The full text of this column is posted at WindowsSecrets.com/2011/04/07/01 (opens in a new window/tab).
Columnists typically cannot reply to comments here, but do incorporate the best tips into future columns.[/td]
[/tr][/tbl]

|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Home » Forums » Newsletter and Homepage topics » LizaMoon infection: a blow-by-blow account
Columnists typically cannot reply to comments here, but do incorporate the best tips into future columns.[/td]
[/tr][/tbl]
When your computer was infected by the Liza Moon virus were you logged on as an administrative user or a limited user? If the latter, did you have to entire your admin password at some point? I guess the main thing I am trying to discover is could this thing take over a system as you describe without logging on via the admin acct?
hey even paid antivirus software will ley such things run. i used nod32 for 5 years without a problem. then got hit by the same sort of malware. my daughter was at the computer when it happen. she tried to close it down with the red X. when i contacted nod32 they told me to download free software that would remove the malware. since then i have not paid for nod32, and use MSE. i also keep malwarebytes up to date manually. i have also seen this problem with other paid and free antivirus programs. so be disappointed if you want, but keep a image handy. that was my way of taking care of the problem in 5 minutes.
richard
I thought that by using the red X the malware would still do some of its bad work. I was taught to use the ALT + F4 to kill the page. Using windows Task Manager is sometimes hard to figure out which is the bad process. A buddy had this and I had him go into safe mode and restore a previous version to get healthy.
Hi roundsdd, and welcome to the Lounge!
There are many scareware variants circulating around the Internet these days, and some of them will inject malware when clicking the red close square in the upper right corner of the popup, or by clicking anywhere in the popup. To cover all possible avenues of infection when encountering one of these, the safest action is to start Task Manager and just look for the name of your Internet browser process, such as iexplore.exe (Internet Explorer), Chrome.exe, Firefox.exe, etc. The browser process is the only one that needs to be killed, as anything running in the current browser session is killed when you shut down the browser process.
I got something very similar via a different route; disguised as a packing note for a DHL shipment in an email (had nothing to do with DHL of course). I would normally never have opened it but I was expecting a package from overseas. McAfee told me the email was clean but I was extra careful. It was an attached zip file (that I detached and scanned separately with McAfee and it reported clean), then a ‘pdf’ file (that I scanned with McAfee and it reported clean) that I ran and saw no pdf file but all the same looking pop ups that Fred got. McAfee offered to help me get rid of it for a fee (after being a loyal customer for over 10 years) but running Malawarebytes from safe mode and rkill.com (a small tool to kill suspect processes) took care of it in about 30 mins. I no longer run McAfee and as a test used MSE to scan the same email file. It picked it first time, so I’m happy with MSE.
Most surfers could/would avoid going to the site that contained the malware if they were using WOT or like service. It is hard not to notice the red circle!
Hi ratchet,
WOT and other systems like it are very useful, and do offer some protection. However, when a previously clean site becomes a host to malware, there is some time involved before it is discovered and updated as a risky site. It is good to remember that no security measures are 100% effective. This helps us to stay alert, and to exercise good judgment
I have run into LizaMoon, installed by panicked users certain their systems were infected by some horrible virus. Clicking the X to kill the program has no effect, and in some cases it is not possible to start Task Manager, install Malware Bytes or scan with MSE. Running anti-virus programs in Safe Mode sometimes works, but this is the single hardest to get rid of virus I’ve run into in 30+ years of tech support. I reformat and start over, just to be sure everything is gone.
My PC business averages one infected customer PC a day. The fake AV viruses are usually what they have. Most come in the same way (a popup window or ad). Many times the customer claims they clicked on the X to close the window and things went downhill from there. I have received a popup and tested the X myself and verified their claims.
The infected PCs have had a variety of protections including Norton, McAfee, MSE, etc. If anyone has found a protection that detects the contents of these bogus popups please share. We want to try it!!
Echoing earlier posts: We usually have to kill the processes with RKill and run ComboFix/Malwarebytes to get the PC cleaned up enough to put it back on its own internal protections. Regularly use Kaspersky rescue disk to boot to a non-Windows OS and scan. Also safety.live.com, TDSSKiller, and F-Secure’s Blacklight. Occasionally have to run an EXE reg fix to restore file associations. Also have to reset IE Proxy to get back online.
I have run into LizaMoon, installed by panicked users certain their systems were infected by some horrible virus. Clicking the X to kill the program has no effect, and in some cases it is not possible to start Task Manager, install Malware Bytes or scan with MSE. Running anti-virus programs in Safe Mode sometimes works, but this is the single hardest to get rid of virus I’ve run into in 30+ years of tech support. I reformat and start over, just to be sure everything is gone.
I see this a lot. Many of the fake anti-virus attackers turn off the ability to run any exe files. they delete part of the system registry. I keep some registry parts on a USB stick to fix those systems. Then you have a short window on boot to get to msconfig. Once you are there you can turn off everything and reboot. In most cases you now have a system that will let you install and run malwarebytes and MSE or the anti-virus of choice. You may need to reinstall the registry bit for system restore at this point to make sure the service runs. Scan with all your tools and return the system to the client. I usually get 75-100.00 for doing this. I don’t know of any anti-virus that can catch these things. I have seen just about everything you can think up that has been infectedd by one of these. I even got caught by comics.com once.
I have run into LizaMoon, installed by panicked users certain their systems were infected by some horrible virus. Clicking the X to kill the program has no effect, and in some cases it is not possible to start Task Manager, install Malware Bytes or scan with MSE. Running anti-virus programs in Safe Mode sometimes works, but this is the single hardest to get rid of virus I’ve run into in 30+ years of tech support. I reformat and start over, just to be sure everything is gone.
I remove a couple of these rogues every week. I’ve learned a couple of tricks.
1st: either close the dialog box(es) with CRTL-ALT-DEL and the task manager or right click them on the task bar and close them that way.
