Google is sending emails that our website has some links on it that are redirecting visitors, or directing them to malicious sites when clicked.
Can anyone recommend software that will scan a site and list any outgoing links it finds?
Thanks

|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
-
how to detect hidden malicious links on website?
Home » Forums » Developers, developers, developers » Web design and development » how to detect hidden malicious links on website?
- This topic has 28 replies, 7 voices, and was last updated 4 years, 6 months ago.
AuthorTopicVincenzo
AskWoody PlusSeptember 15, 2020 at 5:25 pm #2296614Viewing 20 reply threadsAuthorReplies-
Paul T
AskWoody MVP -
Alex5723
AskWoody PlusSeptember 16, 2020 at 4:37 am #2296674There are some free web scanner like :
https://sitecheck.sucuri.net/
Google’s https://transparencyreport.google.com/safe-browsing/search?hl=en -
doriel
AskWoody LoungerSeptember 16, 2020 at 5:46 am #2296677What about VirusTotal?
Personally I use that if Im not sure and I belive its a good tool.Dell Latitude 3420, Intel Core i7 @ 2.8 GHz, 16GB RAM, W10 22H2 Enterprise
HAL3000, AMD Athlon 200GE @ 3,4 GHz, 8GB RAM, Fedora 29
PRUSA i3 MK3S+
-
This reply was modified 4 years, 6 months ago by
doriel. Reason: My grammar is so weak
-
This reply was modified 4 years, 6 months ago by
-
OH_dutch
AskWoody LoungerSeptember 16, 2020 at 6:09 am #2296680I have to agree that the question could be more clearly expressed, and others are posting links to try. My professional opinion for browsing someone else’s website:
- Modern web browsers will display a hyperlink’s resolution address, or URL, when the link is hovered over. If the link’s domain differs from the one in the text, odds are it’s trouble-in-River-City. When in doubt I will email the site webmaster to confirm its validity.
And for received mail:
- Ensure that your personal network, and PCs, stay current on software patches in order to reduce known gotchas.
- Ensure that your PC(s) have firewalls turned on. The default Windows Defender is not fancy but certainly works to divert many attacks.
- Your browser is likely to divert suspected spam mail, including mail addressed in a bulk distribution list.
- Distrust all hyperlinks in any email until you have satisfied that they are legitimate. You may reach out to the sender and request confirmation. For example, a vendor’s disclaimer might mention their legitimate email will never ask the customer to reply with PII as “confirmation”.
To drive home the lesson, my (large federal contractor) employer will periodically slip in official-looking mail that includes a benign bomb. Eventually I wised up and created an email rule to quarantine most all inbound mail. There is an exception clause that provides a whitelist of accepted domains. A smililar rule could catch all inbound mail having attachments.
Good luck from a Dutch Uncle!
1 user thanked author for this post.
-
doriel
AskWoody LoungerSeptember 16, 2020 at 6:49 am #2296687Your desire
software that will scan a site and list any outgoing links it finds
requires specialized SW I think. You say
Google is sending emails that our website has some links on it
I suppose you use some CMS (Drupal, WP, ..). I would open the source code and count how many times “href” is found, Could this do the job? Did you put some of these links there? Are you aware, that you web is redirecting users?
If the link’s domain differs from the one in the text, odds are it’s trouble-in-River-City. When in doubt I will email the site webmaster to confirm its validity.
That is true. Unfortunatelly my experience is, that websites redirect regullary to display ads for you. If you are aware, that there are ads on the website, this method is not 100% valid. But if linked domain is suspicious, leave the webpage.
