A couple of years ago, Windows Defender stopped automatically installing new definitions updates in Vista. This was not a big problem because it was still possible to manually download the updates and install them by running the definitions file (mpas-fe.exe) as Administrator; and I managed to keep doing just that until four weeks ago.
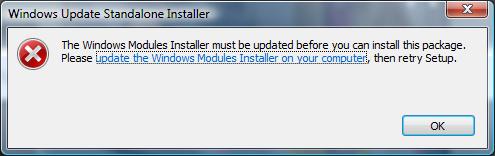
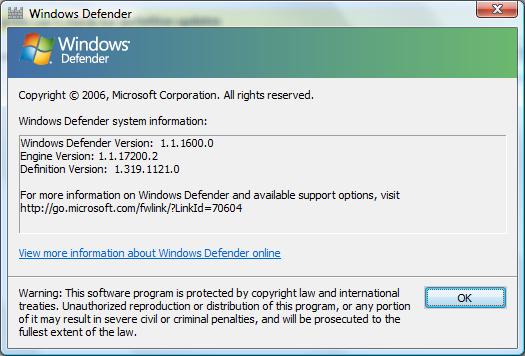
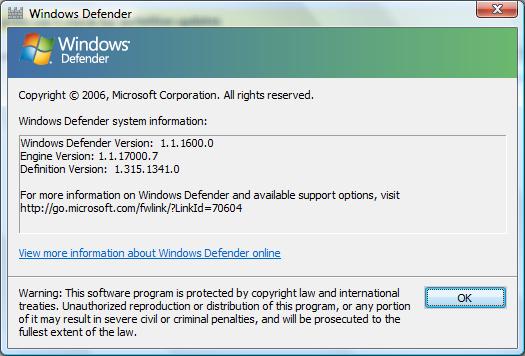
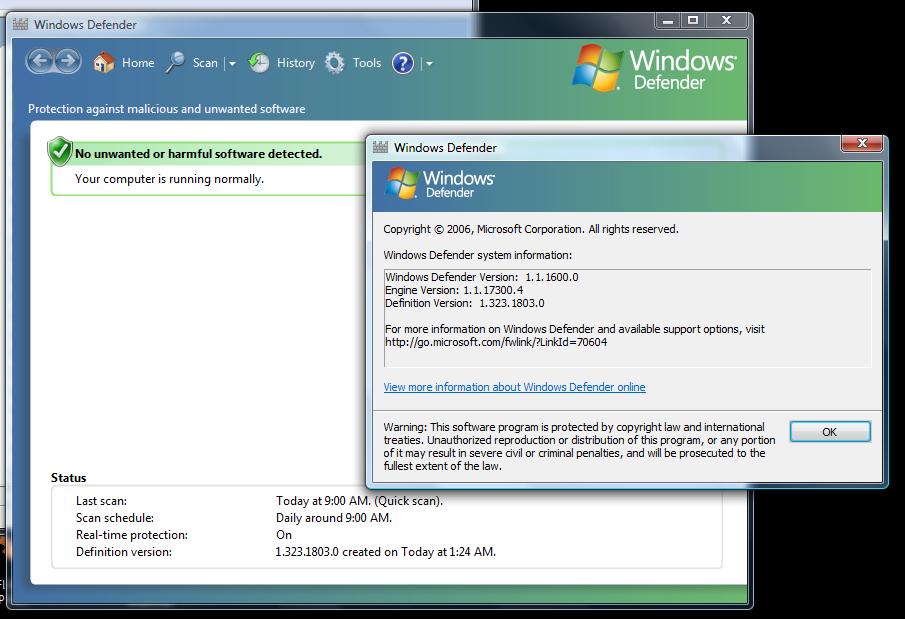
Since the beginning of August, though, this manual method has stopped working. The last definition version is “1.321.534.0 created on 8/3/2020 at 10:49 AM”. Does anybody have insight into what happened this summer (and not before this year) to make this manual installation method stop working?
Adding to the strangeness is that when I hover the mouse pointer over the mpas-fe.exe file in Windows Explorer, the file information there differs from what I gave above: it has the file version as 1.323.290.0 with a creation date of 7/9/2020 at 11:45 AM.
Please, no inquiries or comments as to why I’m still running Vista or Windows Defender. I wish to focus on what change did or may have occurred to have the effect described above.
Thanks.