When the instructions say to put W7ESUI.CMD “next to” the MSU files, does that mean “in the same directory as”?

|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
-
Comments on Abbodi86’s Win7 ESU Installer Script (2020 Archive)
Home » Forums » AskWoody support » Windows » Windows 7 » Win7 beyond End-of-life » Comments on Abbodi86’s Win7 ESU Installer Script (2020 Archive)
- This topic has 577 replies, 70 voices, and was last updated 4 years, 5 months ago.
AuthorTopicanonymous
GuestMarch 20, 2020 at 9:40 am #2209123Viewing 576 reply threadsAuthorReplies-
jabeattyauditor
AskWoody Lounger -
PKCano
Manager -
honx
AskWoody LoungerMarch 20, 2020 at 9:59 am #2209128if i decide to install february and march group b patches on win7, is there anything to consider about these patches (bugs or anything else)?
PC: Windows 7 Ultimate, 64bit, Group B
Notebook: Windows 8.1, 64bit, Group B -
PKCano
ManagerMarch 20, 2020 at 10:10 am #2209137See this thread for information, especially the note at the top about the Group B patches. And the similar blogpost about the Feb Patch Tues.
There are also notes in AKB2000003.
-
honx
AskWoody LoungerMarch 20, 2020 at 10:35 am #2209146See this thread for information, especially the note at the top about the Group B patches. And the similar blogpost about the Feb Patch Tues.
There are also notes in AKB2000003.
thx, how can i check, if ssu kb4490628 is installed already? i know i have kb4474419 (because i had to install 3 times kb4474419 last year which i clearly remember) but i can’t find the kb4490628 which is required by march esu patches in windows update (unfortunately there is no search-box in windows update).
and in which order is that new ssu kb4550735 to be installed? after february win7/ie patches?
for example like this?
february kb4537813 (win7)
february kb4537767 (ie)
reboot
ssu kb4550735
( i downloaded the file linked in:
https://www.askwoody.com/forums/topic/initial-impressions-of-patch-tuesday-march-2020/#post-2189166 )
reboot
march kb4541500 (win7)
march kb4540671 (ie)
reboot
office and other non-windows patches
reboot (just to make sure)PC: Windows 7 Ultimate, 64bit, Group B
Notebook: Windows 8.1, 64bit, Group B -
PKCano
ManagerMarch 20, 2020 at 10:49 am #2209151To see if kb4490628 is installed look in Windows Update. On the lower left corner click on “View installed updates.”
You can sort by any column. Click on the column title to choose the column to sort by. It is a toggle, alternating ascending/descending.
kb4490628 was issued in april 2019, so if you sort by date it will be 3/12/2019 or later. If you sort by title, each category will have the KB number sorted numerically. -
PKCano
ManagerMarch 20, 2020 at 10:52 am #2209153 -
honx
AskWoody LoungerMarch 20, 2020 at 10:52 am #2209154can’t edit my post anymore, so i have to reply: what do i have to deactivate in order to get rid of this diagtrack thingamajigs in march update? (microsoft are now charging for win7 updates and these to purchase patches still contain spyware – i don’t get it…)
PC: Windows 7 Ultimate, 64bit, Group B
Notebook: Windows 8.1, 64bit, Group B -
PKCano
ManagerMarch 20, 2020 at 10:56 am #2209157See AKB2000012.
5 users thanked author for this post.
-
honx
AskWoody LoungerMarch 20, 2020 at 10:58 am #2209158You can collect the updates and the needed file(s) in one folder.
If you are using @abbodi86 ‘s script, you should follow those instructions.
The Office, MSRT updates are still available through Windows Update for supported versions.so all february, march and that ssu in the same folder and that script takes care about the order and installs also that march ssu at the right time?
PC: Windows 7 Ultimate, 64bit, Group B
Notebook: Windows 8.1, 64bit, Group B -
abbodi86
AskWoody_MVPMarch 20, 2020 at 11:05 am #2209161 -
Pim
AskWoody PlusMarch 20, 2020 at 11:42 am #2209166Just out of curiosity: why? My reason for asking: I have seen other contributors on AskWoody claiming this is illegal.
I myself take a practical approach: I have lost so very many hours (> 100) because of Microsoft’s absence of client focus that I honestly do not care whether it is illegal (normally I do). One example: only informing that Ultimate is also covered by ESU in late November which caused me much stress trying to get my systems on Windows 10 in the months before November 2019, which failed, because of a lack of time and energy on my part caused by insufficient health.
1 user thanked author for this post.
-
Chriski
AskWoody PlusMarch 20, 2020 at 11:46 am #2209167Use 0patch or script installer (no ESU, Win 7 group B through Jan patches) or both?
I installed 0patch(free) after the Jan patches, and it’s been doing fine.
Also use the script installer because more is better and it will enhance things missing from 0patch, or is this 0patch tool probably sufficient?
Thanks for opinions..
C.
-
Susan Bradley
ManagerMarch 20, 2020 at 12:42 pm #2209178Does it violate licenses and eulas….. yes …but my morals are slipping. We are in unusual times where people are using Win7’s to remote in from home. I’ve sent an email to Satya to ask him to open up 7 patching for all given the circumstances.
Susan Bradley Patch Lady/Prudent patcher
-
Melvin
AskWoody PlusMarch 20, 2020 at 1:41 pm #2209184Does it violate licenses and eulas….. yes …but my morals are slipping. We are in unusual times where people are using Win7’s to remote in from home. I’ve sent an email to Satya to ask him to open up 7 patching for all given the circumstances.
Yes, considering so many must now work from home, it would be good if Microsoft would step up and open up the ESU for some period of time. I guess this is most applicable to people who have their “home” computer and until now have only used the IT-supported computers at their work place.
Indeed, I saw a report that bad actor’s may have increased their efforts against homes and home users anticipating increased opportunities in these new circumstances.
Win 11 Pro 23H2, Office 2024.
Win 10 Pro 64-bit 22H2, Office 2019.
Win 7 Pro 64-bit, Office 2010.
Nethermost of the technically literate. -
honx
AskWoody LoungerMarch 20, 2020 at 1:45 pm #2209188Yes
You only need the latest SSU (March KB4550735), and the latest IE11 cumulative (March KB4540671)
in addition to security only update for both February and Marchthanks, i’ll wait for ms defcon 3 or higher and for some observations by other users here before i try it myself.
PC: Windows 7 Ultimate, 64bit, Group B
Notebook: Windows 8.1, 64bit, Group B -
Geo
AskWoody PlusMarch 20, 2020 at 1:55 pm #22091930patch pro is half the price of ESU and is working just fine. I’m a home premium user . Getting a number of micro patches lately.
-
anonymous
GuestMarch 20, 2020 at 2:00 pm #2209189Open Windows Update > click on View Update History (in left navigation) > click on the linked Installed Updates > copy & paste the KB number into the top left search field.
That way you don’t have to waste time sorting and searching by date.
Hope I could help.
1 user thanked author for this post.
-
anonymous
GuestMarch 20, 2020 at 2:02 pm #2209192Any known issues using this script on a Kaby Lake (intel 7xxx) box running wufuc ?
-
KWGuy
AskWoody PlusMarch 20, 2020 at 2:05 pm #2209199Every time I think I’ve found a way to outsmart Mother Microsoft re: updating, it usually backfires…or at least causes more anxiety and takes more time than it’s worth.
My gut tells me that this unsanctioned (and per SB , a license violation) approach is not a good option. I acknowledge that I’m a non-techie home user with a less adventurous spirit than most. I agree, though, that MS should extend traditional W7 patching due to current circumstances.
-
T
AskWoody LoungerMarch 20, 2020 at 2:30 pm #2209203Thank you so much for this, abbodi86. This should tide me over until i figure out what i’m going to do long term, with no option being ideal. However, i am a little concerned implementing it because this violates the EULA and i worry microsoft will start deactivating the product keys of genuine installs and then you’re effectively using a pirate copy. Also, it was my understanding that this workaround had been prevented with the latest SSU.
-
PKCano
ManagerMarch 20, 2020 at 2:34 pm #2209212I have just run the script on one of my Win7 Ultimate x64 VMs that was updated through Jan.
There were no problems during the install.
There were two (2) reboots afterward.
Here is the result. -
woody
Manager -
woody
ManagerMarch 20, 2020 at 2:56 pm #2209225OK. I’ll bite. How does running abbodi86’s script violate the Win7 EULA?
-
T
AskWoody LoungerMarch 20, 2020 at 3:04 pm #2209226Oh, does it not? Susan upthread seems to agree that it does. My concern is just what microsoft will do to clamp down on obtaining ESUs for free.
Then again, we’re currently living through a period where so many more people are working from home and win7 still has a huge user base.
-
This reply was modified 5 years, 2 months ago by
T.
-
This reply was modified 5 years, 2 months ago by
-
alkhall
AskWoody LoungerMarch 20, 2020 at 3:54 pm #2209262No file to download, link gives blank page.
-
Volume Z
AskWoody LoungerMarch 20, 2020 at 4:15 pm #2209270 -
b
AskWoody_MVPMarch 20, 2020 at 4:45 pm #2209281How does running abbodi86’s script violate the Win7 EULA?
8. SCOPE OF LICENSE.
You may not
· work around any technical limitations in the software;1 user thanked author for this post.
-
ch100
AskWoody_MVPMarch 20, 2020 at 4:59 pm #2209283I think Susan’s assessment and subsequent action – to write to Satya asking for a waiver given the times are appropriate. This is a grey area and open to interpretation either way.
I would like to raise a technical issue though, only for clarification.
This script installs SSU first and the relevant update in the second step.
I was under the impression that this order does not matter anymore, because the SSU released in a specific month actually applies to the update released next month, this being done by Microsoft to avoid past issues. There is still a requirement to update regularly because SSU is not released each month.
Is this true about the SSU order, or is only true for Windows 10 or is not true at all?
-
Seff
AskWoody PlusMarch 20, 2020 at 5:00 pm #2209284Isn’t this all rather academic at the moment? We’re at DefCon 2 for heaven’s sake.
-
alkhall
AskWoody LoungerMarch 20, 2020 at 5:03 pm #2209286You’re doing it wrong.
Got it, thanks.
-
italiangm
AskWoody PlusMarch 20, 2020 at 5:28 pm #2209292Hello all. Wanted to share experience and ask a question:
Since FEB2020 updates were cleared for installation, I downloaded kb4537767-x64 and kb4537813-x64 msu from Microsoft Update Catalog. Followed the instructions so kindly provided by abbodi86.
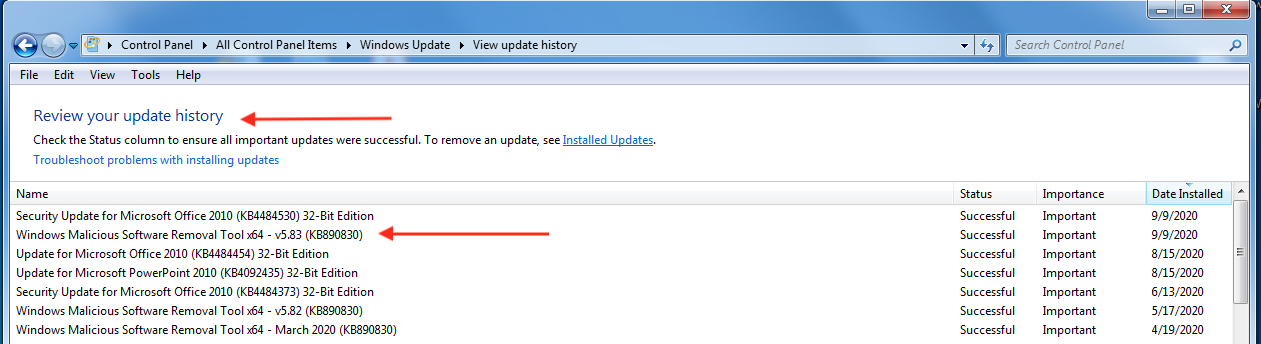
Install ran without a hitch. After successful reboot, I opened Windows Update and selected View Update History. KB4537767 and KB4537813 do not appear.
Checked Control Panel > Installed Updates. KB4537767 and KB4537813 were listed there.
Is there a reason why the FEB2020 updates do not appear in View Update History?
-
PKCano
ManagerMarch 20, 2020 at 5:29 pm #2209300Is there a reason why the FEB2020 updates do not appear in View Update History?
Yes, Windows Update History is the history of updates that Windows Update installed. Windows Update didn’t install those updates, you did.
But to verify that they are installed, they are listed in “Installed Updates.” -
Volume Z
AskWoody LoungerMarch 20, 2020 at 7:12 pm #2209323Are you telling us that any given Security Only Update is impossible to appear in Update History?
-
PKCano
ManagerMarch 20, 2020 at 7:36 pm #2209326Security-only updates are not released through Windows Update.
I could be wrong, but I believe that would be the case if you do a manual install.
An exception would be if the SO were released through WU.
I don’t think it shows in Update History, but it does in “Installed Updates.”
Also, if you uninstall an update, it doesn’t disappear from Update History. It is still listed in History at the time/date it was installed (but it is no longer in Installed Updates).Note: This applies to current updates that MS designated as Rollup and Security-only, not to the prior updates that were designated Updates for Windows and Security Updates for Windows (2016 and before)
-
Volume Z
AskWoody LoungerMarch 20, 2020 at 7:54 pm #2209330By thinking, any update installed manually – like any given Security-Only – does not appear in Update History, you’re thinking wrong. It should be easy for you to verify in any Windows 7 installation.
-
PKCano
ManagerMarch 20, 2020 at 7:57 pm #2209331I only do Rollups. Can you post a screenshot?
I’m certainly open to stand corrected. -
anonymous
Guest -
Volume Z
AskWoody Lounger -
PKCano
ManagerMarch 20, 2020 at 8:23 pm #2209349Thanks.
Were those manual installs or using WSUS or one of the installers? -
RDRguy
AskWoody LoungerMarch 20, 2020 at 8:27 pm #2209352@PKC … I’m not sure that’s the case … being Group B since the very beginning, I’ve only manually installed all the monthly SO & IE11 Cum updates downloaded either directly from the MS Update Catalog or AKB2000003 and everyone of them DO appear in the Windows Update History as well as the “Installed Updates” on all of my Win7 systems.
I suspect this may be due to the processes used by @abbodi86’s batch script to incorporate the post ESU Win7 updates into non-ESU Win7 systems.
If so, it’s implementation may not use (or use in the normal way) any or all of the actual Windows Update mechanisms that would normally be used either pre or post ESU to incorporate Win7 updates.
Could/should/would this be changed in a future batch script update … I suspect only @abbodi86 can answer.
Win7 - PRO & Ultimate, x64 & x86
Win8.1 - PRO, x64 & x86
Groups A, B & ABS -
PKCano
Manager -
alpha128
AskWoody PlusMarch 20, 2020 at 8:51 pm #2209366My goodness – this is the greatest thing since sliced bread. And since the last time I was in a grocery store there was no bread – that makes this the greatest thing going today!
I downloaded the script and installed per your instructions. I used to it to install the March Servicing Stack update (KB4550735) and 2020-03 Security Monthly Quality Rollup for Windows 7 for x64-based Systems (KB4540688). As advertised, the servicing stack was installed first, and then the roll-up.
As other users report, these updates did not appear in my Windows Update history, but they do appear when running, e.g., powershell (get-hotfix -id KB4540688). They also appear as installed updates in Control Panel.
Thank you so much!

5 users thanked author for this post.
-
woody
ManagerMarch 20, 2020 at 9:45 pm #2209373I don’t feel so guilty.
Don’t know of any specific EULA or license that says you can’t use freely available patches on a licensed copy of Win7….
Playing devil’s advocate, of course.
-
woody
ManagerMarch 20, 2020 at 9:51 pm #2209375I hear ya but… I’m not so sure that applying updates is working around a technical limitation.
For example, I don’t think 0patch patches violate the EULA.
One could make the argument that running any Win7 utility is working around a technical limitation in the software…. antivirus…
-
abbodi86
AskWoody_MVPMarch 20, 2020 at 11:04 pm #2209391Not really, latest SSU first, is still the correct order
if you installed higher stack installer version, it will take precedence and work for all lower versions– Check required stack installer version for each update
if an update require higher SSU, the script will show error message and skip it
and that’s why for manual installation of ESU updates, you should only download and use latest SSU, even if current updates require previous SSU
-
abbodi86
AskWoody_MVPMarch 20, 2020 at 11:14 pm #2209392Windows Update History show the history of updates installed via WU, or via msu file directly (double-click)
but not if the updates are installed via DISM.exe tool (like the script does)Update History can be reset/wiped easily, but “Installed Updates” will always show the updates
@RDRguy
Windows Update is more like a GUI front-end for CBS (the actual engine that process updates)
DISM.exe is the CLI front-end for CBS -
ch100
AskWoody_MVPMarch 21, 2020 at 1:11 am #2209410@abbodi86
My comment was more in relation to this (hypothetical) scenario:– SSU 2020-01 installed
– Patches for 2020-02 are released
– Install 2020-02 CU first (for whatever reason, see below for an example)
– Install 2020-02 SSUIf 2020-02 CU require minimum 2020-01 SSU, then the previous sequence would still work, while not installing the 2020-02 SSU first.
Same would be repeated next month 2020-03 in this example, if 2020-03 CU require as minimum 2020-02 SSU and not 2020-03 SSU.
This may have practical implications when let’s say 2 patches are pushed simultaneously via WSUS or SCCM and they are installed without a reboot between them. This is a very common scenario in fact and I have seen the SSU is not always installed first due to the sequence having other criteria like randomization, which patch is downloaded first from the update server etc.
Ideally the updates should be installed in 2 steps, SSU first, waiting for it to be deployed everywhere and then the CU for the month. But this is not practical or always possible taking in consideration the operational requirements, except for the smallest of environments and as such it is never done in 2 steps.
Note: In WSUS or SCCM which leverages the same WSUS, SSU and CU are always installed separately and not bundled as it is the case for Windows Update.
-
Kranium
AskWoody Lounger -
abbodi86
AskWoody_MVPMarch 21, 2020 at 2:08 am #2209419 -
Sinclair
AskWoody LoungerMarch 21, 2020 at 3:53 am #2209439Used this on Windows 7 x64 Home Premium. Everything went well and after two reboots the computer still works. I did it with the network cable pulled. Once everything was done I ran the W10Tel.cmd After another reboot I replugged the network cable. So far so good.
W10&11 x64 Pro&Home
-
woody
Manager -
alpha128
AskWoody PlusMarch 21, 2020 at 10:12 am #2209514Used this on Windows 7 x64 Home Premium. Everything went well and after two reboots the computer still works. I did it with the network cable pulled. Once everything was done I ran the W10Tel.cmd After another reboot I replugged the network cable. So far so good.
According to the Pros above, this new script does “Include the Telemetry neutralize tweaks”. So you may not need W10Tel.cmd any more.
After running the new script on my system I see:
Directory of C:\ProgramData\Microsoft\Diagnosis
File Not Found
Directory of C:\ProgramData\Microsoft\Diagnosis\ETLLogs
11/15/2016 08:00 PM <DIR> .
11/15/2016 08:00 PM <DIR> ..
0 File(s) 0 bytesTotal Files Listed:
0 File(s) 0 bytesI did previously have files there, but I had stopped them from being updated. Now they are gone.

-
Sinclair
AskWoody LoungerMarch 21, 2020 at 2:46 pm #2209589This Windows 7 Home Premium x64 Computer installation is from 2009. Still in use every day. It has seen its fair bumbs and bobs along the way.
My Directory of C:\ProgramData\Microsoft\Diagnosis contains
User.dat 16-09-2015 0 kb
and 8 Folders
\AsimovUploader 16-01-2017 empty
\DownloadedScenarios 19-05-2015 empty
\DownloadedSettings 16-01-2017
..cfc.flights.json 04-06-2015 1 kb
..telemetry.ASM-WindowsDefault.json 16-01-2017 11 kb
..telemetry.ASM-WindowsDefault.json.bk 15-09-2015 6 kb
..utc.app.json 16-01-2017 38 kb
..utc.app.json.bk 15-09-2015 22 kb
\ETLLogs\AutoLogger 20-03-2020 empty
\ETLLogs\ShutdownLogger 16-01-2017 empty
\LocalTraceStore 16-01-2017 empty
\Sideload 16-01-2017 empty
\SoftLanding 16-01-2017 access denied
\SoftLandingStage 16-01-2017 access deniedW10&11 x64 Pro&Home
-
italiangm
AskWoody PlusMarch 21, 2020 at 3:27 pm #2209595After using the script on my Win 7 SP1 PC, I noticed a new file named RunOnce_W10_Telemetry_Tasks.cmd on the desktop.
FYI, I did not place MSUs, zip file, or extracted files on the desktop, nor run W7ESUI.cmd from there.
Can I delete RunOnce_W10_Telemetry_Tasks.cmd from the desktop without causing problems if I run the script in the future?
-
abbodi86
AskWoody_MVPMarch 21, 2020 at 3:39 pm #2209599I forgot to mention this, sorry
the script is ment to disable the relevant schedule task after installing Monthly Rolup (they only can be disabled after restart)
therefore, you just need to run it as administrator, it will be self-deleted afterwards
or just delete it -
anonymous
GuestMarch 21, 2020 at 3:44 pm #2209598Hopefully you have a full system backup and maintain files backup in case Microsoft decides to plug the free patch access hole.
-
anonymous
GuestMarch 22, 2020 at 4:34 am #2209819Standalone installer script for Windows 7 ESU, regardless the license.
Dowloaded W7ESU1 files and extracted ok . Then downloaded February and March Group B updatesKB4537767 KB4537813 KB1540671 KB1541500 for my Win 7 X64 Pro Laptop and placed in same folder as advised. Script runs fine however after extracting the cab files it telle me I need :
SSU VERSION 6.1.7601.24544
SSU VERSION 6.1.7601.24548I already have KB4490628 and KB4474419 installed and all Group B security updates up to and including January installed. Advice please.
-
PKCano
ManagerMarch 22, 2020 at 4:40 am #2209822Have you been installing the SSUs before EOL?
Try installing KB4536952 Jan SSU manually first before running the script.
Also did you include Mar SSU KB4550735 in the download folder with the script?
You only need the latest IE11 CU b/c they are cumulative. -
abbodi86
AskWoody_MVP -
anonymous
Guest -
italiangm
AskWoody PlusMarch 22, 2020 at 1:01 pm #2209939Right clicked on RunOnce_W10_Telemetry_Tasks.cmd then selected Run as administrator. The process ran and deleted RunOnce_W10_Telemetry_Tasks.cmd at the end as stated. Thanks again!
-
Cybertooth
AskWoody PlusMarch 22, 2020 at 1:09 pm #2209942OK, just to make sure that I understand the process:
Supposing that one installs February’s Security Only patch for Windows 7 by using this script. Come time to install the March updates, would one then manually run the script again?
-
abbodi86
AskWoody_MVPMarch 22, 2020 at 2:01 pm #2209959Yes, placing March Security Only update (and March SSU) next to it
you don’t need to move the February update, the script should detect it as installed and skip it (after extraction)
3 users thanked author for this post.
-
Ed
AskWoody LoungerMarch 22, 2020 at 4:08 pm #2209983@abbodi86… “if you installed higher stack installer version, it will take precedence and work for all lower versions”
I’m questioning my reading comprehension level here… If I’m understanding this statement correctly I only need to to install the latest SSU (KB4550735) FIRST and then I would be able to install all updates available since August 2019 on two Group B systems that haven’t been patched since then?
-
PKCano
ManagerMarch 22, 2020 at 4:16 pm #2209985Put SSU KB4550735, all the Security-only updates, and the latest IE11 CU KB4540671 in the folder with the script. The script will install the SSU first and then the rest of the updates.
Be sure you have SHA2 support updates KB4490628 and KB4474419 already installed beforehand.
-
pandarunnerpt
AskWoody PlusMarch 22, 2020 at 6:52 pm #2210020I have been using 0Patch since 11/18/19, my husband about a month after. We both are on Win 7 Professional 64 bit SP1 computers, I am i7 6700, he is i3 4130. We both were group B until January when we had to install the rollups in order to assure that 0Patch would work properly.
Acting as guinea pigs for the 0Patch people on the board, and as per this link from 0Patch saying that it was not an issue to use both 0Patch and ESU at the same time https://0patch.zendesk.com/hc/en-us/articles/360011192299-Can-I-use-0patch-in-parallel-to-Windows-Extended-Security-Updates– I installed abbodi86‘s script and then the Feb. Security and IE updates today.
Installation went as described and both of us have had no problems at all. 0Patch is still working as expected, too.
Thank you abbodi86 and thank you everyone in this conversation who made it easier for me to give this a try.
Win 7 Professional, 64 bit, was Defiantly Group B, but installed 0Patch and needed to become group A to comply.
1 user thanked author for this post.
-
Geo
AskWoody PlusMarch 22, 2020 at 7:31 pm #22100260patch put out an email today mentioning only W7 users who HAVEN’T taken the ESU downloads are able to use the 0patch micro-patches . Mentions they are not compatible with the ESU downloads. Be interesting if some one with ESU and 0patch are having problems as 0patch is mentioning.
1 user thanked author for this post.
-
abbodi86
AskWoody_MVP -
RDRguy
AskWoody Lounger -
woody
Manager -
anonymous
GuestMarch 23, 2020 at 2:53 pm #2210255Tells me I have to run as administrator even when I right click and do just that.
-
PKCano
ManagerMarch 23, 2020 at 2:55 pm #2210259Are you logged in with a Standard (non-Administrator) ID?
-
anonymous
GuestMarch 23, 2020 at 3:00 pm #2210261No, an admin account
-
analogkid
AskWoody PlusMarch 23, 2020 at 5:36 pm #2210311Downloaded the required W7ESUI and then the Feb SO updates.
I made sure I had the SSU necessary installed which I already did way back when as I did installed the Group Jan update prior to buying 0patch subscription.
Well I thought I would try this new ESL and for me it didnt work. I got the cmd window with all of the same script as pictured but when I hit the zero key nothing happened.
Just noticed I needed SSU KB4550735 so I went to the Microsoft Update Catalog and downloaded it.
Must admit, I am kind of lost where to go from here but then I am not computer savvy
"An analog kid in a digital world"
Win7 Ultimate home built desktop Running 0patch Pro
Two former 8.1 Laptops & two desktops now running Win 10
Win 10 Dell desktop
-
This reply was modified 5 years, 2 months ago by
analogkid.
-
This reply was modified 5 years, 2 months ago by
-
PKCano
ManagerMarch 23, 2020 at 5:43 pm #2210314I made sure I had the SSU necessary installed which I already did way back when as I did installed the Group Jan update prior to buying 0patch subscription.
You can’t have installed the March SSU back in Jan. SSU KB4550735 was just released Mar. 10th. It needs to be in the folder with the Mar Group B updates KB4541500 SO and KB4540671 IE11 CU.
-
anonymous
GuestMarch 23, 2020 at 5:50 pm #2210312Well it seems that after 3 reboots it is working. Not sure what was going on.
-
analogkid
AskWoody PlusMarch 23, 2020 at 6:02 pm #2210321OK, so I need to skip the Feb SO updates and instead download the March SO updates instead?
I had just figured I would installed the Feb updates as we are still on DefCon 2 with the March updates.
Thanks PK. I may still have to wait until my IT brother visits and let him do it so he can show me in person. Who knows how long that will be though
I feel so stupid when it comes to this “stuff”
Also what I meant is that I have installed already the two prior SSU’s. I checked my installed updates just to be sure and they are listed.
"An analog kid in a digital world"
Win7 Ultimate home built desktop Running 0patch Pro
Two former 8.1 Laptops & two desktops now running Win 10
Win 10 Dell desktop
-
PKCano
ManagerMarch 23, 2020 at 6:23 pm #2210327You need the Feb and Mar SO (KB4537813 and KB4541500).
You need the Mar IE11 CU (KB4540671).
You need the Mar SSU KB4550735
All of them in the folder with the script3 users thanked author for this post.
-
Elly
AskWoody MVPMarch 23, 2020 at 7:23 pm #2210343I feel so stupid when it comes to this “stuff”
From a non-techy who is attempting to embrace tech- you aren’t stupid. You are asking questions, learning the terminology, and applying it to your personal situation. Pretty darn smart, if you ask me!
And the more you hang around here, the more you will learn… and the more it will make sense.
Also, the more you know, the better you can converse with your IT brother… if tech can improve your bonding… so much the better!
Just know that if you follow PKCano’s instructions, it will do what you want it to do… always works for me!

