https://www.welivesecurity.com/2023/03/01/blacklotus-uefi-bootkit-myth-confirmed/
(The first in-the-wild UEFI bootkit bypassing UEFI Secure Boot on fully updated UEFI systems is now a reality. Bypassing Secure Boot, Microsoft Defender, VBS, BitLocker).
..In this blogpost we present the first public analysis of this UEFI bootkit, which is capable of running on even fully-up-to-date Windows 11 systems with UEFI Secure Boot enabled. Functionality of the bootkit and its individual features leads us to believe that we are dealing with a bootkit known as BlackLotus, the UEFI bootkit being sold on hacking forums for $5,000 since at least October 2022…
Following are the key points about BlackLotus and a timeline summarizing the series of events related to it:
It’s capable of running on the latest, fully patched Windows 11 systems with UEFI Secure Boot enabled.
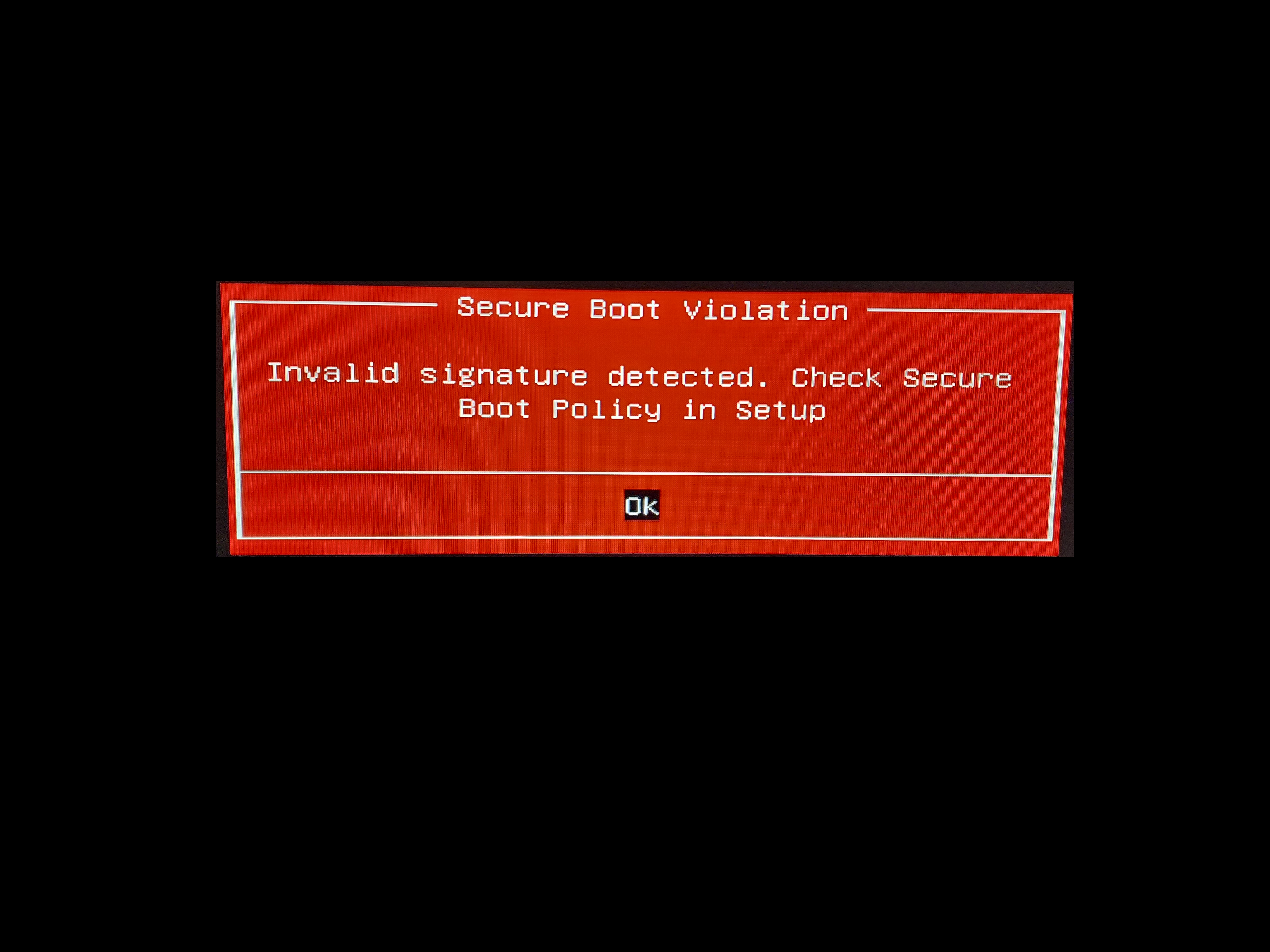
It exploits a more than one year old vulnerability (CVE-2022-21894) to bypass UEFI Secure Boot and set up persistence for the bootkit. This is the first publicly known, in-the-wild abuse of this vulnerability.
Although the vulnerability was fixed in Microsoft’s January 2022 update, its exploitation is still possible as the affected, validly signed binaries have still not been added to the UEFI revocation list. BlackLotus takes advantage of this, bringing its own copies of legitimate – but vulnerable – binaries to the system in order to exploit the vulnerability.
It’s capable of disabling OS security mechanisms such as BitLocker, HVCI, and Windows Defender.
Once installed, the bootkit’s main goal is to deploy a kernel driver (which, among other things, protects the bootkit from removal), and an HTTP downloader responsible for communication with the C&C and capable of loading additional user-mode or kernel-mode payloads.
BlackLotus has been advertised and sold on underground forums since at least October 6th, 2022. In this blogpost, we present evidence that the bootkit is real, and the advertisement is not merely a scam.
Interestingly, some of the BlackLotus installers we have analyzed do not proceed with bootkit installation if the compromised host uses one of the following locales:
Romanian (Moldova), ro-MD
Russian (Moldova), ru-MD
Russian (Russia), ru-RU
Ukrainian (Ukraine) , uk-UA
Belarusian (Belarus), be-BY
Armenian (Armenia), hy-AM
Kazakh (Kazakhstan), kk-KZ…