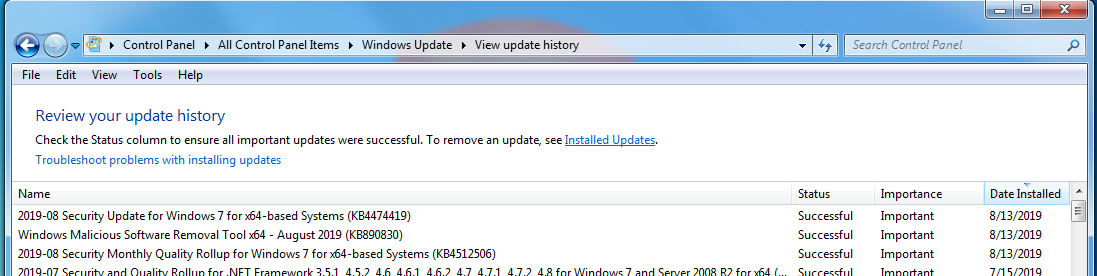
Looks like we’re getting 90 separate patches for 93 individually reported security holes (CVEs).
[See the full post at: August 2019 Security patches: It’s a biiiiiiiiig month]

|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
-
August 2019 Security patches: It’s a biiiiiiiiig month
Home » Forums » Newsletter and Homepage topics » August 2019 Security patches: It’s a biiiiiiiiig month
- This topic has 197 replies, 43 voices, and was last updated 5 years, 7 months ago.
AuthorTopicViewing 56 reply threadsAuthorReplies-
PKCano
ManagerAugust 13, 2019 at 12:31 pm #1907307The 2019-08 Security-only Update and IE11 Cumulative Update have been added to AKB2000003 for Group B patchers (and anyone else who needs them).
NOTE: The links in AKB2000003 are direct download links to the MS Update Catalog.
A reminder for those still on Windows 7 and/or Server 2008: SHA-2 Code Signing has become mandatory. You will also need to download KB4474419 (the SHA-2 v.2 update dated 8/12) and the Servicing Stack KB4490628 if it has not been previously installed.
Also be sure you have installed the Servicing Stack Update for Win 8.1 KB4504418
UPDATE: See #1907649 below UPDATE UPDATE
No, SO KB4512486 is telemetry-free
-
This reply was modified 5 years, 8 months ago by
PKCano.
-
This reply was modified 5 years, 8 months ago by
-
Matthew
AskWoody Plus -
PKCano
ManagerAugust 13, 2019 at 1:33 pm #1907328The MS pages for KB4474419 say the following:
-
This security update was released March 12, 2019 for Windows 7 SP1 and Windows Server 2008 R2 SP1.
-
This security update was updated May 14, 2019 to add support for Windows Server 2008 SP2.
-
This security update was updated June 11, 2019 for Windows Server 2008 SP2 to correct an issue with the SHA-2 support for MSI files.
-
This security update was updated August 13, 2019 to include the bootmgfw.efi file to avoid startup failures on IA64 versions Windows 7 SP1 and Windows Server 2008 R2 SP1.
If the latter point applies to your situation, you will definitely need to apply this patch.
UPDATE: MS pages also say:This update also includes the following improvements:
-
Further hardening of infrastructure files that are used by the Windows Update and Microsoft Update client.
-
A more secure communication channel between the service and the Windows Update and Microsoft Update client has been added.
So it would seem this patch should be installed for Win7 in general, not just IA46 based systems.
-
-
OscarCP
MemberAugust 13, 2019 at 4:33 pm #1907397Thanks for the advice. According to it, I better install this latest version of the SHA-2 patch. I have this question: Is there any particular urgency in installing it, or can this wait a few weeks, along with the rest of this month’s patches?
Windows 7 Pro, SP1, x64.
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV -
PKCano
Manager -
Tex265
AskWoody PlusAugust 13, 2019 at 5:01 pm #1907484Windows 7 Pro SP1 x64
Per PKCano comment above, what does IA64 based mean?
Back on April 2 I installed the March Security Update KB4489878, the SHA-2 KB4474419, and separately first installed the Service Stack KB4490628.
Windows Update is now showing me 2019-08 KB4474419 (again) and the MSRT, but not KB4512506 (the real August Security Update).
Do I have to install KB4474419 again before Windows Update will give me KB4512506?
If KB4474419 was previously updated in May then June, why was this not provided by Windows Update back then? And, should’nt we be installing now 2 months later?
Windows 10 Pro x64 v22H2 and Windows 7 Pro SP1 x64 (RIP) -
PKCano
Manager -
Matthew
AskWoody PlusAugust 13, 2019 at 5:16 pm #1907499From my simplistic understanding, most Windows users are on x64 (64-bit) or x86 (32-bit) architecture. The IA64 architecture is different, mainly meant for servers, and usually cannot run 32-bit applications (unlike x64 which usually can). Most of us running a desktop or laptop don’t have IA64.
-
Tex265
AskWoody PlusAugust 13, 2019 at 7:44 pm #1907586Windows Update is now showing me 2019-08 KB4474419 (again) and the MSRT, but not KB4512506 (the real August Security Update).