Non-techy Win 10 Pro and Linux Mint experimenter
-
RDRguy
AskWoody LoungerMarch 23, 2020 at 8:15 pm #2210352Finally took the plunge and converted two fully up-to-date non-ESU Win7 “Group B” test systems to “Group A” by first installing KB4534310 (2020-01 Monthly Quality Rollup) then KB4536952 (2020-01 SSU).
After successful reboot, used @abbodi86’s automated batch script to install the following ESU updates:
2020-02 – KB4537829 (Feb SSU)
2020-03 – KB4550735 (Mar SSU)
2020-02 – KB4537820 (Feb Monthly Quality Rollup)
2020-03 – KB4540688 (Mar Monthly Quality Rollup)ESU batch script processed both SSUs first then both Monthly Rollups successfully.
After reboot, the installed updates (via the control panel) listed both SSUs & the Mar Rollup as installed. As expected, the Feb Rollup was not installed due to supersession by the Mar Rollup. A subsequent Windows Update found only the March 2020 MSRT.
Afterwards, performed a couple of Windows Update offline scans via the Microsoft Baseline Security Analyzer (MBSA) tool using the current wsusscn2.cab file.
As the MBSA tool is no longer available for download as described here, I also performed additional offline scans via Powershell using a .vbs script found here and a .ps1 script found here.
MBSA and both Powershell offline scan scripts indicate the following updates are still missing:
2019-10 – KB4519108 (DST changes for Norfolk Island and Fiji Island)
2020-02 – KB4538483 (ESU Licensing Preparation Package)Interesting that KB4519108 is found via offline scanning but not via the normal WU scan since it’s pre-ESU, it’s not installed & it’s not hidden. No real concerns about the DST update as I don’t live on Norfolk or Fiji Islands.
But, have a question for @abbodi86 and/or other AskWoody_MVPs in the know concerning KB4538483 …
Should non-ESU Win7 updaters now in “Group ABS” (Abbodi86’s Batch Script) be concerned about the missing ESU Licensing Prep Package KB4538483 on non-ESU systems being patched with ESU updates?
Win7 - PRO & Ultimate, x64 & x86
Win8.1 - PRO, x64 & x86
Groups A, B & ABS -
analogkid
AskWoody PlusMarch 23, 2020 at 8:40 pm #2210365Wow, I did it!! I kept trying and then recalled that I did something similar years ago with a file named “pciclearstalecache”.
I surprised myself when I hit the zero key and it began the installation process.
I waited a long time to reboot and then let it sit another good long time before signing in. Just checked the installed updates and I see four listed with today’s date./
I am also using 0patch Pro and so far it is working fine.
WOO HOO
Thank you to everyone in this thread, PK and of course abbodi.
BTW, I have been on askwoody site for many, many years as a devoted Group B’er. I decided to join as a Plus Member recently.
"An analog kid in a digital world"
Win7 Ultimate home built desktop Running 0patch Pro
Two former 8.1 Laptops & two desktops now running Win 10
Win 10 Dell desktop
-
abbodi86
AskWoody_MVPMarch 23, 2020 at 9:14 pm #2210371KB4538483 is solely ment for actived ESU-license customers to recieve ESU updates via WU.
no other purpose for non-ESU users, and the update contents are already included in the Monthly Rollup.now if you installed it and checked wsusscn2.cab again, it will still not show ESU updates (installed or not)
because WU engine check the status of active ESU license before it show the updates -
RDRguy
AskWoody LoungerMarch 23, 2020 at 9:42 pm #2210380Thanks, I kinda figured that but just had to ask if NOT having the ESU Prep Pkg Update installed could potentially result in unforeseen problems with having the ESU updates installed in non-ESU systems.
Win7 - PRO & Ultimate, x64 & x86
Win8.1 - PRO, x64 & x86
Groups A, B & ABS -
Ulti P. Uszer
AskWoody LoungerMarch 24, 2020 at 1:23 am #2210410@Woody, with this development, I hope you didn’t buy a ESU license for 7 Semper Fi. Are you still using that machine? I also know personally that abbodi86’s other script that brings 7 ESUs through WU also works magnificently.
Been disabling secure boot and other tomfoolery for over 10 years now.
I run IoT 11 in MBR. -
byteme
AskWoody PlusMarch 24, 2020 at 11:33 pm #2210702Win7 Home Premium 64-bit. Group B.
I just used abbodi86’s .cmd script to install the February Win7 64-bit security-only updates.
SHA2 support updates KB4490628 and KB4474419 had already been installed on my PC (in April and September, respectively, of 2019).
I put four files in an otherwise-empty folder: (1) abbodi86’s .cmd file, (2) the Feb. SSU (KB 4537829), (3) the Feb. Win7 SO update (KB 4537813), and (4) the Feb. IE SO update (KB 4537767).
Then I right-clicked on the .cmd file, chose Run as Administrator, and hit 0 in response to the opening menu.
The process took just about exactly 30 minutes. Then I rebooted, and then I ran (as Administrator) the RunOnce anti-telemetry file that the .cmd script had deposited on my desktop.
Everything seems fine, I thank abbodi86 for his assistance, and I plan to do the March updates the same way (when their time has come).
5 users thanked author for this post.
-
anonymous
GuestMarch 27, 2020 at 12:18 pm #2211481At first: To abbodie, many thanks for your tool !
A question:
I use the Group A scenario with rollups.
And I want to know, if I don’t update for many months,
can I restart the updates from the most recent month rollup ?
Skipping all the months in between ?Thanks
Frankie -
PKCano
ManagerMarch 27, 2020 at 12:25 pm #2211492And I want to know, if I don’t update for many months, can I restart the updates from the most recent month rollup ? Skipping all the months in between ?
Technically, and in normal circumstances, the answer would be Yes, since Group A Rollups are cumulative.
BUT:
+ There is no guarantee that @abbodi86 ‘s script will work next month, or the month after. Microsoft may put another roadblock in the works. They won’t be happy with people getting for free, what they are charging subscription fees for.
+ There will probably be other qualifying installs, like the SSU changing.As long as things stay like they are, skipping monthly patches may work. But who knows??
1 user thanked author for this post.
-
Frankie
AskWoody LoungerMarch 27, 2020 at 1:15 pm #2211520Thanks PKCano,
I should have said: “if I DIDNT update for many months” for the lasts months.
So I will update my others PCs rapidly!Frankie
-
PKCano
ManagerMarch 27, 2020 at 1:16 pm #2211525Be sure you have the prerequisites installed – listed above.
-
anonymous
GuestMarch 28, 2020 at 4:45 am #2211750I have already installed the SHA2 support updates KB4490628 and KB4474419 since the time of their release (more or less). Today, I have followed the advice of PKCano in #2210327 above. After rebooting, the four new updates are now listed in my “installed updates” and everything seems to work fine up to now.
System: Win7 x64 Ultimate and “Group B”.
Note: “RunOnce_W10_Telemetry_Tasks.cmd” did not appear, probably because I have already set the script “W10Tel.cmd” to run on startup as a scheduled task. No additional telemetry related tasks or services have shown.
Many thanks to abbodi86 for the scripts he provides and the people in this forum offering their knowledge.
Tryfonas
1 user thanked author for this post.
-
Moonbear
AskWoody LoungerMarch 28, 2020 at 11:36 am #2211818How does this script work with the Group A rollups?
I didn’t think you could use the rollups with the script since they aren’t individually downloaded files. Or is there another way to get the rollups besides Windows Update?
-
PKCano
ManagerMarch 28, 2020 at 11:42 am #2211820You can download the Rollups from the MS Update Catalog. Enter the KB number without the “KB” (just the numerical part) and download the one that is right for your OS version and bitedness.
Or you could use one of the download managers WUMgr, Sledghammer, etc.
-
Moonbear
AskWoody Lounger -
Mcinwwl
GuestMarch 28, 2020 at 1:08 pm #2211829Hi, I used the script to install updates for Windows 7 and internet explorer, and I noticed two side effects:
- after restarting, I got prompted to wait when Windows applies updates (obvious). When it ended, PC rebooted itself… and hang on black screen. Not even Bios was initiated.
yuck… why? This is the first occurrence of such misbehaviour in 4-years lifespan of this machine… After another reset, PC booted as usually. - i was offered KB3118401 update. It was purposedly not-installed and hidden due to potential connection with M$ snooping, as listed in: https://msfn.org/board/topic/173752-how-to-avoid-being-upgraded-to-win-10-against-your-will/?tab=comments#comment-1097746
- after restarting, I got prompted to wait when Windows applies updates (obvious). When it ended, PC rebooted itself… and hang on black screen. Not even Bios was initiated.
-
PKCano
ManagerMarch 28, 2020 at 1:16 pm #2211834Did you have the prerequisites (KB4490628 and KB4474419) installed first?
Did you include the required Servicing Stack KB4550735?KB3118401 is an update for Universal C Runtime. The MS pages say:
The Windows 10 Universal CRT is a Windows operating system component that enables CRT functionality on the Windows operating system. This update allows Windows desktop applications that depend on the Windows 10 Universal CRT release to run on earlier Windows operating systems
-
Mcinwwl
AskWoody LoungerMarch 28, 2020 at 1:28 pm #2211835Servicing stack was applied, following the readme script should recognize it and install before other updates, right?
Prequisites were installed, I checked using powershell’s get-hotfix.
KB3118401 do not look like a necessary prequisite. However, if you think it should not be considered part of microsoft snoopware, I will inform original thread author from MSFN to remove it from the list.
PS past post is mine… you took me by suprise, I have never ever used forum where one can comment as a guest
-
Mattchu
AskWoody LoungerMarch 29, 2020 at 8:46 am #2212103Just wanted to join to say a big thank you to aboddi86 & PKcano especially for the creation of this and the help supplied to various people.
Just so Im clear, I dont use Windows 7 much anymore but do have a few boxes that its on, my old man however does still use it and I want to get him up to date. I think group A is the way I`ll go. So Ive checked the prerequisites KB4490628 and KB4474419 installed, Jan SSU [KB4531786] installed, everything done until EOL.
Downloaded the March CU [KB4540688] and the latest SSU [KB4550735] and placed them in the same folder as the extracted W7ESUI.cmd [as picture]
Now it should be a case of right click W7ESUI.cmd and “run as administrator”? I don`t need the February CU [KB4537820] or any other SSU?
Cheers

