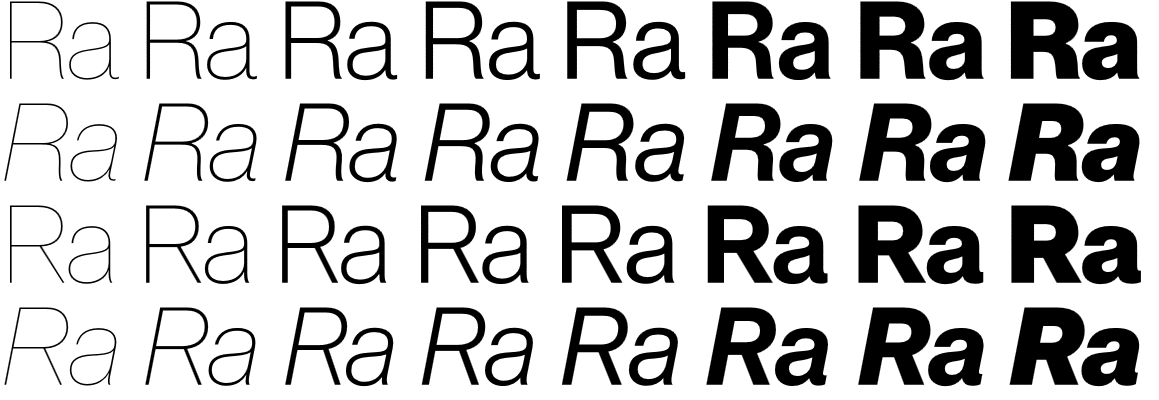There are 212 entries in the Windows Update Catalog for July. Two major issues affecting all versions of Windows have been addressed by Microsoft, alo
[See the full post at: July 2019 Patch Tuesday has arrived]

|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
-
July 2019 Patch Tuesday has arrived
Home » Forums » Newsletter and Homepage topics » July 2019 Patch Tuesday has arrived
- This topic has 98 replies, 26 voices, and was last updated 5 years, 8 months ago by
anonymous.
Tags: July 2019 Black Tuesday
AuthorTopicViewing 33 reply threadsAuthorReplies-
PKCano
ManagerJuly 9, 2019 at 12:20 pm #1872633The 2019-07 Security-only Update and IE11 Cumulative Update have been added to AKB2000003 for Group B patchers (and anyone else who needs them).
NOTE: The links in AKB2000003 are direct download links to the MS Update Catalog.
A reminder for those still on Windows 7 and/or Server 2008: SHA-2 Code Signing also becomes mandatory in July. You will also need to download KB4474419 (the SHA-2 update) and the Servicing Stack KB4490628 if they have not been previously installed.
There is also a new Servicing Stack Update for Win 8.1 KB4504418
-
T
AskWoody LoungerJuly 9, 2019 at 4:16 pm #1872790I might be misreading things but the code signing support page seems to be saying that the SHA-2 code signing and servicing stack updates (KB4474419 & KB4490628) will be mandatory from august onwards not july. For windows 7 anyway. I just did an update check and i was offered the monthly rollups for july, i assumed if i didn’t have either of those updates installed then i wouldn’t be offered it. Currently i only have the servicing stack update installed.
-
PKCano
ManagerJuly 9, 2019 at 4:52 pm #1872803Microsoft’s pages on SHA-2 say:
Any devices without SHA-2 support will not be offered Windows updates after July 2019.
It would seem making it required with the July patches is a better option than wondering why Windows Update doesn’t work in August.
Although there will be those that decide to wait and come begging for help when the August patching comes around and they have no updates.
-
anonymous
GuestJuly 9, 2019 at 12:47 pm #1872663Correction: SHA-2 Code Signing becomes mandatory for Windows Server 2008 this month. For Windows 7 and Windows Server 2008 it will be mandatory only next month.
-
T
AskWoody Lounger
b
AskWoody_MVPJuly 9, 2019 at 12:55 pm #1872671Installed:
KB4507453 2019-07 Cumulative Update for Windows 10 Version 1903 for x64-based Systems (OS Build 18362.239)
KB4506991 2019-07 Cumulative Update for .NET Framework 3.5, 4.8 for Windows 10 Version 1903 for x64
KB4509096 2019-07 Servicing Stack Update for Windows 10 Version 1903 for x64-based Systems
No issues.
1 user thanked author for this post.
Alex5723
AskWoody Plus-
b
AskWoody_MVP -
Alex5723
AskWoody Plus -
b
AskWoody_MVPJuly 9, 2019 at 1:37 pm #1872709They were holes until today and are holes until end of deferral days.
Both? The choice is ours.
The fact remains. Windows 10 is less secure than Windows 7.
That’s no fact. You can’t judge security by the number of patches not issued for an OS which hasn’t been developed for 4.5 years.
Windows 10 vs Windows 7: Microsoft’s newer OS is almost ‘twice as secure’
-
Seff
AskWoody PlusJuly 9, 2019 at 2:06 pm #1872726You can judge security by the number of actual attacks that occur in the wild, as opposed to the speculative potential for theoretical attacks. On that basis both Windows 7 and 10 seem pretty reliable.
Some of that may be down to the protective measures applied by MS through updates, but the positive experience of those who abandoned those measures some time ago on Windows 7 suggests we shouldn’t apply too much credence to the importance of those measures – at least in respect of Windows 7 as there’s no corresponding experience to report on Windows 10 although there’s no reason to suppose it would be any different if there were.
-
b
AskWoody_MVPJuly 9, 2019 at 3:30 pm #1872775You can judge security by the number of actual attacks that occur in the wild, as opposed to the speculative potential for theoretical attacks. On that basis both Windows 7 and 10 seem pretty reliable.
