with Linux,offline
Win7 Home Premium x64 SP1 Ivy Bridge, 0patch Pro,offline -
Microfix
AskWoody MVP
-
-
anonymous
GuestAugust 24, 2018 at 2:18 pm #212967Windows 7 SP1 64bit, with Broadcom network card. Group B.
Installed a few days ago, July’s updates; IE11 KB4339093, Security Only KB4338823 then installed KB4345459 (some say 4345459 covers 4338823 but Microsoft did not say so).
Installed KB4340004 SO .net – with the one for 3.5.1 kb4338612.
From the catalog; Installed IE11 first, Windows SO 2nd and 3rd, and .net last.
Installed one at a time.
No network issues. No oddities.
Rebooted 3 times and let it sit for several minutes.
No Problems.
Thanks to all here.
-
Microfix
AskWoody MVP
anonymous
Guest-
OscarCP
MemberAugust 24, 2018 at 5:54 pm #212993As of now, all patches for all systems, etc. are listed as “OK to install” in the Patch Lady’s Master Patch List, here at Woody’s.
With my thanks, again, to the Patch Lady, for keeping the List up to date and all inclusive.
For my part, I am going to wait for another week, or else for some days after Woody’s DEFCON goes up, whichever comes first.
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV1 user thanked author for this post.
-
Kirsty
ManagerAugust 26, 2018 at 2:46 am #213157all patches for all systems, etc. are listed as “OK to install”
Ah, not exactly! August’s list says Win10-1803 (declared semi-annual) is “Not at this time”, and July’s list has a number of notable entries…
and “KB2952664 | Compat/Telemetry Update | Not at this time”Generalities can be problematic. We are expecting Woody to change the MS-Defcon rating in coming days.

-
anonymous
GuestAugust 24, 2018 at 6:35 pm #212998I am really glad that the update to V1803 doesn’t mess up the Start Menu and it doesn’t install all the games that all the 160X and 170X updates did each time. WOODY you should do an article on this. It’s a big change and makes it a lot easier to stomach the update to V1803. Especially when I have multiple Profiles that I have to configure the same on each PC.
I even used the Win 10 Update Assistant to go from 1511 straight to 1803 and it keep my start menu the same without any of the usual bloat and marketing ware.
1 user thanked author for this post.
-
woody
Manager -
rc primak
AskWoody_MVPSeptember 4, 2018 at 10:04 am #215082This was a 1511 to 1803 upgrade. That difference does witness a significant increase in bloat. My own 1709 to 1803 upgrade showed an actual decrease in the amount of disk space used, and I got more control over the MS adware which is increasingly foisted into the OS and the browsers. From the Lock Screen to Notifications to App notifications, the spamming of the Windows 10 OS continues to grow with every new release if the user is not savvy enough (or annoyed enough) to take actions.
-- rc primak
-
anonymous
GuestAugust 24, 2018 at 6:36 pm #212999I just allowed the newest Cumulative August updates, skipped everything .net and now I have some PC’s in WSUS asking for Servicing Stack Update KB4338819, but https://support.microsoft.com/en-ca/help/4338819/windows-10-update-kb4338819 says ‘When installing both the servicing stack update (SSU) KB4343669 and the latest cumulative update (LCU) from the Microsoft Update Catalog, install the SSU before installing the LCU.’
Should I just skip the SSU since the CU is already installed?
(anon #212998)-
woody
Manager
anonymous
GuestAugust 26, 2018 at 7:34 pm #213278Win 7 SP1, Group B
Laptop, Dell Inspiron 5520, i7-3612QM, 64 bit, Intel Centrino Wireless-N 2230 adapter.
Desktop, locally built, i7-4770 Haswell, 64 bit, Intel Ethernet Connection 1217-V adapter.
Installed July 2018 security updates, one at a time and restart as required, on both pc yesterday afternoon:
First, KB4339093, Cum. Sec for IE11, next KB4338823, Sec. only, next KB4345459,
then KB4340004 Sec only with KB4338612 for .NET Framework 3.5.1, last KB4338602 for .NET Framework 4.5.2
Have restarted the computers two or three times and shut down once after the installation. So far so good, no problems.
Thanks y’all3 users thanked author for this post.
anonymous
GuestSeptember 2, 2018 at 9:41 am #214738Previously I had installed July’s update but that was the first since Jan & Feb plus KB4100480 in March.
Just installed Aug 18 update on my wife’s PC (well someone has to be a guinea pig). It’s AMD ASUS A88XM-A with A4 5300 processor running Win 7 Prof. 64bit.
Download took ages (in fact yesterday I abandoned it). OK today but the actual update took ages. So far seems OK. Desktop eventually loaded and I can access the internet using FireFox. (don’t use IE).
Not too sure if I will also update my own similar PC. It’s time consuming and stressful.