-
PKCano
ManagerMarch 29, 2020 at 8:49 am #2212106Now it should be a case of right click W7ESUI.cmd and “run as administrator”? I don`t need the February CU [KB4537820] or any other SSU?
That’s correct.
After the reboot, if it asks for one, run the RunOnce_W10_Telemetry_Tasks.cmd if it appears on your desktop to eliminate the telemetry. -
Mattchu
AskWoody LoungerMarch 29, 2020 at 9:19 am #2212110Cheers PKCano, much appreciated I`ll post back with the results, just doing the first test box now
-
maisy2
AskWoody PlusMarch 29, 2020 at 1:27 pm #2212171I didn’t know if it was good or bad, but I too thought Rollups were better at the EOL era after being strictly security-only all these years.
Foldered: W7ESUI.cmd / KB4550735 March SSU / KB4537820 (Feb Monthly Quality Rollup)Everything purposefully disabled in task scheduler was untouched after the Rollup install.
– or was it the Telemetry neutralize tweaks?:)
So nothing changed, although, the Installed Updates window got a clean-up albeit for a load of Microsoft .Net Frameworks; but comforting to find you can find old security-only numbers and older ssu’s if you place what you’re looking for in the upper corner search.I hope the coming month will still allow theW7ESUI, SSU & March rollup combo to install through this brilliant development.
The ReadMe has’# for offline integration’; I had disabled WU and didn’t go offline, # for offline integration meant for the desktop RunOnce_W10_Telemetry_Tasks.cmd but was too hasty to take this into account – I shall do it offline if i get to install again next month.Thanks to Creator of this, and wonderful and educational to read the poster’s questions and results on here. Big thank you.
-
This reply was modified 5 years, 2 months ago by
maisy2.
-
This reply was modified 5 years, 2 months ago by
Kirsty.
1 user thanked author for this post.
-
This reply was modified 5 years, 2 months ago by
-
abbodi86
AskWoody_MVPMarch 29, 2020 at 9:52 pm #2212231@Mcinwwl
Universal C Runtime (KB3118401 or KB2999226) is part of VC++ 2015-2019 redistributable, which is used by Office 2016 and later, Firefox, Edge Chromium and otherswhile most of them bundle it locally, it’s best practice to have it globally installed
and it has nothing to do with telemetry or snooping -
Moonbear
AskWoody Lounger -
anonymous
GuestMarch 31, 2020 at 3:40 pm #2212735Hi,
I have been installing the monthly roll-ups, the last updates I see when checking for updates with WU, is the 01-2020 monthly preview.
So I understand I only need the latest march monthly roll-up and SSU, but what about the security roll-up for .NET, is that no longer being updated?
Thanks
-
abbodi86
AskWoody_MVP -
HanJohnJo
AskWoody PlusApril 1, 2020 at 2:50 am #2213311I might have missed something, for sure. But we are now in April and the MS-defcon for the March updates is still at 2 but I can’t see the reason, at least for Win 7. After almost one month patch reliability is still unclear? Maybe now MS-defcon applies only to Win 10 updates.
Frangar non flectar
-
Paul T
AskWoody MVP -
anonymous
GuestApril 1, 2020 at 4:23 am #2213316Win7 ult x64 updated normally via WU, last update 3 updates were:
Windows Malicious Software Removal Tool x64 – February 2020 (KB890830)
2020-01 Servicing Stack Update for Windows 7 for x64-based Systems (KB4536952)
2020-01 Security Monthly Quality Rollup for Windows 7 for x64-based Systems (KB4534310)I have extracted W7ESUI zip into a folder, along with the following files:
windows6.1-kb4550735-x64_18117664b4a0482c3d34a2f05f70c6819296240f
windows6.1-kb4540688-x64_70ad29faea4602dfa5c3159350afe6ec86e87e52I ran the cmd as admin, and it detected the files.
It installed kb4550735, but it didnt prompt for restart, it just said “finished” and I had to press 9 and then manually restarted.
I checked installed updates after restart and kb4550735 was there.I then did the same again, it extracted the kb4540688 cab, but then it finished stating ” All applicable updates are detected as installed”
I tried also with the Feb SSU and Monthly rollup, but same thing.
I did install the first SSU kb4550735 while the internet was disabled, but when installing the rollup the net was enabled, would that have anything to do with it?
Also, just a note, would it be possible to not auto delete the extracted cab file or an prompt, as I tried many times, and each time it had to extract again.
thanks.
-
PKCano
ManagerApril 1, 2020 at 4:28 am #2213321Did you have the prerequisites (KB4490628 and KB4474419) installed first?
-
abbodi86
AskWoody_MVPApril 1, 2020 at 4:55 am #2213327The cab and temporary files are extracted to randomly-named temporary folder
they cannot be preserved for later usageare you sure kb4540688 is not already installed?
did you verify the integrity of downloaded msu file? -
Douglas
AskWoody PlusApril 1, 2020 at 2:30 pm #2213430I am a Win7 x64 Pro Group B user. I just finished using the script to install the March updates, KB4540671 and KB4541500. Everything seemed to run fine. It reported both installs were 100% successful.
However, just before it started removing the temporary files and asking me to press 9, it gave me the following message:
==== Error ====
Windows6.1-KB4541500-x64 require SSU version 6.1.7601.24548Is that the servicing stack update KB4550735 that is also a March ESU-only update? I restarted and everything seems to be running just fine. But should I also download that update and use the script to install it?
Thank you.
-
PKCano
ManagerApril 1, 2020 at 2:38 pm #2213434KB4540671 is the IE11 Cumulative Update.
KB4541500 is the Security-only UpdateYou need to install the Servicing Stack KB4550735, which is REQUIRED. That must also be in the folder with the other updates.
-
Douglas
AskWoody PlusApril 1, 2020 at 2:44 pm #2213439Should I rerun the script with all 3 in the folder, or would it be okay with just KB4550735?
Thanks.
-
PKCano
Manager -
honx
AskWoody LoungerApril 1, 2020 at 5:21 pm #2213490since we’re on defcon 3 now, do we already know if it’s “safe” to install esu updates using this script (without paid license)? or will windows 7 be not activated/”pirated” at some point in the future? i read something like this, so i’d rather ask before doing anything.
PC: Windows 7 Ultimate, 64bit, Group B
Notebook: Windows 8.1, 64bit, Group B -
You.Are.Ah.Toyyyyy
AskWoody LoungerApril 1, 2020 at 6:59 pm #2213514Did you have the prerequisites (KB4490628 and KB4474419) installed first?
I went into installed updates and found both of them:
Update for Microsoft Windows (KB4490628) Installed 21/03/2019
Security Update for Microsoft Windows ( KB4474419 ) Installed on 19/09/2019The cab and temporary files are extracted to randomly-named temporary folder
they cannot be preserved for later usageare you sure kb4540688 is not already installed?
did you verify the integrity of downloaded msu file?Just checking Installed updates again.
kb4550735 is there and also kb4537829, so the Feb ssu seems to have installed. But the rollups aren’t installing.windows6.1-kb4540688-x64_70ad29faea4602dfa5c3159350afe6ec86e87e52.msu
sha512: D10FCB521D406564DBE2BFCA78BE9E0D95E22998A57EF204A02DE03CDF64619D3B210694F15CA351C89C39D3E992E0DB80E0C2B6AD3963395E0498D856ED5468windows6.1-kb4537820-x64_3ee2a66a320dfe4eea2bda70bf9b5471b014f2a3.msu
sha512: F5ABF6072C73ECAD556F83F90778A04469785B5365B4941115FA8EEB76455189E550750361A239FB13AA9E7C3D1D8F5DA3CD6A1A5270B3038E9BDD934CB44FE1BTW, windows update is still popping up showing me updates to install:
Windows Malicious Software Removal Tool x64 – March 2020 (KB890830)
2020-01 Preview of Monthly Quality Rollup for Windows 7 for x64-based Systems (KB4539601)thanks again.
-
You.Are.Ah.Toyyyyy
AskWoody LoungerApril 1, 2020 at 10:46 pm #2213569After checking the AV and other things that might be interfering, I tried again and it still gave the message “All applicable updates are detected as installed”.
So I looked over the readme a few more times, and thought I had better double check the storage space. It was low, but I wasn’t sure how much space the final extracted files took, so I deleted some files to meet the recommended 10gb free space.
After trying once more, it finally worked, and the installation completed and the update was visible in the Installed Updates list.
Is there maybe a way to alert that there wasn’t enough storage when extracting the files during installation? Because at the moment, even though it seems all the files were not successfully extracted, the final message was simply no update was necessary.
-
Cybertooth
AskWoody PlusApril 2, 2020 at 12:10 am #2213602Shortly (~45 sec.) after running the script for the February patch batch, Bit Defender popped up an alert:
False positive? Unrelated coincidence?
-
Paul T
AskWoody MVPApril 2, 2020 at 3:29 am #2213632BD is looking for activities that change Windows itself and that is exactly what the script does, so the report is correct. You can safely ignore the warning because you want Windows changed.
cheers, Paul
2 users thanked author for this post.
-
EP
AskWoody_MVPApril 2, 2020 at 11:03 am #2213719Shortly (~45 sec.) after running the script for the February patch batch, Bit Defender popped up an alert:
False positive? Unrelated coincidence?
add the script to “exclusion” or Ignore list in BitDefender
1 user thanked author for this post.
-
EP
AskWoody_MVPApril 2, 2020 at 11:08 am #2213721Did you have the prerequisites (KB4490628 and KB4474419) installed first?
I went into installed updates and found both of them:
Update for Microsoft Windows (KB4490628) Installed 21/03/2019
Security Update for Microsoft Windows ( KB4474419 ) Installed on 19/09/2019The cab and temporary files are extracted to randomly-named temporary folder
they cannot be preserved for later usageare you sure kb4540688 is not already installed?
did you verify the integrity of downloaded msu file?Just checking Installed updates again.
kb4550735 is there and also kb4537829, so the Feb ssu seems to have installed. But the rollups aren’t installing.windows6.1-kb4540688-x64_70ad29faea4602dfa5c3159350afe6ec86e87e52.msu
sha512: D10FCB521D406564DBE2BFCA78BE9E0D95E22998A57EF204A02DE03CDF64619D3B210694F15CA351C89C39D3E992E0DB80E0C2B6AD3963395E0498D856ED5468windows6.1-kb4537820-x64_3ee2a66a320dfe4eea2bda70bf9b5471b014f2a3.msu
sha512: F5ABF6072C73ECAD556F83F90778A04469785B5365B4941115FA8EEB76455189E550750361A239FB13AA9E7C3D1D8F5DA3CD6A1A5270B3038E9BDD934CB44FE1BTW, windows update is still popping up showing me updates to install:
Windows Malicious Software Removal Tool x64 – March 2020 (KB890830)
2020-01 Preview of Monthly Quality Rollup for Windows 7 for x64-based Systems (KB4539601)thanks again.
install the KB4539601 rollup first.
Jan. 2020 rollups (either KB4534310 or KB4539601) are also required before installing any new ESU based updates from Feb. 2020 and later
-
abbodi86
AskWoody_MVPApril 2, 2020 at 3:02 pm #2213810Neither KB4539601 or kb4537820 are needed, March rollup kb4540688 is enough
@You.Are.Ah.Toyyyyy
the numbers/letters before .msu extension are SHA1 hash, you should verify against that -
You.Are.Ah.Toyyyyy
AskWoody LoungerApril 3, 2020 at 1:19 am #2213962I already posted an update yesterday a few posts up, thanks.
-
This reply was modified 5 years, 2 months ago by
You.Are.Ah.Toyyyyy.
1 user thanked author for this post.
-
This reply was modified 5 years, 2 months ago by
-
maisy2
AskWoody PlusApril 3, 2020 at 3:40 pm #2214165Grateful I got to install the March rollup too now that it’s April.
In a roundabout way this is great as I’ve finally found that the new rollup does immediately overwrite the previous month’s rollup in the Update history. – it’s no more, gone even in searching for it at the top corner. I’ve been unsure of this in updating my reset win 8.1 laptop since the start of the year. I wasn’t sure rollups overwrite instantly after new updates. This fact couldn’t be found online, leaving me wondering if my pc was malfunctioning. And it did not help that I find Ms Mvp saying in a slightly older MS answer forum that if it’s not in the Update history opposed to the Windows history that it is not installed.
Sorry for my long-windedness but I wish there was a written notation by MS to affirm this. All this for being new to cumulative rollups.
The Update history that was thought to be cleaned-up has reappeared whole again as well. So glad I got to do this in two parts. Thank you. -
PKCano
ManagerApril 3, 2020 at 3:47 pm #2214170Rollups are CUMULATIVE. That means the later one contains the one(s) before. SO, once the March Rollup is installed it would be redundant to have the Fem also listed b/c it is contained in the Mar Rollup. So the Feb, Jan, Dec, Nov…. Rollups are no longer listed.
1 user thanked author for this post.
-
Chriski
AskWoody PlusApril 3, 2020 at 3:56 pm #2214174I have 3 Win 7 laptops I have been keeping up to date. I used this wonderful script on two of them, and it went without a hitch. I moved onto the 3rd today with full confidence…
I have also been venturing into win7/kubuntu dual boot territory because of the online implications of using win 7 for important things. This 3rd machine is the dual boot machine and my guess is that is why the update try went awry.
The cmd file displays a line about a “patchable module etc.” and then exits. Opening up a cmd window as admin and executing the script yields the same start and an exit with “syntax of the command is incorrect.” I edited the cmd file, turned of echo, and turned on debug, but my capability with command files is limited and quite rusty.
I fear this is a very lot to ask, but I was hoping that after a quick look (it doesn’t take long to exit) you might be able to suggest something simple that might help the script to get on it’s way.
Or a simple answer (understandably) is that my situation is beyond the scope of the original design intent, and is not worth the time and effort.
Thanks in advance,
Chris
-
maisy2
AskWoody Plus -
davinci953
AskWoody PlusApril 3, 2020 at 11:53 pm #2223045The same thing is happening on my Windows 7 system. The command window opens, indicates that “Patchable module found: C:\Windows\system32\GDI32.dll with hash 4dd319b1e6b8a09d121ad669dbcbab95bacad64e”, and then closes. February updates ran as expected, and I have the March SSU installed, but I can’t get it to work with the March updates (security only).
-
abbodi86
AskWoody_MVPApril 4, 2020 at 5:50 am #2223229Are you using 0patch?
https://0patch.zendesk.com/hc/en-us/articles/360012826660–Patchable-module-found-string-appears-in-console-based-applicationsyou don’t really need W7ESUI.ini for live os installation, so just delete it and try again
for some reason, the script fail to set the required variables correctly because of W7ESUI.ini presence
so it error and exit before doing anything-
This reply was modified 5 years, 2 months ago by
abbodi86.
-
This reply was modified 5 years, 2 months ago by
abbodi86.
-
This reply was modified 5 years, 2 months ago by
abbodi86.
2 users thanked author for this post.
-
This reply was modified 5 years, 2 months ago by
-
Chriski
AskWoody PlusApril 4, 2020 at 10:56 am #2223290Are you using 0patch?
https://0patch.zendesk.com/hc/en-us/articles/360012826660–Patchable-module-found-string-appears-in-console-based-applicationsyou don’t really need W7ESUI.ini for live os installation, so just delete it and try again
for some reason, the script fail to set the required variables correctly because of W7ESUI.ini presence
so it error and exit before doing anythingI (of the 3 Win 7 laptops above) AM using 0patch. A study of running them together via this thread and 0patch lead me to conclude it would probably be ok, and I tried 0patch on the 3 machines first.
Anyway, got rid of the .ini file, and the script is running and chugging along right now. Thanks for your help.
(NB: I did NOT remove the ini file on the other 2 laptops, and the script ran fine. They also have 0patch. Also the “patchable module” message was gone on the latest one — 0patch probably updated. I saw a note to that effect.)
Chris
-
davinci953
AskWoody Plus -
Chriski
AskWoody PlusApril 4, 2020 at 2:15 pm #2223339abbodi’s suspicion that 0patch had a tie in to the script erroring out was right on.
I circled back (out of curiosity) and put the ini file back in with the cmd script, and with 0patch now fixed (according to the link posted above from 0patch.zendesk), the script runs through to asking to proceed or exit, which is past where the problem was occuring.
You are truly a wizard, sir!
Thanks for all you do.
Chris
3 users thanked author for this post.
-
anonymous
GuestApril 6, 2020 at 2:59 pm #2223870I just downloaded W7ESUI and the March Cumulative Update (KB4540688). I assume I do not need to install the February Cumulative Update first.
Do I need to install Service Stack Updates?
If I will need SSIs, how do I find out which ones I need?
-
PKCano
Manager -
anonymous
GuestApril 7, 2020 at 2:49 pm #2224054The script said it installed
KB4537828 – Feb SSU
KB4550735 – Mar SSU
KB4537820 – Feb Monthly and
KB4540688 – Mar Monthly in that order
But KB4537820 – Feb Monthly does not show up as installed in Windows Update?
The other three are there.
-
PKCano
ManagerApril 7, 2020 at 2:54 pm #2224058Monthly Rollups are CUMULATIVE.
By definition, Mar Rollup KB4540688 contains Feb Rollup KB4537820 and the preceding Rollups from Jan, Dec, Nov, etc, So it is no longer necessary to list the older Rollups (it would be redundant). -
KP
AskWoody Plus -
anonymous
GuestApril 7, 2020 at 5:51 pm #2224091Thanks much for all the help you give to me and everyone.
-
KP
AskWoody PlusApril 7, 2020 at 6:08 pm #22240950x800f081f – solution if this helps someone.
First, thanks to @abbodi86 for the 5-star W7ESUI.cmd .
This came about, installing patches in this order:
2020-02 Service Stack Update – KB4537829
2020-02 Monthly Rollup – KB4537820
2020-03 Service Stack Update – KB4550735
2020-03 Monthly Rollup – KB4540688(I know I did not need to run the February SSU and February Monthly Rollup, but I did it as an experiment.)
You can see it failed on the 2020-03 Monthly Rollup – KB4540688 {Failed 0x800f081f(1).PNG}
I let Windows Update run and you can see, it installed:
.NET 4.8 KB4503548
Windows 7 Update KB2952664
2019-07 Windows 7 Update KB4493132{WindowsUpdates for W7ESUI.PNG}
The last two are Telemetry
KB2952664 – see AKB2000004, AKB2000007
KB4493132 – see AKB2000003My guess is that .NET 4.8 (KB4503575) allowed KB4540688 (2020-03 Monthly Rollup) to succeed using W7ESUI. This you can see in the Program&Features picture{Program&Features.PNG}.
oddities:
1) .NET 4.8 shows up as KB4503548 in Windows Update and as KB4503575 in Program&Features
2) KB4537820 (2020-02 Monthly Rollup) is missing in the Program&Features listing, as noted in previous posts.After you get the March patches installed, you can remove the Telemetry in the following order (or not install them in the first place):
KB4493132
KB2952664
-
This reply was modified 5 years, 1 month ago by
KP.
-
This reply was modified 5 years, 1 month ago by
KP.
-
This reply was modified 5 years, 1 month ago by
KP.
-
This reply was modified 5 years, 1 month ago by
Kirsty.
2 users thanked author for this post.
-
This reply was modified 5 years, 1 month ago by
-
Mattchu
AskWoody Lounger -
PKCano
ManagerApril 14, 2020 at 2:54 pm #2241426You also need the SSU KB4550738
-
Mattchu
AskWoody LoungerApril 14, 2020 at 3:15 pm #2241446 -
anonymous
GuestApril 14, 2020 at 6:58 pm #2241608I am on Windows 7 Home Premium 32 bit. I successfully installed SSU KB4550738 with the script and rebooted. Then I successfully installed the April 14, 2020 rollup—KB4550964. What’s weird is it did not ask me to reboot the system after installing the rollup. I checked installed updates and KB4550964 was listed. I rebooted anyway and my machine simply rebooted without configuring updates. This KB includes kernel updates so how could this install without configuring on a reboot?
-
EP
AskWoody_MVP -
RDRguy
AskWoody LoungerApril 14, 2020 at 9:10 pm #2241663Can anybody comment on what/why it was changed (e.g. bug fixes, new capability, etc) and whether or not we should now be using the updated 0.2 version vs the original 0.1 version?
Edit: Answered my own question …
Opened the Changelog contained in the “W7ESUI-ReadMe” file which states …– 0.2:
added support to install SHA2 updates KB4490628 and KB4474419 if detectedThat answers that
Win7 - PRO & Ultimate, x64 & x86
Win8.1 - PRO, x64 & x86
Groups A, B & ABS-
This reply was modified 5 years, 1 month ago by
RDRguy.
-
This reply was modified 5 years, 1 month ago by
-
abbodi86
AskWoody_MVPApril 14, 2020 at 9:49 pm #2241682I was waiting to confirm that the procedure is still working with April updates, before announcing v.0.2
the second version simply add support to install SHA2 support updates, if not already installed
meaning, put msu files for KB4490628 and KB4474419 along with ESU updates msu files, and the script will install them for you first5 users thanked author for this post.
-
Moonbear
AskWoody LoungerApril 14, 2020 at 9:55 pm #2241685 -
abbodi86
AskWoody_MVP -
anonymous
GuestApril 16, 2020 at 4:46 am #2242282Any urgent need to install the April ESU updates?
-
PKCano
ManagerApril 16, 2020 at 4:47 am #2242285No emergencies at this point. You can wait for DEFCON-3 or above (or whenever you decide to do it).
-
PKCano
Manager -
anonymous
GuestApril 16, 2020 at 5:10 pm #2242560Do Monthly Rollups include updates to IE? How about .NET Framework? If I remember correctly .NET Framework were separate updates in Windows Update.
-
anonymous
GuestApril 17, 2020 at 11:22 am #2242782How does the script W7ESUI.cmd get added to “exclusions” in BitDefender? No matter how I try to enter it I get an “Invalid Path” message.
-
anonymous
Guest -
PKCano
Manager -
Cybertooth
AskWoody PlusApril 17, 2020 at 1:58 pm #2242837To do this, open Settings in the BitDefender window (it’s the cog wheel at top right), then in the drop-down menu select Exclusions. From there, click on Add Exclusion and navigate to the file/folder that you want to exclude, and select it.
That’s it!
-
anonymous
GuestApril 17, 2020 at 3:59 pm #2242879I got it to add but it looks like this w7esui[1].cmd. Where did the [1] come from and what is it doing there? Is it OK that way?
-
Cybertooth
AskWoody PlusApril 17, 2020 at 4:08 pm #2242881That suggests that you’ve ended up with two copies of that .CMD file in the same folder. For example, if you have a file called baberuth.jpg in your Downloads folder, and then from a USB flash drive you copy a file called baberuth.jpg onto the same Downloads folder, the file that you just copied over will have that “[1]” added to its file name so that you can tell it apart from the one you already had.
Look for the folder(s) where you’re storing the files w7esui.cmd and w7esui[1].cmd. You should discover that you have a copy of each in the same folder somewhere.
-
anonymous
GuestApril 17, 2020 at 4:33 pm #2242883It says I need these items
a) if you are Group A user, you need:
latest Servicing Stack Update
latest Security Monthly Rollup
latest .NET rollupI see the SSUs that are needed listed in the docs for the Monthly Rollup. But I can’t find anything on what .NET rollups (latest?) are needed. Nor do I have any idea on where to find .NET rollups.
Please excuse my lack of knowledge.
-
EP
AskWoody_MVPApril 17, 2020 at 9:35 pm #2247729latest .NET Rollup for Windows 7 is KB4535102 from Jan 2020 – nothing higher than that:
https://support.microsoft.com/help/4535102/ -
EP
AskWoody_MVPApril 17, 2020 at 9:37 pm #2247785only if you have not installed the latest one
latest .NET rollup for Win7 is KB4535102 (as I said below) before “free” support for Win7 ended in mid-January 2020
-
anonymous
GuestApril 18, 2020 at 10:37 am #2251961Confused. KB4535102 shows as successfully installed 1/24/2020 in update history, but comes up as “No items match your search.” in Installed Updates. Of course it does not come up in Windows Update.
Is it installed or is it not installed?
Should I pull it from the catalog and try installing it using W7ESUI?
-
PKCano
ManagerApril 18, 2020 at 10:45 am #2251965Look on the MS pages for KB4535102.
KB4535102 is a .NET Rollup composed of a bundle of individual patches for each of the versions of .NET
The Rollup’s KB number will not show up in Installed Updates, but any of the individual patches that were installed will be listed.
Look under the section “Additional information about this update.” If any of those KB numbers show in Installed Updates, those are the version(s) of .NET installed on your computer that received updates.1 user thanked author for this post.
-
anonymous
GuestApril 18, 2020 at 4:39 pm #2252014KB4532945 shows in installed updates. Now I can stop being concerned about this. Thank you.
-
anonymous
GuestApril 21, 2020 at 6:39 pm #2252964You are very good at explaining things in a way that even I can understand. Thank you.
1 user thanked author for this post.
-
glnz
AskWoody PlusApril 27, 2020 at 8:23 am #2255853It’s April 27. Is this still working? Thanks,
-
PKCano
ManagerApril 27, 2020 at 8:35 am #2255855The script and instructions were revised for the April updates.
-
glnz
AskWoody PlusApril 27, 2020 at 9:29 am #2255873PKCano – what would we do without you? What is Defcon for the April updates for Win 7 Pro 64-bit?
-
PKCano
ManagerApril 27, 2020 at 9:36 am #2255874The DEFCON number displayed at the top of the site applies to ALL versions of WIndows. Current month = April
-
anonymous
GuestApril 29, 2020 at 9:32 am #2257425Hi,
May be I am actually a dim person but I can’t work out from the instructions for th Stand alone script for Win7 ESU.No problem with downloading the W7ESUI.cmd and W7ESUI.ini, the next part is where I fail. . . . . what exactly does place W7ESUI.cmd next to the download files mean?
Put them all in a new folder?
I tried that and nothing happened. So I tried entering the Windows 7 update file location in 2] select updates location in the command window and the returned message is ‘specified location is not valid’.
The update is in a folder on the C: drive – c:\win7sp1_esu\Win7SP1-kb4550964-x86Any advice, suggestion, instruction would be most welcome.
Many thanks.
-
PKCano
ManagerApril 29, 2020 at 9:34 am #2257453what exactly does place W7ESUI.cmd next to the download files mean? Put them all in a new folder?
Yes, everything in the same folder then execute the script.
-
Gordski
AskWoody PlusApril 29, 2020 at 11:01 am #2257491Yes, and I already did that to no avail. Does it not need me to enter the location of the update at line 2] of the script. But when I do that it doesn’t accept the location of the Windows7 update file, as I pointed out in the previous post (please refer back to it).
Any other suggestions?
Thank you and best regards,
Gordon -
PKCano
ManagerApril 29, 2020 at 11:18 am #2257497– Extract W7ESUI.cmd from the zip file, or extract the whole zip file
– Copy or move W7ESUI.cmd and place it next to (in the same folder as) the downloaded msu files
ini file W7ESUI.ini is not really necessary in this case– Right-click on W7ESUI.cmd and “Run as administrator”
– If all goes well, you should get cmd window
– Now press the zero 0 number on keyboard to start the process
– At the end, restart the system if prompted
-
Cybertooth
AskWoody PlusApril 29, 2020 at 11:55 am #2257520The wording about placing the CMD file “next to” the MSU files has generated more than one question. (I would have been added to the list had I not seen the first time it was posed.) It may help to edit the original instructions to direct the user to place the CMD file in the same folder as the MSU files; that way you won’t have to keep explaining what “next to” means.
-
WSRobF228
AskWoody PlusApril 29, 2020 at 1:37 pm #2257538I’m a home user with Win7 x64 pro. Just using a workgroup for the household. Am I a “Group A” user?
Thank you much!
-
PKCano
ManagerApril 29, 2020 at 1:40 pm #2257540If you have been installing the Monthly Rollups through Windows Update, you are a Group A user.
If you have been downloading from the MS Catalog and manually installing the Security-only Updates and the IE11 Cumulative Updates, you are a Group B user.
-
Gordski
AskWoody PlusApril 29, 2020 at 2:41 pm #2257583Problem solved.
Because I had changed the name of the update slightly the script was not happy with the new name.
I binned the first update file that I renamed and another original and left it as is, put it in the folder with the W7ESUI enabler pressed the button and hey-ho it all works.
(Moral of that saga is don’t mess with stuff unecessarily)
Thank you me.
-
Duncan
AskWoody LoungerApril 30, 2020 at 2:08 pm #2257904As Windows 7 and Windows Server 2008 R2 are on the same software base, is it possible to use this on Server 2008 R2 ? Any suggestions?
-
anonymous
GuestMay 1, 2020 at 1:13 am #2258001Is W7ESUI_0.2.ZIP the revised script for April? Thanks.
-
PKCano
ManagerMay 1, 2020 at 4:37 am #2258064Yes. script and instructions updated for April.
-
Cybertooth
AskWoody PlusMay 1, 2020 at 11:57 am #2258182Quick questions: for Group B, can I use an earlier version of the script + instructions to apply the April updates? Or, conversely, can I use the April version of the script to apply updates for March?
-
PKCano
ManagerMay 1, 2020 at 12:05 pm #2258184The April version works for March and April.
1 user thanked author for this post.
-
anonymous
GuestMay 1, 2020 at 2:36 pm #2258220I just installed the March update by following your instruction “Put SSU KB4550735, all the Security-only updates, and the latest IE11 CU KB4540671 in the folder with the script. The script will install the SSU first and then the rest of the updates.” dated March 22, 2020.
A big THANK YOU.
-
abbodi86
AskWoody_MVP -
woody
Manager -
honx
AskWoody LoungerMay 7, 2020 at 10:08 am #2260523i still haven’t installed any post esu-group b windows 7 and ie patches (february, march, april) and that ssu kb4550734. if i decide to risk it this month, will that new script work through all these patches in the right order (including that ssu)?.
PC: Windows 7 Ultimate, 64bit, Group B
Notebook: Windows 8.1, 64bit, Group B -
PKCano
ManagerMay 7, 2020 at 10:28 am #2260529See here and here and here.
Be sure you have the prerequsites installed (see instructions at the top).
Put the script .cmd file, the latest SSU (April), the latest IE11 CU, and all SOs (Feb-April) in a folder. See #2257497.
Right-click and run the .cmd file as Admin.
Press 0 (zero) to install.
Wait till it finishes and reboot. -
honx
AskWoody LoungerMay 7, 2020 at 10:49 am #2260546thx, according to wmic qfe | find “…” both prerequsites kb4490628 and kb4474419 are both installed.
do we already know if there will be some disadvantages in future if we i go this route inofficially installing post-esu-patches without paying. something like os not “genuine” any more or other shenanigans this kind? i really fear installing these updates!
PC: Windows 7 Ultimate, 64bit, Group B
Notebook: Windows 8.1, 64bit, Group B -
PKCano
Manager -
EP
AskWoody_MVPMay 7, 2020 at 11:19 am #2260555speaking of KB4538483, it got a recent revision this May 2020
expand the “file information” sections for all supported X86 and X64 versions to see updated files from MS support article 4538483:
https://support.microsoft.com/help/4538483/ -
byteme
AskWoody PlusMay 9, 2020 at 12:24 pm #2261021Win7 Home Premium 64-bit. Group B.
I just used abbodi86’s .cmd script to install the April Win7 64-bit security-only updates — having previously used it for February (as described in a previous post) and March.
SHA2 support updates KB4490628 and KB4474419 had already been installed on my PC (in 2019), and I’m helping another Group B-er to install each month’s updates, so I kept things simple and stuck with the original version of the script.
I put four files in an otherwise-empty folder: (1) abbodi86’s .cmd file, (2) the April SSU (KB 4550738), (3) the April Win7 SO update (KB 4550965), and (4) the April IE SO update (KB 4550905).
Then I right-clicked on the .cmd file, chose Run as Administrator, and hit 0 in response to the opening menu.
The script took just under 30 minutes to complete, and I hit 9 at the end (as instructed) to exit.
Then I restarted Windows (also per the script’s instructions), and it was the usual more involved (“Configuring Windows updates…”) post-updates restart, and it took around 10 minutes.
Everything seems normal, and I once again thank abbodi86 for his script.
5 users thanked author for this post.
-
glnz
AskWoody PlusMay 9, 2020 at 8:20 pm #2261097WOW – IT WORKED!
Now I can update the old 7 machine in my wife’s SOHO.
THIS IS GREAT!!!
Will this work again in a month when Woody gives us Defcon 3 for the May updates?
Thanks to abbodi86 and PKCano for translating some of the details!!!
-
This reply was modified 5 years ago by
glnz.
1 user thanked author for this post.
-
This reply was modified 5 years ago by
-
Paul T
AskWoody MVPMay 10, 2020 at 2:18 am #2261131Will this work again in a month
No guarantee MS won’t try to plug this gap, but details will be provided here.
cheers, Paul
-
honx
AskWoody LoungerMay 10, 2020 at 4:57 pm #2261224i just read about another ssu kb4550738 (april). is this covered by the 0.2 script or will it be only subject for future script version (may)?
if latter i think it’s better to wait until defcon 3 or higher for may to install all missing post-esu-updates and corresponding ssu using that script…
and will i still need march ssu as well (both ssu in same folder with that script) or only newer one?
PC: Windows 7 Ultimate, 64bit, Group B
Notebook: Windows 8.1, 64bit, Group B-
This reply was modified 5 years ago by
honx.
-
This reply was modified 5 years ago by
-
PKCano
Manager -
Qnu
AskWoody LoungerMay 12, 2020 at 3:50 am #2261696Will this work again in a month
No guarantee MS won’t try to plug this gap, but details will be provided here.
cheers, Paul
I think the chances are slim to none, how many people use this? A couple hundred? Not really worth the trouble to go out of your way to plug it. Also, the majority of us are using it on HOME PCs, so they are not losing money simply because we can’t even buy it. We “steal” updates we can’t pay for anyway. And Win10 is still for free as far as I know if you have a Win7 key. Correct me if I am wrong.
It’s an issue that costs MS money to fix, but gains them 0 money. Almost all business would not bother with this.
-
This reply was modified 5 years ago by
Qnu.
1 user thanked author for this post.
-
This reply was modified 5 years ago by
-
Mattchu
AskWoody Lounger -
Qnu
AskWoody Lounger -
abbodi86
AskWoody_MVP -
A1ex
AskWoody LoungerMay 13, 2020 at 8:56 am #2262229I installed the May SSU ok, are there some update files I need.
I would appreciate a monthly list of the required kb files for each months updating process, if that’s possible.
A1ex
-
PKCano
ManagerMay 13, 2020 at 9:02 am #2262230See the top post in this thread.
There is also a list on the Win7 Update History site. If you click on the support pages, the SSU is listed there.
-
abbodi86
AskWoody_MVPMay 13, 2020 at 9:06 am #2262231Group A:
get the latest Monthly Rollup from Win7 update history
https://support.microsoft.com/en-us/help/4009469it should also contain reference to latest SSU
Group B:
you need latest SSU, latest IE11 Cumulative, and each month Security Only update
https://www.askwoody.com/forums/topic/2000003-ongoing-list-of-group-b-monthly-updates-for-win7-and-8-1/for .NET updates, you can foloow the blog:
https://devblogs.microsoft.com/dotnet/net-framework-may-2020-security-and-quality-rollup-updates/ -
Mattchu
AskWoody LoungerMay 13, 2020 at 2:12 pm #2262363So as folks may by now know there was an “issue” with the .Net update for May, Abbodi86 has posted a solution but there was another [not sure if posted] which is easy and worked for me.
All credit to vinzf and pesho_georgiev from mdl.
Here’s how to successfully install the infamous .NET May Update:
1. Download this:
http://download.windowsupdate.com/d/msdownload/update/software/secu/2020/05/ndp48-kb4552921-x86_608b67e4011b9e103ca18deadbfc013d1c328508.exe (x86)
http://download.windowsupdate.com/d/msdownload/update/software/secu/2020/05/ndp48-kb4552921-x64_6912af0422fc16a14f4f398fda98117f1e2f01b8.exe (x64)
2. Create a shortcut of the executable.
3. Right click on the shortcut and go to Properties.
4. On the Target box, add this: /msioptions “ESU_LOCK=2D40812E-974C-4EA2-8DCC-63C992D505B9” (make sure to add a space before adding it)
5. Click Apply and OK.
6. Run the shortcut and proceed with the installation.On the “Properties Box” of the right clicked shortcut, make sure you add the /msioptions, etc line from number 4. after the .exe that is already in the box [dont overwrite the lot].
Cheers…
4 users thanked author for this post.
-
Qnu
AskWoody LoungerMay 14, 2020 at 4:28 am #2262530You better go ahead with May SSU KB4555449
Do I need to install the April SSU before installing the May SSU?
-
PKCano
ManagerMay 14, 2020 at 4:45 am #2262532You need the April SSU preinstalled before you can install the May Rollup or SO/IE11 if you don’t install the May SSU at the same time as the May patches.
The May SSU will be necessary for the June patches.
But if you install the May SSU along with the May Rollup or SO/IE11, you do not need to install the April SSU first. -
Qnu
AskWoody LoungerMay 14, 2020 at 5:20 am #2262535Thanks, so basically, May SSU, May Rollup and then run the script and it will install the SSU prior to the Rollup automatically.
-
Qnu
AskWoody LoungerMay 14, 2020 at 3:44 pm #2262704Reporting that I installed May Rollup, May SSU as well as NET. Framework 3.5.1 and 4.7.2 update with aforementioned methods. No issues and everything works smoothly. Thanks for all the help and assistance, as usual.
Out of curiosity: What would happen if you try to install a NET. Framework update version that you don’t have installed on your windows? I used a tool to determine which I had, it showed 3.5 and 4.7.2 so I only installed those two.
-
abbodi86
AskWoody_MVPMay 15, 2020 at 5:53 am #2262824It give you error message about blocked or mismatched situation
-
RDRguy
AskWoody LoungerMay 16, 2020 at 9:32 pm #2263194Referencing @Mattchu’s post above #2262363, a word of warning … if you copy & paste:
/msioptions “ESU_LOCK=2D40812E-974C-4EA2-8DCC-63C992D505B9”
… the ESU .NET update will fail to install & you’ll get the 643 error.
But, if you copy & paste:
/msioptions "ESU_LOCK=2D40812E-974C-4EA2-8DCC-63C992D505B9"… from @abbodi86’s post #2262211, the ESU .NET update should install correctly.
Though both look the same, the difference is the “” marks … “” (fails) vs “” (works)
This is true for both @abbodi86’s command prompt method or @Mattchu’s shortcut method.
EDIT: when this reply is submitted for posting, both “” marks end up looking the same – probably due to @Mattchu’s post being originally submitted using “visual” text while @abbodi86’s post was submitted using plain “text” mode and now because my post contains @Mattchu’s “visual” quote marks, even though I’m submitting this post in plain text mode, after processing, it’s being posted as “visual” text so everyone’s “” marks in my post look exactly the same.
You need to actually look at both @Mattchu’s & @abbodi86’s posts to see the difference in their “” marks. Again, @Mattchu’s fails & @abbodi86’s works.
Moderator note: I’ve fixed the “correct” post so it copies correctly.
Win7 - PRO & Ultimate, x64 & x86
Win8.1 - PRO, x64 & x86
Groups A, B & ABS -
Qnu
AskWoody Lounger -
7ProSP1
AskWoody LoungerMay 17, 2020 at 10:21 am #2263276First of all, a sincere thank you to everyone for your informative contributions to this topic which allow us to continue staying safe while using Windows 7.
This has given me both a revelation and resulted in a few additional .NET related questions:
I have both 4.5.2 and 3.5.1 installed on my system but I ignorantly and erroneously assumed that by keeping 4.5.2 continually updated with 4.5.2 security fixes that 3.5.1 would also be updated. Oops. After checking my Windows Update history I have learned that the last time a security update to 3.5.1 was applied was with KB3163425 on July 12, 2016. (Did I say Oops?) I immediately went ahead and successfully installed 3.5.1 security only update KB4552965.
Here are my questions:
1. I assume .NET security and quality rollup updates are cumulative while .NET security only updates have to be applied successfully to get the full benefit of their intended protection, correct? While I’m OK with 4.5.2, I’m obviously way out of sync with 3.5.1.
2. What is the risk of installing the .NET security and quality rollups? Is there telemetry hidden in these updates like the regular Windows 7 security and quality rollups? I have always been a Group B user and I prefer to remain that way but I’m obviously concerned what risks are posed by not taking the appropriate sooner-than-later steps to plug the holes that are still present in 3.5.1.
Finally, rhetorically, why does Microsoft have to have such disdain towards Windows 7 users?
1 user thanked author for this post.
-
abbodi86
AskWoody_MVP -
PKCano
ManagerMay 17, 2020 at 10:37 am #2263281.NET has never been included in Group B patching. The telemetry Group B is avoiding is in the Windows Security and Quality Monthly Rollup and in the individual telemetry patches like KB2952664.
There is no problem with installing the .NET Rollup. -
PKCano
ManagerMay 17, 2020 at 2:48 pm #2263345I have updated one of my WIn7 Ultimate VMs with the MAY patches on May 17, 2020.
It have .NET 3.5.1 and 4.7 installed.I put KB4556836 (Rollup), KB4555449 (SSU) and KB4552940 (the .msu patch for .NET 3.5.1) in a folder with @abbodi86 ‘s script. Then executed the script as admin.
I executed (as admin) the .exe patch for .NET 4.7 KB4552919 with the Bypass switches as per @abbodi86 in #2262211.Everything installed correctly.
Update: Two more done (same versions of .NET) without problems.5 users thanked author for this post.
-
7ProSP1
AskWoody LoungerMay 17, 2020 at 3:15 pm #2263349I know AKB 2000003 has never included .NET updates when there were some issued but I erroneously assumed they included telemetry of some sort.
It’s a rather unusual feeling when a Windows 7 user realizes that Microsoft is issuing quality updates that actually only include quality updates.
1 user thanked author for this post.
-
alpha128
AskWoody PlusMay 17, 2020 at 8:36 pm #2263386I’m also running .NET 4.7, so the procedure you outlined above is exactly what I plan to do. Glad to learn it works!