Devices that use Windows 10 are at least twice as secure as those running Windows 7
-
-
-
warrenrumak
AskWoody LoungerJuly 10, 2019 at 4:30 pm #1873688Ehhh, you’re exaggerating. Nearly 100% of the delta between this month’s Windows 7 and Windows 10 patch count is down to a single root issue.
The reality of what happened here is pretty interesting. Windows 10 1709 included new support for OpenType Variable Fonts. This new standard allows for setting any arbitrary level of bold-ness, not just “bold” and “normal”. Like this:
Adobe has an open-source library on GitHub for interpreting this new type of font. Microsoft decided to incorporate this library into DirectWrite. Google Project Zero investigated this library and discovered it does almost no error checking at all when loading these fonts from disk. A rookie mistake — as we’ve come to expect from Adobe, if the number of Flash vulnerabilities over the years has been any indication.
Anyways, as a result, DirectWrite’s font loading inherited a lot of vulnerabilities caused by maliciously-crafted Adobe OpenType font files. According to Google, the vulnerability can only be exploited when someone tries to print a file containing a malicious OpenType font file via Edge, or by using “Microsoft Print to PDF”. Just looking at it in the browser is apparently safe.
Because exploiting the vulnerability requires printing a document from unproven origin, it’s been rated as a low security threat.
So, yes, sure, Windows 7 doesn’t have those vulnerabilities…. but that’s ONLY because it is 9 years behind in its font standards support!
-
This reply was modified 5 years, 9 months ago by
warrenrumak.
-
This reply was modified 5 years, 9 months ago by
warrenrumak.
1 user thanked author for this post.
abbodi86
AskWoody_MVP-
Alex5723
AskWoody Plus -
Microfix
AskWoody MVPJuly 9, 2019 at 1:57 pm #1872723yes, and adobe released flash updates today!
Adobe Flash Player 32.0.0.223 but none from MS for W8/W10..strangeJuly 9, 2019
In today’s scheduled release, we’ve updated Flash Player with important bug fixes.from: https://helpx.adobe.com/flash-player/release-note/fp_32_air_32_release_notes.html
Windows - commercial by definition and now function...1 user thanked author for this post.
-
EP
AskWoody_MVPJuly 9, 2019 at 5:23 pm #1872812because these new Flash updates are non-security updates and do not address any new security issues
MS may release the Win8.x & Win10 versions of Flash 32.0.0.223 between Wed. and Fri (or whenever they’re ready this week)
-
abbodi86
AskWoody_MVP -
EP
AskWoody_MVPJuly 11, 2019 at 12:40 pm #1874094that may only apply to the Win8.1 version of KB4462930, abbodi.
The Win10 versions of KB4462930 (as well as the Win8 embedded/server 2012 r0 version) are properly superseded by newer flash updates and attempting to install KB4462930 produces “not applicable” message when newer flash updates were installed.
-
abbodi86
AskWoody_MVPJuly 11, 2019 at 1:57 pm #1874120I’m pretty sure 9200 builds have the same issue
yes, Win 10 don’t have the issue because the update is declared superseded via CBS (flash component version didn’t change like Win 8.1)nevertheless, this does not change the fact that this update should be added to Flash supersedence chain, or expired
just check the details for any OS, the update is rogue without any relation
https://www.catalog.update.microsoft.com/Search.aspx?q=KB4462930 -
EP
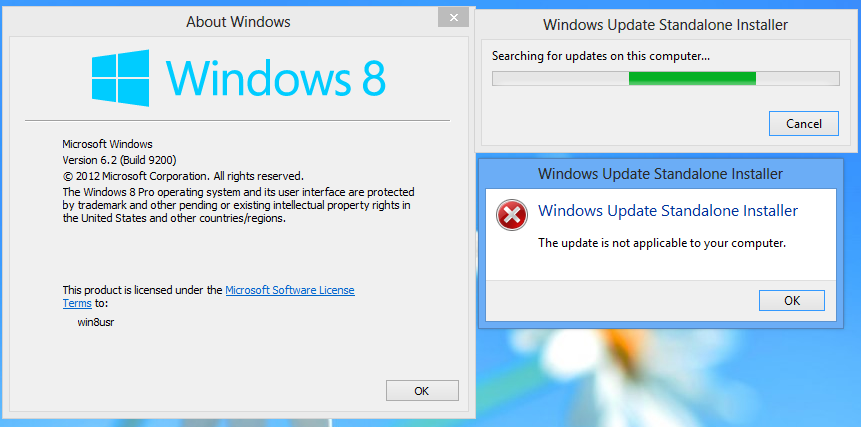
AskWoody_MVPAugust 1, 2019 at 12:23 pm #1900434NO abbodi86!
I manually ran the Win8.0 version of KB4462930 on a Win8.0 Pro 9200 machine while it had a newer flash update already installed like KB4503308 and the KB4462930 patch told me that “the update is not applicable to your computer.” I’ve done a test on this to confirm that (at least that occurred with Win8.0 Home/Pro/Enterprise – don’t know if the result will be the same on Win8 embedded or Server 2012) – so 4462930 on Win8.0 IS properly superseded by newer flash updates
-
This reply was modified 5 years, 8 months ago by
EP.
-
This reply was modified 5 years, 8 months ago by
EP.
1 user thanked author for this post.
