News on that infuriating MSRT update bug. If you recall, the version of KB 890830 that arrived on Patch Tuesday was all over the map. As I said in Com
[See the full post at: Born: Microsoft incorrectly signed the MSRT update that’s been bouncing around. It’s fixed now.]

|
There are isolated problems with current patches, but they are well-known and documented on this site. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
-
Born: Microsoft incorrectly signed the MSRT update that’s been bouncing around. It’s fixed now.
Home » Forums » Newsletter and Homepage topics » Born: Microsoft incorrectly signed the MSRT update that’s been bouncing around. It’s fixed now.
- This topic has 19 replies, 12 voices, and was last updated 5 years, 6 months ago.
AuthorTopicwoody
ManagerNovember 14, 2019 at 1:01 pm #2005424Viewing 8 reply threadsAuthorReplies-
Hopper15
AskWoody Plus -
Speccy
AskWoody LoungerNovember 14, 2019 at 1:30 pm #2005430With all due respect, Gunter’s article is inaccurate: the Catalog “Last Updated” date disparity (12 Nov for Win8.1/10 and 13 Nov for Win7/Server 2008/R2) has nothing to do with the issue and it certainly does NOT mean that (quoting) “Microsoft has updated the package for Windows 7 and Server 2008/r2 and replaced the faulty certificate.“: the binaries are exactly the same (digitally signed November 7, 2019).

There was no “faulty certificate”, nor was it replaced: the root cause of the issues IS the [lack of] SHA-2 support (and probably some metadata glitches on WU) – as I explained here. -
woody
ManagerNovember 14, 2019 at 2:11 pm #2005438OMG. Here’s your conclusion:
Last month’s MSRT (v5.76, Oct, 2019) was still SHA-256 and SHA-1 signed, but this month’s MSRT (v5.77, Nov, 2019) is NOT SHA-1 signed (only SHA-256 signed) – and that seems to be the core reason for the reported errors…
WU might have (had?) a conflict issue (metadata?) with that, since it was offering MSRT on Tuesday but not yesterday (Nov 13, 2019)… don’t know if Microsoft fixed it already but, whatever the reason is, MSRT may be manually downloaded from the Catalog (here) and, for sure, it will execute properly if BOTH the SHA-2 support and SSU updates have been installed.
And I can confirm that the binaries are the same — at least the binary in the latest version of the patch is signed November 7.
4 users thanked author for this post.
-
-
howardagoldberg
AskWoody PlusNovember 14, 2019 at 3:19 pm #2005458“UPDATE: @Speccy has observed that the problem isn’t with the certificate, but with our old friend the SHA-2 signing problem with Win7 patches. Looks like he’s right. Read more here.”
Well, if that is true – then my comment in this thread: https://www.askwoody.com/forums/topic/november-2019-patch-tuesday-arrives/ …
‘At any rate, it looks like the issue is with WU trying to install the November MSRT before installing the SSU, and MSRT needed SSU to be installed first …’
May have been the issue. Interesting …
-
Speccy
AskWoody LoungerNovember 14, 2019 at 4:39 pm #2005472Also, the KB890830 links are currently (as I write this) BROKEN:
- The “Download the x64 MSRT package now.” link should be
https://www.microsoft.com/en-us/download/details.aspx?familyid=585d2bde-367f-495e-94e7-6349f4effc74
(redirecting to https://www.microsoft.com/en-us/download/details.aspx?id=9905)
instead of the broken
http://www.microsoft.com/downloads/en/details.aspx?familyid=585d2bde-367f-495e-94e7-6349f4effc74 - The “Download the x86 MSRT package now.” link should be
https://www.microsoft.com/en-us/download/details.aspx?familyid=ad724ae0-e72d-4f54-9ab3-75b8eb148356
(redirecting to https://www.microsoft.com/en-us/download/details.aspx?id=16)
instead of the broken
http://www.microsoft.com/downloads/details.aspx?familyid=ad724ae0-e72d-4f54-9ab3-75b8eb148356&displaylang=en
Microsoft websites seem to be under major overhauling (with many broken links and contents being moved or deleted).