-
analogkid
AskWoody PlusMay 18, 2020 at 12:06 pm #2263545Just a question for us 0patch users….
I purchase 0patch pro in March after my one month trial. I have also installed the Win 7 ESU updates through April using the “abbodi86” method and everything seems to be running well.
The AskWoody PLUS Newsletter that arrived this morning in my inbox had and article entitled “.NET Framework oddities and ESU issues highlight May patching”.
In it there is the recommendation to purchase an ESL key but what about those of us who have purchase 0patch pro? Are we still vulnerable?
"An analog kid in a digital world"
Win7 Ultimate home built desktop Running 0patch Pro
Two former 8.1 Laptops & two desktops now running Win 10
Win 10 Dell desktop
-
Paul T
AskWoody MVPMay 19, 2020 at 6:58 am #22638660patch would say “no, you are not vulnerable”, which is the whole point of switching to an alternative update mechanism. If 0patch misses stuff I’m sure we’ll hear about it, but in the meantime, continue to backup regularly.
cheers, Paul
1 user thanked author for this post.
-
anonymous
GuestMay 19, 2020 at 9:39 am #2263931Hello,
I would really love to install the W7 ESUs, but have seen a report that they break Sandboxie.
htxxs://community.sophos.com/products/sandboxie/f/forum/119455/can-t-install-any-version-on-win7-with-windows-7-extended-security-updates-esu
Any help would be very much appreciated.
Many thanks
.
-
EP
AskWoody_MVPMay 19, 2020 at 12:07 pm #2264043contact Sophos about the problem between Sandboxie & Win7 ESU
-
anonymous
Guest -
glnz
AskWoody PlusMay 20, 2020 at 6:19 am #2264316So I have now run the APRIL updates on my wife’s Win 7 Pro 64-bit PC in her SOHO.
BUT … normal Windows Update is now prompting me to install this update from 2014:
System Update Readiness Tool for Windows 7 for x64-based Systems (KB947821) [May 2014]
This tool is being offered because an inconsistency was found in the Windows servicing store which may prevent the successful installation of future updates, service packs, and software. This tool checks your computer for such inconsistencies and tries to resolve issues if found.
More information: https://support.microsoft.com/kb/947821
I do not recall seeing anything like this when I ran the last normal Group A rollup update in January.
ALSO … just now, when I used this tool to install the April updates (KB4550738 and KB4550964), I was NOT prompted to reboot. Is that expected? I rebooted anyway.
Any thoughts about these two? Thanks.
-
PKCano
ManagerMay 20, 2020 at 6:31 am #2264320Hide KB947821, you don’t need it.
ALSO … just now, when I used this tool to install the April updates (KB4550738 and KB4550964), I was NOT prompted to reboot. Is that expected? I rebooted anyway.
The prompt to reboot is not the one you used to see when using regular updates. It is only a line at the bottom of the Command Prompt when it finishes install telling you a reboot is necessary for the changes to take place.
-
glnz
AskWoody PlusMay 20, 2020 at 6:36 am #2264325PKCano – thanks again.
Just to be clear, when this special ESU tool finished installing KB4550738 and KB4550964, I did not get ANY prompt to reboot, including in the cmd window. But since I thought these two included the April Group A rollup, I had expected a prompt somewhere to reboot.
So – was NO prompt to reboot expected for the April Group A rollup? Or did I have the Group B security-only update only (which would be wrong for me)?
-
PKCano
ManagerMay 20, 2020 at 6:41 am #2264326KB4550964 is the Rollup and KB4550738 is the correct SSU for April.
You did good to reboot.
Check Installed Updates to be sure both installed correctly. If so, you should be fine. -
glnz
AskWoody PlusMay 20, 2020 at 6:44 am #2264327PKCano – yes – both are listed in Installed Updates. So I feel fine! Thanks!!!
-
glnz
AskWoody PlusMay 20, 2020 at 6:51 am #2264328New question – when Woody gives us the Defcon3 “go ahead” for the May updates, should we use this special tool also to install
4538483 5/9/2020 SPECIAL ESU UPDATE (from Susan Bradley’s patch list)
Or does abbodi86’s special tool NOT need that?
-
abbodi86
AskWoody_MVP -
Mattchu
AskWoody LoungerMay 20, 2020 at 11:20 am #2264385Cheers RDRguy, never knew the board formatted quotation marks differently in visual or plain, I will remember to do plain next time if there are any “”
It even messes up when you put 2 single quotation marks in sentences, like I`m, etc…
1 user thanked author for this post.
-
glnz
AskWoody PlusMay 20, 2020 at 6:58 pm #2264478Finished using this on our third and final Win 7 Pro 64-bit PC, a slow Dell Optiplex 3010.
Two odd small consequences —
1) In Belarc Advisor, the long list of installed updates to Win 7 is gone.
2) Normal Windows Update is now showing me “Update for Windows 7 for x64-based Systems (KB2952664),” whose MS article is captioned “Compatibility update for keeping Windows up-to-date in Windows 7”, and whose WUD Details say it has been superseded by numerous Monthly Security Quality Updates (rollups), including the 04-20 one I just installed using this tool.
Just a bit of static, I suppose.
-
This reply was modified 5 years ago by
glnz.
-
This reply was modified 5 years ago by
-
PKCano
ManagerMay 20, 2020 at 7:06 pm #2264480KB2952664 functionality has been included in the Win7 Rollup since Sept or Oct of 2018 (I think). That would supersede the any older copy of the stand-alone patch.
-
glnz
AskWoody PlusMay 20, 2020 at 7:49 pm #2264492PKCano – I am guessing that KB2952664 has shown up because something in the special tool or the 04-2020 update deleted the long historic list of past updates, so the PC is not picking up that the superseding Monthly Security Quality Updates were installed.
Is there a way to get the old list restored to wherever it used to be?
-
Qnu
AskWoody LoungerMay 21, 2020 at 3:41 am #2264558Can you link me to the post, I don’t see it.
-
abbodi86
AskWoody_MVPMay 21, 2020 at 6:22 am #2264585W7ESUI don’t clean or remove any update history
KB2952664 show up in WU because of missing metadata for ESU updates
meaning, on metadata level, WU has knowledge only for 2020-01 Monthly Rollup KB4534310, but now 4534310 is superseded by the manually installed 2020-05 Monthly Rollup KB4556836
which lead to WU thinking that KB2952664 is not superseded -
glnz
AskWoody PlusMay 21, 2020 at 6:56 am #2264590abbodi86 – you are correct, and I owe you an apology. I rechecked, and in Belarc Advisor, the long Win 7 update history has returned.
Thanks for your explanation, and thanks with BIG KISSES WITH NO SOCIAL DISTANCE for your update tool.
… And let me add that this thread is a great reason for everyone reading this to donate a little something to Askwoody, as I have. A little something multiplied by each of us would let Woody and PKCano have a much-deserved vacation (as long as they don’t take breaks at the same time).
-
This reply was modified 5 years ago by
glnz.
-
This reply was modified 5 years ago by
-
Larry B
AskWoody LoungerMay 24, 2020 at 10:50 am #2265295Keep getting error 1188 “Element not found”. KB4490628 and KB4474419 are both installed. I tried to install kb4550738-x64 and kb4550964-x64 using the script.
-
PKCano
ManagerMay 24, 2020 at 11:05 am #2265299Create a folder.
Put kb4550738 April SSU, kb4550964 April Rollup in the folder.
Extract W7ESUI.cmd from the zip file, or extract the whole zip file.
Copy or move W7ESUI.cmd and place it in the same folder.
Right-click on W7ESUI.cmd and “Run as administrator”
In the cmd window press 0 (zero) and wait for the script to run.
When it is finished, press 9 to exit.
Reboot the computer. -
Larry B
GuestMay 24, 2020 at 1:59 pm #2265334All of those were in a folder I was running from a USB drive. I will try putting that folder on my HDD, not sure if that will make a difference.
-
Larry B
GuestMay 24, 2020 at 2:42 pm #2265349Putting the same folder from my USB drive on my HDD did the trick. On another PC I installed this from another partition on the same HDD with no issues, but a USB drive with >26GB of free space would not work.
-
Moonbear
AskWoody LoungerJune 1, 2020 at 12:18 pm #2268380Where do I need to put the bypass switch to get 4.7 to install?
Do I need to run the switch in a command prompt?
-
PKCano
ManagerJune 1, 2020 at 12:24 pm #2268381You do it the same way you do “sfc /scannow”
You run “filename /bypass”
One easy way is to make a shortcut to the file, right click on the shortcut, choose properties.
In the “target” box where it shows the file name, add the bypass switch to the end of the string.
Click OK and double click on the shortcut.1 user thanked author for this post.
-
Moonbear
AskWoody LoungerJune 1, 2020 at 12:29 pm #2268384Cheers, PK
You are a life saver!
-
Geo
AskWoody PlusJune 1, 2020 at 12:58 pm #2268391The easier thing to do is pay about $25 for 0patch pro.
-
Mattchu
AskWoody Lounger -
glnz
AskWoody PlusJune 1, 2020 at 5:53 pm #2268480So now that we are Defcon 4 for the May patches, I am running this installer script for KB4555449 and KB4556836 on one of my Win 7 Pro 64-bit machines.
However, Susan B also recommends
>>>> 4556399 5/12/2020 Install .NET Framework security/quality updateWhen I went to download that from MS Update Catalog, the subwindow that popped up showed me at least ten sub-files, and I don’t know which one(s) to pick. The dotnet.exe tool says I have these versions of .NET on my machine: 2.0, 3.0, 3.5 and 4.8.
So, what should I do? Thanks.
-
PKCano
ManagerJune 1, 2020 at 6:12 pm #2268482You need KB4552940 (3.5) and KB4252921 (4.8).
KB 4556399 is a Rollup – it is a bundle of updates for the different versions of .NET.
When you go to the Catalog, instead of clicking on “Download,” click on the Namd of the update. In the popup choose “More Information.”
That will take you to the MS Support page for that Rollup and an explanation of which patch is for which version. -
glnz
AskWoody PlusJune 1, 2020 at 6:23 pm #2268485Thank you, PKCano. I see what you mean.
Now, should I put those two KBs into abbodi86’s Standalone ESU tool on this thread and run it again, or should I go to the other thread about .NET and follow those odd instructions? (And where is that again?)
-
PKCano
Manager -
glnz
AskWoody PlusJune 2, 2020 at 7:22 am #2268673Just FYI that, after running abbodi86’s tool for the May updates in my third Win 7 Pro 64-bit machine (a Dell Optiplex 3010 with 8GB RAM), the May updates show in Installed Updates, but the long list of historic updates in Belarc Advisor is now mostly gone – none of the Win 7 updates show, from 2014 to now. This has continued after a reboot, etc.
The last time, they came back after a while. But not yet this time.
-
This reply was modified 5 years ago by
glnz.
-
This reply was modified 5 years ago by
-
glnz
AskWoody PlusJune 2, 2020 at 10:09 am #2268737Update – checked that machine again, and Belarc Advisor got back its long list of Windows 7 updates.
abbodi86 and PKCano – curious whether you might have a guess as to why this happens.
But I’m super-happy about doing these updates – many thanks again.
-
Silenus
AskWoody LoungerJune 2, 2020 at 10:39 am #2268741Hello to all member of AskWoody.com! This is my first post here, though I’ve been following this site from long ago.
I wanted to thank everyone who made and refine this tool to let us keep using our beloved OS.
I’ve never update my system since ESU came in, so here’s what I did. I put the following files in the same folder as the installer:
- February SO Update – KB4537813
- March SO Update – KB4541500
- April SO Update – KB4550965
- May SO Update – KB4556843
- May IE Update – KB4556798
- .NET 3.5.1 Update – KB4552940
- May SSU – KB4555449
then ran it as administrator. Everything went super smooth, and these updates appear on the installed list in Windows Update.
Then I’ve installed .NET 4.7 Update (KB4552919) as explained here.
Again, everything was good, and my PC seems to run perfectly fine.
I did not install March and April SSU. Do I need them?
Is there any other important update that I miss?
Thanks again!
1 user thanked author for this post.
-
PKCano
Manager -
Cybertooth
AskWoody PlusJune 7, 2020 at 5:07 pm #2270211May I suggest a KB-style article that lists all of the files needed each month to keep a Windows 7 system up to date with @abbodi86’s method? This would include not only Windows and IE11 patches, but also any new .NET patches and whatever else comes down the chute–especially the SSU for the corresponding month and any new versions of the installation script.
Having everything (or at least the links for it) together in one place would save considerable time hunting around for this bit “here” and that bit “over there.” A thread such as this one that’s currently running to 257 replies may not be the most practical method for listing new files, as they inevitably get buried in an avalanche of new comments and questions.
At the very least, it would be helpful to formally and regularly post availability of, and links for, the new SSU in a predictable place. The reason I’m asking is that two days ago, I installed the May patches on a Win7 laptop without problems. But today I used the same folder containing the same files (copied over, of course) on a different Win7 machine, and the installation kept failing. Eventually, I discovered somehow that another new SSU had been released, and put that in the folder for May, and then the installation worked. But then, why did the installation of the same set of patches (minus the May SSU) work just fine on the first laptop?
The greatest benefit IMO would come from posting announcements and links to each month’s new SSU in a fixed location. If this is already taking place, please let me know the page so that I can bookmark it.
Thank you.
-
This reply was modified 4 years, 12 months ago by
Cybertooth.
-
This reply was modified 4 years, 12 months ago by
-
WSandrewcee
AskWoody LoungerJune 9, 2020 at 7:44 pm #2271066Any help here would be appreciated – I have been able to install all updates up to May 2020 on Win7 x86 ( old machine ) However now when I run W7ESUI.cmd ( 0.2 version) it won’t accept the 0 to proceed with install ( but it will accept 9 to exit )….I am running 0patch (free) as well – I have tried disabling it to run the command with the same result…any ideas would be very appreciated ( the keyboard works fine )
Thanks
-
PKCano
ManagerJune 9, 2020 at 7:48 pm #2271071You need to wait on the installation of the June patches until @abbodi86 has a chance to evaluate the situation. DO NOT try to install the June patches yet.UPDATE: It appears that W7ESUI_0.2 still works for June patches.
-
This reply was modified 4 years, 12 months ago by
PKCano.
-
This reply was modified 4 years, 12 months ago by
Kirsty.
2 users thanked author for this post.
-
This reply was modified 4 years, 12 months ago by
-
abbodi86
AskWoody_MVPJune 9, 2020 at 7:57 pm #2271072The script won’t proceed if required options are not met, specially “updates location”
can you post screenshoot of cmd window?
1 user thanked author for this post.
-
EP
AskWoody_MVPJune 9, 2020 at 10:04 pm #2271097Here from MS Update Catalog, Qnu. KB4538483 is only available from the MS Catalog site & WSUS and not available thru Windows Update
manually download the 5-5-2020 version of KB4538483 for your Win7 system, install it and reboot
-
EP
AskWoody_MVPJune 9, 2020 at 10:11 pm #2271100see if this helps, Larry B
-
alpha128
AskWoody PlusJune 9, 2020 at 11:11 pm #2271103“May I suggest a KB-style article that lists all of the files needed each month to keep a Windows 7 system up to date with @abbodi86‘s method? This would include not only Windows and IE11 patches, but also any new .NET patches and whatever else comes down the chute–especially the SSU for the corresponding month… – Cybertooth”
Plus Members like us can use Susan Bradley’s month-end master patch list for this purpose, e.g., 2020-05-29-Pre-Win10-Updates-.pdf
Susan’s file includes links to the Microsoft support pages for all the various patches. That’s what I used to locate and download the appropriate 2020-05 updates from the Microsoft Update catalog.

-
This reply was modified 4 years, 12 months ago by
alpha128.
-
This reply was modified 4 years, 12 months ago by
alpha128.
-
This reply was modified 4 years, 12 months ago by
alpha128.
1 user thanked author for this post.
-
This reply was modified 4 years, 12 months ago by
-
Cybertooth
AskWoody PlusJune 10, 2020 at 2:04 am #2271136Thanks @alpha128, the Master Patch List does give all the MS patches for the month, and that’s good. However, note that using this method involves:
- Visiting the Master Patch List page, from where one then
- Clicks on the link for the PDF list, which contains links that
- Lead one to a MS Support page that still doesn’t provide a download link to the actual patches (example). You need to look around the page to locate the link for the listings to that patch on the MS Update Catalog, then
- Click on that link, and then finally once on the Update Catalog listings
- Click on the download link for the patch.
This is a rather more cumbersome process than, for example, the AKB2000003 page for Group W patchers, which not only lists the patches but also provides direct links to the patches on the MS Update Catalog. Relative to the Master Patch List procedure, this saves three steps (clicking on a PDF, then clicking on a MS Support page, then clicking to reach the Update Catalog list).
And of course, the Master Patch List doesn’t mention updated versions of the W7ESUI script, of which there have now been two versions and doubtlessly will be more in the future. So this still involves looking in a variety of places for all the parts.
Remember, the suggestion is to have a single place listing everything that’s needed to keep Windows 7 patched. Basically, a page that combines the completeness of the Master Patch List with the simplicity of the AKB system–and throws in the W7ESUI to boot.
-
WSandrewcee
AskWoody LoungerJune 10, 2020 at 4:27 am #2271156When I try that ( shift+right click ” copy as path ” to the folder ) it says “specified location is not valid”
-
PKCano
ManagerJune 10, 2020 at 4:40 am #2271161Have any of you looked at the first post in the Patch Tuesday Main Blog thread?
Most of what you need is listed there with download links.That happens every month, thank you very much.
-
Paul T
AskWoody MVPJune 10, 2020 at 4:49 am #2271164All the update files need to be in the same folder as W7ESUI. If not you need to specify the location of the update files.
cheers, Paul
-
Mattchu
AskWoody Lounger -
PKCano
ManagerJune 10, 2020 at 6:42 am #2271179 -
alpha128
AskWoody PlusJune 10, 2020 at 8:10 am #2271196“Remember, the suggestion is to have a single place listing everything that’s needed to keep Windows 7 patched. Basically, a page that combines the completeness of the Master Patch List with the simplicity of the AKB system–and throws in the W7ESUI to boot.” – Cybertooth
The procedure I outlined above isn’t that onerous. A find for the word “catalog” on each support page takes you right to the updates you need.
For April, I just searched the Update Catalog for “2020-04 Windows 7 x64” and was able to easily find the needed patches. But a search for “2020-05 Windows 7 x64” produced a long confusing list, and I discovered that using the Master Patch list for this purpose is much easier.
About the only thing the Master Patch list lacks is info about the W7ESUI script itself, so I just check the opening post of this thread for updates to the script.