-
This reply was modified 5 years, 8 months ago by
-
EP
AskWoody_MVPAugust 1, 2019 at 1:36 pm #1900465and I have recently gotten proof of this
double-clicking on the KB4462930 MSU W8.0 file when a Nov. 2018 (KB4467694) or higher flash update is installed (recent one of course is KB4503308 from Jun. 2019), results in this under Win8.0:
therefore KB4462930 under Win8.0 is truly superseded by newer flash updates, unless you can prove otherwise and do actual testing on a Win8.0 machine, abbodi.
-
-
-
geekdom
AskWoody_MVPJuly 9, 2019 at 2:20 pm #1872733Beta Test Report Windows 7 x64 Updates
– Windows Malicious Software Removal Tool x64 – July 2019 (KB890830)
– Security and Quality Rollup for .NET Framework 3.5.1, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2, 4.8 for Windows 7 SP1 and Server 2008 R2 SP1 (KB4507420)Both updates installed without error and the system rebooted without error.
Checked again for updates.
– July 2019 Security Monthly Quality Rollup Windows7 x64 (KB4507449)
This update installed without error and the system rebooted without error.
On permanent hiatus {with backup and coffee}
offline▸ Win10Pro 2004.19041.572 x64 i3-3220 RAM8GB HDD Firefox83.0b3 WindowsDefender
offline▸ Acer TravelMate P215-52 RAM8GB Win11Pro 22H2.22621.1265 x64 i5-10210U SSD Firefox106.0 MicrosoftDefender
online▸ Win11Pro 22H2.22621.1992 x64 i5-9400 RAM16GB HDD Firefox116.0b3 MicrosoftDefenderBarry
AskWoody Loungerabbodi86
AskWoody_MVPJuly 9, 2019 at 3:50 pm #1872779Monthly Rollup for Windows 8.1 (KB4507448) also required two restarts to complete on my machine, no issues
according to CBS.log, this seem to be related to updated IE11 product policy
C:\Windows\System32\spp\tokens\ppdlic\Microsoft-Windows-IE-InternetExplorer-ppdlic.xrm-ms-
abbodi86
AskWoody_MVP -
Microfix
AskWoody MVPJuly 16, 2019 at 2:36 pm #1875831I did encounter a double restart for KB4507448 but don’t do previews unless they fix something that’s busted from patch tuesday’s offerings that affect our systems.
more info on this preview:
https://support.microsoft.com/en-us/help/4507463/july-16-2019-kb4507463-os-build-preview-of-monthly-rollupAbbodii86: have you checked for/noticed any changes in the task scheduler after installing the preview?
Windows - commercial by definition and now function...1 user thanked author for this post.
-
abbodi86
AskWoody_MVP -
Microfix
AskWoody MVPJuly 18, 2019 at 1:04 pm #1876576Abbodi, I’m curious..and perhaps using an old apple slogan ‘think different’
Is there anything to gain/lose by flipped patching..no SMQR (Group A) on patch tuesday, just dotnet/flash etc.. then install the preview a week later on W8.1.? Theoretically, the patch tuesday SMQR should have burning issues fixed in the preview as well as introductory fixes. Pros and cons going in this direction?Windows - commercial by definition and now function...1 user thanked author for this post.
-
abbodi86
AskWoody_MVP
-
-
-
-
PKCano
ManagerJuly 16, 2019 at 3:35 pm #1875841
CraigS26
AskWoody PlusJuly 9, 2019 at 4:29 pm #1872793Installed:
KB4507453 2019-07 Cumulative Update for Windows 10 Version 1903 for x64-based Systems (OS Build 18362.239)
KB4506991 2019-07 Cumulative Update for .NET Framework 3.5, 4.8 for Windows 10 Version 1903 for x64
KB4509096 2019-07 Servicing Stack Update for Windows 10 Version 1903 for x64-based Systems
No issues.
1903 was Same for me; Install time drags but no issue. WU inst’d SSU as I didn’t see it until -b- posted and I looked.
W10 Pro 22H2 / Hm-Stdnt Ofce '16 C2R / Macrium Pd vX / GP=2 + FtrU=Semi-Annual + Feature Defer = 1 + QU = 0
anonymous
GuestJuly 9, 2019 at 7:12 pm #1872865Warning for group B Windows 7 users!
The “July 9, 2019—KB4507456 (Security-only update)” is NOT “security-only” update.
It replaces infamous KB2952664 and contains telemetry. Some details can be found in file information for update 4507456 (keywords: “telemetry”, “diagtrack” and “appraiser”) and under http://www.catalog.update.microsoft.com/ScopedViewInline.aspx?updateid=7cdee6a8-6f30-423e-b02c-3453e14e3a6e (in “Package details”->”This update replaces the following updates” and there is KB2952664 listed).
It doesn’t apply for IA-64-based systems, but applies both x64 and x86-based systems.
-
abbodi86
AskWoody_MVP -
OscarCP
MemberJuly 9, 2019 at 8:05 pm #1872925So should this update be skipped or installed? This appears to pose a dilemma, at least right now. I hope that some weeks from now, by the time we are closer to a green DEFCON, this has been sorted out.
Group B, Windows 7, SP1, x64, with I-7 “sandy bridge” four cores CPU.