2nd. Some variants block MalwareBytes. When you download the program (I get it from Download.com, it is always in the top 10) rename it to IEXPLORE.EXE when you save it to your desktop. It will now install, but be sure to uncheck the update and run boxes near the end of the install sequence. Then, with Windows explorer, navigate to Program FilesMalwareBytes and change the name of MBAM.exe to Explore.exe. Then, you can run it with a double click, right from Windows Explorer. Now, you can update it and do a full scan, and it will get most of the critters. I usually follow up with a scan with SuperantispywareFree (also from Download.com) and then Combofix if the machine still doesn’t “feel” right. Please read the ENTIRE tutorial for Combofix and use it at your own risk. It does not play well with AVG. You will have to uninstall AVG to get Combofix to run.
Super Antispywarre and several other antivirus programs have USB Flash Drive versions. You download them from another, clean PC, and run the scan directly from the Flash Drive in Safe Mode. This is seldom blocked.
-- rc primak
I agree with RoundsDD. The advice in the article to dismiss the web page dialog using the red X is bad advice. In many cases the dialog is not a true dialog but simply part of the infecting web page and clicking the X (or any other part of the page) starts the infection.
There was a Lounge discussion on this a while back, we concluded the safest route out was to use ctrl-alt-del to bring up Task Manager and kill the browser process. ctrl-alt-del is handled by Windows at a very low level and cannot be subverted by anything (as far as I’m aware – I’m sure some rootkit author is working on it)
I’m sensitive about this subject right now because I’ve just spent a day clearing a fake AV infection from my daughter’s laptop. She claims it just appeared after visiting a previously good website, didn’t click or agree to anything suspicious. She was sitting in the room with me and as soon as the first indication appeared she handed me her PC. Her system includes Windows Vista, McAfee AV, Firefox and she hadn’t disabled UAC.
The culprit called itself “spyware protection” and part of it was an exe: “c:users****appdataroamingdefender.exe”. It had already disabled launching task manager from the taskbar. It took four different AVs, two Malwarebytes passes and msconfig to clear about 30 items identified as “trojan.”. Before her McAfee sub runs out next month I’ve told her to switch to MSE. If your AV is going to miss something critical it’s as well you’re not paying through the nose for it as well. All the detections were by free tools like HouseCall and Malwarebytes.
Ian
Right after WS starter declaring how great MSE was, I used MSE for 2 weeks before I ran into an infected page on a very popular site. MSE did not catch until too late. (gocomics if I remember right).
I dumped it immediately going back to Avast, which has blocked several such attacks in embedded ad’s on known good safe sites.
My wife’s computer (Windows 7 Home Premium, WSE, Administrative user account) got infected with this on 4/5. I rebooted in Safe Mode, and ran a full WSE and McAfee scan. Neither found anything amiss. Eventually removed it manually by deleting suspicious folders in Program Data and similarly-named keys in several Run or RunOnce entries in the Registry. Demoted user to Standard to lessen chance of further problems.
I had a similar problem. I was expecting aUPS package and received an email purporting to contain details. When I clicked on the enclosed file I got similar warnings to LizaMoon called CleanThis but was fooled by the Microsoft appearance to thinking it was genuine. After clicking the clear all button my PC was infected. I also turned off my network connection and sought advice on the internet from another computer. Several solutions were offered including several needing payment but I found one that recommended starting up the infected PC and entering as another user. Fortunately my wife was already entered as a user with full authority. I entered under her name and immediately went to system restore and picked a restore point before the infection. Bingo the system was clear!! I then entered in my own right and ran all the usual AV checks to find only 2 items which MacAfee safely removed. All my PCs now have an extra user with full authority in case of further need.
I had a similar problem. I was expecting aUPS package and received an email purporting to contain details. When I clicked on the enclosed file I got similar warnings to LizaMoon called CleanThis but was fooled by the Microsoft appearance to thinking it was genuine. After clicking the clear all button my PC was infected. I also turned off my network connection and sought advice on the internet from another computer. Several solutions were offered including several needing payment but I found one that recommended starting up the infected PC and entering as another user. Fortunately my wife was already entered as a user with full authority. I entered under her name and immediately went to system restore and picked a restore point before the infection. Bingo the system was clear!! I then entered in my own right and ran all the usual AV checks to find only 2 items which MacAfee safely removed. All my PCs now have an extra user with full authority in case of further need.
I have a “safe” email address that was hacked at Epsilon, got the nice little “we’re so sorry” notes from Target and Best Buy, but immediately notice I was now getting spam from various delivery services – UPS, FedEx, a couple others as well, whereas prior to the hack I got NO spam at my “safe” address. All of those notices were poorly phrased English, first clue and had attached zip files – NEVER, EVER, open a zip file from someone you don’t know has always been my rule. It helped that I hadn’t ordered anything from anyone too, of course. I did reply to one of them saying, gee I wonder what you could have for me since I haven’t ordered anything, I am SO excited. It bounced back undeliverable in a little bit. I am quite annoyed with Epsilon and believe Best Buy violated their own privacy policy which was supposed to NOT share my address with anyone else, not even Epsilon. That Reward Zone card is now gone too along with the business I have given Best Buy over the years. And the business I would have given them in the future. When will someone get serious about prosecuting these fools? Many years ago, I’d send headers to the FCC but I don’t believe they ever do anything about them. The Internet will always be a modern day “Wild West” until companies and governments get serious about prosecuting internet criminals whether they live in Moscow or Bejing.
I have a “safe” email address that was hacked at Epsilon, got the nice little “we’re so sorry” notes from Target and Best Buy, but immediately notice I was now getting spam from various delivery services – UPS, FedEx, a couple others as well, whereas prior to the hack I got NO spam at my “safe” address. All of those notices were poorly phrased English, first clue and had attached zip files – NEVER, EVER, open a zip file from someone you don’t know has always been my rule. It helped that I hadn’t ordered anything from anyone too, of course. I did reply to one of them saying, gee I wonder what you could have for me since I haven’t ordered anything, I am SO excited. It bounced back undeliverable in a little bit. I am quite annoyed with Epsilon and believe Best Buy violated their own privacy policy which was supposed to NOT share my address with anyone else, not even Epsilon. That Reward Zone card is now gone too along with the business I have given Best Buy over the years. And the business I would have given them in the future. When will someone get serious about prosecuting these fools? Many years ago, I’d send headers to the FCC but I don’t believe they ever do anything about them. The Internet will always be a modern day “Wild West” until companies and governments get serious about prosecuting internet criminals whether they live in Moscow or Bejing.