As an additional tip, some “broken links” might be “fixed” simply by searching for the ENGLISH contents (or manipulating the URL to include ‘/en/’ or ‘/en-us/’).
4 users thanked author for this post.
- The “Download the x64 MSRT package now.” link should be
-
-
PKCano
ManagerNovember 14, 2019 at 3:35 pm #2005465Yesterday, the MSRT failed on my Win7.
I installed the Nov Cu KB4525235 and the SSU KB4523206 (KB4490628 and KB4516655 and the 4474419s all versions had been installed previously).
Went back twice, later and much later, and the MSRT failed again both times.
I concluded it was not the SSUs being the problem. -
Speccy
AskWoody LoungerNovember 14, 2019 at 5:50 pm #2005524A couple more hints on what might have happened (and partially explain why different people are having seemingly random results with WU offering/not offering MSRT upon multiple executions, errors thrown, etc.)…
1) From the KB890830 FAQs:
Q8: Why do not I see the tool on Microsoft Update, Windows Update, or Automatic Updates?
A8: (…) If you have already run the current version of the tool from Windows Update, Microsoft Update, Automatic Updates, or from either of the other two release mechanisms, it will not be reoffered on Windows Update or Automatic Updates.Q9: How do Microsoft Update, Windows Update, and Automatic Updates determine who the tool is offered to?
A9: (…) The users have not already run the current version of the tool.2) From the KB891716 FAQs:
Q2. How do I verify that the removal tool has run on a client computer?
A2. You can examine the [Version REG_SZ] value data for the [HKLM\SOFTWARE\Microsoft\RemovalTools\MRT] registry entry to verify the execution of the tool. (…)
Every time that the tool is run, the tool records a GUID in the registry to indicate that it has been executed:1ED49A70-3903-4C40-B575-93F3DD50B283 (November 2019) E63797FA-851A-4E25-8DA1-D453DD437525 (October 2019)
This occurs regardless of the results of the execution.
3 users thanked author for this post.
-
woody
Manager -
Speccy
AskWoody LoungerNovember 16, 2019 at 5:57 am #2006222When manually executed, the KB890830 package will simply unpack MRT.exe to the %WINDIR%\System32 folder and exit the thread, transferring control to it.
Then the %WINDIR%\System32\MRT.exe process will start executing, writing
--------------------------------------------------------------------------------------- Microsoft Windows Malicious Software Removal Tool v5.77, November 2019 (build 5.77.16547.2) Started On Sat Nov 16 11:15:52 2019 Engine: 1.1.16500.1 Signatures: 1.305.993.0 MpGear: 1.1.16330.1 Run Mode: Interactive Graphical Mode
into the %WINDIR%\debug\mrt.log file. Once you press the ‘Next’ button twice, the tool will start scanning (a Quick Scan, by default, if not otherwise selected).
During the scanning process the ‘Version’ REG_SZ registry value remains unaltered: the GUID update in the Registry only happens near the end (when the scanning process finishes – either normally or, presumably, also through an exception catching mechanism if an error occurs and the application ends abnormally):

Then the tool waits for the user input:
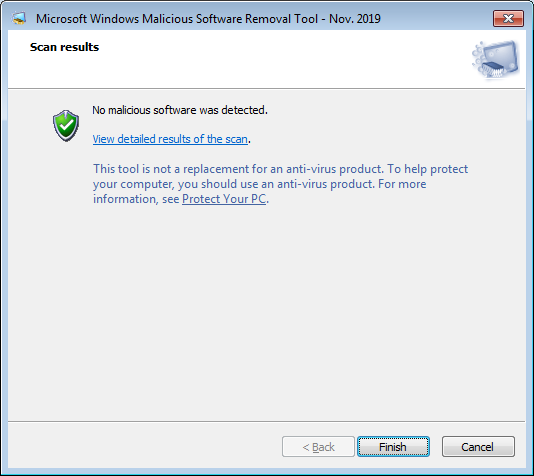
Once the ‘Finish’ button is pressed, the %WINDIR%\debug\mrt.log file is appended with the collected results (and the heartbeat “phone home” attempt occurs – successfully or not, depending if you allow it or not to happen):Results Summary: ---------------- No infection found. Failed to submit clean hearbeat MAPS report: 0x80072EE7 Microsoft Windows Malicious Software Removal Tool Finished On Sat Nov 16 11:28:40 2019 Return code: 0 (0x0)
1 user thanked author for this post.