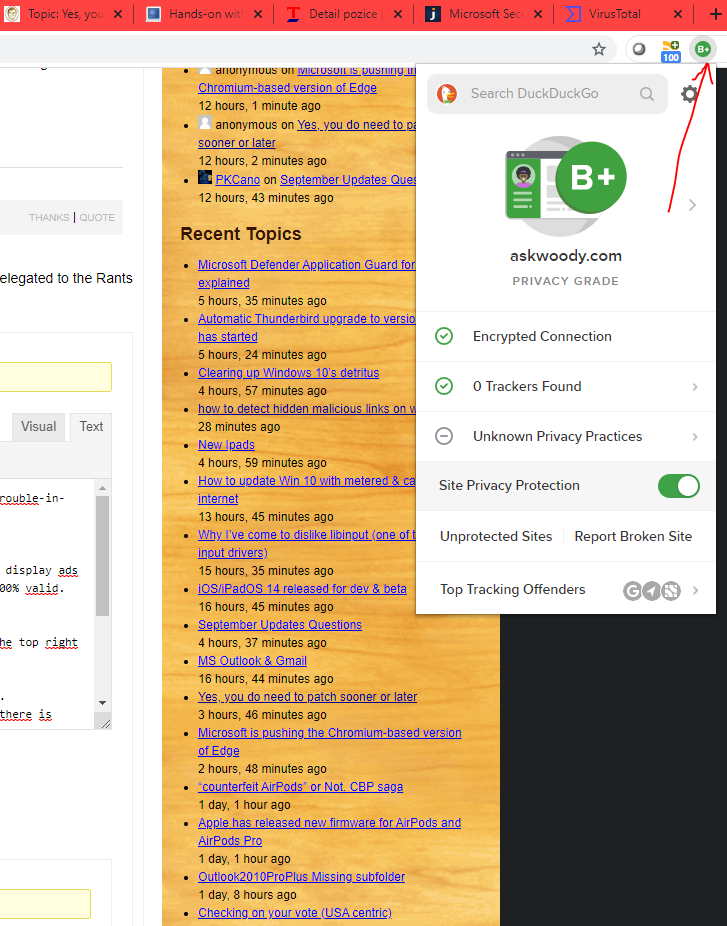
Another tip: Install DuckDuckGo privacy essentials extension to your browser. On the top right corner of address field, there will small button, which immediatelly tells you security rating of the webpage and risks. Woody gets B+, which is not bad at all.
Appendix:
When opening attachments, its highly recommended to have displayed file extensions!
Example: you will get picture in the email. you download it. In downloaded folder there is filePIC.jpeg
but if you unhide extensions, you will see
PIC.jpeg.exe
And that is definatelly fraud dont click it.
Dell Latitude 3420, Intel Core i7 @ 2.8 GHz, 16GB RAM, W10 22H2 Enterprise
HAL3000, AMD Athlon 200GE @ 3,4 GHz, 8GB RAM, Fedora 29
PRUSA i3 MK3S+
-
satrow
AskWoody MVPSeptember 16, 2020 at 7:05 am #2296695First analyse and trace the email headers to ensure they’re genuine:
https://support.google.com/mail/answer/29436?hl=en
https://whatismyipaddress.com/email-header
https://mxtoolbox.com/EmailHeaders.aspxWhere/what are you hosting your website from, a remote host, local host, a computer at your home/work?
Vincenzo
AskWoody PlusSeptember 16, 2020 at 10:25 am #2296737Thanks for the replies.
Sorry, I could have given more details.The site is hosted on a shared server on Godaddy.
The person doing SEO on the site has a Google Ad campaign in place. The ads have been running for a while with no problem.
Last week Google sent her several emails saying they had suspended the campaign, here is the message:“Our latest scan from your site came back, and still detects Malware/links that are potentially harmful to you and to the site visitors. It seems that your site (landing page) redirects users to malicious links OR triggered when clicked.”
Then they listed 3 links, supposedly on the homepage/landing page (we don’t have a specific landing page other than the homepage) to sites we’ve never heard of.
So the Google emails are genuine, they are not the problem. Problem is the malicious links Google is detecting.
I manually went through the site, did not see any obvious issues. I also scanned with Sucuri, the Google Transpareny Report, and Virustotal.
I installed an extension on Chrome that lists all the outgoing links on page. That came up with no unexpected links on the homepage.
I also checked the site with the Google Search Console, it showed no problems. But it is limited in what it detects.
(Oddly, Google provides a link to this page https://support.google.com/webmasters/answer/3258249 which details how to get details from the Search Console on what malicious files they detected. But it shows “No Issues Detected”.
(The emails from Google listing the problems do appear genuine).As far as actual experience on the site, it works fine on the computers I’ve tested it on, using 3 browsers on each. But on two iPhones, the redirect did happen to a 3rd party site. It happened once on my iPhone, once on another iPhone, and then not again. Yet.
What I have not done yet is go through the files in the site looking for href instances that provide clues. I am hoping to find software that will make that task easier.
Thanks
-
satrow
AskWoody MVP
Vincenzo
AskWoody PlusSeptember 16, 2020 at 10:42 am #2296749Vincenzo
AskWoody PlusSeptember 16, 2020 at 10:46 am #2296751“Rip the site to your own PC and work through it locally: https://www.httrack.com/”
ThanksThe problem i see doing that is that the site works fine for me online, I imagine it still would if I ripped it to my PC.
I am depending on the Google Ad campaign scans to let me know where the problem is, at this point anyway. But getting details from them is difficult. when I make a change to site and ask them to rescan, it takes a few days before I get the result back.-
This reply was modified 4 years, 6 months ago by
Vincenzo.