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV -
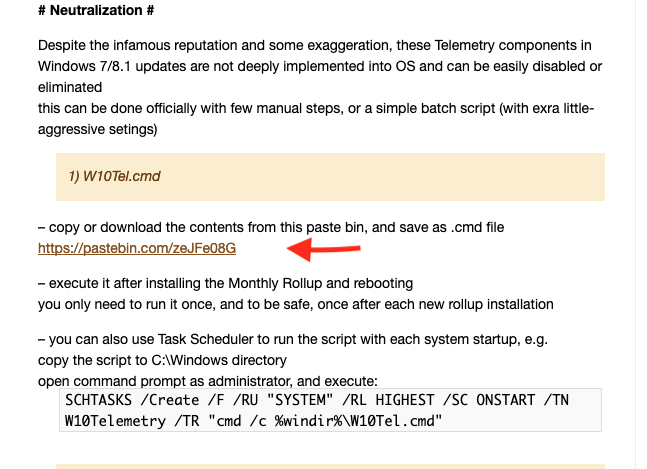
abbodi86
AskWoody_MVPJuly 9, 2019 at 8:17 pm #1872928Disabling (or deleting) these schedule tasks after installation (before reboot) should be enough to turn off the appraiser
\Microsoft\Windows\Application Experience\ProgramDataUpdater
\Microsoft\Windows\Application Experience\Microsoft Compatibility Appraiser
\Microsoft\Windows\Application Experience\AitAgentbut it’s best to wait next month to see if the SO update comes clean
-
This reply was modified 5 years, 9 months ago by
abbodi86.
-
This reply was modified 5 years, 9 months ago by
-
Microfix
AskWoody MVPJuly 10, 2019 at 1:57 am #1873233For those who use the ‘Group B’ (Security Only /SO) method of patching, @abbodi86 has previously posted a great checklist and walkthrough in:
AKB2000012 – Neutralize Telemetry & Sustain Win 7, 8.1 Monthly Rollup Model
looks like this is applicable to both SMQR and SO patching groups henceforth..Windows - commercial by definition and now function...
-
-
anonymous
Guest-
OscarCP
MemberJuly 9, 2019 at 10:41 pm #1873042Anonymous: “… so then what?”
My guess would be to follow abbodi86’s advice ( #1872928 ). If those “Experience” services one would disable accordingly, came back as active during the next install, then the procedure would have to be repeated. Tedious, yes, but this is a tedious issue, so the solution would fit the problem.
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV
woody
ManagerJohnH
AskWoody Plus-
abbodi86
AskWoody_MVPJuly 10, 2019 at 4:13 am #1873305The monthly rollup had been carrying already
the “Unified Telemetry Client” since since October 2016 preview rollup, and the “Compatibility Appraiser” since September 2018 preview rollupsecurity-only update KB4507456 only have the second payload (Appraiser)
1 user thanked author for this post.
-
PKCano
Manager
anonymous
Guest-
PKCano
Manager
anonymous
GuestJuly 10, 2019 at 1:18 am #1873085Rather than waiting until the end of the month like I usually do, I went ahead and updated 3 X64 Win 7 systems: two Ultimate and one Home Premium.
No problems noted – other than MS re-installing the Win 10 comparability stuff (eg: compattel). I anticipated this, so I confirmed the Application Experience tasks were as I had them set: disabled. I checked again before rebooting after the install: yep, still disabled. But, after the reboot I found them enabled again, so I had to disable them yet again. Sheesh.
One thing I noted is win32\compattelrunner.exe is indeed a new version and a slightly larger file size than the previous version (which was installed in Jan 2019). So this tells me MS is still actively developing code for automatically assessing Win 10 compatibility of Win 7 (or 8.1) systems. They REALLY want this service running on all Win 7/8.1 systems.
I can’t help but think this is in preparation for a “Last Chance To Get Win 10 Free” campaign. But, to me, this is so silly. My Win 7 systems are all 6+ years old and not really worth upgrading them to 10. I’m going to replace the systems in the next 12-24 months & when I do THAT’S when I’ll put Win 10 on some/all of them.
I just wish MS would just implement a simple one time pop-up that asks:
“Hey, we’ve been inspecting every last bit of your system (every time you boot) and noticed it’s pretty old. It’s probably not ideal for Win 10. Select one of these: 1) I plan to replace this system with new suitable hardware & install Win 10 on it. 2) I don’t intend to install Win 10 on this old system. 3) Yep, I plan to attempt installing Win 10 on this antique.”
For responses 1 & 2, there’s no need for MS to bother constantly scanning your system over and over and over again for potential Win 10 compatibility.
I’m half serious here, but I can imagine calculating the amount of power being wasted by compattelrunner.exe unnecessarily loading up the millions of Win 7/8 systems every time it runs. A few watts per system – multiplied by millions – probably adds up to a pretty big number…
Geoff King
AskWoody LoungerJuly 10, 2019 at 1:24 am #1873229On one machine, .Net Framework failed to install with the comment Retry.
Wonder if that’s a sneaky way for Microsoft to make you a ” Seeker ” !
-
This reply was modified 5 years, 9 months ago by
Geoff King.
JohnH
AskWoody PlusJuly 10, 2019 at 2:36 am #1873240Call me a knowledgeable user, not an expert by any means, but what I don’t get is why a non-security Office 2016 update of 248.4MB is needed to fix what seems a remarkably straightforward issue (see uploaded screen grab). In fact, it seems that almost every month there is an Office 2016 patch that exceeds 200MB. The fact that I’m even posing this issue demonstrates how comprehensively MS has shattered my confidence over the years by including sneaky s*** (that’s the tech term, right?) in the update channel.
MVP Edit: please refrain from posting bad language as per lounge rules.
-
abbodi86
AskWoody_MVPJuly 10, 2019 at 4:23 am #18733121- Since Office 2013 SP1, Office 2013 and Office 2016 patches are cumulative and multilingual
that’s why the size is big, and gets bigger (because it cover more and more different-version binaris)
2- Traditional MSI technology don’t support delta-express delivery mechanism, so you are committed to download and install the whole patch
3- Microsoft had forsaken MSI technology in the favor of Click To Run
that’s why there will be no more Service Packs -
mn–
AskWoody LoungerJuly 15, 2019 at 2:07 am #18750761- Since Office 2013 SP1, Office 2013 and Office 2016 patches are cumulative and multilingual
that’s why the size is big, and gets bigger (because it cover more and more different-version binaris)
… and this kind of thing really isn’t sustainable in the long term.