First, Best Buy does not do what you accuse them of. Second, please avoid ethnic slurs such as your last sentence. If you can’t prove allegations, don’t post them here.
-- rc primak
The missing piece in this “blow by blow” article is exactly the process used to disinfect the PC. Did it require running the scanners in Safe Mode? How did the latest versions of the scanners get on the PC if it was disconnected – USB stick, CD burned on another PC, etc.?
Yes the ComboFix/Malwarebytes scans usually were run in Safe Mode (with networking) since we wanted to download the latest copies with updates. Safe Mode also gives us a better chance to run these scans without being interfered with by the virus. Rkill if necessary to stop virus processes long enough to get our scans started. Tough cases required a boot scan using something like Kaspersky’s rescue disk.
Fred, Thanks so much for walking us through your created experience. I am a part time IT consultant and have run into Lizamoon a half dozen or more times on other people’s computers. I have seen it get so far that it was impossible to use the computer with the pop-ups being constant. It did not allow any software to be run on the computer, whether already installed or not.
The only good way I found to get the cleaning process started is to run RKill, which does a wonderful job of stopping any running malware processes. Before that I could not even access or run Task Manager, even in safe mode it was impossible to do anything. For the people who rely on me, I now have a cocktail CD of RKill, Malwarebytes, Spybot Search and Destroy and sometimes one or two other malware killers. I give that to the people, tell them how and in what order to run the cleanup and have seen it work 100% of the time.
As I saw on one of the other posts, often the internet connection, for browser and email has a proxy server change or setup, which keeps the computer from getting on the internet. I always check that once the cleanup is done.
Harald
…….I now have a cocktail CD of RKill, Malwarebytes, Spybot Search and Destroy and sometimes one or two other malware killers. I give that to the people, tell them how and in what order to run the cleanup and have seen it work 100% of the time.
Harald
Sounds like a good thing to have, and I hope easy to create, when all is working well!
I really appreciate all of you folks and the info you share; rarely is anyone ‘snarky’ in a response.
BJ
I now have a cocktail CD of RKill, Malwarebytes, Spybot Search and Destroy and sometimes one or two other malware killers. I give that to the people, tell them how and in what order to run the cleanup and have seen it work 100% of the time.
Are there any licensing issues doing that, or are all of those ingredients in the cocktail freeware?
In the above captioned article, it is suggested to use the red x-box to close suspicious dialogue boxes. Couldn’t a malicious programmer just program the red x-box to run their malware ?
It seems that it would be more prudent to always use the task manager to end the program.
Am I missing something ?
In the above captioned article, it is suggested to use the red x-box to close suspicious dialogue boxes. Couldn’t a malicious programmer just program the red x-box to run their malware ?
It seems that it would be more prudent to always use the task manager to end the program.
Am I missing something ?
Hi rziulek,
Welcome to the Lounge!
And no, you are not missing something. It is best to invoke Task Manager and kill the current browser session to avoid infection. Clicking any area of the pop up is an invitation to trouble. I go as far as instructing clients to avoid clicking anywhere within the browser page, whether inside the popup or within the underlying page, and to never attempt to close the browser via the red square or via the menu exit. It is easier for most folks to remember that.
I actually sent the editor a letter asking the same, and I was directed to come here to post.
Also I’m new, so I also wanted to say hello!
PS- I already tried to post this, but I’m not sure if it needs to go through a moderator first, so if this a repeat, my apologies.
Regards,
b1rd
My letter:
Hi, and thanks for taking the time to read this.
I was reading Fred Langa’s article about the “LizaMoon” infection in the Windows Secrets Newsletter • Issue 283 and I noted he made the below statement, and I was wondering about a possible problem with this.
“Typically, when you encounter any suspicious webpage dialog, the correct procedure is to immediately dismiss it via the red-X close box in the upper-right corner of the dialog box or to simply close the browser. (If needed, you also can use Windows’ Task Manager to kill offending software or its processes.)”
I’ve always been under the impression that these types of rouge malware should be closed, via right-clicking the tab on the taskbar, or bringing up the Task Manager and closing the entire browser. I’m not sure if he meant close the page via the red X on the browser, or on the rouge dialog box itself.
The reason I’m asking is that is it not possible that the programmer has the ability to create the user interface so that anywhere that one clicks on it actually initiates the install command? I don’t know enough about programming, but I can’t see why the install command can’t be disguised as a red X.
Also, I’ve removed a few of these from some computers. (Different variations, but the same type of scare tactic) The last one I did for a friend would not even allow me to install MalwareBytes from a flash drive and disabled his ability to go online. I was finally able to install MalwareBytes through SafeMode, then scanned it and everything was eventually fixed.
Thanks, and thanks for a great newsletter.
I was helping a friend remove this from his computer, only it was called “Win XP Security” in that version. I was able to download MalwareBytes after rebooting in safe mode with networking support, but was not able to run it . I then found an article on my laptop from the MalwareBytes forums that recommended renaming the MalwareBytes download from *****.exe to ****.com. I was then able to install the program. (The **** indicate the latest version, which changes numbers with each new version.)
I then went to the install location, and rename the “mbam.exe” to “mbam.com” which was able to run normally. I let it run and deleted the results, and it killed the infection immediately. I ran it in “full scan” till no more infections came up. I then tried to update the computer but was unable to until I re-registered the dll files associated with Windows Security Center. You can find articles on Google to do this. I launched windows update and updated all. The process was brief, as the computer was set up for automatic updates already, but the infection had disabled that.
Since this was the second time this had happened to him, I encouraged him to purchase a license for MalwareBytes. If you look around you can find coupons to reduce the price. He ended up paying about $21.45 for a license, and it started blocking him from attacks immediately. I was very impressed with this.
I did not run Microsoft’s Security Center, but after reading this article I might suggest he change from Avira anti-virus to MSC.
Thanks for the great article, Mr. Langa.
I was helping a friend remove this from his computer, only it was called “Win XP Security” in that version. I was able to download MalwareBytes after rebooting in safe mode with networking support, but was not able to run it . I then found an article on my laptop from the MalwareBytes forums that recommended renaming the MalwareBytes download from *****.exe to ****.com. I was then able to install the program. (The **** indicate the latest version, which changes numbers with each new version.)