-
-
-
-
Seff
AskWoody Plus -
Pierre77
AskWoody Plus
-
-
CADesertRat
AskWoody PlusNovember 14, 2019 at 7:26 pm #2005556So far this discussion has been about the MSRT for W7. Yesterday 11/13/19 I got a CU/SSU and MSRT on 1809 and all installed but the MSRT failed. So my assumption is that MSRT is failing on every version of windows. Is that correct?
Seems odd that after all these years that MS has been doing great with MSRT, all of a sudden MSRT is as screwed up as the rest of MS’s updates. Month by month things aren’t getting better, they are getting worse.
Don't take yourself so seriously, no one else does
All W10 Pro at 22H2,(2 Desktops, 1 Laptop). -
PKCano
Manager -
Myst
AskWoody PlusNovember 15, 2019 at 1:47 am #2005631Seems odd that after all these years that MS has been doing great with MSRT, all of a sudden MSRT is as screwed up as the rest of MS’s updates.
Not the first time there’s been a problem with the MSRT. This came up in a recent post https://www.askwoody.com/forums/topic/heartbeat/#post-1999709
https://borncity.com/win/2017/04/13/issued-with-update-kb890830-microsoft-removal-tool/MacOS iPadOS and sometimes SOS
4 users thanked author for this post.
-
CADesertRat
AskWoody PlusNovember 15, 2019 at 9:32 am #2005761Not the first time there’s been a problem with the MSRT. This came up in a recent post
Thanks, I hadn’t seen that but your still talking about a recent event. I don’t remember ever having a problem with MSRT on my W7 or W10 machines previously.
Don't take yourself so seriously, no one else does
All W10 Pro at 22H2,(2 Desktops, 1 Laptop).1 user thanked author for this post.
-
-
-
dgreen
AskWoody LoungerNovember 15, 2019 at 4:47 am #2005683I stopped installing and started hiding MSRT updates in Feb. this year.
My reason was nothing more than just a “gut” feeling.
I’m glad I did.Dell Inspiron 660 (new hard drive installed and Windows 7 reloaded Nov. 2017)
Windows 7 Home Premium 64 bit SP 1 GROUP A
Processor: Intel i3-3240 (ivy bridge 3rd generation)
chipset Intel (R) 7 series/C216
chipset family SATA AHCI Controller -1 E02
NIC Realtek PCLE GBE Family Controller
MSE antivirus (has new name now)
Chrome browser
DSL via ethernet (landline)-
This reply was modified 5 years, 6 months ago by
dgreen.
-
This reply was modified 5 years, 6 months ago by
-
ch100
AskWoody_MVPNovember 16, 2019 at 1:41 pm #2006396The KB90830 MSRT November 2019 for Windows 7 and 2008 R2 is not “fixed”, but removed from Windows Update/expired from WSUS.
This is the only reason why it is not seen as failing anymore.
It is no longer offered.
There was a workaround for the failing installation, which was mentioned before by someone else.
By “installing” manually, which means running the executable from the Catalog, the broken patch was no longer offered by Windows Update as it was seen as previously installed successfully.
All of the above do not apply to later versions of Windows.While I don’t completely understand the reasons for the Windows update failures, I would say with a high degree of certainty that it is related to the WU agent not understanding the new signing mechanism for this update. It is likely that we will see either a new version of the WU agent released soon, or as an intermediate solution, a new release of the MSRT using the previous signing implementation.