Vincenzo
AskWoody PlusSeptember 16, 2020 at 10:52 am #2296759The site in question is ‘https:// www. get organized with bridges .com’.
satrow edited: not redirecting to infect (no virus or other data-damaging code) but to an annoyance posing as a chance to win… whatever. The hosting server also serves adult-based ads. that look too good to be true, too (I’m just peeking into the code, right!). So, link broken, hope no-one got stuck there and that every winner receives their prize 🙂
access-mdb
AskWoody MVPSeptember 16, 2020 at 11:01 am #2296763Try checking with W3C linkchecker
Eliminate spare time: start programming PowerShell
1 user thanked author for this post.
Vincenzo
AskWoody PlusSeptember 16, 2020 at 11:58 am #2296781Try checking with W3C linkchecker
Thanks. Just tried it, nothing malicious or 3rd party comes up.
Paul T
AskWoody MVPSeptember 17, 2020 at 2:47 am #2296954If you are getting occasional redirects it suggest either a malicious script or DNS hijack.
A malicious script won’t be spotted by an external check, you need to scan the server side files.
DNS hijack would be more likely to be a permanent change, not intermittent, but you should be able to rule that out by testing from different external sites / countries.
I’ve just used the link to your site and was instantly redirected to “https://insectr unfollow8.li ve/?ut m_campa ign=QPF8 euu28II5lw7O 2iHhCidoSOX mw5oLx D6bwphw 43U1&t=mai n9”. (I’ve added spaces to the link to prevent it being used from Woodys.)
This site is listed as malware/spam on VirusTotal.
The redirect makes it look like a malicious script.Note: I run my browser with javascript turned off.
cheers, Paul
satrow
AskWoody MVPSeptember 17, 2020 at 4:19 am #2296969You can safely check the source of pages and some other types by prefixing the URL with (don’t click, copy!) http://view-source:FullURL but I can’t see how to show it on this platform, using it in a link breaks it as it adds a further https:// prefix.
-
This reply was modified 4 years, 6 months ago by
satrow.
-
This reply was modified 4 years, 6 months ago by
satrow.
-
This reply was modified 4 years, 6 months ago by
satrow.
1 user thanked author for this post.
Alex5723
AskWoody PlusSeptember 17, 2020 at 4:41 am #2296984On the redirected site, why?
You can check for fishing, spam, privacy…. behavior.
-
satrow
AskWoody MVP
Vincenzo
AskWoody PlusSeptember 17, 2020 at 5:25 pm #2297128I am somewhat surprised that you guys got re-directed since I have only seen it re-direct on the phone, and I’ve tried it from 3 browsers on 2 of my computers. I guess I should have disabled the link when I posted it, so it could not be accidentally clicked. Sorry.
I am going to try some of the suggestions, also try it using a VPN to see if that makes it redirect. It’s hard to troubleshoot from my computer when I can’t make the issue appear.
Vincenzo
AskWoody PlusSeptember 17, 2020 at 5:31 pm #2297132A malicious script won’t be spotted by an external check, you need to scan the server side files.
How would I do that?
Thanks
Vincenzo
AskWoody PlusSeptember 17, 2020 at 5:33 pm #2297134Here’s something interesting. When I turn on the VPN in Norton and visit the site, I do get the re-directs. That’s the only time I’ve been able to see it myself on my computer. I see that the VPN made it appear like I am in North Carolina.
Not sure what to make of that.
I’ll try some of the above suggestions now.
-
This reply was modified 4 years, 6 months ago by
Vincenzo.
-
satrow
AskWoody MVPSeptember 17, 2020 at 6:18 pm #2297146Check your DM messages, there’s one that attempts to give clearer links to looking at page sources as code – it should help a lot.
I’ve read reports that the redirect triggers on the first view but not subsequent, I’ve seen the opposite! So, it might be random or based on some ‘order’, expect the unexpected but look at the source code where you can before going in with standard URLs.
Vincenzo
AskWoody PlusSeptember 17, 2020 at 7:32 pm #2297181Check your DM messages, there’s one that attempts to give clearer links to looking at page sources as code – it should help a lot.
Thanks, using your view-source: as a url prefix, I can finally see the redirect.
Oddly it happens in Firefox but the site loads normally in Chrome.
Any ideas on how to remove this redirect?
Thanks
-
This reply was modified 4 years, 6 months ago by
Vincenzo.
Vincenzo
AskWoody PlusSeptember 17, 2020 at 7:39 pm #2297182All I can see when I use that technique is the redirect, but I can’t see where it is located on the page so I could remove it.
And why would the page even load correctly as it does in Chrome when the source code only shows the redirect??
-
This reply was modified 4 years, 6 months ago by
Vincenzo.
-
satrow
AskWoody MVPSeptember 17, 2020 at 8:25 pm #2297188Scripts, maybe browser UA, mouse action detection or something similar (do nothing unless…).