I then went to the install location, and rename the “mbam.exe” to “mbam.com” which was able to run normally. I let it run and deleted the results, and it killed the infection immediately. I ran it in “full scan” till no more infections came up. I then tried to update the computer but was unable to until I re-registered the dll files associated with Windows Security Center. You can find articles on Google to do this. I launched windows update and updated all. The process was brief, as the computer was set up for automatic updates already, but the infection had disabled that.
Since this was the second time this had happened to him, I encouraged him to purchase a license for MalwareBytes. If you look around you can find coupons to reduce the price. He ended up paying about $21.45 for a license, and it started blocking him from attacks immediately. I was very impressed with this.
I did not run Microsoft’s Security Center, but after reading this article I might suggest he change from Avira anti-virus to MSC.
Thanks for the great article, Mr. Langa.
Malwarebytes is available in a free version. There is no need to pay for it, unless you want the frilly, fancy, unnecessary features of the paid version.
-- rc primak
I have had similar malware attack systems with McAfee and Trend Micro successfully. If caught quickly enough I have been successful removing it with System Restore. In several instances the restore points were not available and I had to manually restore using a seperate PC. One of the PC’s infected took several different tools to remove all of the garbage and one needed to have a system reload.
Malwarebytes is available in a free version. There is no need to pay for it, unless you want the frilly, fancy, unnecessary features of the paid version.
I think he was referring to the “real-time” protection aspect and perhaps the automated updates, thus blocking the problem rather than trying to fix it.
COMODO is decent, however it’s only a snapshot. Also, it does insert itself into the Master Boot Record, so if there’s a problem with it- that can be a problem (However I do use it with no problems)
Another FREE option is PargaonBackup & Recovery 2011 (Advanced) Free It’s a free mirroring program in the event you can’t boot. (You need to make an ISO image media which the initial installation will prompt you to do)
I have made several archives, however I have yet to try and restore my system using this program, so I have no comments on that part. I did see it received decent ratings though. Also, if you can boot, you can still use the restore feature without the boot media, but remember it will bring your entire system back to the date of the archive, thus taking away anything you’ve saved as of that time period.
Personally, I use COMODO / TrueImage / and Paragon to back things up.
Paragon is defaulted to save the archive on the main drive, but I would suggest saving it to an external drive (Or another internal dive if you have one) if possible, to reduce the chances of a corrupted archive file, not to mention the longer defrag lag time on a the main drive as well.
b1rd
me too I would like to know. I have a return of the malware so have pulled the plug to wi fi and need to know how to get rid of it. Last time i had to have the drive reformated. Can I just turn the clock back with a restore. Ctl -alt del dont work — they just flash up and are killed. should I use safe mode.. I cant get in in any significant way. should I boot from another disc or pen drive. Can I load a prog to a pen drive and scan from there. I have a lap link usb can I scan from another computer. Any help would be great Thanks
I was able to get rid of it through SafeMode. I installed MalwareBytes from a flash drive while in SafeMode, then ran it while still in SafeMode.
Several people have had success with renaming the file from .exe to .com (renaming it, not changing the file extension) Both during the download, as well as within the programs folder.
Another option I found some place was a portable version of SuperAnti Spyware. It assigns the file a random name, and can be both downloaded directly to a flash drive, then run from it as well. I would still suggest running either in Safemode, or if you can boot, then hit Run> type msconfig and select diagnostic start up, which is basically the same, just easier to get to on many systems.
Edit:
I did do some quick checking and there were a couple people saying not to start this in Safemode, but did not indicate why. They suggested to bring up the task manager Run > msconfig and get to the start up tab ASAP, and quickly uncheck it if you can find it. Personally, I’ve removed several of these, however different variations, and that has never worked for me. Also, I can’t see why running the fix in Safemode would be any problem at all.
This is just another example of the failure of Microsoft to produce a truly secure system. If Microsoft simpled used the same techniques that are routinely employed on *.nix systems, along with its handling of files, none of this would have occurred. I assume you have heard about the Epsilon data breach. Just another example at Microsoft’s failed attempt to provide security for its users. Honestly, why anyone with any common sense would use Microsoft for Web browsing or reading e-mail is beyond my comprehension. There are better Web browsers and far superior MUAs available for the non-windows user. With the possible exception of MS Office, there is not a single program that Microsoft produces that is worth the hassle of using Windows and its required AV/Firewall, etcetera paraphernalia just to attempt a mediocre sense of security. Microsoft != Security is a well understood concept.
This is just another example of the failure of Microsoft to produce a truly secure system. If Microsoft simpled used the same techniques that are routinely employed on *.nix systems, along with its handling of files, none of this would have occurred. I assume you have heard about the Epsilon data breach. Just another example at Microsoft’s failed attempt to provide security for its users. Honestly, why anyone with any common sense would use Microsoft for Web browsing or reading e-mail is beyond my comprehension. There are better Web browsers and far superior MUAs available for the non-windows user. With the possible exception of MS Office, there is not a single program that Microsoft produces that is worth the hassle of using Windows and its required AV/Firewall, etcetera paraphernalia just to attempt a mediocre sense of security. Microsoft != Security is a well understood concept.
Indeed. I use PCs with XP, Win 7, Linux Mint and Ubuntu Studio. For serious business I can’t get away from Windows primarily because of Office. Neither Wine nor Crossover are a full enough solution to be able to run Office 2003, let alone 2010, especially Outlook with IMAP connections.
For most other people linux with Open office and Evolution is more than adequate, and so they could easily use Linux instead on their existing PC. For people with deeper pockets and an absolute need for MS Office then the only alternative is to go for a Mac with Office 2011 or 2004 and get the safety of Unix.
As for staying on Windows, Fred is very naive and trusting of MS, sorry to say. On my Win 7 machine I do use MSE but it is supplemented with the excellent Prevx and Comodo firewall with HIPS enabled. Prevx is easy enough for all users but COmodo needs some expertise and is not for the casual user unless an expert sets it up for them on “default deny” config.
On the XP I use Comodo Internate Security and Prevx plus Malwarebytes for daily scans. So good so far.