-
Mattchu
AskWoody LoungerJune 10, 2020 at 8:14 am #2271197Cheers bud, I did a search but couldn`t see any after May…Got to run the script several times again now, but hey ho…
-
PKCano
ManagerJune 10, 2020 at 8:17 am #2271198https://www.askwoody.com/forums/topic/june-2020-patch-tuesday-rolls-out/#post-2270882
1 user thanked author for this post.
-
PKCano
ManagerJune 10, 2020 at 8:18 am #2271199https://www.askwoody.com/forums/topic/june-2020-patch-tuesday-rolls-out/#post-2270882
1 user thanked author for this post.
-
PKCano
ManagerJune 10, 2020 at 8:19 am #2271200https://www.askwoody.com/forums/topic/june-2020-patch-tuesday-rolls-out/#post-2270882
1 user thanked author for this post.
-
WSandrewcee
AskWoody LoungerJune 10, 2020 at 10:24 am #2271235All the update files need to be in the same folder as W7ESUI. If not you need to specify the location of the update files.
cheers, Paul
They are – there are 2 update files and the installer .cmd in that folder ( and only that )
-
Cybertooth
AskWoody PlusJune 10, 2020 at 10:40 am #2271241Have any of you looked at the first post in the Patch Tuesday Main Blog thread? Most of what you need is listed there with download links.
The answer to the question is, “No.”
Reason is, I wait for Woody to set the MS-DEFCON level above 2. But then, by the time that happens, the blog post announcing the patches, and its associated discussion thread, are long since buried in the silt of newer posts.
And one would still have to find out if there is an updated W7ESUI script.
That’s why it would be preferable to have a single place that puts all of this together. Heck, I’d even be willing to do the work myself, to save others the effort of gathering the parts every month. But again, like an AKB it would have to be a singular, fixed location where users know they can go to each month for the needed information.
The idea is to make it as easy and convenient as possible for the user to get this done.
-
PKCano
ManagerJune 10, 2020 at 10:42 am #2271242Do you have the May SSU KB4555449 installed? It is a prereq for the June patches.
If all are in the same folder, in an elevated Command Prompt, all you have to do is press 0 (zero). You don’t have to change any of the other settings. -
PKCano
ManagerJune 10, 2020 at 10:48 am #2271243The updated script is always HERE.
The patches for the month are released on Patch Tuesday.
If you want a list of the patches, look on the Patch Tuesday for the month you want the patches.
As a matter of fact, you could even download them and save them (in the folder you intend to use for the updates) on Patch Tuesday, then wait for the DEFCON to change. -
SueW
AskWoody PlusJune 10, 2020 at 1:48 pm #2271312@Mattchu, PK included the link in her response to you as it contains the June SSU download links. Just download whichever ‘bittedness’ you need and add it to the folder along with your script.
Win 7 SP1 Home Premium 64-bit; Office 2010; Group B (SaS); Former 'Tech Weenie'-
This reply was modified 4 years, 12 months ago by
SueW.
1 user thanked author for this post.
-
This reply was modified 4 years, 12 months ago by
-
Steve
AskWoody PlusJune 15, 2020 at 12:56 am #2272382Whew.
A big ‘thank you’ to abbodi86 for this installer.
One of the major disruptions of the COVID-19 pandemic was that the “Stay at home” command meant I could not go to a venue to download these Windows® 7 ESU patches. Yes people, the only connection from the abode here to the Internet is a v.92 one.
No way I could download all of these patches (or for that matter, the newest versions of Firefox and TorBrowser) in any semblance of reasonable time.
The pandemic even shut down the Chicago Public Library branch where I could (and have) do this.
I’m keenly considering writing my Aldercritter. Yes, he has a few more crucial items now on his list, but I will allege that broadband internet connectivity is a utility, necessary as much as electricity and home heating. It is pathetic that the choices for broadband connectivity here is limited to corporations earning windfall profits for their abysmal product; laden with impossible to avoid fees, requiring two-year contracts, and dramatically escalating monthly charges with ‘cancellation‘ fees equal to the cost of the service if the contract was not cancelled.
I was without broadband internet access for 90 days. This past week, the Library finally reopened. Thankfully, it was not vandalized. However, due to its closed-air circulation, a patron is limited to one hour inside.
Downloading all these updates via the Library’s wi-fi network (onto a flash drive inserted into my Windows® 8.1 laptop) took 57:36. Yikes.
Bringing it back here and setting it up to execute was simple to follow. I have put prior updates from Microsoft into a specified folder, and that is where abbodi86’s script and the seventeen patches (February [Win7], March, April, May) went. I would have downloaded June’s, but owing to how little time I had left, did not.
The program ran exactly as described. (I also enjoyed the magenta text.)
Here is the picture of the patches installed on this Windows® 7 computer
(I also installed the regular patches on Windows® 8.1; but they are not shown in this picture.) This computer is finally caught up.Mod edit: Pic now removed as external link target has changed.
Important links you can use, without the monetization pitch = https://pqrs-ltd.xyz/bookmark4.html -
Qnu
AskWoody LoungerJune 20, 2020 at 4:39 am #2273738That’s a good idea, I did just that because I usually wait 1 month before installing.
-
Microfix
AskWoody MVPJune 21, 2020 at 1:20 pm #2274038After an image backup, I gave this a try..
RESULT! x86Pro TestNote for @abbodi86; close attention to screenshot above – minor really, Telemetry script didn’t appear on desktop upon douuble restart (no biggie) using the sandscript
May the force AND your god be with you always!
Windows - commercial by definition and now function... -
JimBean
AskWoody LoungerJune 22, 2020 at 1:07 pm #2274291Hi,
W7 HP x64, W7ESUI_0.2.
Installed:
- Jun Service Stack update
- Jun IE cumulative update
- Feb – Jun SO updates
- May .NET 3.5.1 SO update
Everything ran super smooth, took about 25 mins. After reboot, ran the Telemetry script.
No problems to report. Very happy
.
A thousand thanks, @abbodi86.
-JB
1 user thanked author for this post.
-
Moonbear
AskWoody LoungerJune 26, 2020 at 2:30 pm #2275523Is the a way to tell if we need any of the .NET patches every month?
I ask since it seems highly likely that going forward we won’t be able to simply install the ESU script anymore, so if at all possible I’d dearly love the option to just skip them.
-
PKCano
Manager -
Moonbear
AskWoody LoungerJune 26, 2020 at 3:21 pm #2275544That’s exactly what I’m talking about.
How do you tell if the update is recommended or not?
-
PKCano
Manager -
Microfix
AskWoody MVPJune 26, 2020 at 3:27 pm #2275546Have a look at Susan Bradley’s Master Patch list.
For instance: the last security/quality .net was in May kb4556399 and with this KB you can go directly to it in the catalog to download.
Listings of just May updates excel/pdf/html
Listings for that particular month shows what you need.Windows - commercial by definition and now function...1 user thanked author for this post.
-
MrChaz
AskWoody LoungerJuly 2, 2020 at 11:10 am #2277199I’m intrigued now, our trusty Windows 7 Pro 32bit is patched up to the end of january 2020 running with a third party antivirus avira. Would it be advisable to disconnect from the internet and disable the antivirus before attempting this to avoid any security interference?
I would image the system before attempting as a keeper for the future.
illegitimi Non Carborundum -
PKCano
ManagerJuly 2, 2020 at 11:18 am #2277215Disconnecting from the Internet is OK after you download the updates from the Catalog. Be sure you have either 1. all Security-only updates plus the latest IE11 CU (see AKB2000003) or 2. the latest Rollup. You will also need the latest Servicing Stack.
Disabling the AV is probably not necessary if it hasn’t given you any problems with updating in the past. But it certainly wouldn’t hurt to do it.
-
Paul T
AskWoody MVPJuly 3, 2020 at 4:08 am #2277415There is no point disconnecting as you are not turning off your standard protections.
Turning off AV for the duration doesn’t mean your machine will rush off to download a bunch of bad files, unless you tell it to.cheers, Paul
1 user thanked author for this post.
-
glnz
AskWoody PlusJuly 4, 2020 at 3:30 pm #2277715All – Happy and relentlessly safe Fourth!
I imagine we’ll soon see Woody’s DefCon “Go Ahead” for the June updates to Win 7. Susan Bradley has already indicated corporate users can go ahead.
Will aboddi86’s fabulous method work again? Also the .NET method?
Thanks!
1 user thanked author for this post.
-
PKCano
Manager -
alpha128
AskWoody PlusJuly 5, 2020 at 3:48 pm #2277886Susan Bradley’s latest Master Patch list already gave the go-ahead on the June updates. So, on July 2nd, I used the script to install 2020-06 Security Monthly Quality Rollup for Windows 7 for x64-based Systems (KB4561643) and 2020-06 Servicing stack update (KB4562030).
No problems with either the script or the updates it installed.

1 user thanked author for this post.
-
Alex5723
AskWoody PlusJuly 6, 2020 at 2:41 am #2277959Susan Bradley’s latest Master Patch list already gave the go-ahead on the June updates.
Susan Bradley’s OK is aimed at Businesses which have an IT department to thoroughly test monthly patches.
Woody’s DefCon is aimed at small SMBs, home users…and June updates are still at Defcon = 2. -
alpha128
AskWoody PlusJuly 6, 2020 at 10:40 pm #2278098The MS DEFCON rating is one size fits all, while Susan’s Master Patch List is version and patch specific.
You can wait if you want.
But after waiting for almost a month, with Susan’s recommendation, and a three day holiday weekend, I went ahead.

-
glnz
AskWoody PlusJuly 8, 2020 at 1:03 pm #2278602On our spare (test) Win 7 Pro 64-bit machine, I have just now installed KB4562030, KB4561603 and KB4561643.
Thank you again abbodi86 and PKCano!!! And Woody for making this all possible. And Woody’s mom for making Woody possible !!!
Reminder to all to donate!!! I did, and it’s certainly worth it.
-
anonymous
GuestJuly 8, 2020 at 3:02 pm #2278654glnz wrote:
On our spare (test) Win 7 Pro 64-bit machine, I have just now installed KB4562030, KB4561603 and KB4561643.KB4561603 is Jun’20 Cumulative Security Update for IE.
KB4561643 is Jun’20 Cumulative Update/Monthly Rollup for Win7.Unless I’m mistaken, if you installed (or planned to install) KB4561643, then KB4561603 should be redundant and so shouldn’t need to be installed.
Hope this helps.
-
PKCano
ManagerJuly 8, 2020 at 3:03 pm #2278658You are correct. The IE11 CU is included in the Rollup. You only need it if you install the Security-only Updates following Group B.
-
byteme
AskWoody PlusJuly 8, 2020 at 5:55 pm #2278724Win7 Home Premium 64-bit. Group B.
I neglected to report on the May updates, which I successfully installed using abbodi86’s script. That install also included the May .NET update — as a two-part task, with the script updating the older .NET versions and the separate .exe file we were linked to updating the bigger-than-4 .NET version. Or maybe it was the other way round; it’s been a month. In any case, I’m glad there isn’t a recommended .NET update every month.
In fresher news, I have just installed the June SSU, Win7 update and IE update using abbodi86’s script — Version 1! (I’m old fashioned) — and all seems normal. Including the post-installation reboot, the whole process took around 35 minutes.
The one little burp that’s maybe worth mentioning is that, as part of that post-installation reboot, I got a black screen that hung in there for quite a while, and for most (I think) of that time, there was a small message box in the upper left that said, “Setting up personalized settings for Windows Desktop Update.” I don’t recall ever seeing that message before, in any context — but in any case, the black screen yielded to my desktop after two or three minutes. And a while later I did another reboot, and it was completely normal.
And I once again thank abbodi86 for his script.
3 users thanked author for this post.
-
anonymous
GuestJuly 8, 2020 at 7:54 pm #2278765Are there a June updates to NET Framework? Specifically version(s) 3.5 and/or 4.8.
-
PKCano
Manager -
TonyC
AskWoody LoungerJuly 9, 2020 at 7:36 am #2278858While planning to do the June updates for my Windows 7 system, I have just noticed that W7ESUI_0.2 is available. Hitherto, ever since the February updates, I have been using W7ESUI_0.1.
I presume that there is no problem switching to use W7ESUI_0.2 for the June updates instead of using W7ESUI_0.1?
And I apologise if this is a daft question but is there any way of being informed when a new version of W7ESUI.cmd becomes available? Or is it simply a matter of inspecting this topic every month before doing my updates?
-
PKCano
ManagerJuly 9, 2020 at 8:49 am #2278865 -
TonyC
AskWoody LoungerJuly 9, 2020 at 10:27 am #2278889Thank you for the reply.
My Windows 7 system has only .NET 3.5.1 and, last month (for the May updates), W7ESUI_0.1 installed KB4552940 (the Security and Quality Rollup for .NET 3.5.1) without any problem. So I don’t need to worry about the later versions of .NET.
Anyway, for the June updates, I will use W7ESUI_0.2.
-
jburk07
AskWoody PlusJuly 11, 2020 at 12:14 pm #2279387Results for June 2020 Windows 7 patching:
Win7 Home Premium x64:
After the regular image backup, used abbodi86’s script to install the June Rollup KB4561643 and June SSU KB4562030. Took about 10 minutes including the restart and both patches are showing up in Installed Updates.
I’m using primarily Linux Mint these days but I still occasionally need to use Windows 7 online. It’s great to be as up-to-date as possible. Thanks to abbodi86 and PKCano for all your help on this!
Linux Mint Cinnamon 21.1
Group A:
Win 10 Pro x64 v22H2 Ivy Bridge, dual boot with Linux
Win l0 Pro x64 v22H2 Haswell, dual boot with Linux
Win7 Pro x64 SP1 Haswell, 0patch Pro, dual boot with Linux,offline
Win7 Home Premium x64 SP1 Ivy Bridge, 0patch Pro,offline -
MrChaz
AskWoody LoungerJuly 13, 2020 at 2:01 pm #2280070Feedback: Downloaded respective kb’s for my system from the catalog and disconnected from the internet. I then disabled the AV and other security measures and continued to carried out the whole procedure as instructed above by abbodi86. (May) SSU and dotnet security patch, (June) monthly security and quality patch and SSU
Thank you sir, my reliable and trusty windows 7 lives on until hardware or MS decides.
illegitimi Non Carborundum1 user thanked author for this post.
-
Mattchu
AskWoody LoungerJuly 14, 2020 at 1:53 pm #2280450July updates installed successfully with the script. x64 Security [KB4565479 + KB4565539] and Cumulative [KB4565524] and x86 Cumalitive [KB4565524] done so far with no issues.
Latest SSU [KB4565354] installed as well.
Just the .net one to do now.
-
Qnu
AskWoody LoungerJuly 14, 2020 at 3:15 pm #2280471The 3.5.1 should work with the script again, right? Can someone post the “code” again to install the update for the 4.7.2 .net framework?
-
Microfix
AskWoody MVPJuly 14, 2020 at 3:26 pm #2280473 -
PKCano
Manager -
Qnu
AskWoody LoungerJuly 14, 2020 at 5:25 pm #2280508Do you know why there are 2 versions for it in the KB4566517?
windows6.1-kb4019990-x64_35cc310e81ef23439ba0ec1f11d7b71dd34adfe5.msuwindows6.1-kb4565612-v2-x64_0b0093d044fe0b7bd96f45a9653be0375c7b7e97.msuThe bottom one has “v2”.-
This reply was modified 4 years, 10 months ago by
Qnu.
-
This reply was modified 4 years, 10 months ago by
-
abbodi86
AskWoody_MVP -
7ProSP1
AskWoody LoungerJuly 14, 2020 at 6:56 pm #2280538Is anyone having issues installing the Security Only update for .NET Framework v4.5.2?
I have followed the above instructions to the T (just like when the May Security Only .NET update for v4.5.2 was installed) but this time I keep getting a fatal error during installation message stating installation failed with error code: (0x80070643).
If it makes any difference, I successfully installed the Security Only .NET update for v3.5.1 just prior to this.
-
abbodi86
AskWoody_MVP -
7ProSP1
AskWoody LoungerJuly 14, 2020 at 7:33 pm #2280543A-ha. It’s been driving me nuts trying to figure out what the problem might be, so this explains everything.
I am confident, as I type this, there are great minds working on a fix to allow for the continued successful installation of security only .NET updates that relied on the previous ESU_WORKAROUND.
-
7ProSP1
AskWoody LoungerJuly 14, 2020 at 7:55 pm #2280551Oops, I meant ESU_LOCK workaround (not ESU_WORKAROUND) above.
Also, I noticed when downloading the Security Only .NET update for v4.5.2 (KB4565583) that a file named 32114089_6572f8ca4563143988d5e724d4632a35703c0975.cab was also presented. Is it necessary to download this as well and, if so, what does it do?
-
abbodi86
AskWoody_MVPJuly 14, 2020 at 9:35 pm #2280580those cab files are WU metadata, not needed for us, they accidentally included them in MU catalog download
—
there is no alternative for ESU_LOCK workaround, except using BypassESU v7
not to be discussed here1 user thanked author for this post.
-
Moonbear
AskWoody LoungerJuly 14, 2020 at 9:56 pm #2280583Can you give any possible insight into why MS is targeting the ..NET updates as the ones to mess with?
-
Qnu
AskWoody LoungerJuly 15, 2020 at 5:39 am #2280655Just to be sure: The 3.5.1 update should still work with your script since it didn’t rely on the workaround before, right?
-
PKCano
Manager -
Qnu
AskWoody LoungerJuly 15, 2020 at 11:55 am #2280742I have 3.5.1 and 4.7.2, so having one update is better than none I guess. But seems like I have to switch to Win10 soon, if I can’t get the 4.7.2 update to work.
-
PKCano
Manager -
7ProSP1
AskWoody LoungerJuly 15, 2020 at 2:21 pm #2280813Yes indeed, that is my experience exactly as the v3.5.1 .NET Security Only (.msu file) installed successfully while the later version of .NET (.exe file, v4.5.2 Security Only in my case) would not install.
Interestingly, I had neither the June nor July SSU installed and the v3.5.1 .NET Security Only update installed just fine using the May SSU.
YMMV, I suppose.
-
This reply was modified 4 years, 10 months ago by
7ProSP1.
-
This reply was modified 4 years, 10 months ago by
-
abbodi86
AskWoody_MVPJuly 15, 2020 at 6:18 pm #2280885It’s not targeting particularly
they put same effort to validate ESU licenses in both Windows and .NET 4 updatesbut the design of Windows updates and WinSxS component store, allowed us to find a way to suppress the validation check
that’s cannot be done with .NET 4 updatesthere are two ways to bypass the validation for .NET 4
1- use external BypassESU hook
2- create administrative installation including the updatesthe first one allow to install .NET 4 updates directly
while the second way require uninstalling .NET 4 Framework, then reinstall the created updated pack -
Moonbear
AskWoody LoungerJuly 15, 2020 at 8:51 pm #2280911Option 2 sounds like it’d be way above my pay-grade.
The thought of uninstalling anything as deep in the system as a .NET package makes me very nervous.
I thought the ESU bypass for the .NET updates wasn’t working anymore?
-
abbodi86
AskWoody_MVP -
Moonbear
AskWoody LoungerJuly 16, 2020 at 1:26 pm #2281139Is there any chance of a new workaround like the one for the May updates?
-
abbodi86
AskWoody_MVP -
Moonbear
AskWoody LoungerJuly 16, 2020 at 8:55 pm #2281224If I were to begin using 0patch PRO, will I still need to install the monthly updates?
-
Alex5723
AskWoody Plus -
Microfix
AskWoody MVPJuly 18, 2020 at 10:11 am #2281507Using the external BypassESU hook works for x86 with all pre-requesits
however, on x64 with all pre-requesits, it fails
screenshot of x86 post unhook:
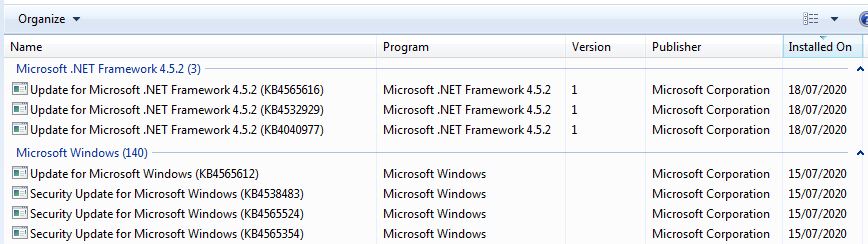
EDIT 21st July: Winx64 .NET update succesful on 2 devices over the w/end, happy days!
Windows - commercial by definition and now function...-
This reply was modified 4 years, 10 months ago by
Microfix.
-
This reply was modified 4 years, 10 months ago by
Microfix.
1 user thanked author for this post.
-
This reply was modified 4 years, 10 months ago by
-
Guest
AskWoody LoungerJuly 18, 2020 at 1:10 pm #2281524Thank you for this script.
Well written also as I had Malwarebytes block it as ransomware (had to exclude it) when it was nearly complete (during the cleanup stage) so I had to run it again. It was much faster the second go around as it recognized what was previously installed so basically just double checked everything and then picked up where it left off.
I did notice for me, that the neutralize telemetry run once file didn’t catch everything so did some additional cleanup based on the other thread here and the other wintel file also.
One question, I noticed in Event Viewer a couple of listings for the following. These are as expected for some of the patches (I hadn’t updated since February)?
Reservation for namespace identified by URL prefix http://+:80/Temporary_Listen_Addresses/ was successfully added.
Reservation for namespace identified by URL prefix http://*:2869/ was successfully added. -
abbodi86
AskWoody_MVPJuly 18, 2020 at 1:39 pm #2281527It seems normal events
https://kb.eventtracker.com/evtpass/evtpages/EventId_15007_Microsoft-Windows-HttpEvent_61955.asp1 user thanked author for this post.
-
PKCano
ManagerJuly 20, 2020 at 8:26 am #2281894Successfully installed the Rollup, the SSU, .NET 3.5 on both 32-bit and 64-bit Win7 Pro SP1 using W7ESUI_0.2.
Successfully installed .NET 4.7 (KB4565623 v4.6-4.7.2) onboth32-bitand 64-bitWin7 Pro SP1 using dotNetFx4_ESU_Installer.I created two folders in the root of the C: drive, one for the OS and .NET 3.5 updates, one for the .NET 4.7.2 updates, along with the .cmd that was applicable.
I installed the Rollup, SSU, and .NET 3.5 first, then without rebooting, installed .NET 4.7.2.
After the install completed, I rebooted and verified the successful install.
Removed the install folders from the C: drive.Correction: I was mistaken. On a second inspection, I realize the 64-bit KB4565623 for .NET 4.6-4.7.2 did NOT install.
-
KP
AskWoody PlusJuly 20, 2020 at 11:00 am #2281924I did not know about dotNetFx4_ESU_Installer. Here is a link to it:
https://host-a.net/f/247682-dotnetfx4esuinstallerzip . You can also find it via a Google search.
1 user thanked author for this post.
-
abbodi86
AskWoody_MVPJuly 20, 2020 at 4:08 pm #2282005dotNetFx4_ESU_Installer is just automated script for the ESU_LOCK workaround, which no longer works for July updates
-
7ProSP1
AskWoody LoungerJuly 20, 2020 at 6:57 pm #2282080As mentioned previously, this has been my experience exactly.
How were you able to get your .NET 4.7.2 update to install using the dotNetFx4_ESU_Installer on 64 bit Windows 7 as you described above, @PKCano?
As I understand it, there’s no issue installing the July .NET 4.x updates on 32 bit versions of Windows 7, only the 64 bit variety, correct?
-
Microfix
AskWoody MVPJuly 21, 2020 at 10:34 am #2282233ok, I managed to get the x64 .NET 4.5.2 in for July on two devices.
How I done it was:
Restarted the device and do absolutely nothing other than:
go to services, stop BITS, Cryptographic Services and WU whilst offline.
then use the dotNetFx4_ESU_Installer and do everything in the readme file as admin
even install the .exe as admin.
Worked a treat hereWindows - commercial by definition and now function... -
7ProSP1
AskWoody LoungerJuly 21, 2020 at 1:14 pm #2282263Using Windows 7 x64, I followed your steps exactly as you listed them and after the dotNetFx4_ESU_Installer finished doing its thing, it said “done”; however, upon going to Windows Update → View update history → Installed Updates, the .NET update for 4.x is, in fact, NOT listed.
Thinking I did something wrong, I rebooted and re-did the steps with the same result but this time I noticed the word “rollback” flashed very quickly in the bottom left corner of the Microsoft .NET framework installer screen.
An error screen is not shown using the dotNetFx4_ESU_Installer script (as when you try to install the .NET 4.x updates manually using the filename.exe /msioptions “ESU_LOCK=2D40812E-974C-4EA2-8DCC-63C992D505B9” command), so anyone would conclude the installation was successful; unfortunately, this is not the case and, as @abbodi86 stated above, “dotNetFx4_ESU_Installer… no longer works for July updates.”
Microsoft is supposedly working on a fix to allow for the successful installation of the July .NET 4.x updates on Windows 7 x64 systems as they are failing on all of them at the moment. Maybe @abbodi86 will beat them to the punch.
-
Microfix
AskWoody MVPJuly 21, 2020 at 1:24 pm #2282269Looks like you checked the wrong thing as WU isn’t reliable for checking updates installed.
check control panel> Programs Features> Installed updates instead.
The ESU_Lock no longer works for July, it’s stated further up this thread but the dotNetFx4_ESU_Installer does work! see #2282005Windows - commercial by definition and now function... -
7ProSP1
AskWoody LoungerJuly 21, 2020 at 1:52 pm #2282283In my above post, I went into Control Panel → Windows Update → View update history → Installed Updates (which brings me to the same screen as Control Panel → Programs Features → Installed updates) and Under Microsoft .NET Framework, and after following all your helpful steps and advice, the July update is still NOT listed.
I don’t understand where I’m going wrong or what I’m doing wrong. If you don’t mind, could you please check your Installed Updates and/or provide a screenshot of your successful July .NET update install?
-
Microfix
AskWoody MVPJuly 21, 2020 at 2:03 pm #2282286 -
7ProSP1
AskWoody LoungerJuly 21, 2020 at 2:16 pm #2282290I notice in your screenshot that you installed the Security and Quality Rollups for all your installed .NET updates, while I have only installed and am trying to install the Security Only .NET update for July (KB4565583).
I wonder if this difference is what may be causing my issue?
It would be helpful if someone else here could try to duplicate the same result.
-
This reply was modified 4 years, 10 months ago by
7ProSP1.
-
This reply was modified 4 years, 10 months ago by
-
Moonbear
AskWoody Lounger -
7ProSP1
AskWoody LoungerJuly 21, 2020 at 2:31 pm #2282294I did what you said @Moonbear and the last .NET update I have installed is the Security Update for Microsoft .NET Framework 4.5.2 (KB4552952) on 05/14/2020.
The July Security Update for Microsoft .NET Framework 4.5.2 (KB4565583) did not/will not install for me using the dotNetFx4_ESU_Installer.
-
Microfix
AskWoody MVP -
7ProSP1
AskWoody LoungerJuly 21, 2020 at 2:48 pm #2282302OK, I have checked this three ways now:
Control Panel → Windows Update → View update history → Installed Updates
Control Panel → Programs Features → Installed Updates
Control Panel → Windows Update → Installed Updates (in the bottom left corner)
The results, after following @Microfix ‘s steps, all tell me the exact same thing:
The last .NET update I have installed is the Security Update for Microsoft .NET Framework 4.5.2 (KB4552952) on 05/14/2020.
-
anonymous
Guest -
Microfix
AskWoody MVPJuly 24, 2020 at 4:47 am #2282814On July 23, 2020, update KB4565583 v2 was released to replace v1 for .NET Framework 4.5.2 for Windows 7 SP1 and Windows Server 2008 R2 SP1 and Windows Server 2008 SP2. The v1 update did not install for customers who had certain ESU configurations. The v2 update corrects the issue for customers who could not install the v1 update.
Source: https://support.microsoft.com/en-us/help/4565583/kb4565583
Remember, v1 needed some workarounds v2 may not??
so you’re on your own here at MS-Defcon2Windows - commercial by definition and now function...1 user thanked author for this post.
-
PKCano
Manager -
Microfix
AskWoody MVPJuly 24, 2020 at 5:57 am #2282820Yes, that was only an example of what the MS support document states across all versions so that everyone could quickly view it.
Windows - commercial by definition and now function... -
7ProSP1
AskWoody LoungerJuly 24, 2020 at 10:30 am #2282849Despite MS re-issuing all July .NET 4.x patches and following all steps and instructions here:
Installation Did Not Succeed.
Software update KB4565583 has not been installed because:
Fatal error during installation.
MSI returned 0x643
Entering Function: MspInstallerT >::RollbackI would appreciate it if anyone else could report their results.
I don’t know how you managed to get your July .NET update to install successfully, @Microfix, but I’m sure glad you were able to.
-
abbodi86
AskWoody_MVP -
7ProSP1
AskWoody Lounger -
anonymous
GuestJuly 25, 2020 at 2:04 pm #2283089Link for the revised dotNetFx4_ESU_Installer please.
-
anonymous
GuestJuly 25, 2020 at 4:23 pm #2283107A browser search will find it.
-
Qnu
AskWoody LoungerJuly 26, 2020 at 4:14 pm #2283265A browser search will find it.
Typed in “revised dotNetFx4_ESU_Installer”
found 3 links with nothing of help.
-
PKCano
Manager -
alpha128
AskWoody PlusJuly 26, 2020 at 11:40 pm #2283323I found it.
The ReadMe.txt says, “Extract the zip file contents to a folder with simple path.” What constitutes a simple path? Is something like “2020-07-DotNet4” simple enough?

