How can you change permissions?
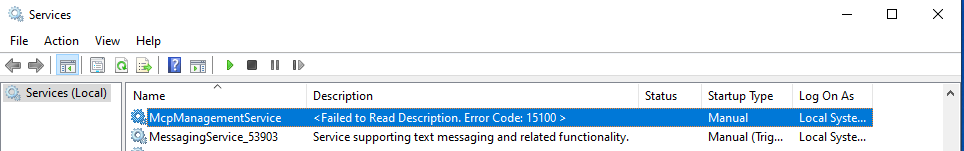
I am facing a strange issue when I install Window 10 & I have tried it in all different ways, I end up with System and Administrators not having any rights on Widows and all its subfolders including Windows\Systrom32. This causes a lot of problems with services such as DNS client and McpManagerService as well as others.
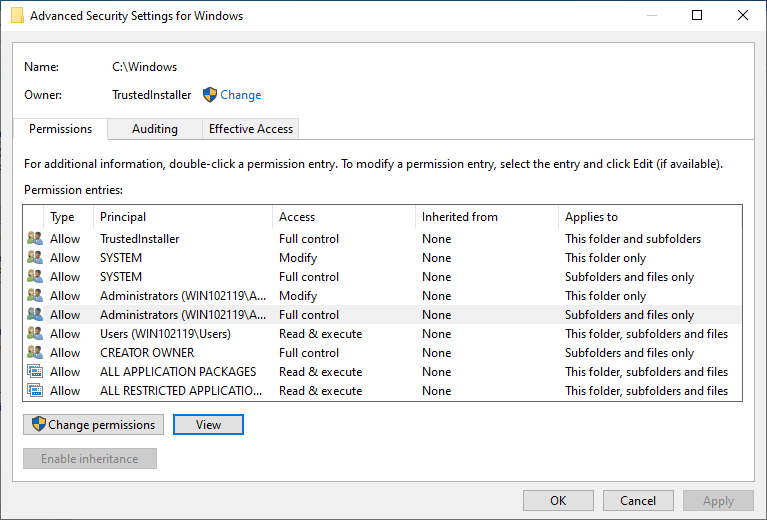
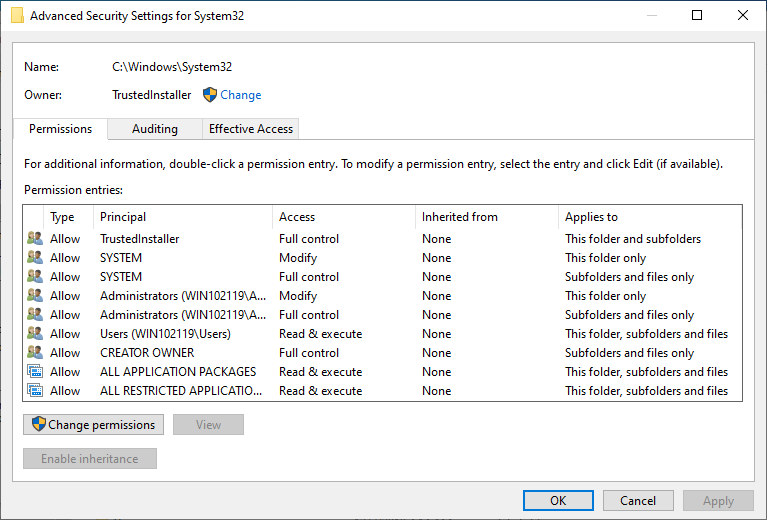
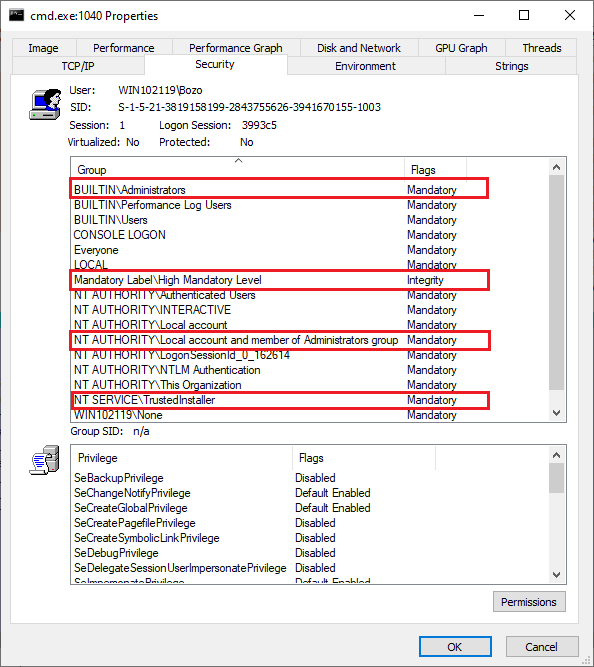
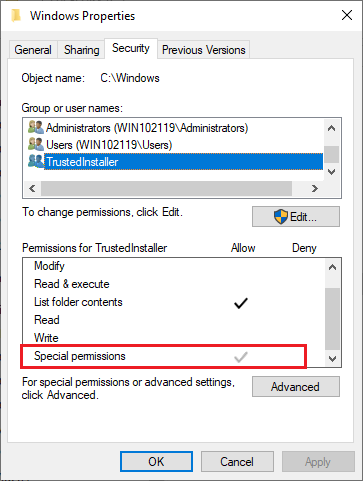
You can’t change it through security tab on properties either. If you try there are no squares to tick and even if they appear you can’t tick them. This appeared to be very strange to me especially when you use the advanced button, both system and administrators have two entries: 1- Full control on the folder, 2- Full control on files and subfolders. The inheritance is set to None.
I didn’t quite understand this. I tried icacls to reset permissions, but it failed. This was until I checked the effective access and noticed that while both accounts had quite a few rights but short of full control and one of the exclusions is the permission to change permissions.
Now it made sense. I tried the third-party tool SetAcl Studio but it didn’t work and ended up corrupting the system. I guess I should have used undone when there was an error but then that would defeat the purpose.
My guess is that this needs to change in the registry in a way updates and security updates specially cannot change them. Because as it stands the permissions are contradictory.
BTW, Dell engineers have had a go and someone on Microsoft tech who suspected that I was misunderstanding things and that there were no problems asked me to send him icacls output on Windows\System32 folder and a sample file in that folder which I did but didn’t hear anything back from him after 48 hours, but the permissions were different to his Windows 11.