This is just another example of the failure of Microsoft to produce a truly secure system. If Microsoft simpled used the same techniques that are routinely employed on *.nix systems, along with its handling of files, none of this would have occurred. I assume you have heard about the Epsilon data breach. Just another example at Microsoft’s failed attempt to provide security for its users. Honestly, why anyone with any common sense would use Microsoft for Web browsing or reading e-mail is beyond my comprehension. There are better Web browsers and far superior MUAs available for the non-windows user. With the possible exception of MS Office, there is not a single program that Microsoft produces that is worth the hassle of using Windows and its required AV/Firewall, etcetera paraphernalia just to attempt a mediocre sense of security. Microsoft != Security is a well understood concept.
Dump Microsoft and get a secure system plus you will save a fortune in time and money. 😎
For most other people linux with Open office and Evolution is more than adequate, and so they could easily use Linux instead on their existing PC. For people with deeper pockets and an absolute need for MS Office then the only alternative is to go for a Mac with Office 2011 or 2004 and get the safety of Unix.
‘.NIX invulnerability is a myth. Mac Os is a ‘NIX, and it has viruses. Same with BSD.
you know, my advice to my friends who encounter this problem. save any documents you have open in the background and then hit the reset button, I’m sure it will be gone that way. yes, it is not a “clean” way to shutdown your PC but then again, you most likely will not be infected (and I say very very likely). As for using UPS, why don’t you sign onto their website to see if they send you an email. I always disgard msg from ups
Doing the Hardware Reset can cause the malware to install on the next boot-up.
As for staying on Windows, Fred is very naive and trusting of MS, sorry to say. On my Win 7 machine I do use MSE but it is supplemented with the excellent Prevx and Comodo firewall with HIPS enabled. Prevx is easy enough for all users but COmodo needs some expertise and is not for the casual user unless an expert sets it up for them on “default deny” config.
On the XP I use Comodo Internate Security and Prevx plus Malwarebytes for daily scans. So good so far.
Prevx has for me been nothing but trouble. It flags EVERYTHING as malware, and blocks everything which has changed since Prevx was last uninstalled and reinstalled. Needs to be reinstalled for this reason every month, when MS Updates are installed. Nothing but hassles and false alarms in my experience.
Comodo and Malwarebytes are fine programs, but you still need a real-time antivirus app. For this I would use MSE on Windows 7, and Avast on Windows XP, unless Avast does weird things on your computer, as it did in Version 6 on my WinXPPro SP3 laptop. There, I reverted to MSE.
-- rc primak
I have been called on at least a dozen times since November to fix this kind of problem after the fact, lots of variations in the screens that come up. This kind of thing consistently gets through Norton, AVG, McAfee, MSE and others, which, considering how widespread it is, is disgraceful.
My solution after the fact, which has worked almost every time:
Boot with f8 to safe mode with networking.
Check Internet Connections in control panel or proxies and turn them off, even if you use other browsers
Check c:/windows/system32/drivers/etc/hosts and remove anything other than 127.0.0.1, even if they say they were put there by an antispyware program
Check Network Connections in control panel for DNS hijackings
Check other browser connections for proxy settings and turn them off
These checks will generally let you download AND update Malwarebytes Anti-Malware AND Super Anti-Spyware from Download.com, which have caught and cleared the problem almost every time.
Twice these things didn’t work and I removed the hard drive and ran the same scans on my own computer with a usb disk controller harness and the damaged disk. One worked, one didn’t.
I have been called on at least a dozen times since November to fix this kind of problem after the fact, lots of variations in the screens that come up. This kind of thing consistently gets through Norton, AVG, McAfee, MSE and others, which, considering how widespread it is, is disgraceful.
My solution after the fact, which has worked almost every time:
Boot with f8 to safe mode with networking.
Check Internet Connections in control panel or proxies and turn them off, even if you use other browsers
Check c:/windows/system32/drivers/etc/hosts and remove anything other than 127.0.0.1, even if they say they were put there by an antispyware program
Check Network Connections in control panel for DNS hijackings
Check other browser connections for proxy settings and turn them offThese checks will generally let you download AND update Malwarebytes Anti-Malware AND Super Anti-Spyware from Download.com, which have caught and cleared the problem almost every time.
Twice these things didn’t work and I removed the hard drive and ran the same scans on my own computer with a usb disk controller harness and the damaged disk. One worked, one didn’t.
Since I make money fixing problems like this, I am glad it happens. Seriously though, why would anyone put themselves through this sort of torture? Dump Microsoft and get a secure system plus you will save a fortune in time and money. 😎
Fred,
Great article, I only have one problem, the next version of this is going to be harder to detect due to your detailed description of the “Giveaways”. I’ll lay odds that the QA will be much tighter on the next one.
My spouse was working on some research the other day and got hit by this, the first thing was a call to me, “just shut it down” was my advice. I then ran my AV tools from linux on the USB stick to make sure the system was clean. Tightly monitored systems, user training, backups and alternate tools are the keys to Clean Systems.
Look who is back! Haven’t encountered this malware in over a year our so! My son and I just fired up an old laptop I had, installed Win 7 Ultimate, MSE, Office 2003 and we were off to the races! He was very excited to have a PC which for the post part was his. Dissapointment set in the next morning when he yelled downstairs ”dad come here quick!” Now my son is only 12 but is well versed in this particular malware as we had gotten it on various PC’s in our house 3 other times in the past few years. My children all know what to do, well atleast they did in the past – don’t click anything, ”Three Finger Solute” (may be dating myself but this is the old school term for Task Manager Alt-Ctrl-Delete), shut ALL instances of the browser down, wait for a minute or so to insure no other pop-ups appear which indicates you were not successful in thwarting the attack and further steps need to be taken, then reboot. He made the mistake of clicking the red X on the pop-up warning box like the one noted in your article. My experience has been, clicking any portion of the box be it , red X, Ok etc, will take you the next step down the road to infection. If this is any thing like the other strains, you were only a few minutes away from your browser be hijacked as well. Usually clicking another pop-up box will get you there.