Alan in UK
1 user thanked author for this post.
anonymous
GuestSeptember 2, 2018 at 9:44 am #214739Should have said. I applied
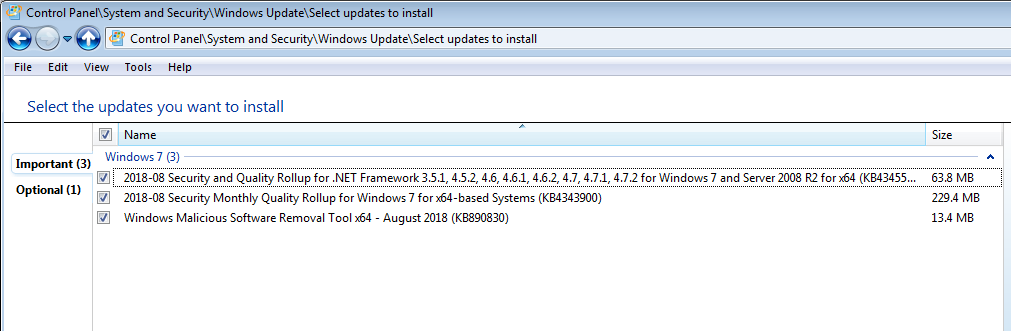
1. Definition Update for Windows Defender Antivirus – KB915597 (Definition 1.275.542.0)
2. 2018-08 Security and Quality Rollup for .NET Framework 3.5.1, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2 for Windows 7 and Server 2008 R2 for x64 (KB4345590)
3. 2018-08 Security Monthly Quality Rollup for Windows 7 for x64-based Systems (KB4343900)
4. Windows Malicious Software Removal Tool x64 – August 2018 (KB890830)1 user thanked author for this post.
-
anonymous
GuestSeptember 2, 2018 at 12:01 pm #214767Anonymous 214738 and 214739-
This past week I d/l’d and installed same as you except I didn’t get the Windows Defender update since I have that program disabled. I also didn’t go get them all at once, but, instead, one at a time.
All of them downloaded quickly EXCEPT the update for .net framework, KB4345590, which was 84.6 megs in size. It downloaded this past Wednesday evening at dial-up speed (56k) however the following morning, on another computer, it downloaded at a more normal speed.
The download at dial up took almost a half hour to complete, but once it did, the install went well, proceeding at normal speed.
How do I know the d/l happened at dial up speed? through the use of the Resource Monitor built into Windows 7! It has a section for internet /network connections and I was able to see the connection for the .net update was running at a paltry 56k speed.
The monthly roll-up was as slow as usual. It doesn’t take all that long to actually download, the now-massive thing. However, the status indication within the WU screen remains stuck at “downloading x%” until the inner working of WU decide just what parts of the massive update they actually need. Once that’s complete, WU then proceeds to install what it needs. This is based on my own observations of the updating behavior using Task Manager while running Windows Update.
1 user thanked author for this post.
Viewing 19 reply threads -

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Microsoft Defender as Primary Security Question
by
blueboy714
1 hour, 15 minutes ago -
USB printers might print random text with the January 2025 preview update
by
Alex5723
27 minutes ago -
Hacktool:Win32/Winring0 (Awaiting moderation)
by
Marvel Wars
4 hours, 4 minutes ago -
Google’s 10-year-old Chromecast is busted, but a fix is coming
by
Alex5723
5 hours, 58 minutes ago -
Expand the taskbar?
by
CWBillow
5 hours, 49 minutes ago -
Gregory Forrest “Woody” Leonhard (1951-2025)
by
Susan Bradley
4 hours, 1 minute ago -
March 2025 updates are out
by
Susan Bradley
1 hour, 19 minutes ago -
Windows 11 Insider Preview build 26120.3380 released to DEV and BETA
by
joep517
23 hours, 35 minutes ago -
Update Firefox to prevent add-ons issues from root certificate expiration
by
Alex5723
1 day, 6 hours ago -
Latest Firefox requires Password on start up
by
Gordski
1 day, 1 hour ago -
Resolved : AutoCAD 2022 might not open after updating to 24H2
by
Alex5723
1 day, 19 hours ago -
Missing api-ms-win-core-libraryloader-11-2-1.dll
by
IreneLinda
18 hours, 19 minutes ago -
How Much Daylight have YOU Saved?
by
Nibbled To Death By Ducks
21 hours, 17 minutes ago -
A brief history of Windows Settings
by
Simon Bisson
14 hours, 55 minutes ago -
Thunderbolt is not just for monitors
by
Ben Myers
13 hours, 31 minutes ago -
Password Generators — Your first line of defense
by
Deanna McElveen
18 hours, 58 minutes ago -
AskWoody at the computer museum
by
Will Fastie
14 hours, 34 minutes ago -
Planning for the unexpected
by
Susan Bradley
19 hours, 58 minutes ago -
Which printer type is the better one to buy?
by
Bob99
1 day, 21 hours ago -
Upgrading the web server
by
Susan Bradley
1 day, 19 hours ago -
New Windows 11 24H2 Setup – Initial Win Update prevention settings?
by
Tex265
2 days, 14 hours ago -
Creating a Google account
by
DavidofIN
2 days, 13 hours ago -
Undocumented “backdoor” found in Bluetooth chip used by a billion devices
by
Alex5723
2 days, 19 hours ago -
Microsoft Considering AI Models to Replace OpenAI’s in Copilot
by
Alex5723
3 days, 6 hours ago -
AI *emergent misalignment*
by
Alex5723
3 days, 8 hours ago -
Windows 11 Disk Encryption/ Bitlocker/ Recovery Key
by
Tex265
1 day, 16 hours ago -
Trouble signing out and restarting
by
Tech Hiker
15 hours, 22 minutes ago -
Windows 7 MSE Manual Updating
by
Microfix
12 hours, 9 minutes ago -
Problem running LMC 22 flash drive
by
Charlie
2 days, 15 hours ago -
Outlook Email Problem
by
Lil88reb
2 days, 15 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.