-
Speccy
AskWoody LoungerNovember 17, 2019 at 6:27 am #2006643“(…) I would say with a high degree of certainty that it is related to the WU agent not understanding the new signing mechanism for this update. It is likely that we will see either a new version of the WU agent released soon, or as an intermediate solution, a new release of the MSRT using the previous signing implementation.”
I agree. It is also my understanding about what might have happened – you nailed it!
(emphasis above, on the possibility of an upcoming, new MSRT to be released soon: it has happened before [December 2008, August 2005] and, in fact, currently the Catalog is not “offering” KB890830 for Windows 7/Server 2008/R2 [that, basically, was the same unique binary currently being offered only for Windows 8.1/10/Server 2012/R2/Server 2016] anymore…)
1 user thanked author for this post.
-
-
JohnW248
AskWoody LoungerNovember 16, 2019 at 5:29 pm #2006479
Viewing 8 reply threads -

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Windows AI Local Only no NPU required!
by
RetiredGeek
3 hours, 40 minutes ago -
Stop the OneDrive defaults
by
CWBillow
6 hours, 42 minutes ago -
Windows 11 Insider Preview build 27868 released to Canary
by
joep517
9 hours, 8 minutes ago -
X Suspends Encrypted DMs
by
Alex5723
11 hours, 20 minutes ago -
WSJ : My Robot and Me AI generated movie
by
Alex5723
11 hours, 38 minutes ago -
Botnet hacks 9,000+ ASUS routers to add persistent SSH backdoor
by
Alex5723
12 hours, 15 minutes ago -
OpenAI model sabotages shutdown code
by
Cybertooth
12 hours, 52 minutes ago -
Backup and access old e-mails after company e-mail address is terminated
by
M W Leijendekker
1 hour, 2 minutes ago -
Enabling Secureboot
by
ITguy
8 hours, 1 minute ago -
Windows hosting exposes additional bugs
by
Susan Bradley
20 hours, 46 minutes ago -
No more rounded corners??
by
CWBillow
16 hours, 34 minutes ago -
Android 15 and IPV6
by
Win7and10
6 hours, 20 minutes ago -
KB5058405 might fail to install with recovery error 0xc0000098 in ACPI.sys
by
Susan Bradley
1 day, 9 hours ago -
T-Mobile’s T-Life App has a “Screen Recording Tool” Turned on
by
Alex5723
1 day, 11 hours ago -
Windows 11 Insider Preview Build 26100.4202 (24H2) released to Release Preview
by
joep517
1 day, 6 hours ago -
Windows Update orchestration platform to update all software
by
Alex5723
1 day, 19 hours ago -
May preview updates
by
Susan Bradley
1 day, 6 hours ago -
Microsoft releases KB5061977 Windows 11 24H2, Server 2025 emergency out of band
by
Alex5723
22 hours, 6 minutes ago -
Just got this pop-up page while browsing
by
Alex5723
1 day, 11 hours ago -
KB5058379 / KB 5061768 Failures
by
crown
1 day, 8 hours ago -
Windows 10 23H2 Good to Update to ?
by
jkitc
10 hours, 35 minutes ago -
At last – installation of 24H2
by
Botswana12
2 days, 10 hours ago -
MS-DEFCON 4: As good as it gets
by
Susan Bradley
7 hours, 22 minutes ago -
RyTuneX optimize Windows 10/11 tool
by
Alex5723
2 days, 22 hours ago -
Can I just update from Win11 22H2 to 23H2?
by
Dave Easley
21 hours, 18 minutes ago -
Limited account permission error related to Windows Update
by
gtd12345
3 days, 12 hours ago -
Another test post
by
gtd12345
3 days, 12 hours ago -
Connect to someone else computer
by
wadeer
3 days, 6 hours ago -
Limit on User names?
by
CWBillow
3 days, 10 hours ago -
Choose the right apps for traveling
by
Peter Deegan
2 days, 23 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.