Now to be fair to MSE, a few years back, a copy of my up to date Trend Micro did not stop this attack either. Best course of action that I have found is reboot to Safe Mode (no networking, just plane SF) and roll back the PC to a previous restore point. In Win 7,reboot the PC (sometimes you have to hold the power button down for 5 our so seconds to force the PC off, those nasty pop-ups sometimes get in the way and depending on the severity of the browser hi-jack, may bring your PC to a crawl). Once the PC is booting or rebooting (depending on what method you had to take – force-off or reboot), hold F8 key down, next screen select Safe Mode ONLY. Wait for the system to boot. Click the Windows Orb, type ”restore” (no quotes) and select ‘restore pc to a restore point (something to that effect)..’ in the following list of results. Hopefully you have restore points and are not of the chosen few who thought shutting off Automatic System Restore points was a good idea in the name of disk space! 😉 Select a restore point and confirm you want to roll back to this point. This will most likely take quite some time, like a minimum of 30 minutes, my experience is it will be in the hour time frame. Once the system is rolled back, open a browser and hit a few websites, if no pop-up warnings show up, your are back in business!! If they do show up, you can try rolling back further. FYI, rolling back your PC can cause loss of settings you had made since the date of the restore point and the date you chose to roll back to this point. My experience, documents, pics etc.. stay.
My two cents, hope it helps.
you know, my advice to my friends who encounter this problem. save any documents you have open in the background and then hit the reset button, I’m sure it will be gone that way. yes, it is not a “clean” way to shutdown your PC but then again, you most likely will not be infected (and I say very very likely). As for using UPS, why don’t you sign onto their website to see if they send you an email. I always disgard msg from ups
Read with interest your article, Fred, as I have been doing for what must be 15 years now. I, too, have seen that fake message, but have never allowed it to act. I’d also like to point out that I’ve never in 20 plus years with personal computers had a virus or piece of malware get through my defenses. I have never used Windows options, until a month ago when my Eset Nod subscription was up for renewal and I relied on your advice, as well as a few other places I respect, and dumped Eset for MSE. I kept Comodo but got rid of Spybot and TeaTimer. I do run MalwareBytes periodically too.
I have to say though, now that you have demonstrated that MSE is NOT what you, and others, have alleged it to be, a safe alternative to other paid products, I am going to dump it and renew Eset Nod and go back to my standalone versions of various products. I stopped using suites when Symantec bought out Peter Norton, or Peter Norton sold his soul to Symantec. Granted I would have to be foolish enough to actually answer yes to ridiculous dialog boxes – which as you point out use atrocious English – nonetheless you have destroyed my confidence in MSE, as if I should have EVER trusted a Microsoft product in the first place, lol. Despite your assurances, I do not use IE, ever. Simply do not trust MS browsers and never will, I have it ON my system, but if I ever need an IE window, I use the IE Tab Plus feature in FF to temporarily turn a FF tab into an IE one which can fool even Windows Update. I will upgrade to IE 9 when it is finally officially released, but won’t use it either, because Microsoft products, even those touted by such respected sources as you, always, in the end, turn out to be full of exploitable holes. Sigh…
as “… it’s deactivated when you install MSE”. I don’t know if that is true or not, as Windows Update on a regular basis offers Windows Defender updates and installs them. I am running MSE and Windows firewall, but am now tempted, as others have done, to go back to ESET NOD32. If MSE didn’t catch this from the get-go, it is essentially a TOTAL failure.
Thanks for the report, but like others, where malware is involved, NEVER trust the close window icon to stop the infection. It is likely too late at that point anyway. Turn off javascript and run it only when you trust what it is doing.
Greetings from LeonSprings,
I have not had the time to read all of these posts, but; very sure they are having something to do with that report by Fred Langa in Windows Secrets latest newsletter. Thank you to Fred for this report, as I have been doing just what he has suggested for many years, do not accept any bogas recommendations from unknown sources.
I have just had somewhat of a similar experience this evening just before downloading Fred’s report . . . my MSC (Microsoft’s Security Client version 2 of MSE) and it could not restart, title bar was RED and the restart button was also RED and could not be restarted by that button. I went into MSC Settings tab and to Real-time protection and unchecked the box for Turn-on real-time protection (recommended) and saved that setting. Then rechecked that box, turning it back on, and it did restart after a few seconds, maybe 20-30 of them. Did an imediate quick scan and all came back clean. Am going to do another with various other AV and malware software I am using on my system.
If I were to wear a hat I would take it off and SALUTE you, Fred Lanaga. I don’t so I will just sing your praises here.
"Infinite CREATOR" cast "Loving Light" upon thee
TIA, CU L8R, 'd' "LoneWanderer"
"Only you can control your future." Dr. Seuss
NOT a leader,
NOT a BLIND follower,
Join US and LIVE this LIFE as ONE!
Original author Unknown
Greetings from LeonSprings,
I have not had the time to read all of these posts, but; very sure they are having something to do with that report by Fred Langa in Windows Secrets latest newsletter. Thank you to Fred for this report, as I have been doing just what he has suggested for many years, do not accept any bogas recommendations from unknown sources.
I have just had somewhat of a similar experience this evening just before downloading Fred’s report . . . my MSC (Microsoft’s Security Client version 2 of MSE) and it could not restart, title bar was RED and the restart button was also RED and could not be restarted by that button. I went into MSC Settings tab and to Real-time protection and unchecked the box for Turn-on real-time protection (recommended) and saved that setting. Then rechecked that box, turning it back on, and it did restart after a few seconds, maybe 20-30 of them. Did an imediate quick scan and all came back clean. Am going to do another with various other AV and malware software I am using on my system.
If I were to wear a hat I would take it off and SALUTE you, Fred Lanaga. I don’t so I will just sing your praises here.
Actually, what you are reporting is entirely different, and may not arise from malware at all. On my Windows XP laptop, MSE frequently fails to start up at Windows boot. The issue with me is that if the boot process takes too long (due to a slow-loading driver or too many Startup Items) MSE will simply time out. It can then take a long time to restart the MSE Service (called MSC in your Startups List). Completely different issue.
-- rc primak
Fred,
[INDENT][snip from first dialog box]
The system will perform a fast and free check your PC for malicious programs.
[/INDENT]To me the telltale sign was the last sentence of the first dialog box because of, not only, like you said, its incorrect grammar, but also the fact that it used the word “free”.
Excellent Article,
Randy
Fred,
Long time reader, first time writing.