-
anonymous
GuestJuly 27, 2020 at 12:33 am #2283325alpha128 wrote:
What constitutes a simple path?Maybe something like this?
c:\temp\Or maybe this?
c:\dnfx4\Hope this helps.
-
anonymous
GuestJuly 27, 2020 at 12:47 am #2283331A simple path would be any folder 1 or 2 levels deep in the drive’s root directory like c:\DotNet4 or maybe even c:\ESU\DotNet4 but c:\2020-07-DotNet4 would work just fine.
A not so simple path might be a folder several levels deep and include spaces in the folders or sub-folders name(s) like c:\folder name 1\sub-folder name 1\sub-sub-folder name 2\etc-1\etc_2\etc~3
In reality though, a complex folder path will still work just fine only it’ll require a lot more typing setting the administrators command prompt path to the location of the folder containing the extracted “.bat” command file in order to execute it.
-
A1ex
AskWoody LoungerJuly 27, 2020 at 4:46 am #2283366I found it ok and downloaded the zip file, but it’s password protected!
A1ex
-
alpha128
AskWoody PlusJuly 27, 2020 at 7:12 am #2283381“A simple path would be any folder 1 or 2 levels deep in the drive’s root directory like c:\DotNet4 or maybe even c:\ESU\DotNet4 but c:\2020-07-DotNet4 would work just fine.”
Actually, the full path of the folder I created is “C:\W7ESUI\2020-07-DotNet4”. So I’ll leave it that way. Thanks!

-
Paul T
AskWoody MVP -
Microfix
AskWoody MVPJuly 27, 2020 at 7:31 am #2283387Without verifying checksums that were issued with the original?
If there is no zip password, it’s not the original file.Windows - commercial by definition and now function... -
PKCano
Manager -
alpha128
AskWoody PlusJuly 27, 2020 at 8:07 am #2283404 -
alpha128
AskWoody PlusJuly 27, 2020 at 8:23 am #2283408Here is the checksum information for the version I downloaded. Do I have the correct version? Please let me know! Thank you.
Name: dotNetFx4_ESU_Installer_r.zip Size: 8126 bytes (7 KiB) CRC32: 4A837AD0 CRC64: 7BECD50A61C1CC9A SHA256: 3E1F48478404CC3FC372D4B8D00CC5E5B532BEE64AB9D78F5ECF2DDDA49E1227 SHA1: 574937759D3DFACE77AA91082D80808EF093D65F BLAKE2sp: 732BB16B10CF115C13362624FBB42A1D6C1BACFD5B70E98B309AE867B48120F2

-
This reply was modified 4 years, 10 months ago by
alpha128.
1 user thanked author for this post.
-
This reply was modified 4 years, 10 months ago by
-
Microfix
AskWoody MVPJuly 27, 2020 at 8:35 am #2283411ORIGINAL zip file contains a password with an SHA-256 checksum as follows:
3e1f48478404cc3fc372d4b8d00cc5e5b532bee64ab9d78f5ecf2ddda49e1227Windows - commercial by definition and now function...-
This reply was modified 4 years, 10 months ago by
Microfix. Reason: wrong checksum
1 user thanked author for this post.
-
This reply was modified 4 years, 10 months ago by
-
Chriski
AskWoody PlusJuly 27, 2020 at 10:01 am #2283421I’m certainly confused.
I found: https://host-a.net/u/abbodi86
and:
which certainly seems legitimate (has abbodi86 ref), and yields the SHA256 checksum displayed in #2283411, but extracts just fine with NO password.
Is there another REAL file somewhere else?
(BTW the CMD in this file runs and installs the 7/23 .Net updates for Net 4.6 for x32 and Net 4.7 for x64; does it do something else I should worry about?)
Thanks.
-
PKCano
Manager -
Chriski
AskWoody PlusJuly 27, 2020 at 10:25 am #2283425Perhaps…
The same named file in the other abbodi86 repository from the initial post in this thread is an exact binary compare, and it too extracts with no password.
Why are people being cryptic about locations etc.? Are we giving up secrets we shouldn’t? I mean if we’re participating in this thread, and doing the operations mentioned, then we’ve already given consideration to all the implications, and we’re “in”. In for a penny, in for a pound, no?
Chris
-
Chriski
AskWoody PlusJuly 27, 2020 at 1:33 pm #2283482More confused …
Verifying newly downloaded files and those that I used the past couple days … (all the same by the way)
It comes to mind that the hash for a PW protected zipped fileset would be different than for the same fileset without a password. Wouldn’t it? (The password would need to be stored inside the zip file I would think.)
My head is starting to hurt.
[old proverb: “one fool can ask more questions than 20 wise men can answer”]
-
Chriski
AskWoody PlusJuly 27, 2020 at 1:45 pm #2283487Just curious if the checksum info you posted was for a PW protected zip file or did it just extract without a password? Did you find a .zip with a PW? (The ones I found match yours and have the same SHA256 checksum, no password.)
1 user thanked author for this post.
-
Microfix
AskWoody MVPJuly 27, 2020 at 2:23 pm #2283492Correction, my error, (copied from wrong folder on my PC)
The original password locked dotNetFx4_ESU_Bypass.7z
size 3455bytes (3kb)
SHA256:
0EA25AE5023145BE8C1D8B1836F4AF5A2C36E7D93538429B05EF1ECFF1C5F3F1
sincere apologies for the confusion.
It is impossible to change any file without affecting checksums.Windows - commercial by definition and now function... -
Chriski
AskWoody PlusJuly 27, 2020 at 3:33 pm #2283508Thank you very much for this!
The .ZIP file is NOT password protected; in the one repository there is also a .7z file that IS password protected.
Not having the password, I cannot check the actual file contents to see if they are the same …
But since they are (as near as I can tell) abbodi86’s repositories, and I’ve been happily using the main ESU script from his repository for months, I’m confident all is good.
Chris
-
geekdom
AskWoody_MVPJuly 27, 2020 at 3:41 pm #2283510I don’t have a pony in this race, but could a summary and clarification be provided on what to download, where, and if a password is necessary.
On permanent hiatus {with backup and coffee}
offline▸ Win10Pro 2004.19041.572 x64 i3-3220 RAM8GB HDD Firefox83.0b3 WindowsDefender
offline▸ Acer TravelMate P215-52 RAM8GB Win11Pro 22H2.22621.1265 x64 i5-10210U SSD Firefox106.0 MicrosoftDefender
online▸ Win11Pro 22H2.22621.1992 x64 i5-9400 RAM16GB HDD Firefox116.0b3 MicrosoftDefender -
RDRguy
AskWoody LoungerJuly 27, 2020 at 4:40 pm #2283523All, I think everyone’s talking apples & oranges here. @abbodi86 has 4 different dotNetFx4 scripts posted and some are password protected and some are not.
The 2 “installer” scripts (dotNetFx4_ESU_Installer) don’t seem to be password protected and the 2 “bypass” scripts (dotNetFx4_ESU_Bypass) are.
2 scripts (1 bypass & 1 installer) are pre-Jul and the 2 other (1 bypass & 1 installer) were revised in Jul after the Jul .Net updates were released as noted by the “_r” at end of file name (before the “.” file extension).
As I’m not @abbodi86, I can only surmise that both the latest “installer” and the latest “bypass” scripts will install the Jul .Net (ver 4.5 & up) updates in non-ESU systems – one will do it via ESU “bypass” method requiring 1st installing the ESU bypass, then installing the .Net update then removing the ESU bypass while the “installer” method essentially does all this (or something very similar) automatically.
Hope this helps.
Edit: typos
Win7 - PRO & Ultimate, x64 & x86
Win8.1 - PRO, x64 & x86
Groups A, B & ABS-
This reply was modified 4 years, 10 months ago by
RDRguy.
-
This reply was modified 4 years, 10 months ago by
-
abbodi86
AskWoody_MVP -
Paul T
AskWoody MVP -
abbodi86
AskWoody_MVPJuly 28, 2020 at 9:05 am #2283729The bypass is mainly ment for installing .NET 4 updates through WU, manual installation works too
but it has compatibility issue and cause other MSI programs to fail (including KIS 2020 or Office C2R)the first installer was merely a simple script for installing .NET 4 updates manually using the ESU_LOCK workaround
the revived version include temporary self-bypass to work with July updatesdotNetFx4_ESU_Installer_r.zip is the safest approach so far
-
Paul T
AskWoody MVPJuly 28, 2020 at 10:57 am #2283760The correct file to use is available at this link,
but it is a password protected 7z file.
https://host-a.net/f/252519-dotnetfx4esubypassr7z
https://host-a.net/f/252903-dotnetfx4esuinstallerrzipcheers, Paul
-
PKCano
ManagerJuly 28, 2020 at 11:03 am #2283765dotNetFx4_ESU_Installer_r.zip is the safest approach so far
This one is not password protected.
-
Microfix
AskWoody MVPJuly 28, 2020 at 12:27 pm #2283790I’m sticking with the dotNetFx4_ESU_Bypass.7z (password protected)
Why? ’cause I don’t, nor am I likely to use MS Office and my method works with no SFC errors. Done the trials and errors, earlier this month and sticking to it until MS issue busted patches again. YMMVWindows - commercial by definition and now function... -
alpha128
AskWoody PlusJuly 28, 2020 at 6:39 pm #2283888The bypass is mainly ment for installing .NET 4 updates through WU, manual installation works too
but it has compatibility issue and cause other MSI programs to fail (including KIS 2020 or Office C2R)the first installer was merely a simple script for installing .NET 4 updates manually using the ESU_LOCK workaround
the revived version include temporary self-bypass to work with July updatesdotNetFx4_ESU_Installer_r.zip is the safest approach so far
I do use Office Click to Run so I will be trying out this one when the time comes.

-
Microfix
AskWoody MVPJuly 30, 2020 at 1:15 pm #2284321Heads up folks:
https://www.catalog.update.microsoft.com/Search.aspx?q=2020-07
2020-07 Extended Security Updates (ESU) Licensing Preparation Packages for Windows 7/server 2008R2
click [last updated] released 7/29/2020Windows - commercial by definition and now function...1 user thanked author for this post.
-
abbodi86
AskWoody_MVP -
EP
AskWoody_MVPJuly 31, 2020 at 11:06 am #2284571The KB4538483 ESU Licensing Preparation Package has been recently superseded by a new ESU Preparation package – KB4575903
https://support.microsoft.com/help/4575903/
https://www.catalog.update.microsoft.com/Search.aspx?q=kb4575903
-
Moonbear
AskWoody LoungerJuly 31, 2020 at 11:52 am #2284585How do you find the checksums for the non password protected dotNetFx4_ESU_Installer_r.zip?
-
PKCano
ManagerJuly 31, 2020 at 11:58 am #2284588right click on the file/zip. There should be a menu choice the shows the checksum. It’s 256, I think.
-
Moonbear
AskWoody LoungerJuly 31, 2020 at 12:02 pm #2284591I don’t see an option to see the checksum when I right click on the zip.
-
abbodi86
AskWoody_MVP -
PKCano
ManagerJuly 31, 2020 at 12:21 pm #2284596OK, the reason I had the menu selection is because I have 7zip installed. It puts the selection in the context menu.
See the information on 7zip here, as well as the command line you can use.Or hashmyfiles from Nirsofe.
1 user thanked author for this post.
-
Geo
AskWoody PlusJuly 31, 2020 at 12:31 pm #2284597Easier to just pay $25 dollars and get 0patch pro.
1 user thanked author for this post.
-
Moonbear
AskWoody LoungerJuly 31, 2020 at 2:28 pm #2284626After some careful consideration, I’ve decided that I’ll just install 7-zip. Is this the right site? https://www.7-zip.org/
-
PKCano
Manager -
Moonbear
AskWoody Lounger -
PKCano
ManagerJuly 31, 2020 at 2:52 pm #2284634Try downloading from MajorGeeks
-
Moonbear
AskWoody LoungerJuly 31, 2020 at 2:56 pm #2284635Ok will do, sorry for taking up so much of your time with this.
-
Moonbear
AskWoody LoungerJuly 31, 2020 at 3:21 pm #2284646Still showing as an unverified publisher even though Majorgeeks. I’m assuming that isn’t normal?
-
PKCano
Manager -
Moonbear
AskWoody LoungerJuly 31, 2020 at 5:12 pm #2284681Are there multiple .NET 4.7 files that I’ll need to download when I install july’s patches or am I just reading the update catalog wrong?
-
PKCano
ManagerJuly 31, 2020 at 6:16 pm #2284691For .NET 4.7 you need KB4565623 (Rollup) OR KB4565586 (security-only) – not both
-
Moonbear
AskWoody Lounger -
Moonbear
AskWoody LoungerJuly 31, 2020 at 10:25 pm #2284713When I went to download the exe for KB4565623 I got the new mixed content warning in Google Chrome saying this file couldn’t be securely downloaded.
Has anyone else seen this when trying to download the exe for KB4565623 on Chrome?
It let me choose to keep downloading the file but why did that mixed content warning only kick off with the exe file?
-
This reply was modified 4 years, 10 months ago by
Moonbear.
-
This reply was modified 4 years, 10 months ago by
-
abbodi86
AskWoody_MVPAugust 1, 2020 at 12:00 am #2284721download.windowsupdate.com links are http
that does not mean the files (or links) are not safe
-
alpha128
AskWoody Plus -
alpha128
AskWoody Plus -
Moonbear
AskWoody LoungerAugust 1, 2020 at 5:06 am #2285305Ok, I did see that the download links were in http.
But why would that not give the same warning with the .msu files as with the .exe?
-
abbodi86
AskWoody_MVPAugust 1, 2020 at 8:40 am #2285314Probably because viruses are usually exe files
-
Moonbear
AskWoody LoungerAugust 1, 2020 at 9:23 am #2285316Ok, let me see if I’m understanding everything.
The warning triggered on the exe because the download link was for an executable with an http link on a https site.
The warning won’t trigger on the msu files because they don’t register as an executable.
Even with the warning the download should be safe since it was the insecure link and not what was being downloaded that triggered the warning.
Did I miss anything?
-
This reply was modified 4 years, 10 months ago by
Moonbear.
1 user thanked author for this post.
-
This reply was modified 4 years, 10 months ago by
-
PKCano
Manager -
anonymous
GuestAugust 1, 2020 at 1:05 pm #2285360What do I do with the Run_Once_W10_Telemitry_Tasks.cmd left on my WIN 7 SP1 desktop.
-
anonymous
GuestAugust 1, 2020 at 1:46 pm #2285365I had the same problem when I trying to download ndp47-kb4565623-v2-x64 with Chrome. So I downloaded it with Firefox instead!
-
alpha128
AskWoody PlusAugust 1, 2020 at 1:58 pm #2285378I believe you right-click on it and run as administrator. IIRC, the script runs once and then deletes itself.
I had already disabled telemetry on my system before I ran W7ESUI.cmd for the first time, so the second script was never created for me.

