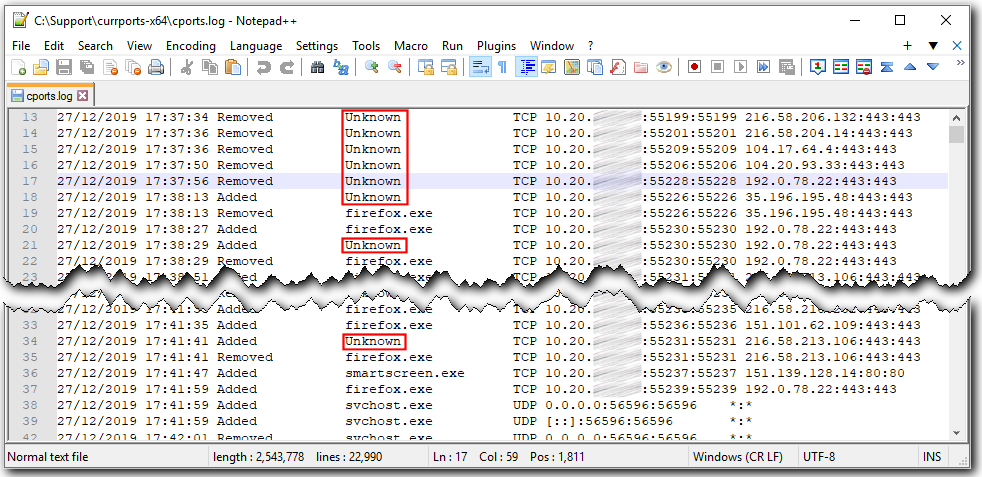
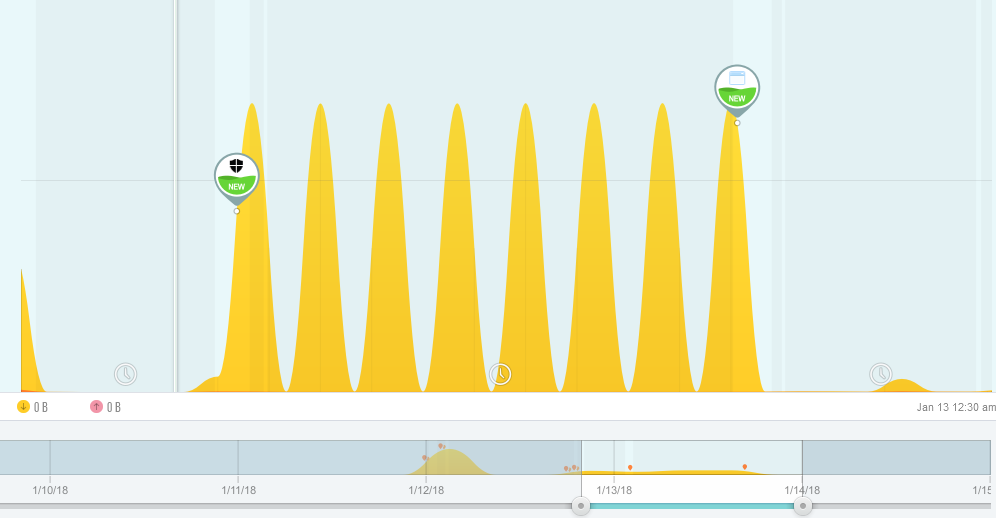
This was submitted by @Kathy-Stevens
While booting our Windows 10 PCs, we frequently observe a high level of internet traffic as indicated by blinking lights on our servers and routers. While some of the traffic is related to our internet security apps, I assume that the bulk of the traffic is between the computer and Microsoft. Is it a good idea to install a physical internet kill switch between our routers/modems and the internet service provider or between a work station and its router in-order to block internet access during boot-up? A quick internet search has revealed that such switches are available. One vendor is located at https://internetswitches.com/ .