With regards to your very excellent article on the LizMoon virus, I wouldtake exception to one piece of advice. I advise my clients to NEVER touch ANYselectable object in a suspect window. The reason being that any object(including the X to close) does what it does because it is actually running asmall program.
One of the most common that I am running into is a modification of the”X” that causes your installed security application(s) to loseinternal communication between the search engine module and the databasemodule. The search engine continues to operate normally (thus no error messagefrom the Security Center), but the database can’t hear it (although it is stillloaded and being updated), and thus can’t tell it to stop.
Use of Ctrl+Alt+Del makes perfect sense to us old guys who started withcomputers back in the days before we had mice . . . but is WAY too geeky forthe next couple of generations who grew up with a mouse in their hand. Toogeeky translates into “they won’t remember it when the time comes”,and thus I ALWAYS recommend that they very carefully remove the cursor from thesuspect window, go down to the TaskBar, right click, and select Task Manager(or Select Task Manager).
This works in all versions of windows and does not further confuse the usersof Vista and Windows 7 by giving them the extra window. Once there, I instructthem to select the Applications tab if it is not already selected, and locatethe suspect window based on its Title Bar information, select it, and then justclick on the End Task button.
For your readers that might benefit from a more complete set ofinstructions, they are welcome to go to http://www.1stComputerTechnologies.com/newsand copy my article. They have my permission to copy the article (prints out toabout 2.6 pages) so that they can share it with their friends and/or clients.
Gary R Hill
1st Computer Technologies, Inc.
Zephyrhills FL
Hi b1rd, and welcome to the Lounge!
Evidently, the “LizaMoon” can be dealt with as Fred described, by clicking the red X in the dialog box. However, there are numerous iterations of this class of malware also known as “scareware”, and in some variants, clicking the red X does result in an infection. In questioning clients who have brought machines to me to clean, I have found that most of them did click the red X on the dialog box, and that is when they found their machine extremely infected.
My policy is as stated in my post# 38 above. I advise everyone to never click either on the scareware page or anywhere on any visible browser page after the scareware popup appears, but to bring up Task Manager and kill the current browser session. Those who have followed that practice have not been back for more malware cleaning.
…but to bring up Task Manager and kill the current browser session
Thanks, that’s been my practice too.
In fact, this popped up on my personal computer just last week. Pretty impressive UI, however I was already familiar with this, and I have two internal hard drives, which this one failed to imitate.
I might add that this was the initial page that showed up, unlike what Fred Langa had, so I’m guessing it’s a different variation. This was an actual screen shot I took prior to shutting down the browser.
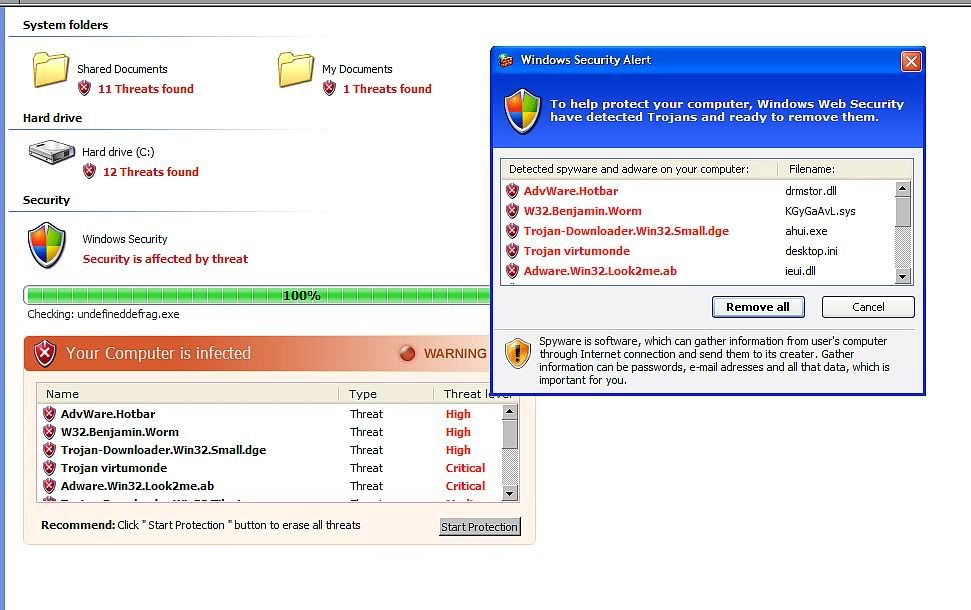
I remove a couple of these rogues every week. I’ve learned a couple of tricks.
1st: either close the dialog box(es) with CRTL-ALT-DEL and the task manager or right click them on the task bar and close them that way.
2nd. Some variants block MalwareBytes. When you download the program (I get it from Download.com, it is always in the top 10) rename it to IEXPLORE.EXE when you save it to your desktop. It will now install, but be sure to uncheck the update and run boxes near the end of the install sequence. Then, with Windows explorer, navigate to Program FilesMalwareBytes and change the name of MBAM.exe to Explore.exe. Then, you can run it with a double click, right from Windows Explorer. Now, you can update it and do a full scan, and it will get most of the critters. I usually follow up with a scan with SuperantispywareFree (also from Download.com) and then Combofix if the machine still doesn’t “feel” right. Please read the ENTIRE tutorial for Combofix and use it at your own risk. It does not play well with AVG. You will have to uninstall AVG to get Combofix to run.
Thanks again Bird.. I downloaded super anti spyware to my flash drive — via another computer — started my computer in safe mode and ran restore. I restored to the day before. All seemed well. so ran super antispy and it unearthed 7 nasties. Have since been running other scanners but have not found anything else. I learnt from the last time not to exit by clicking X I also pulled out the wifi and disconnected from the internet. So thanks again Cheers Damer Farrell
Originally Posted by Dammer
Have since been running other scanners but have not found anything else.
If things seem fine, and if you don’t have already it, this might be a good time to download MalwareBytes and do a direct install to the computer / update and do full scan. I think these two programs that I mentioned are the only two free ones, that I’m aware of that rids this thing.
Also, you did a system restore it sounds like. I just wonder if any of these variations include a time bomb, which simply means set to trigger on a certain date. I doubt it at this time, as I’ve never ready anything about that as of yet, however I did have a program that did that.