Oh well, product management choice at MS to do it that way instead of one of the better ways.
-
gborn
AskWoody_MVPJuly 10, 2019 at 5:39 am #1873340Got some messages, that cumulative Update KB4507453 for Windows 10 V1903 is causing a reboot loop – the user receives a notification, the the machine need to reboot in times, if it isn’t in use, to sucessful install this update. But this notification is indefinitely.
One user has cured it with shutting down the machine via start menu command and was able to solve that issue. Don’t know, how widespread this issue is (I found a hand full German users affected)
German article: Windows 10 V1903: Update KB4507453 mit Reboot-Schleife
Ex Microsoft Windows (Insider) MVP, Microsoft Answers Community Moderator, Blogger, Book author
https://www.borncity.com/win/
anonymous
Guestanonymous
GuestJuly 10, 2019 at 10:09 am #1873471KB4504418 service stack update for Windows 8.1 showed up after all of the July updates were installed. When I went to install the service stack update it said I needed to be administrator to install, which I already am. I’ve never had this issue before – don’t remember installing service stack updated previously either though. I did successfully install manually through the Microsoft website.
-
PKCano
ManagerJuly 10, 2019 at 10:13 am #1873479Servicing Stack Updates have to be installed exclusively (by themselves). They will not show up in the update queue as long as there is any pending update (checked or unchecked). So that’s why it showed up after you installed everything else. Because the update queue is often never emptied completely, some people miss the SSUs completely.
BTW Win8.1 hasn’t had a new Servicing Stack update in a long time.
-
anonymous
GuestJuly 10, 2019 at 10:31 am #1873494Thank you for the information – I really appreciate it. Any idea on why Windows Update would not let me install stating I need to be an Administrator even when I already am an Administrator? I’ve never had this issue previously. Just previous to trying to install the servicing stack I was able to successfully update all the other July updates in Windows Update.
Wondering if I need to run DISM RestoreHealth or Scannow (haven’t had any other issues though) or maybe the issue with KB4504418 is on Microsoft’s end (haven’t seen anything else about this online).
Thank you again for your help.
-
PKCano
Manager -
anonymous
Guest
-
-
-
abbodi86
AskWoody_MVP -
anonymous
GuestJuly 10, 2019 at 4:21 pm #1873685
-
-
walker
AskWoody LoungerJuly 10, 2019 at 2:05 pm #1873611@PKCano: I have encountered an update that I have been unable to find in “hidden updates” (as that sometimes occurs). It was referenced in a group of updates otherwise noted from April, and installed at that time. Those are KB 4474419 and KB4490648. The one which I have not been able to locate (this happens sometimes when attempting to find “hidden patches”) is KB 4484071
The one I cannot locate (as being installed or hidden) is: KB 4484071. Do you have any information on that one?
I also noted that a KB 4503392 showing a JULY date was installed on July 7th. I do not recall ever installing that one. Also I cannot locate any information on that one. It seems to be getting “crazier and crazier”. Thank you for any information you may be able to provide. Your assistance, as always, is most sincerely appreciated.
-
PKCano
ManagerJuly 10, 2019 at 2:24 pm #1873626KB4484071 is for Windows Server 2008 – not for you
I do not have the information on the other one at the momentUpdate: If the second patch is KB4503292 (instead of 392), that is the June Rollup for Win7, and you should have it installed.
-
This reply was modified 5 years, 9 months ago by
PKCano.
-
This reply was modified 5 years, 9 months ago by
-
walker
AskWoody LoungerJuly 10, 2019 at 2:33 pm #1873630@PKCano: Thank you so much PK! You are a “miracle worker” when it comes to finding out “everything there is to know”. At least I can put that one to rest, and that helps considerably, as I like to keep everything “up to date” as much as possible.
Know how busy you must be fielding all of the questions which are thrown at you so rapidly. My admiration for your abilities continues to increase “ad finitum”. Once again, “Thank you so very, very much”.
-
walker
AskWoody LoungerJuly 10, 2019 at 7:49 pm #1873754@PKCano: My most sincere apology. The KB number IS, as you noted, KB4503292. I made a typo. You are CORRECT, and it is a June update. Installed in July as one of the June updates. I am having more and more problems with my vision, and will strive to not make such an error again.
THANK YOU, THANK YOU, THANK YOU!!!
Geo
AskWoody PlusJuly 10, 2019 at 2:56 pm #1873659Group A, Win 7X64, Home Premium, security essentials, AMD. Took the roll up and removal tool. said Net Framework not needed. Everything OK, no slow down. Only used for email,internet and printing.
-
This reply was modified 5 years, 9 months ago by
Geo.
1 user thanked author for this post.
ashfan212
AskWoody LoungerJuly 10, 2019 at 5:07 pm #1873702Windows 7 x64 Home Premium Group A.
All of this month’s updates installed successfully followed by a successful reboot. However, I experienced severe issues the first time that I started my computer after the successful reboot and shutdown. I am hoping that someone may be able to offer guidance.
On this next startup, I received a SYSTEM EVENT NOTIFICATION SERVICE error. Visually, the taskbar graphics no longer appeared in their usual aero theme. Out of desperation, I ran the command NETSH WINSOCK RESET from an elevated command prompt. I had difficulties rebooting my computer after successfully running that command as EXPLORER.EXE would not terminate neither on its own nor when I clicked on the button to force the termination of that process. After a hard shutdown and going through the same process a couple of times, I was able to reboot my computer and, as far as I can tell, the SENS message/error disappeared and my taskbar graphics reverted back to normal.