-
Chriski
AskWoody PlusAugust 1, 2020 at 2:05 pm #2285383Also, opening a command window and using:
certutil -hashfile <file_of_interest> SHA256
will give the hash for the file of interest, for the algorithm, in this case SHA256.
It will do: MD2 MD4 MD5 SHA1 SHA256 SHA384 SHA512
Win 7 and later I believe. Supposedly case sensitive; is on my win 7 version.
-
glnz
AskWoody PlusAugust 1, 2020 at 3:21 pm #2285410Hey, everyone – now that Woody has gone to DefCon 3, I want to install the July updates on our three (3) Win 7 Pro 64-bit machines, one of which is the production PC in my wife’s SOHO. (I start with the other two to see whether they survive.)
There has been a LOT of traffic here the last three weeks, and I haven’t followed.
First – is the # W7ESUI # script at the very top of this thread still good for Windows updates (and I’m in Group A)? (Not .NET.)
If not, where is the shortlist of new steps?Second – we have .NET 4.8. What exactly should I do to install any updates? I’ve seen emails of the posts here about password and not password and don’t know where to start.
Thanks.
-
This reply was modified 4 years, 10 months ago by
glnz.
-
This reply was modified 4 years, 10 months ago by
-
PKCano
ManagerAugust 1, 2020 at 3:43 pm #2285413Use this script. https://host-a.net/f/252903-dotnetfx4esuinstallerrzip for the .NET 4.
You need KB4565636-v2 issued 7/23 for .NET 4.8W7EUSI_0.2.zip for the rest KB4565524 Rollup, KB4565354 SSU, and KB4565612 .NET 3.5
1 user thanked author for this post.
-
byteme
AskWoody PlusAugust 1, 2020 at 4:00 pm #2285418Win7 Home Premium 64-bit. Group B.
I have just installed all (I think) of the appropriate (I hope) July Windows updates.
I prepared two folders, the first with the W7ESUI.cmd script (I’m still using the first version of that) and the Win7 64-bit versions of four files: kb4565354 (the July SSU); kb4565539 (Win7 security-only); kb4565479 (IE security-only); and kb4565579-v2, that last file being the corrected (v2) version of the .NET update that the W7ESUI script can effectively use for .NET versions lower than 4.
As always, I right-clicked on the .cmd file and chose “Run as administrator,” and the whole process took a little over half an hour (including the post-installation restart).
The second folder was set up to install the updates for installed NET versions starting with 4 (4.8 in my case). It had the revised (i.e., July 23) version of the dotNetFx4_ESU_Installer.cmd file (linked here), and the corrected version (v2) of the July security-only update that was appropriate for NET 4.8 (an .exe file, the name of which started with “ndp48-kb4565589-v2-x64_”); and it also had a folder named “bin” with four other files that were included in the same .zip as the installer.cmd file: two ending in .manifest, and two ending in .dll.
(I went into that detail partly because my initial unpack of the .zip file had the four files that should have been in the bin folder in the parent folder instead, probably due to a bad unzip choice on my part — which I discovered when the script started to run and immediately pointed out that it couldn’t find one of those files in the bin folder, and aborted.)
I right-clicked on the .cmd file and chose “Run as administrator,” and the installation took very little time. There was no indication that a restart was required, but I restarted anyway.
Everything seems normal at this point, and I checked the Installed Updates list in Windows Update, and it shows all five updates as successfully installed.
Thanks again to abbodi86.
1 user thanked author for this post.
-
glnz
AskWoody PlusAugust 1, 2020 at 5:31 pm #2285437PKCano – I first ran W7EUSI_0.2.zip for KB4565524 Rollup, KB4565354 SSU and KB4565612 .NET 3.5.
However, for KB4565524-x64 (the last of the three),
after the last “The operation completed successfully.” and “Removing temporary extracted files…” and
just before “Finished” ,
I getC:\W7ESUItemp_2012\WINDOW~2.1-K\WO1E08~1.240\racpldlg.dll.mui – The process cannot access the file because it is being used by another process.
What should I do? Have not rebooted yet. Thanks.
EDIT – I went to that folder C:\W7ESUItemp_2012\WINDOW~2.1-K\WO1E08~1.240\
and the ONLY file in that folder is racpldlg.dll.mui.Maybe for some reason the W7EUSI could not delete that file after the updates were finished? Ignore for now, reboot, and go delete it after?
-
PKCano
ManagerAugust 1, 2020 at 5:47 pm #2285444If you followed all the instructions in the Readme file, try that. Check in Installed Updates to be sure the updates installed.
-
glnz
AskWoody PlusAugust 1, 2020 at 6:38 pm #2285451All seems OK on first of three machines. Thanks again.
-
glnz
AskWoody PlusAugust 3, 2020 at 6:43 am #2285762And now all seems OK on the other two machines, including wife’s SOHO production machine!
abbodi86 and PKCano – you guys are GREAT!
And – another noodge – those benefiting from these install techniques – please donate to AskWoody. Even small amounts because there are many of us.
-
PKCano
ManagerAugust 11, 2020 at 3:02 pm #2287984dotNetFx4_ESU_Installer_r.zip is the safest approach so far
This is the one you need for August .NET4 and later installations.
-
Mcinwwl
AskWoody LoungerAugust 16, 2020 at 2:55 pm #2289037Little question about installing .NET patches with dotNetFx4_ESU_Installer_r.zip. I installed KB4565636-v2 for .NET 4.8.
I am trying to install ndp45-kb4565616-v2 and ndp47-kb4565623-v2. These do not install, the script do not see them as patches to work on. From posts above I understand that those are not mandatory… but this in nowhere explicitly written?
Should these got installed or are they somehow bundled into KB4565636-v2 and I should worry not? Or do I misunderstand something badly?
-
anonymous
GuestAugust 16, 2020 at 3:19 pm #2289040You only need the patches for the version(s) or .NET that is installed on your machine.
You do not need all of the .NET4 patches unless you have all of the versions installed.
Do you know what versions are installed on your computer?
If the version is not there, the patch won’t install. -
abbodi86
AskWoody_MVPAugust 16, 2020 at 10:37 pm #2289106.NET 4.x versions are upgrades to each other
4.8 is the latest and you only need its patch
-
glnz
AskWoody PlusAugust 20, 2020 at 9:17 am #2290033It’s August 20, and in maybe two weeks Woody will give DefCon 3 for the August updates. I have Win 7 Pro 64-bit, with .NET 4.8, and I am Group A.
Are the two methods here still good for getting and installing the August updates?
(I mean (a) the method at top of this page — W7ESUI — for Updates and
(b) dotNetFx4_ESU_Installer_r.zip for any .NET 4.8 update.)Cheers!
-
PKCano
Manager -
anonymous
GuestAugust 20, 2020 at 3:19 pm #2290078Are there .NET framework updates for Win7 for August? If so where will I find them. Can you give me KB numbers for .NET framework 3.51 and for .NET framework 4.6, please?
-
PKCano
ManagerAugust 20, 2020 at 3:40 pm #2290087The .NET Rollup KB4570506 contains the bundle of updates for all versions of .NET. When you click on the “Download” button, you will see all of them. Only download the ones you need. The KB number is in the name of the file download.
KB4569767 .NET 3.5.1
KB4569780 .NET 4.5.2
KB4569775 .NET 4.6 – 4.7.2
KB4569754 .NET 4.8 -
anonymous
GuestAugust 20, 2020 at 4:08 pm #2290096Thank you very much.
I have no problem finding SSU information or the Monthly rollup information, but for some reason I can never find information on the .NET stuff.
-
abbodi86
AskWoody_MVPAugust 21, 2020 at 12:37 am #2290149dotNetFx4_ESU_Installer_r ReadMe.txt gives a hint, the .NET blog gives much details
https://devblogs.microsoft.com/dotnet/e.g. August security updates
https://devblogs.microsoft.com/dotnet/net-framework-august-2020-security-and-quality-rollup-updates/ -
glnz
AskWoody PlusSeptember 1, 2020 at 6:54 pm #2293183PKCano – I’m Group A.
So – am I correct that if I want to do the August Win 7 64-bit updates, I should do:
August Rollup KB4571729 Download 64-bit .
(I must have <b>July Servicing Stack KB4565354 previously installed</b> to receive these updates.)
And also install new August Servicing Stack KB4570673.The above would be using the method at top of this page — W7ESUI — for Updates.
Are there any .NET August updates for .NET 4.8?
Thanks.
-
This reply was modified 4 years, 9 months ago by
glnz.
-
This reply was modified 4 years, 9 months ago by
-
PKCano
ManagerSeptember 1, 2020 at 7:37 pm #2293188You are correct about the Rollup and the SSU.
For .NET, you will need:
KB4569767 for .NET 3.5.1 – it needs to go with the Rollup and SSU in the method at top of this page.KB4569754 for .NET 4.8 – it needs to use this https://host-a.net/f/252903-dotnetfx4esuinstallerrzip
The .NET patches are found in the Rollup KB4570506.
1 user thanked author for this post.
-
glnz
AskWoody PlusSeptember 2, 2020 at 1:30 pm #2293353My Win 7 Pro 64-bit is updated through the August updates, thanks to this excellent thread.
However, the Microsoft 365 on that machine (formerly Office 365) now says that it will not do more non-security updates because Win 7 is now end of life.
So our updates via abbodi86’s technique are not enough to overcome that little snarl.
Question # 1 – are you seeing the same thing?
Question # 2 – if you have a genuine ESU license and Microsoft 365, are you getting the same warning about no more non-security updates to MS365? Or is your ESU license good for all updates to MS365?
-
This reply was modified 4 years, 9 months ago by
glnz.
-
This reply was modified 4 years, 9 months ago by
-
PKCano
ManagerSeptember 2, 2020 at 1:51 pm #2293364The non-security updates are just “improvements” that you may (of may not) want.
The SECURITY updates are what’s important. Are you still getting those? -
glnz
AskWoody PlusSeptember 2, 2020 at 2:00 pm #2293368PKCano – I’m not sure on all the details because that pop-up message was (of course) on my Win 7 machine, but my Win 7 machine is actually part of a dual-booting machine and I’m spending all my time these days on its Win 10 side. (I update its Win 7 side to see what happens as a guinea pig and then I later update my wife’s SOHO production Win 7 machine.)
I should have marked down the message, but my recollection is that it said I would get only security updates on MS365 going onward because Win 7 is obsolete. (My MS365 is Home 64-bit.)
So let’s see if the crowd here has answers to my two Qs directly above.
-
This reply was modified 4 years, 9 months ago by
glnz.
-
This reply was modified 4 years, 9 months ago by
-
abbodi86
AskWoody_MVPSeptember 2, 2020 at 11:38 pm #2293449Everybody will see the same thing, Microsoft/Office 365 support is limited on Windows 7, regardless if you have ESU license or not
https://docs.microsoft.com/DeployOffice/windows-7-support -
PKCano
ManagerSeptember 4, 2020 at 12:35 pm #2293802Before you ask about August .NET:
Download only the update for the version(s) installed on your PC..NET Rollup KB4570506
.NET 3.5.1 KB4569767
.NET 4.5.2 KB4569780
.NET 4.6 – 4.7.2 KB4569775
.NET 4.8 KB4569754.NET SO KB4570500
.NET 3.5.1 KB4569736
.NET 4.5.2 KB4569743
.NET 4.6 – 4.7.2 KB4569740
.NET 4.8 KB4569733 -
anonymous
GuestSeptember 4, 2020 at 5:07 pm #2293869Ladies and gentlemen, please take note:
PKCano, not content with merely operating “in the zone”, has broken through the temporal bonds constraining mere mortals and is now answering questions before they are asked…PKCano, I am in awe of your productivity – thank you so much for the almost ridiculous amount of regular assistance you provide to virtually all of us!
-
glnz
AskWoody PlusSeptember 4, 2020 at 10:39 pm #2293912MS web page “Windows 7 end of support and Office” says:
Support for Windows 7 ended on January 14, 2020. Even though Windows 7 is no longer supported, we’ve decided to continue to provide you with security updates for Microsoft 365 for the next 3 years, until January 2023. We’re doing this to give you additional time to make the transition from running Microsoft 365 on devices running Windows 7 to a supported operating system, such as Windows 10. But, during that time, as long as the device is still running Windows 7, Microsoft 365 won’t receive any new features updates.
So even with the special updates here to Win 7, M365 is now getting only security updates.
-
zat_so
AskWoody Plus -
woody
Manager -
byteme
AskWoody PlusSeptember 5, 2020 at 11:44 pm #2294132It’s the Great Karnac! John Karnac. He created Doom, right? (Who says my memory is fading?)
Win7 Home Premium, 64-bit. Group B.
I installed all (I think) of the appropriate August Windows updates a few hours ago, and everything seems normal.
August was identical to July — four .msu files installed with the W7ESUI.cmd script, and one .exe file installed with the revised (i.e., July 23) version of the dotNetFx4_ESU_Installer.cmd file — so I won’t repeat the steps I described in my July-updates post (https://www.askwoody.com/forums/topic/standalone-installer-script-for-windows-7-esu-regardless-the-license/#post-2285418).
In case it’s useful to anyone, here are the KB numbers of my August set:
The four .msu’s installed with W7ESUI.cmd:
4570673 (August SSU)
4571687 (Win7 security-only)
4571719 (IE security-only)
4569767 (.NET 3.5.1 security and quality rollup)The .exe installed with dotNetFx4_ESU_Installer.cmd:
4569754 (.NET 4.8 security and quality rollup)
Thanks again to abbodi86.
-
TonyC
AskWoody LoungerSeptember 7, 2020 at 9:37 am #2294490Can you still print from your Win7 system after installing the security only update (K4571719)? There is a report in the post #2292943 that, after installing either the security only update or the rollup (KB4571729), printing no longer works.
(By the way, unless I am confused, I believe you got the Win7 and IE11 updates the wrong way round.)
1 user thanked author for this post.
-
byteme
AskWoody PlusSeptember 7, 2020 at 1:24 pm #2294580I just printed a page from Word 2010 (32-bit), so it looks like I can still print (at least to some extent). And when I “view devices and printers” in Control Panel, my printer shows (unlike what was reported in that post you linked to).
You’re correct that my list has the KB nos. for Win7 and IE the wrong way ’round. 4571719 is the Win7 update, and 4571687 is the IE update.
-
anonymous
GuestSeptember 7, 2020 at 2:12 pm #2294594On Sept, 4 I installed all of the below August Windows updates on two Win 7, SP 1 Home Premium systems.
Three .msu’s installed with W7ESUI.cmd:
4570673 (August SSU)
4571729 (Win 7 Monthly Rollup)
4569767 (.NET 3.5.1 security and quality rollup)The .exe installed with dotNetFx4_ESU_Installer.cmd:
4569754 (.NET 4.8 security and quality rollup)Everything has been running fine with no printing problems.
Thanks to abbodi86 and PKCano for all their invaluable assistance.
-
glnz
AskWoody Plus -
Cyrus Khambatta
AskWoody LoungerSeptember 8, 2020 at 12:51 am #2294733I’m a contributor too, and this site and this post are invaluable for guys still running Windows 7. Many thanks, abbodi86 and PKCano .
-
TonyC
AskWoody LoungerSeptember 8, 2020 at 9:52 am #2294844Thank you for confirming that you can still print.
However, I was a little worried about your use of the phrase “at least to some extent”. Does it signify anything potentially significant? Or are you simply emphasizing that being able to print one page does not really constitute an extensive test?
-
TonyC
AskWoody LoungerSeptember 8, 2020 at 9:57 am #2294849But you didn’t install the August 2020 cumulative security update for IE11, KB4571687? Yes/no?
-
PKCano
Manager -
TonyC
AskWoody LoungerSeptember 8, 2020 at 10:36 am #2294864I apologise. I actually knew that information. But, as a member of Group B, I am so used to installing the IE11 CU each month that I forgot for a moment that members of Group A don’t need to do it.
-
byteme
AskWoody PlusSeptember 8, 2020 at 11:23 am #2294878“To some extent” was just my way of emphasizing that I hadn’t done any testing beyond printing that one page from Word.
-
PKCano
ManagerSeptember 8, 2020 at 2:23 pm #2294972Information about September .NET:
Download only the update for the version(s) installed on your PC..NET Rollup KB4576628
.NET 3.5.1 KB4569767 (2020-08 update, do not need to reinstall)
.NET 4.5.2 KB4569780 (2020-08 update, do not need to reinstall)
.NET 4.6 – 4.7.2 KB4576612
.NET 4.8 KB4576487.NET SO 4.8 KB4576490
-
PKCano
ManagerSeptember 10, 2020 at 5:03 am #2295343Last night, 9/9/2020, I updated one of my Win7 machines to Sept patches.
OSFolder:
W7ESUI_0.2 script
KB4577051 Rollup
KB4566371 DST for Yukon.Canada
(no new SSU for Sept)
(.NET 3.5.1 KB4569767 – 2020-08 update, not necessary, installed in Aug).NETFolder:
dotnetFx4_Installer_r
KB4576612 .NET 4.6 – 4.7.2 (the only .NET4 I have installed)All installed successfully
-
abbodi86
AskWoody_MVP -
PKCano
ManagerSeptember 10, 2020 at 10:19 am #2295390Ahhhh! I remember now. I just forgot about that.
Something about losing it in your old age………Thanks.
-
TonyC
AskWoody LoungerSeptember 12, 2020 at 9:48 am #2295764I apologise if this question has been answered before, but I couldn’t find it.
If I ever need to uninstall an update that had been installed by W7ESUI, how do I do it? Can I simply uninstall it from Programs and Features > Installed Updates?
-
anonymous
GuestSeptember 12, 2020 at 3:15 pm #2295800I would go to Windows Update > Installed Updates (in the lower left corner).
Or click Start ball > enter installed updates in the search bar > click on View installed updates.
-
abbodi86
AskWoody_MVPSeptember 12, 2020 at 7:08 pm #2295849You cannot not uninstall an ESU update in this case, unless there is a higher/later ESU update is installed
if you are using Monthly Rollups, then Disk Cleanup > Update Cleanup should be able to remove the old ones
2 users thanked author for this post.
-
Microfix
AskWoody MVP -
TonyC
AskWoody LoungerSeptember 13, 2020 at 10:45 am #2296008Thank you for the reply. However, I’m sorry but the double negative in the first sentence has confused me completely. Perhaps we can consider the following scenario?
Each month, I use W7ESUI to install the following:
- The Win7 security only update (SOU) (Group B, so I don’t use the rollup)
- The IE11 cumulative update (CU)
- The security and quality rollup for .NET Framework 3.5.1 (if there is one)
- The latest SSU (if there is one)
Suppose, after installation, I discover that the Win7 SOU or the IE11 CU is causing a problem in my system. Can I simply uninstall either of these in the usual way from Installed Updates?
-
TonyC
AskWoody LoungerSeptember 13, 2020 at 10:49 am #2296009Surely, it doesn’t matter which way you get to Installed Updates. Or am I missing some subtlety here?
-
PKCano
ManagerSeptember 13, 2020 at 11:11 am #2296012Installed Updates is the same no matter which way you get to it.
Do it whichever way you want. -
anonymous
GuestSeptember 13, 2020 at 1:19 pm #2296024The is the home of the Bypass project. You’ll find everything you need to know and lots of stuff you don’t need or want to know. There are also people there who answer questions.
You have to register for the forum before you can access it.
1 user thanked author for this post.
-
abbodi86
AskWoody_MVPSeptember 13, 2020 at 5:23 pm #2296079You cannot
the reason is that when you uninstall current ESU update, the ESU component found in previous ESU update becomes active, and therefore Windows perform ESU validation during the uninstall process, which will fail if you don’t have real ESU license
4 users thanked author for this post.
-
glnz
AskWoody PlusSeptember 13, 2020 at 6:14 pm #2296088Maestro (abbodi86) – Just curious. If we need to uninstall a recent update, could we succeed by uninstalling ALL of the ESU updates that we did with your W7ESUI patcher (back to February), and then reinstall most of those updates up to (but not including) the update we don’t want?
I suppose that would require being able to uninstall many updates AT ONCE. Is that possible?
-
abbodi86
AskWoody_MVPSeptember 13, 2020 at 6:45 pm #2296089If you use Monthly Rollups, you can install 2020-01 Rollup KB4534310 (using dism with cab)
then you can uninstall the latest Monthly Rollup installed with W7ESUIfor Security Only group, it’s harder task
consider installing BypassESU-v9-AIO instead
-
TonyC
AskWoody LoungerSeptember 14, 2020 at 2:15 am #2296154Not good news! Have you considered stating this limitation prominently in the introduction at the beginning of this topic?
Suppose you create a restore point before running W7ESUI. Is it possible subsequently to uninstall all the updates just installed by restoring the system to that restore point? Or do you encounter the same problem?
And what about restoring the system from a system image created just before running W7ESUI? Will that effectively uninstall all the updates just installed?
-
abbodi86
AskWoody_MVPSeptember 14, 2020 at 5:12 pm #2296361I did not cross my mind, or encountered such situation
restore point approach might work, but i never used restore points at all
-
Cyrus Khambatta
AskWoody LoungerSeptember 17, 2020 at 12:30 am #2296932The post in mydigitallife is by abbodi86, too. My question is, if you’ve been using the batch file in askwoody, could we switch to the one in mydigitallife ? Or are they the same ?
-
Paul T
AskWoody MVPSeptember 17, 2020 at 2:27 am #2296950I expect they are the same, but you need to login to access MDL…
And we know the one here works because many have reported success using it.cheers, Paul
1 user thanked author for this post.
-
abbodi86
AskWoody_MVPSeptember 17, 2020 at 10:33 pm #2297210W7ESUI is the same here and there
2 users thanked author for this post.
-
glnz
AskWoody PlusSeptember 28, 2020 at 4:14 pm #2299639Per Susan Bradley (but not yet Woody), it’s time to install the September patches for Win 7 (and I copy only the cumulative ones below).
Is it still OK to use the two abbodi86 methods we’ve been using here since February?
>>>> 4577051 9/8/2020 Install Monthly rollup
>>>> 4577010 9/8/2020 Install Internet Explorer cumulative security
>>>> 4576628 9/8/2020 Install .NET security/quality rollupBut I just realized that Susan doesn’t list a Servicing Stack Update. So still hold off ??
-
PKCano
Manager -
alpha128
AskWoody PlusSeptember 28, 2020 at 11:07 pm #2299748I just took a look in the Microsoft Update Catalog for 2020-09 Servicing Stack and I don’t see one listed for Windows 7.