Anyhow, glad to hear it appears you got things fixed. This one can be a pain to work with.
I would seriously look at Paragon Back-up & recovery 2011 Free .It’s free and when things get really bad, it might be a good way to get things back to normal. Again, I’ve only made archives, never a restore, as I’m a big believer in Acronis TrueImage, which has saved my several times.
b1rd
Great info on this nasty program. My wife had the same experience with one of the older fake anti-bad guy programs, in that she clicked the red X to close the warning only to find the bad guy got in anyway. Next time it happened she called me and I tried most of the tricks to prevent installation. She asked if we could just power down manually (5 second power button hold) and this solved the problem. Works if you do not have unsaved work that you care about.
After clicking the Red X I was fortunate to have Taskmanager open and I noticed an explosion of numerically titled .exe processes launching. I spent several minutes closing the processes, then did a search on the filename and found it in my browser temp files. I deleted it, but it also corrupted my registry and regedit would not allow me to delete the entries – telling me I did not have permission. I had to run everything using the right-click Run As option.
I tried several antivirus tools in addition to my normal VIPRE without them finding anything.
I finally found a free Registry repair tool that removed the corrupted entries (Free Window Registry Repair) from CNET. It did the job and now I am back to normal.
Next time something like that appears, I will go directly to Taskmanager and close the IE process, then delete all of my temporary files by hand. In addition, I create a restore after every software installation.
After clicking the Red X I was fortunate to have Taskmanager open and I noticed an explosion of numerically titled .exe processes launching. I spent several minutes closing the processes, then did a search on the filename and found it in my browser temp files. I deleted it, but it also corrupted my registry and regedit would not allow me to delete the entries – telling me I did not have permission. I had to run everything using the right-click Run As option.
I tried several antivirus tools in addition to my normal VIPRE without them finding anything.
I finally found a free Registry repair tool that removed the corrupted entries (Free Window Registry Repair) from CNET. It did the job and now I am back to normal.
Next time something like that appears, I will go directly to Taskmanager and close the IE process, then delete all of my temporary files by hand. In addition, I create a restore after every software installation.
For getting rid of the browser Temporary Files, CCleaner in Safe mode might be an option. Then again, if you do not boot the hard drive at all, but run a Linux Live CD instead, manually deleting the Temporary Files from the now non-active Windows hard drive might be safer.
-- rc primak
Hi all
I had this Malware come up last month on a computer that I maintain and was able to remove it with MalwareBytes. A day or so later I noticed that Windows Update would not work. After testing and researching the issue I found two or three Windows Update files were missing and a registry problem prevented the updates. Microsoft had KB articles helping with the issue. Luckily there was an error message in Windows Update that helped with the investigation. I assume that the broken updating issue was related to the malware, since there were no other noted virus attacks.
2 hours to troubleshoot and clean up the malware (not incl travel time)
3 more hours researching and fixing Windows Update issue (not incl travel time)
The computer still misbehaves a bit, so I might not be finished yet!
Thanks to the *amazing* Fred Langa and to the posters at “The Lounge” for helping us to better understand our enemies.
I have seen variants of this scumware that will proceed with its attempt to install even if you press Cancel OR click on the red X.
One of the more amusing things I’ve seen is when the false “Virus Scan” pops up begins scanning my “C:Windows” drive… on my machine that is running Ubuntu 10.10.
The non-amusing thing is the number of friends’ and coworkers’ infected home PCs I’ve had to clean this scumware from.
I just wanted to let you know that one of my friends caught the Security Shield Fake security today and was using an updated Microsoft Security Essentials.
I had put MSE on her computer last month.
She received an Email from a friend with a link to this site
http://www.mollyhughes.co.uk/void.html
It ask you if you are Happy today or sad. When clicked it will bring up another box to install a video driver.
After I cleaned her computer of it (Puts a file i her profile called FVOGE.EXE and a register entry.)
I went to that site on my computer which is running ESET 4.0, It would not even display the page, saying a trojan was enbedded.
yet MSE allowed me to enter using her computer and I went as far as clicking on the Driver it wanted to download, but I ended the task via task mgr and scanned two times with Malwarebytes as well as MSE and nothing was there.
Bottom line is this? I believe ESET 4.0 is much better than MSE.
Bill
I enjoyed Fred’s article on his LizaMoon infection. It was deja vu all over again.
I, too, met LizaMoon in the wild. Like Fred, I thought I would have fun doing battle with this (obvious) malware. Unfortunately, my skill set is inferior to Fred’s.
Long story short; I ended up reformatting my C drive (other factors also contributed to this decision).
Hats off to Fred for this amusing (and informative) article.
To summarize:
1. No anti-malware product will be 100% effective 100% of the time.
2. A product rated as #1 today maybe #3 or #7 tomorrow, depending on who does the review.
3. User education (IMHO) is more important than blindly trusting installed security products.
4. Once infected, you can never be 100% sure that all traces of the infection have been removed.
5. The only way to know all traces (of the infection) have been removed is to install a known clean OS, programs, etc.
If someone has a choice between:
(a) reformatting a HD, reinstalling everything, and then tweaking the computer to get it back to where it was just before the infection (a process that can take many hours if not days), or
(b) using a known clean system image from say, a week ago, updating the OS and installed programs and apps, and being back up and running in about an hour or less,
why would anyone NOT use the system image option? Many stores and internet sites are selling 2TB external USB hard drives for about $100. Too much money or storage space? How about a 500GB external for around $50? Can’t afford the imaging software, you say? Windows 7 provides a free imaging tool that does a more than adequate job. Want some extra bells and whistles not provided by 7? Use Macrium Reflect (free) or Paragon Backup & Recovery 2011 (free).
Stop blaming the anti-malware products and take ownership for your own computer safety. :;):
I cannot recall the name of the virus but I have heard more than once on other computing forums that there was a fake security software malware scam similar to this that actually activated by clicking on the red X to close the dialogue box, people did get infected in this way. Now, whether that is down to insufficient security on their PC or whether the virus could bypass that I have no idea, I’m no expert, but I thought the warning was worth giving – better to close the whole browser instead, to be absolutely sure I would kill it using Process Lasso or Anvir Task Manager myself ;o)

Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.