I have no idea if my running the NETSH WINSOCK RESET command resolved the problem or whether the errors went away fortuitously after executing a few reboots. I also don’t know if what I experienced was related to the Event Viewer issues that this month’s rollup was designed to fix. For the record, I experienced no issues with the June rollup nor did I install the subsequent preview rollup. I never use the Event Viewer and therefore never had experienced any issues pertaining to Custom Views.
If anyone understands what causes these SENS errors in the first place and can suggest a better way to avoid/resolve such issues in the future, I would be most appreciative.
1 user thanked author for this post.
EP
AskWoody_MVPJuly 11, 2019 at 12:45 pm #1874096about KB4507456 security-only update containing the telemetry stuff from KB2952664 – now it’s being mentioned on Softpedia news:
1 user thanked author for this post.
anonymous
GuestJuly 11, 2019 at 12:54 pm #1874098Well, it’s Patch Tuesday +2 and no mention of the 2010 Excel/Office/Outlook patches for Windows 7 x64. They are KB4464572, KB4462224, and KB4475509, respectively. With only six months left for Window 7 support, I am taking all updates MS wants to give me. I envision a crunch at midnight on January 20, 2020. I want to be up-to-date when Windows 7 goes silent so I can continue to use it.
I have read all the doom and gloom warnings, but I have free Norton provided by Concast so I don’t think I have anything to worry about. I have gotten all the latest HP drivers for my HP Compaq 6005 Pro SFF. It has an AMD Athlon II X2 B24 3.00 GHz processor with 4GB of RAM. I feel hackers will turn their focus to the dominant OS as they have done in the past. I believe Vista and 7 can be used until the machines give out.
Appreciate any feedback on my assertions and helps to keep Windows 7 viable for years to come. Thanks, Lefty.
-
anonymous
GuestJuly 12, 2019 at 4:13 am #1874262These 3 Office-updates require the release version of Service Pack 2 for Office 2010 installed on the computer. https://support.microsoft.com/en-us/help/2687455/description-of-office-2010-service-pack-2. Maybe you do not have that SP?
-
anonymous
GuestJuly 12, 2019 at 7:58 am #1874285Thanks Nony. Although I do not have SP1 or SP2 for Office 2010, all three of these patches installed successfully. I have tried to install both service packs, but they won’t install. Apparently I don’t need the SPs.
Still looking for tips and tricks to keep Windows 7 running until my rig gives out. Anyone have any ideas? Thanks, Lefty.
-
PKCano
ManagerJuly 12, 2019 at 8:11 am #1874295We have a Forum specifically for that:
Win7 beyond end-of-life.
-
-
ChrisAVWood
AskWoody Plus-
PKCano
ManagerJuly 12, 2019 at 8:09 am #1874293What it means is there has not been enough time to tell yet. And it all depends on which version of Windows you are referring to. There have been some black screen hangs reported on v1903. And there has been telemetry added to Win7 Security-only updates. These among others.
We are on DEFCON 2, which means wait and let someone else be the Guinea pig.
1 user thanked author for this post.
EP
AskWoody_MVPJuly 12, 2019 at 11:37 am #1874342note to woody and Susan: Microsoft now says that the external USB device or memory card (SD) problems for 1903 are fixed as noted on these pages:
https://docs.microsoft.com/en-us/windows/release-information/resolved-issues-windows-10-1903
https://docs.microsoft.com/en-us/windows/release-information/status-windows-10-1903
-
Alex5723
AskWoody PlusJuly 12, 2019 at 1:07 pm #1874380note to woody and Susan: Microsoft now says that the external USB device or memory card (SD) problems for 1903 are fixed as noted on these pages:
https://docs.microsoft.com/en-us/windows/release-information/resolved-issues-windows-10-1903
https://docs.microsoft.com/en-us/windows/release-information/status-windows-10-1903
Microsoft has lifted 3 blocks in 1903 :
Systems with external USB devices and memory cards are no longer blocked from installing Windows 10 version 1903.
The Dolby Atmos and Dolby Access issue is resolved.
The Dynabook Smartphone link app issue is resolved.But added new bugs :
Constant loop of ‘restart’ notice after installing KB4507453
Back screen in Remote Desktop Protocol windows. -
b
AskWoody_MVPJuly 12, 2019 at 2:12 pm #1874402But added new bugs :
Constant loop of ‘restart’ notice after installing KB4507453
Back screen in Remote Desktop Protocol windows.Where are those two documented please?
I don’t see either at https://docs.microsoft.com/en-us/windows/release-information/status-windows-10-1903 or https://support.microsoft.com/en-us/help/4507453
-
b
AskWoody_MVPJuly 12, 2019 at 10:46 pm #1874508I see the RDP black screen now at https://docs.microsoft.com/en-us/windows/release-information/status-windows-10-1903#534msgdesc
Where’s the restart loop?
-
Alex5723
AskWoody PlusJuly 13, 2019 at 12:52 am #1874525I see the RDP black screen now at https://docs.microsoft.com/en-us/windows/release-information/status-windows-10-1903#534msgdesc
Where’s the restart loop?
Microsoft has not acknowledged the issue yet :
1 user thanked author for this post.