-
PKCano
ManagerSeptember 29, 2020 at 4:26 am #2299782If it’s not listed, there was no new one.
The post is correct for what you need. -
anonymous
GuestSeptember 29, 2020 at 5:28 pm #22999714576628 9/4/2020 (I don’t see a 0/8/2020) Install .NET security/quality rollup says it applies to both 3.5.1 and 4.8. So which script should be used? Or does it need to be run once in each script?
-
PKCano
Manager -
anonymous
GuestSeptember 30, 2020 at 4:15 pm #2300208How did you “break it open” so you could see this list which you display in #2294972?
.NET 3.5.1 KB4569767
.NET 4.5.2 KB4569780
.NET 4.6 – 4.7.2 KB4576612
.NET 4.8 KB4576487Many thanks for doing it for us (and all the other things you help us with), but I would like to learn.
-
PKCano
ManagerSeptember 30, 2020 at 4:18 pm #2300214When you click on the “Download” button in the Catalog, you will see all the patches that are in the bundle (Rollup). The one(s) you need to download will have the individual KB number in the file name.
-
Silenus
AskWoody LoungerOctober 3, 2020 at 9:49 am #2300702In this link you can find the single patches for every OS:
.NET Framework September 2020 Security and Quality Rollup Updates
-
byteme
AskWoody PlusOctober 3, 2020 at 11:28 pm #2300861Win7 Home Premium, 64-bit. Group B.
I installed all (I think) of the appropriate September Windows updates a few hours ago, and everything seems normal.
September was similar to August and July, except that there appears to be no September SSU for Win7, and the .NET update listed for version 3.5.1 is the same as August (so already installed). So I installed two .msu files (instead of four) with the W7ESUI.cmd script, and I installed one .exe file with the revised (i.e., July 23) version of the dotNetFx4_ESU_Installer.cmd file.
For anyone seeking further guidance, I included more detail on the steps involved in my July-updates post (https://www.askwoody.com/forums/topic/standalone-installer-script-for-windows-7-esu-regardless-the-license/#post-2285418).
And just in case it’s useful to anyone, here are the KB numbers of my September set:
(1) The two .msu’s installed with W7ESUI.cmd:
4577053 (Win7 security-only)
4577010 (IE security-only)(2) The .exe installed with dotNetFx4_ESU_Installer.cmd:
4576487 (.NET 4.8 security and quality rollup)
I also installed the last four Office 2010 updates ever.
*sighs*
*sniffles*Thanks to abbodi86 and PKCano for helping keep me in Win7-land for another month.
-
This reply was modified 4 years, 8 months ago by
byteme.
3 users thanked author for this post.
-
This reply was modified 4 years, 8 months ago by
-
TonyC
AskWoody LoungerOctober 4, 2020 at 5:40 am #2300899The KB article for the September 2020 Win7 SO update (KB4577053), in the “Before installing this update section”, states:
“After installing the items above, Microsoft strongly recommends that you install the latest SSU (KB4565354).”
Strangely, KB4565354 is the July 2020 SSU, which I installed with the July 2020 updates. Is the above statement a mistake? Perhaps the author of the article copied and pasted from a previous KB article and was not thorough enough in reviewing this section for changes?
-
PKCano
ManagerOctober 4, 2020 at 6:09 am #2300903You are good with that SSU you have installed. There was no now SSU this time (surprise!).
-
Moonbear
AskWoody LoungerOctober 4, 2020 at 8:46 am #2300918Will the script install the Windows msrt?
I added it to the folder along with the september S&Q rollup, but only the rollup was installed.
-
PKCano
Manager -
Moonbear
AskWoody LoungerOctober 4, 2020 at 9:10 am #2300925Can you still get it even without the ESU license?
-
PKCano
Manager -
Moonbear
AskWoody Lounger -
TonyC
AskWoody LoungerOctober 4, 2020 at 9:58 am #2300933Win7 x64 Group B
I have been using W7ESUI to install updates on my Win7 system. However, I did not install any of the August 2020 updates because of the potential problem of not being able to print from my system after installing the SO update, KB4571719.
I am now planning to install the September 2020 updates. The problem is that the prerequisite August 2020 SSU is not already installed on my system. I would have installed it with the August 2020 updates.
According to the documentation, the August 2020 SSU should be installed and the system restarted before installing the September 2020 updates. Does that mean that I should first use W7ESUI to install only the August 2020 SSU, then restart my system, and then use W7ESUI a second time to install the September 2020 updates?
Or is W7ESUI clever enough to be able to install the August 2020 SSU and the September 2020 updates all in a single run?
-
abbodi86
AskWoody_MVPOctober 4, 2020 at 10:08 am #2300936Last Office 2010 updates ever will be in this October
3 users thanked author for this post.
-
abbodi86
AskWoody_MVPOctober 4, 2020 at 10:12 am #2300937May SSU KB4555449 is the last explicit prerequisite
it’s enough to install May, June, July, August or September updatesand yes, W7ESUI will always install any SSU first
it also check ESU updates themselves to assure that the minimum required servicing stack version is installed -
TonyC
AskWoody LoungerOctober 4, 2020 at 10:18 am #2300943Having used W7ESUI successfully to install Win7 SO updates, IE11 CUs, .NET 3.5.1 rollups and the latest SSUs since February 2020, would you be able to summarise please what would now be involved in switching to use BypassESU-v9-AIO instead? And what is the significance of the smiley?
Was it really a serious suggestion to consider switching to BypassESU-v9-AIO? Would it be a simple process or a complex, time consuming process? If the latter, I think that I would rather spend what little time I have on getting Win10 running on a new PC with all the function that I require. I don’t anticipate needing my Win7 system for very much longer.
-
Moonbear
AskWoody Lounger -
PKCano
Manager -
Moonbear
AskWoody LoungerOctober 4, 2020 at 12:40 pm #2300986Ok, that’s how it shows up on mine as well.
All these years updating my pc and I never noticed before today that the msrt never showed under Installed Updates all this time.
I always look at Installed Updates instead of Update History, I’ll start checking both now that I know how this works
Thanks for the help @PKCano
-
abbodi86
AskWoody_MVPOctober 4, 2020 at 5:34 pm #2301060Extract the 7z file,run LiveOS-Setup.cmd and choose option [2]
yes it’s serious suggestion
but it’s not allowed to post (or probably discuss) BypassESU here, as it invlove “external” helperyou can read the _ReadMe.txt for full details about the project
-
Moonbear
AskWoody LoungerOctober 4, 2020 at 9:13 pm #2301088I’m taking notes so I’ll be ready for next month now that I know I can still install the Windows MSRT and I have one last thing to iron out.
Will everything work if I download and install the MSRT (if one is available) directly after installing patches with the ESU and .NET scripts or will I need to reboot first and then run Windows Update?
-
PKCano
Manager -
Moonbear
AskWoody Lounger -
byteme
AskWoody PlusOctober 6, 2020 at 1:51 pm #2302099CORRECTION: I thought September was the last month for Office 2010 updates, but October is the last month, so there may be security updates next Tuesday (10/13).
ADDENDUM TO CORRECTION: I see abbodi86 beat me to it.
-
This reply was modified 4 years, 8 months ago by
byteme.
-
This reply was modified 4 years, 8 months ago by
-
TonyC
AskWoody LoungerOctober 7, 2020 at 8:17 am #2302266May SSU KB4555449 is the last explicit prerequisite it’s enough to install May, June, July, August or September updates
That is not what the KB article for KB4577053 (2020-09 SO update for Win7) states. It states that you must install the 11 August 2020 SSU (KB4570673) or later, and restart your PC, before installing KB4577053. I would normally have installed KB4570673 with the August updates last month but, as I have explained elsewhere, I eventually decided not to install the August updates.
Suppose that I place the following in a folder:
- KB4577053 (2020-09 SO update for Win7)
- KB4577010 (2020-09 CU for IE11)
- KB4569767 (2020-08/09 rollup for .NET 3.5.1)
- KB4570673 (2020-08 SSU)
and then run W7ESUI. If the KB article is correct, will this work? Will KB4570673 get installed first, and the system restarted, before the remainder of the updates are installed?
If I wanted to be absolutely sure, I suppose that I could first install KB4570673 by itself using W7ESI, then restart my system, and then use W7ESUI for a second time in order to install the remaining three updates.
1 user thanked author for this post.
-
PKCano
ManagerOctober 7, 2020 at 8:42 am #2302268W7ESUI will install the SSU first.
That should be OK. -
abbodi86
AskWoody_MVPOctober 7, 2020 at 6:30 pm #2302408KB articles are not always 100% accurate
you can test yourselfnevertheless, installing latest SSU is generally recommended
and SSUs do not need system restart (unless there were other pending operation before)1 user thanked author for this post.
-
GoneToPlaid
AskWoody LoungerOctober 8, 2020 at 9:38 pm #2302692KB articles are not always 100% accurate
you can test yourselfnevertheless, installing latest SSU is generally recommended
and SSUs do not need system restart (unless there were other pending operation before)Actually, the older SSU might have worked fine during testing on most computers. Recall that MS has encountered timing issues SSUs on some computers. I figure that if MS says that one should first install the latest SSU, then they must have found an issue related to some computers.
1 user thanked author for this post.
-
PKCano
ManagerOctober 13, 2020 at 5:31 pm #2304011Here’s your .NET fix for October. Hold on to your hat if you are doing Security-only, because you have two (2) Rollups.
Download only the update for the version(s) installed on your PC..NET Quality Rollup KB4579977
.NET 3.5.1 KB4578952
.NET 4.5.2 KB4578955
.NET 4.6 – 4.7.2 KB4578963
.NET 4.8 KB4578977NOTE: KB4566466 .NET Security-only was originally released 7/14/2020. The Support page says:
On October 13th, 2020 we are republishing this update to resolve a known issue that affected the original release. You should install this version (V3) of the update as part of your normal security routine.
.NET SO KB4566466 v3
.NET 3.5.1 KB4565579
.NET 4.5.2 KB4565583
.NET 4.6 – 4.7.2 KB4565586
.NET 4.8 KB4565589This is the October 2020 .NET SO which should also be installed if you are doing Security-only .NET.
.NET SO KB4580467
.NET 3.5.1 KB4578980
.NET 4.5.2 KB4578983
.NET 4.6 – 4.7.2 KB4578987
.NET 4.8 KB457899010 users thanked author for this post.
-
byteme
AskWoody PlusOctober 13, 2020 at 11:56 pm #2304111Probably a dumb question, but has that ever stopped me before?
For no particularly good reason, I installed version 2 of the July SO update for NET 4.8 — rather than the Security & Quality Rollup, which I usually install for the NET updates (even though I’m Group B as far as the Win7 updates are concerned). But I’ve since installed the Security and Quality Rollups (rather than the SO update) for NET 4.8 for August and September. Assuming I also install the Security and Quality Rollup for NET 4.8 for October (rather than the SO update), am I correct to assume there’s no need for me to separately install version 3 of the July SO update?
1 user thanked author for this post.
-
PKCano
Manager -
PKCano
Manager -
anonymous
Guest -
anonymous
GuestOctober 14, 2020 at 10:05 am #2304199Thanks for clarifying. I came in the middle of the thread.
-
Ailios
AskWoody LoungerOctober 14, 2020 at 12:46 pm #2304259We have a few apps crashing on some Win 7 Pro computers unfortunate to have .NET KB457997 rollup installed on 10/13/20. Apps include Google Chrome and Outlook 2016 (365). The latter with fault module ucrtbase.DLL errors. I’m going through and removing it and continue to block on the rest. Good thing I only install on a few to test before going company wide.
1 user thanked author for this post.
-
Microfix
AskWoody MVP -
Microfix
AskWoody MVPOctober 14, 2020 at 1:12 pm #2304273If you are installing the Rollups, you should be OK. The problem seems to be only with the .NET SOs.
we HOPE, see #2304259
A reminder for SMQR (group A) patchers:
kb4578623 Fiji Standard Time is NOT r equired as it’s within the monthly rollup.Windows - commercial by definition and now function... -
GoneToPlaid
AskWoody LoungerOctober 14, 2020 at 1:31 pm #2304280Interesting. KB4578977 is not causing any issues on my Win7 computers in either Chrome or Outlook 365.
-
Ailios
AskWoody LoungerOctober 14, 2020 at 5:10 pm #2304333Yes. Sorry about the typo. When I go to uninstall it, what was actually installed for .NET is KB4578977. That’s the one I’m uninstalling. The app crashing most is Outlook 2016. After the uninstall the computers seem to run slow after the reboot. I’m trying to stay hopeful it’s just that they needed time to settle after the reboot.
At end of August I discovered ESU covering many of these computers wasn’t actually working. I cleared that up and ran the critical and important updates available in September. My mistake was not setting their computers back to ‘wait and see’ mode. I’m paying for it now.
I’m so ready to be done with these Windows 7 computers.
-
Mele20
AskWoody LoungerOctober 14, 2020 at 9:30 pm #2304374You need to fix the link in Woody’s main post about .NET updates where he links to PKCano thread that has NOTHING to do with Windows 10 but the last two or three comments in this thread were not yet posted when I read it THINKING IT WAS ABOUT WINDOWS 10 .NET UPDATES, went to Microsoft catalog and got one .NET update for Windows 10, installed it and had to reboot. I did that and somehow ended up in this threadwhen I clicked on my tab to here that loaded along with all last session tabs in Basiilisk!
I wrote a comment about .NET updating and Windows 10 and only when I went to post did I finally see that somehow PKCano’s link ends up in this thread NOT a thread about Windows 10 and .NET update today from Microsoft.
1 user thanked author for this post.
-
woody
Manager -
Mele20
AskWoody LoungerOctober 15, 2020 at 2:24 am #2304406I don’t see a change to say the re-releases are only for Windows 7.
I read this : “Microsoft re-releases buggy July .NET Security Only patches” and there is still NOTHING there to show the topic was in regards to Windows 7 only.
At the bottom of the above topic you have one update that is a link to PKCano’s post which I clicked on and still didn’t understand was irrelevant to Windows 10. To confuse me further, Belarc Advisor says I have one missing 1809 security update and that it is https://support.microsoft.com/en-us/help/4576627. So, I went to Microsoft Catalog and downloaded it only to be told when I try to install it that it is not applicable to my Windows 10 1809 computer.
I figured out (after hair pulling) that I needed to install https://support.microsoft.com/en-us/help/4579976 which I did. Belarc Advisor still claims I need the Sept .NET cumulative update and I have concluded that is because they have not had even 24 hours after Microsoft offered the Oct .NET update to add that to Belarc Advisor.
-
PKCano
ManagerOctober 15, 2020 at 4:54 am #2304416Actually, both Win7 and Win8.1 had re-released July Security-only patches. But this thread is exclusively about Win7, and I am baby-sitting the extended updates for same here. So the only posting here (and on my update first post below the Patch Tuesday blog post) is mostly about Win7.
Further note: Granted, version would have made things clearer in the title, but Win10 DOES NOT have Security-only patches for anything, Only Win7/8.1 still have have that option. So information about July Security-only patches couldn’t have any bearing on Win10 anyway.
-
SFB
AskWoody LoungerOctober 15, 2020 at 10:22 am #2304498Maybe there should be a separate thread that discuss updates / issues for .net (DOTNET). The .NET Blog is the best resource that I have found so far.
A blog post that lists all the October .NET updates can be found here: https://devblogs.microsoft.com/dotnet/net-framework-october-2020-security-and-quality-rollup-updates/
Pinging off of what PKCano said above: Using the chart from the October .NET blog post linked above search the update catalog to find the appropriate Rollup for your system so that you don’t have to install separate updates for each version of .NET installed on your system.
Two examples of Rollups are:
- Windows 7 Security and Quality Rollup (4579977) contains KB4578952, KB4578955, KB4578963, and KB4578977.
- Windows 7 Security Only Rollup (4580467) contains KB4578980, KB4578983, KB4578987, and KB4578990.
The same methodology can be applied to the other versions of Windows using the October chart and the update catalog.
ASoft .NET Version Detector is an extremely helpful program that lists all the .NET versions that are installed in your system along with the associated update KB numbers.
-
TonyC
AskWoody LoungerOctober 16, 2020 at 3:42 am #2304668At one time, I thought that the introduction to this topic stated that W7ESUI is able to install only .NET 3.5.1 updates – that is, it is not able to install .NET 4 updates. However, all mention of “3.5.1” now appears to have disappeared from the introduction.
Is my memory correct? Is it still the case that W7ESUI can install only .NET 3.5.1 updates, or can it now install any .NET update?
-
PKCano
ManagerOctober 16, 2020 at 4:10 am #2304675At one time, I thought that the introduction to this topic stated that W7ESUI is able to install only .NET 3.5.1 updates – that is, it is not able to install .NET 4 updates.
That is correct. W7ESUI does not install the .NET4 updates.
You need to use the BYPASS for the .NET4 patches. The information is at the bottom of the main thread post (the first one at the top) between double rows of ***********. The download link is also there.As a rule, the information you need each month for the ESU updates w/o license is at the top of the comments on the Patch Tuesday Main Blog Post.
See #2303933.1 user thanked author for this post.
-
anonymous
GuestOctober 18, 2020 at 4:25 am #2305093I gather from your comments that W7SU and the Bypass scripts both work for the October patches concerned.
Maybe you should include the new SSU (if any) in your AKB2000003?
-
PKCano
Manager -
Guest
AskWoody LoungerOctober 30, 2020 at 12:56 pm #2308275I have used this once previously with everything going as expected. This second time it did not create the neutralize telemetry script on reboot. Should it have?
I noticed, using https://www.askwoody.com/forums/topic/2000012-neutralize-telemetry-sustain-win-7-8-1-monthly-rollup-model/, that it created (something from August/September/October SO, IE, .Net, newest stack updates) AutoLogger-Diagtrack-Listener again so I manually disabled that.
Would someone mind pasting the contents of that neutralize telemetry script so that I can double check what else might have been changed? I recall the script within this differed a little from the w10tel.cmd one so I want to make sure I check both.
-
anonymous
GuestOctober 31, 2020 at 7:35 pm #2308533On Oct, 30 I installed the below October Windows updates on two Win 7, SP 1, x64 systems.
Three .msu’s installed with W7ESUI.cmd:
4580970 (Servicing Stack Update)
4580345 (Win 7 Security Monthly Quality Rollup)
4578952 (.NET 3.5.1 Security and Quality Rollup for .NET framework 3.5.1)The .exe installed with dotNetFx4_ESU_Installer.cmd:
4578977 (Security and Quality Rollup for .NET Framework 4.8)Updates applied smoothly and everything has been running fine.
Thanks once again to abbodi86 and PKCano.
-
byteme
AskWoody PlusNovember 2, 2020 at 6:21 pm #2309117Win7 Home Premium, 64-bit. Group B.
I installed the October updates over the weekend, and all seems well.
I used the W7ESUI script to install three files (no IE update for October): the SSU (4580970), the Win7 Security Only update (4580387), and the NET 3.5.1 Security and Quality Rollup (4578952). And restarted and waited a while.
And I used the July version of the dotNetFx4_ESU_Installer to install the NET 4.8 Security and Quality Rollup (4578977). And restarted (not officially required) and waited a while.
And then I installed the four final-ever (*sniffles*) updates to Office 2010 using Windows Update.
Thanks once again to abbodi86 and PKCano
-
PKCano
ManagerNovember 10, 2020 at 2:17 pm #2311043Here’s your .NET fix for November. There were no Security-only .NET updates.
Download only the update for the version(s) installed on your PC.
There were only updates for .NET 4.6-4-7-2 and 4.8
The other updates in the Rollup are older and should already be installed..NET Quality Rollup KB4586083
.NET 3.5.1 KB4578952 (Oct update)
.NET 4.5.2 KB4578955 (Oct update)
.NET 4.6 – 4.7.2 KB4585204
.NET 4.8 KB4585205 -
anonymous
GuestNovember 11, 2020 at 4:40 am #2311137HI. I am enquiring about the following that I read for the first time
on the link provided in the … patches out Nov 10 thread:
<Known Issues
Windows 7 SP1 and Server 2008 R2
Updates will uninstall if the system is not subscribed to ESU (Extended Security Updates).>Is this starting in November? I’ve installed Sept & Oct .Net Frameworks
w BypassESU v9 AIO a couple of days ago a well as Monthy Rollup by W7ESUI_0.2
– thank you – which went fine.
The September overview vaguely stated, ‘Updates may fail to install if the
system is not supported by ESU.’
I hope the ones already installed after January won’t have troubles.
Thanks. -
anonymous
Guest -
Paul T
AskWoody MVPNovember 11, 2020 at 8:30 am #2311178Where does it say the updates will be uninstalled? I can’t find it in that thread.
https://www.askwoody.com/forums/topic/ms-defcon-2-windows-and-office-patches-out-nov-10/cheers, Paul
-
PKCano
ManagerNovember 11, 2020 at 8:56 am #2311185From the gHacks link mentioned in #2311054 (this might be for people trying to install without the bypass):
Known Issues
Windows 7 SP1 and Server 2008 R2
-
Updates will uninstall if the system is not subscribed to ESU (Extended Security Updates).
-
Certain rename operations may fail on Cluster Shared Volumes. Workarounds available.
1 user thanked author for this post.
-
-
glnz
AskWoody PlusNovember 12, 2020 at 12:13 pm #2311497FWIW, when I started an hour ago to install the 2020-10 updates for my Win 7 Pro 64-bit, and I ran KB4578977 (to update .NET 4.8) in my dotNetFx4_ESU, it did a “rollback” and showed progress for “rolling back”.
I don’t know why. Maybe I had installed it before??
So I just ran it again, and it gave me normal installation progress.
I’ll check Installed Updates and Belarc Advisor and let you know shortly, when the others finish installing in W7ESUI.
Stand by!!!!!!!!
-
PKCano
Manager -
Cyrus Khambatta
AskWoody Lounger -
anonymous
GuestNovember 24, 2020 at 4:16 pm #2314188On Oct, 23 I installed two of the below November Windows updates on two Win 7, SP 1 Home Premium systems.
NOTE: Only updates for .NET 4.8 and Nov. Rollup needed to be installed. The other updates are older and should already have been be installed.
One .msu installed with W7ESUI.cmd:
SSU KB4580970 (Oct update – should already be installed)
Win 7 Monthly Rollup KB4586827
.NET 3.5.1 KB4578952 (Oct update – should already be installed)The .exe installed with dotNetFx4_ESU_Installer.cmd:
.NET 4.8 KB4585205Thanks to abbodi86 and PKCano for sharing their knowledge.
-
AusJohn
AskWoody PlusNovember 25, 2020 at 6:57 pm #2314451I’ve tried to install Win 7 Monthly Rollup 4586827 on my Win 7 SP1 32-bit Professional machine, using W7ESUI v0.2 run as Administrator, but it stops after a short while with the message:
All applicable updates are detected as installed
============================================================
Removing temporary extracted files…
========================================================================================================================
Finished
============================================================SSU KB4580970 (October 2020) is already installed.
The update (using the .msu file) definitely hasn’t been installed because I just downloaded it from the Windows Update Catalog. And, as expected, it’s not showing in the list of installed updates.
This is the first time that I haven’t been able to install updates using the W7ESUI script.
Any ideas as to what the problem may be, and how I can get it to install?
1 user thanked author for this post.
-
PKCano
ManagerNovember 25, 2020 at 7:10 pm #2314453I had no problem on 3 machines. The obvious questions:
Have you looked in installed updates to verify it’s not already installed?
Have you checked the file name to be sure it is x86 (not x64) and has the right KB number 4586827?
Did you put it in a folder with the contents of W7ESUI.v0.2.zip?
Right click on the .cmd file and Run as Administrator?
Have you tried with a fresh downloaded copy of W7ESUI.v0.2.zip? -
AusJohn
AskWoody PlusNovember 25, 2020 at 8:16 pm #2314468Have you looked in installed updates to verify it’s not already installed?
Yes
Have you checked the file name to be sure it is x86 (not x64) and has the right KB number 4586827?
Yes
Did you put it in a folder with the contents of W7ESUI.v0.2.zip?
Yes
Right click on the .cmd file and Run as Administrator?
Yes
Have you tried with a fresh downloaded copy of W7ESUI.v0.2.zip?
Yes
Any other thoughts or suggestions?
-
PKCano
ManagerNovember 26, 2020 at 4:38 am #2315036One last check then I give up.
Delete the copy of 4586827 you downloaded, download a fresh copy, and try again. -
AusJohn
AskWoody PlusNovember 26, 2020 at 4:49 am #2315039Thanks for the suggestion.
I’ve just done as you suggested, but the result – surprise, surprise – was the same.
That is:
“All applicable updates are detected as installed”
So once again, thank you. You’ve done all you can, and I appreciate that, so now you can give up.
-
abbodi86
AskWoody_MVPNovember 26, 2020 at 8:03 am #2315055W7ESUI include debug mode which may help identifying the issue
edit W7ESUI.cmd with notepad and change
set _Debug=0toset _Debug=1
save changes and run the script, wait until it finish and create the debug log
then zip/attach the log, or use https://pastebin.com -
Sinclair
AskWoody LoungerNovember 26, 2020 at 10:40 am #2315081Not sure if it is related but this website may offer some insight:
The two top articles dated November 22nd, 2020 talk about how Microsoft changed some things in the way ESU checks are done in the October and November patches.
Windows 7 ESU Analysis Updates
W10&11 x64 Pro&Home
1 user thanked author for this post.
-
abbodi86
AskWoody_MVPNovember 26, 2020 at 12:04 pm #2315098The “way” is not changed
they only bumped ESU manifest version from 7601 to 7602, which makes no difference for W7ESUIthat site hacks updates links from WHDownloader, and it spoil the way how ESU bypass works, very selfish
also, what’s the point of uploading msu files (some are splitted) to github when windowsupdates links are working fine? -
Sinclair
AskWoody LoungerNovember 26, 2020 at 12:38 pm #2315106The post was ment as a reply to you in regard to AusJohn’s problem. It got posted as a general reply to your top post. A problem I seem to have a lot on this site even though I hit the reply button.
I was using Google to search the various KB’s as I also wanted to know why AusJohn can not get the patch to install. At one point this site came up. And looking into it it struck me as a sort of Askwoody site. Since he talks about how to patch a fresh 2020 install of Windows 7 and how best to do this.
So I thoughed lets post it here and you or PKCano will say if it usefull or not.
Thank you for your insight. BTW your scripts are amazing most helpfull.
W10&11 x64 Pro&Home
1 user thanked author for this post.
-
AusJohn
AskWoody PlusNovember 26, 2020 at 9:45 pm #2315160 -
anonymous
GuestNovember 27, 2020 at 4:58 am #2315216Have you tried using BypassESU v9 AIO?
-
AusJohn
AskWoody PlusNovember 27, 2020 at 5:14 am #2315218No. Should I?
And if ‘yes’, which option should I select, from 1, 2, and 3?
-
abbodi86
AskWoody_MVP -
PKCano
ManagerNovember 27, 2020 at 6:56 am #2315227One last check then I give up. Delete the copy of 4586827 you downloaded, download a fresh copy, and try again.
I just looked at the download from the Catalog.
There is no “all” in the download file name at this time.
Wonder where that file came from, @AusJohn?1 user thanked author for this post.
-
abbodi86
AskWoody_MVP -
anonymous
GuestNovember 27, 2020 at 11:10 am #2315261After reading @abbodi86 ‘s post just above (#2315254) about the ActiveX version of the catalog adding the word “all” to the file name, thus preventing the script from finding the update, I’d start using another browser to get the updates from now on. As @PKCano has shown, the word “all” doesn’t show up in the file name when using other browsers to download the files from the Catalog.
I believe the browser @PKCano used is Firefox, or one of it’s variants, judging from the look of the image in the post just above showing the filename in the Catalog without the word “all”.
-
anonymous
GuestNovember 27, 2020 at 11:10 am #2315262Oops, forgot to add the phrase “…another browser besides IE (Internet Explorer)…”
-
PKCano
ManagerNovember 27, 2020 at 11:11 am #2315265Using Firefox 83.0
-
RDRguy
AskWoody LoungerNovember 27, 2020 at 4:12 pm #2315323Is tweaking W7ESUI.v0.2.zip to automatically “parse & strip out” or “accommodate” the additional IE11 downloaded update file name characters possible?
An updated W7ESUI.v0.3.zip version perhaps
Yet another reason to stop using IE11 (wonder if EDGE does the same)
Win7 - PRO & Ultimate, x64 & x86
Win8.1 - PRO, x64 & x86
Groups A, B & ABS -
AusJohn
AskWoody PlusNovember 27, 2020 at 6:26 pm #2315340Thank you so much.
I did as you suggested and, of course, the install worked like a charm.
It even shows in the list of “Installed Updates”.
Your assistance is sincerely appreciated.
-
anonymous
GuestNovember 28, 2020 at 7:22 am #2315421Whether you “should” is up to you, but I guess you could give it a try. I’m not sure which Option you should choose.
I have to be careful here because I’m actually not sure about the technical differences between the Bypass and W7ESUI. As far as I understand, thought, both were developed by abbodi1486 and colleagues.
Furthermore, to the best of my understanding – and here I’m skating on very thin ice – the former is used to install the “normal” updates, whereas the latter dealt with some issues related to .NET updates.
Though it’s time consuming, you might want to review some of the earlier posts in this thread.
In regard to the Bypass, obligatory reading is abbodi1486’s original post at
https://forums.mydigitallife.net/threads/bypass-windows-7-extended-security-updates-eligibility.80606/1 user thanked author for this post.
-
PKCano
ManagerNovember 28, 2020 at 7:24 am #2315424Access to abbodi1486’s original post requires login to MyDigitalLife.
-
abbodi86
AskWoody_MVPNovember 28, 2020 at 9:45 am #2315436Is tweaking W7ESUI.v0.2.zip to automatically “parse & strip out” or “accommodate” the additional IE11 downloaded update file name characters possible?
An updated W7ESUI.v0.3.zip version perhaps
Yet another reason to stop using IE11 (wonder if EDGE does the same)
That’s probably doable
i use the same technique to detect update KB number in all my scripts (since 2014 or so)
i also have known about IE-ActiveX changing Catalog downloaded files names since it was exclusive to IE
but this is the first time i encounter this issuei never used MS Edge legacy, and the new MS Edge Chromium will not change the files names
-
Moonbear
AskWoody LoungerNovember 29, 2020 at 7:03 pm #2315765After installing this months updates and restarting, upon reaching 100% installed, my system restarted again. Was this supposed to happen?
No other issues to report and system running smoothly otherwise.
-
This reply was modified 4 years, 6 months ago by
Moonbear.
1 user thanked author for this post.
-
This reply was modified 4 years, 6 months ago by
-
glnz
AskWoody Plus -
PKCano
ManagerNovember 30, 2020 at 6:26 pm #2316595@Cybertooth wrote:
I’m trying to catch up on the patches (have several Windows 7 systems to maintain) and am hitting a snag with the September 2020 patches. After right-clicking on the W7ESUI.com and OK’ing the UAC prompt, I’m getting the following error:What am I doing wrong? This had not happened before.
NOTE:
This discussion has been moved to
Topic #2316545 Can’t open Administrator prompt to run W7ESUI1 user thanked author for this post.
-
byteme
AskWoody PlusDecember 1, 2020 at 11:14 am #2316269Win7 Home Premium, 64-bit. Group B.
I installed the November updates over the weekend, and all seems well.
I used the W7ESUI script to install two files (no SSU or NET 3.5.1 updates for November): the Win7 Security Only update (4586805), and the IE Security Only update (4586768). And restarted and waited a while.
And I used the July version of the dotNetFx4_ESU_Installer to install the NET 4.8 Security and Quality Rollup (4585205). And restarted (not officially required) and waited a while.
And then I installed the unexpected updates to Office 2010, and the Malicious Software Removal Tool, using Windows Update.
Thanks again to abbodi86 and PKCano.
-
Microfix
AskWoody MVP -
alpha128
AskWoody PlusDecember 9, 2020 at 7:29 am #2318233On my own system I’ve been using this script since March 2020. I’ve used it to install the 2020-03 Security Monthly Quality Rollup for Windows 7 for x64-based Systems (KB4540688) through the 2020-11 Security Monthly Quality Rollup for Windows 7 for x64-based Systems (KB4586827).
I recently tried to install the 2020-11 rollup on another computer that hadn’t been updated at all since Win 7 end of life in January 2020. I was able to get the October Servicing Stack (KB4580970) and the October rollup for .NET 3.5 (KB4578952) installed without difficulty using this script. But when I tried to install the big patch, the 2020-11 Win 7 rollup (KB4586827), I got the following output.
File Not Found ============================================================ Checking Updates… ============================================================ All applicable updates are detected as installed ============================================================ Removing temporary extracted files… ============================================================ ============================================================ Finished ============================================================ Press 9 to exit.
I checked and made sure SHA2 support updates KB4490628 and KB4474419 were installed before I did anything. And at the end, I ran a “sfc /scannow” and found no problems.
I don’t know why it’s not working. He definitely doesn’t have any of the Win 7 ESU rollups installed.
The main difference is, as I wrote above, I’ve been updating my system every month (skipping only 2020-02), while I tried to skip nine months (2020-02 through 2020-10) on the other system. Unfortunately I had only copied the latest rollup to my flash drive, and so I couldn’t test the installation of earlier rollups.
Is there something in one of the earlier rollups that needs to be installed for the later rollups to work? Should I try that? Or is there an easier way to get the 2020-11 rollup installed?
Thanks in advance.

-
anonymous
GuestDecember 9, 2020 at 8:05 am #2318239reads like you are missing kb4575903 and kb4580970 SSU to install the november patches
-
Microfix
AskWoody MVPDecember 9, 2020 at 8:28 am #2318244then you’ll need the missing dotNET patches for whatever version is installed.
IIRC November was the last dotNET update for v4.52 onwardsWindows - commercial by definition and now function... -
abbodi86
AskWoody_MVP -
PKCano
Manager -
alpha128
AskWoody PlusDecember 9, 2020 at 8:32 pm #2318383then you’ll need the missing dotNET patches for whatever version is installed.
IIRC November was the last dotNET update for v4.52 onwardsI got that installed without any issues.

-
alpha128
AskWoody Plus -
alpha128
AskWoody PlusDecember 14, 2020 at 7:44 pm #2319627Verify the integrity of the Rollup MSU file
or try to run the script in debug mode as explained here #2315055
I think the November patch I was trying to install the first time was corrupt. I installed all the October patches, and then went back and installed November rollup. No issues the second time. Thanks!

-
anonymous
GuestDecember 21, 2020 at 3:38 pm #2321703Where can I find the .NET updates for December? Specifically looking for the update for a Windows 7 Home Premium, Service Pack 1, x64 machine.
-
PKCano
ManagerDecember 21, 2020 at 3:39 pm #2321708There was no .NET update for Win7 in the Dec updates.
-
anonymous
GuestDecember 29, 2020 at 3:55 pm #2323836On the morning of Dec. 29 I installed these two updates to two Windows 7 Home Premium, Service Pack 1, x64 machines using W7ESUI.
Latest SSU KB4592510
Dec. Rollup KB4592471
I have been using the machines most of the day and have not encountered any problems.
1 user thanked author for this post.
-
-M-
AskWoody LoungerJanuary 2, 2021 at 12:50 pm #2324861Just installed the 2 december updates using W7ESUI_0.1 with no problems. In fact, I got Aero back which I lost for some reason and couldn’t turn back on after a Comodo free firewall product update. I had already installed installed the november updates at the time.
Again, thanks a lot for this script, I have a tough time moving away from W7
1 user thanked author for this post.
Viewing 576 reply threads- The topic ‘Comments on Abbodi86’s Win7 ESU Installer Script (2020 Archive)’ is closed to new replies.
-

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Windows 10 22H2 Update today (5 June) says up-to-date but last was 2025-04
by
Alan_uk
16 minutes ago -
Thoughts on Malwarebytes Scam Guard for Mobile?
by
opti1
3 hours, 24 minutes ago -
Mystical Desktop
by
CWBillow
3 hours, 38 minutes ago -
Meta and Yandex secretly tracked billions of Android users
by
Alex5723
6 hours, 20 minutes ago -
MS-DEFCON 2: Do you need that update?
by
Susan Bradley
47 minutes ago -
CD/DVD drive is no longer recognized
by
WSCape Sand
18 hours, 51 minutes ago -
Windows 11 24H2 Default Apps stuck on Edge and Adobe Photoshop
by
MikeBravo
21 hours, 40 minutes ago -
North Face and Cartier customer data stolen in cyber attacks
by
Alex5723
19 hours, 46 minutes ago -
What is wrong with simple approach?
by
WSSpoke36
12 hours, 18 minutes ago -
Microsoft-Backed Builder.ai Set for Bankruptcy After Cash Seized
by
Alex5723
1 day, 7 hours ago -
Location, location, location
by
Susan Bradley
59 minutes ago -
Cannot get a task to run a restore point
by
CWBillow
1 day, 8 hours ago -
Frustrating search behavior with Outlook
by
MrJimPhelps
23 hours, 20 minutes ago -
June 2025 Office non-Security Updates
by
PKCano
1 day, 19 hours ago -
Secure Boot Update Fails after KB5058405 Installed
by
SteveIT
15 hours, 46 minutes ago -
Firefox Red Panda Fun Stuff
by
Lars220
1 day, 19 hours ago -
How start headers and page numbers on page 3?
by
Davidhs
2 days, 5 hours ago -
Attack on LexisNexis Risk Solutions exposes data on 300k +
by
Nibbled To Death By Ducks
1 day, 8 hours ago -
Windows 11 Insider Preview build 26200.5622 released to DEV
by
joep517
2 days, 14 hours ago -
Windows 11 Insider Preview build 26120.4230 (24H2) released to BETA
by
joep517
2 days, 14 hours ago -
MS Excel 2019 Now Prompts to Back Up With OneDrive
by
lmacri
2 days, 4 hours ago -
Firefox 139
by
Charlie
1 day, 20 hours ago -
Who knows what?
by
Will Fastie
23 hours, 3 minutes ago -
My top ten underappreciated features in Office
by
Peter Deegan
2 days, 15 hours ago -
WAU Manager — It’s your computer, you are in charge!
by
Deanna McElveen
8 hours, 43 minutes ago -
Misbehaving devices
by
Susan Bradley
1 day, 10 hours ago -
.NET 8.0 Desktop Runtime (v8.0.16) – Windows x86 Installer
by
WSmeyerbos
3 days, 21 hours ago -
Neowin poll : What do you plan to do on Windows 10 EOS
by
Alex5723
19 hours, 56 minutes ago -
May 31, 2025—KB5062170 (OS Builds 22621.5415 and 22631.5415 Out-of-band
by
Alex5723
3 days, 19 hours ago -
Discover the Best AI Tools for Everything
by
Alex5723
2 days, 18 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.