The IA64 architecture is different, mainly meant for servers, and usually cannot run 32-bit applications (unlike x64 which usually can). Most of us running a desktop or laptop don’t have IA64.
If true about IA64 and I have x64 – why am I receiving KB4474419 again as a Windows Update?
Windows 10 Pro x64 v22H2 and Windows 7 Pro SP1 x64 (RIP) -
PKCano
Manager -
abbodi86
AskWoody_MVP -
anonymous
GuestAugust 14, 2019 at 10:34 am #1907832
-
-
-
-
geekdom
AskWoody_MVPAugust 13, 2019 at 1:03 pm #1907316August Beta Test Report Windows 7 x64 Updates
Important
– Windows Malicious Software Removal Tool x64 – August 2019 (KB890830)
– August 2019 Security Monthly Quality Rollup Windows7 for x64 (KB4512506)
– August 2019 Security Update for Windows 7 for x64 (KB4474419)Optional
– Microsoft .NET Framework 4.8 for Windows 7 x64 (KB4503548)Selected the important updates.
– KB4512506 failed.
– KB890830 installed.
– KB4503548 installed.I rebooted and checked for updates.
Selected important and optional update.
– KB4512506 installed.
– KB4503548 installed.I rebooted. The system came up. The system automatically rebooted again.
Total time to install four updates was about 45 minutes with an initially failed update and a very slow download time.
The guinea pig did not die and the system functions. However, this was a cumbersome update process.
On permanent hiatus {with backup and coffee}
offline▸ Win10Pro 2004.19041.572 x64 i3-3220 RAM8GB HDD Firefox83.0b3 WindowsDefender
offline▸ Acer TravelMate P215-52 RAM8GB Win11Pro 22H2.22621.1265 x64 i5-10210U SSD Firefox106.0 MicrosoftDefender
online▸ Win11Pro 22H2.22621.1992 x64 i5-9400 RAM16GB HDD Firefox116.0b3 MicrosoftDefender-
geekdom
AskWoody_MVPAugust 13, 2019 at 6:42 pm #1907564Addendum and correction:
First pass, selected the important updates.
– KB4512506 failed.
– KB890830 installed.
-KB4474419 installed, not KB4503548.On permanent hiatus {with backup and coffee}
offline▸ Win10Pro 2004.19041.572 x64 i3-3220 RAM8GB HDD Firefox83.0b3 WindowsDefender
offline▸ Acer TravelMate P215-52 RAM8GB Win11Pro 22H2.22621.1265 x64 i5-10210U SSD Firefox106.0 MicrosoftDefender
online▸ Win11Pro 22H2.22621.1992 x64 i5-9400 RAM16GB HDD Firefox116.0b3 MicrosoftDefender-
This reply was modified 5 years, 8 months ago by
geekdom.
-
This reply was modified 5 years, 8 months ago by
anonymous
Guest-
Microfix
AskWoody MVP -
abbodi86
AskWoody_MVP -
woody
Manager -
GoneToPlaid
AskWoody LoungerAugust 14, 2019 at 10:38 pm #1908151I disabled the two telemetry things in Task Manager which were installed by the July SO update. After installing the August SO update, these two tasks remained disabled. The July SO update telemetry items in Task Manager are set to run infrequently. This suggests that these two tasks merely gather basic information about the computer, as in what updates and programs are installed. In other words, no “real time” data is constantly gathered, unlike when KB2952664 is installed.
A half rant, yet food for thought…
The upshot is that I think that users should install the July SO update and then simply disable the two tasks in Task Manager which gather some limited telemetry. I theorize that Microsoft simply wants to know why so many users refuse to upgrade to Windows 10. Is it because Windows 7 users are using older programs which will not run under Windows 10? Is is because many Windows 7 users are using much older hardware which may have issues with Windows 10? Is it because many Windows 7 users refuse to accept the telemetry which comes with Windows 10? Perhaps these are things which Microsoft wants to know.
On the other hand, and after the abysmal failure of Windows 8, Microsoft could have simply asked their consumers these very questions via online surveys. Microsoft has a penchant for belatedly realizing that they royally messed up in anticipating what consumers really wanted. It seems that it takes Microsoft at least a solid three years to begin to acknowledge that they didn’t get it right.
For the first time in Microsoft’s history, the Microsoft Windows branch (under Sinofsky and subsequently under Nadella), achieved the infamous milestone of releasing two OS versions in a row which were not well received. I wish that Balmer had been brought back to once again perform his magic and fix Windows 8, long before we ever got to this thing which is called Windows 10. The only company which I can think of which was equally inept is Chrysler.
Everyone, please do not respond to my half rant, since doing so would take this topic way off topic. If you want to respond, create your own rant in the appropriate rant section of the forum.
-
abbodi86
AskWoody_MVPAugust 15, 2019 at 3:39 am #1908183+1 for installing July SO
i think you mean Task Scheduler not Task Manager 🙂
1 user thanked author for this post.
-
SueW
AskWoody PlusAugust 15, 2019 at 7:21 pm #1908554@GoneToPlaid, thank you for providing your results regarding installing August’s SO!