-
-
-
Microfix
AskWoody MVPJuly 12, 2019 at 12:35 pm #1874376Guenni over at borncity reports :
A brief warning for administrators using Windows Server 2012 to deploy via SCCM. The June 2019 update KB4503276 causes trouble because it prevents PXE booting (WDS). Microsoft has now confirmed the problem…
Windows - commercial by definition and now function...MiggieNH
AskWoody LoungerJuly 12, 2019 at 2:18 pm #1874399KB4504418 bug: Causes Windows 8.1 computer to no longer be able to print to Word or Outlook. This problem occurred in our case with Office 2016, but it may affect other versions, and other Office programs. After MUCH troubleshooting, the fix was to remove and hide that patch. Printing then started working immediately.
1 user thanked author for this post.
-
Microfix
AskWoody MVP
anonymous
GuestJuly 12, 2019 at 3:13 pm #1874412Windows 7 x64 Pro, “Group B” (I guess), with security-only Windows updates, on an old ThinkPad T510 with integrated graphics and Internet Explorer “turned off” in Programs and Features.
I stopped using Windows Update around October 2016 and have been using WSUS Offline Update since January 2017 to install security-only Windows updates (along with updates to C++, .NET, Silverlight, Remote Desktop, and Defender). It’s been working pretty well. Belarc Advisor routinely gives me a clean bill of health afterwards, and WPD [Windows Privacy Dashboard] catches and disables any telemetry Microsoft sneaks in (which, if you’ve read earlier comments and other posts on this site, you’ll know they in fact did this month — the second time I’ve caught them at it).
Anyway, this month I updated a bit earlier than I normally do, because I’d read reports that at least one vulnerability was already being exploited in the wild. (Ditto for last month or the month before, because of the new WannCry/Petya/NotPetya-type worm scare.) Normally I wait several days to a week after each Patch Tuesday for major bugs to shake out and get reported on the Net, but I shorten that to two or three days when something scary is out there. I’m a little more cautious about security vulnerabilities and a little less cautious about buggy updates than Woody seems to be, maybe because I always have a fresh pre-update clone drive to fall back on, but I still never update immediately.
All seemed to be well after I installed this month’s updates, at least initially, but later in the day, I got a BSOD — something I think has happened only once, possibly twice before on this particular computer. I ran Startup Repair and for good measure threw in a system file check (no integrity violations found), a disk check (no file system problems found), and a memory diagnostic (no memory problems found). Anyway, the computer rebooted okay more than once and has been running okay for several hours since then … knock on wood.
I pulled up the minidump file for the BSOD in Nirsoft’s BlueScreenView utility (because who wants to wade through Windows 7’s Event Viewer?). Apparently, the blue screen was the result of a DRIVER_IRQL_NOT_LESS_OR_EQUAL error caused by NETw5s64.sys (the Intel® Wireless WiFi Link Driver). Intel’s Driver & Support Assistant says all of my Intel software/drivers are up to date, and … that just about exhausts my computer-diagnostics-and-repair-fu. Was the blue screen a random fluke? Should I manually reinstall my Intel WiFi drivers? Or is one of the new Windows updates doing something … “untoward”?
Time will tell, and if one of the updates does turn out to be problematic, I can just swap in a pre-update clone of my system drive. I’ve been maintaining pre-update clones of my system drive (and syncing my data files and select configuration files to them in close to real time) since the early days of Windows XP. With XP, I was more concerned about catastrophic hard-drive failures — and with good reason, having experienced the IBM “DeathStar” and WD “Click of Death” debacles first-hand, more than once. (Hey! They were highly rated drives, and I got a bunch of them before anyone knew of the risk!) With 7, it’s borkogenic updates I’m worried about, especially since roughly spring of 2015. Nothing beats being able to swap in an unborked system drive that’s mostly up to date (apart from Windows and applications) and being able to continue computing on your merry way.
Anyway, I’ll be curious to see whether any other reports of post-update blue screens make their way to the Web … and, of course, curious to see whether I blue-screen again.
1 user thanked author for this post.
gtd12345
AskWoody Plusanonymous
GuestJuly 13, 2019 at 3:58 pm #1874691Can confirm BSOD on restart with AVG free and Win 7 Pro. Installed the two or three updates seconds after they appeared two days ago. Lenovo W541. Also BSOD on startup in Safe Mode. Also fail in “last known good configuration”. ALL restore points missing! Had to reinstall Windows. Two days lost reinstalling all programs, files and settings from backup.
-
anonymous
Guest
Sportsman
AskWoody LoungerJuly 14, 2019 at 8:49 pm #1875008Windows 10 1809 with metered connection and WD here. I chose to install July updates before they were foisted on me 🙂 All went well except that cumulative update KB4507469 downloaded very slowly and then failed to install. Windows automatically retried it; it took about 20 min. to install that time but was successful. After two reboots, no problems observed so far.
Windows 10 Home 64-bit
PKCano
ManagerJuly 15, 2019 at 6:44 am #1875154For those of you using @abbodi86 ‘s script to manage telemetry in Win7/8.1, please note that the script has been modified. Please download a fresh copy from AKB2000012.
-
walker
AskWoody LoungerJuly 19, 2019 at 3:04 pm #1877006@PKCano: When I click on the “latest update”, I cannot locate the latest version. I hope you can direct me to the correct website so I can access it. This is the what I am seeing, however unable to access it. It says “Please download a fresh copy from AKB2000012
I don’t know where to locate it. My apologies for being unable to find it.Your help would be very much appreciated, as always. Thank you.