The redirect is the page – provided you have fulfilled their criteria. If you haven’t, or you’re not vulnerable, you get the real page (maybe, I’ve not seen their script and probably wouldn’t understand it as it’s likely using min.js, or w/e compression is the latest ‘thing’.
Wipe the site, fire your devs/staff/seo experts and claim comp. from them, check and tighten security obviously, reload the site from the original, or latest known-good copy, check security again…
1 user thanked author for this post.
Paul T
AskWoody MVPSeptember 19, 2020 at 3:21 am #2297460Agree with “fire your dev team and sue them”. There is no dev worthy of the name that would allow malicious scripts to be installed.
You can get website apps that will scan your server pages for malicious scripts and check that you have valid packages installed, but this does require some knowledge on your part to install / maintain and it’s not free.
If you have a backup of the site (if not, why not?) you can load it locally and scan the files using search in Windows Explorer for the site name, but it is probably encrypted / hidden to make it more difficult to detect.
What you probably have is a single line that calls a javascript routine from a remote server. That allows the re-direct to be changed as required.
cheers, Paul
1 user thanked author for this post.
Vincenzo
AskWoody PlusSeptember 19, 2020 at 12:06 pm #2297497Thanks for the input.
There is no dev team. The site belongs to a friend of mine for her small business. I did install Updraft Plus backup previously, so there are current backups that can be restored. I am going to try the GoDaddy Security package first to see if that can detect it.
Thanks
Viewing 20 reply threads -

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
WARNING about Nvidia driver version 572.83 and 4000/5000 series cards
by
Bob99
2 hours, 35 minutes ago -
Creating an Index in Word 365
by
CWBillow
2 hours, 41 minutes ago -
Coming at Word 365 and Table of Contents
by
CWBillow
2 hours, 45 minutes ago -
Windows 11 Insider Preview Build 22635.5170 (23H2) released to BETA
by
joep517
7 hours, 42 minutes ago -
Has the Microsoft Account Sharing Problem Been Fixed?
by
jknauth
11 hours, 7 minutes ago -
W11 24H2 – Susan Bradley
by
G Pickerell
13 hours, 3 minutes ago -
7 tips to get the most out of Windows 11
by
Alex5723
11 hours, 4 minutes ago -
Using Office apps with non-Microsoft cloud services
by
Peter Deegan
4 hours, 26 minutes ago -
I installed Windows 11 24H2
by
Will Fastie
2 hours, 44 minutes ago -
NotifyIcons — Put that System tray to work!
by
Deanna McElveen
16 hours, 30 minutes ago -
Decisions to be made before moving to Windows 11
by
Susan Bradley
3 hours, 26 minutes ago -
Port of Seattle says ransomware breach impacts 90,000 people
by
Nibbled To Death By Ducks
1 day ago -
Looking for personal finance software with budgeting capabilities
by
cellsee6
8 hours, 57 minutes ago -
ATT/Yahoo Secure Mail Key
by
Lil88reb
9 hours, 12 minutes ago -
Devices with apps using sprotect.sys driver might stop responding
by
Alex5723
1 day, 17 hours ago -
Neowin – 20 times computers embarrassed themselves with public BSODs and goofups
by
EP
2 days, 2 hours ago -
Slow Down in Windows 10 performance after March 2025 updates ??
by
arbrich
1 day, 4 hours ago -
Mail from certain domains not delivered to my outlook.com address
by
pumphouse
1 day, 10 hours ago -
Is data that is in OneDrive also taking up space on my computer?
by
WShollis1818
1 day, 21 hours ago -
Nvidia just fixed an AMD Linux bug
by
Alex5723
3 days, 13 hours ago -
50 years and counting
by
Susan Bradley
11 hours, 22 minutes ago -
Fix Bluetooth Device Failed to Delete in Windows Settings
by
Drcard:))
14 hours, 11 minutes ago -
Licensing and pricing updates for on-premises server products coming July 2025
by
Alex5723
4 days ago -
Edge : Deprecating window.external.getHostEnvironmentValue()
by
Alex5723
4 days ago -
Rethinking Extension Data Consent: Clarity, Consistency, and Control
by
Alex5723
4 days ago -
OneNote and MS Word 365
by
CWBillow
4 days, 2 hours ago -
Ultimate Mac Buyers Guide 2025: Which Mac is Right For You?
by
Alex5723
4 days, 2 hours ago -
Intel Unison support ends on Windows 11 in June
by
Alex5723
4 days, 2 hours ago -
April 2025 — still issues with AMD + 24H2
by
Kevin Jones
1 day, 17 hours ago -
Windows 11 Insider Preview build 26200.5518 released to DEV
by
joep517
4 days, 14 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.