-
PKCano
Manager -
walker
AskWoody LoungerJuly 19, 2019 at 3:44 pm #1877023@PKCano: I am way over my head with what this action involves. I only have the updates which are indicated for Win 7, x64, (Win Premium) Group A. I don’t have most or none, of the other items which are referenced in the dialogue so it appears that this is something which I may not need. Thank you for the information you have provided, although I am unable to use it. You are such an advanced expert with computers, it is amazing, as well as admirable. Thank you for taking the time to send the information. I sincerely appreciate all of the work, and assistance you provide for all of the members of Woody’s. Thank you once again for all of the help you have provided for us.
-
-
anonymous
GuestJuly 19, 2019 at 8:41 am #1876895Help……In my Win 7 64 “Windows Update History” KB4507420 shows as installed 21 times since Tuesday….however in the “Uninstall an Update” window it is not present. And now my laptop….an Acer 7750G-9823….a pretty ballsy machine despite it’s age with dual SSD and 4 RAM slots with 8g good memory in each slot…..now in 2 days this laptop is running like it’s feet are stuck in a tar pit.
Any reports of problems with this past Tuesday’s July NET Framework roll up? How do I remove those 21 reported instances of successful install of KB4507420 if in fact it isn’t appearing in the “Uninstall an Update” feature designed to remove whacked out updates?
-
PKCano
ManagerJuly 19, 2019 at 9:03 am #1876900Does the History say “Succeeded” or “Failed”? It the latter, nothing will show up in the installed updates as installed.
+ Set Windows Update to “Never check for updates”
+ If KB4507420 is in the queue, right click on it and choose “Hide”
+ If it is not in the queue, click “Check for updates” and then hide it.
+ Look again under “View installed updates” (lower left in Windows Update) to see if the individual updates in the Rollup bundle are installed (KB4507004 for .Net 3.5.1, KB4507001 for .Net 4.5.2, KB4506997 for .Net 4.6, KB4506994 for .Net 4.8). You won’t find the Rollup’s KB number in the installed updates.
+ Reset Windows Update to check for updates at whatever setting it was originally.1 user thanked author for this post.
anonymous
Guestanonymous
Guest-
EP
AskWoody_MVP
anonymous
GuestAugust 1, 2019 at 2:57 pm #1900502Reporting in:
Dell XPS15 with Win 10 Home v1809 and a metered connection.
I have been away, so switched on and allowed Update to work.
8 various updates came down the pipe along with a large Office 2016 update.
That took just over an hour.
All seemed well until I ran DISM //scanhealth which tells me that the corruption is repairable, and then SFC which reports corruption.
Oh well!
-
anonymous
Guest
Viewing 33 reply threads - This topic has 98 replies, 26 voices, and was last updated 5 years, 8 months ago by
-

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
WinRE KB5057589 fake out
by
Susan Bradley
5 hours, 59 minutes ago -
The April 2025 Windows RE update might show as unsuccessful in Windows Update
by
Susan Bradley
6 hours, 7 minutes ago -
Firefox 137
by
Charlie
8 hours, 50 minutes ago -
Whisky, a popular Wine frontend for Mac gamers, is no more
by
Alex5723
12 hours, 18 minutes ago -
Windows 11 Insider Preview build 26120.3863 (24H2) released to BETA
by
joep517
12 hours, 30 minutes ago -
Windows 11 Insider Preview build 26200.5551 released to DEV
by
joep517
12 hours, 33 minutes ago -
New Windows 11 PC setup — can I start over in the middle to set up a local id?
by
ctRanger
5 hours, 38 minutes ago -
Windows 11 Insider Preview Build 26100.3902 (24H2) released to Release Preview
by
joep517
16 hours, 5 minutes ago -
Oracle kinda-sorta tells customers it was pwned
by
Nibbled To Death By Ducks
22 hours, 6 minutes ago -
Global data centers (AI) are driving a big increase in electricity demand
by
Kathy Stevens
1 day, 8 hours ago -
Office apps read-only for family members
by
b
1 day, 11 hours ago -
Defunct domain for Microsoft account
by
CWBillow
1 day, 7 hours ago -
24H2??
by
CWBillow
22 hours, 5 minutes ago -
W11 23H2 April Updates threw ‘class not registered’
by
WindowsPersister
16 hours, 20 minutes ago -
Master patch listing for April 8th, 2025
by
Susan Bradley
19 minutes ago -
TotalAV safety warning popup
by
Theodore Nicholson
7 hours, 21 minutes ago -
two pages side by side land scape
by
marc
3 days, 8 hours ago -
Deleting obsolete OneNote notebooks
by
afillat
3 days, 10 hours ago -
Word/Outlook 2024 vs Dragon Professional 16
by
Kathy Stevens
2 days, 13 hours ago -
Security Essentials or Defender?
by
MalcolmP
2 days, 16 hours ago -
April 2025 updates out
by
Susan Bradley
1 hour, 38 minutes ago -
Framework to stop selling some PCs in the US due to new tariffs
by
Alex5723
2 days, 9 hours ago -
WARNING about Nvidia driver version 572.83 and 4000/5000 series cards
by
Bob99
2 days ago -
Creating an Index in Word 365
by
CWBillow
3 days, 2 hours ago -
Coming at Word 365 and Table of Contents
by
CWBillow
1 day, 14 hours ago -
Windows 11 Insider Preview Build 22635.5170 (23H2) released to BETA
by
joep517
4 days, 5 hours ago -
Has the Microsoft Account Sharing Problem Been Fixed?
by
jknauth
4 days, 9 hours ago -
W11 24H2 – Susan Bradley
by
G Pickerell
4 days, 11 hours ago -
7 tips to get the most out of Windows 11
by
Alex5723
4 days, 9 hours ago -
Using Office apps with non-Microsoft cloud services
by
Peter Deegan
10 hours, 58 minutes ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.