Had you also taken a look at Event Viewer after installing either July’s SO [KB4507456] or August’s SO? Per post #1907151, anonymous posted what he/she found after installing July’s SO — that Event Viewer showed this warning message:
“A provider, InvProv, has been registered in the Windows Management Instrumentation namespace Root\cimv2 to use the LocalSystem account. This account is privileged and the provider may cause a security violation if it does not correctly impersonate user requests.”
I found these Warnings as well, right after installing July’s SO (as noted in the reply thread to anonymous). I’d be very interested in what your ‘take’ is, and if these Warnings can (or should) be deleted. Thanks!
Win 7 SP1 Home Premium 64-bit; Office 2010; Group B (SaS); Former 'Tech Weenie' -
GoneToPlaid
AskWoody LoungerAugust 30, 2019 at 1:33 pm #1926323I checked my Event Viewer logs. I too have the InvProv message with Event ID 63 which showed up after installing KB4507456. I did a bit of googling, and I see that installing KB2952664 also causes the same message in Event Viewer. Some versions of Office also cause the same message. I do not see signs that the July SO installed any deep telemetry like KB2952664 did.
1 user thanked author for this post.
-
anonymous
GuestAugust 17, 2019 at 10:36 am #1910246The very reason for Installing any Security Only Patches are for Patches that only contain Security Only functionality in said Security Only Patches and any Telemetry in them is non-excusable. By definition most folks doing that Security Only patching want to retain their Windows 7 installs without any Nagging or GWX sorts of Windows 10 foisting on MS’s part.
So I can live without any Security Only patches that are not really Security Only patches.
The folks using windows 7, or Windows 8.1(With TIFKAM go away third party software installed), are really and most definitely not wanting windows 10 and that loss of user control over privacy/system maintenance and the eventual OS as a subscription service business model that Windows 10 represents. Things after the 2020-2023 time frame will not be the same under Windows 10 and staying with 7/8.1(With TIFKAM hiding software) will give most of those users at least until 2023 to avoid that which will not be user friendly at a higher Recurring Cost going forward under Windows 10.
By 2023 I’ll expect that some Linux OS based laptop OEM will begin Offering new Linux OS based laptops with AMD’s Zen/Vega or Zen-2/Navi based APUs inside and then I can purchase new laptops that are outside of MS’s reach for the most part and Intel’s/Nvidia’s higher Markups/MSRPs as well as that relates to any PC/laptop total costs of ownership.
I do not want to be tied in to any more recurring monthly expenses other that the necessary ISP expenses. So my OS and related software/services will remain as low cost as possible under Linux/Open Source relative to Windows 10 and some unwelcome monetization expenses to come in the 2020-2023/later time frame.
-
-
-
abbodi86
AskWoody_MVP -
anonymous
GuestAugust 15, 2019 at 5:12 am #1908204? says:
thank you, GTP and abbodi86!
abbodi86, given the fact that security patching for Window’s 7 is scheduled to end soon do you think that skipping the July SO will really matter since the bulk of the file list for the patch seems to be updating the same well worn components and i’m going to relegate the win7 hdds to the closet with the the other Windows EOL versions next January? i do have the July SO patch on hand as well as your beautifully crafted remedy for the (unwarranted\unwanted) telemetry plumbing at the ready i just can’t bring myself to install it…
-
abbodi86
AskWoody_MVP
-
-
anonymous
GuestAugust 13, 2019 at 1:47 pm #1907333I am not being offered the Win 7 monthly rollup KB4512506 (I still see the 2019-07 Preview KB4507437).
I am assuming that this is due to the following:
Symptom:
Microsoft and Symantec have identified an issue that occurs when a device is running any Symantec or Norton antivirus program and installs updates for Windows that are signed with SHA-2 certificates only. The Windows updates are blocked or deleted by the antivirus program during installation, which may then cause Windows to stop working or fail to start.Workaround:
Microsoft has temporarily placed a safeguard hold on devices with an affected version of Symantec Antivirus or Norton Antivirus installed to prevent them from receiving this type of Windows update until a solution is available. We recommend that you do not manually install affected updates until a solution is available.I have Norton Security 22.18.0.213 installed on my Win 7 system.
Assume that there will be many others in the same situation.
-
PKCano
Manager -
OldBiddy
AskWoody LoungerAugust 13, 2019 at 9:11 pm #1907625 -
woody
ManagerAugust 14, 2019 at 7:54 am #1907762Symantec bought Norton in 1990.
Few people realize that Norton, prior to Symantec, was a PC utility company WITHOUT an antivirus product. Norton Antivirus is just a convenient use of a trusted name.
AFAIK, Peter’s still living on Martha’s Vineyard. He’s no longer on the board of Symantec. Rarely hear about him these days, except for his philanthropy.
-
jabeattyauditor
AskWoody LoungerAugust 14, 2019 at 8:05 am #1907764Broadcom bought the Enterprise Security products from Symantec a few days ago, making them once again owned separately from the Norton (home/personal) line. (The transaction will likely close before year-end.)
Broadcom intends to keep the Symantec nameplate in place for now.
1 user thanked author for this post.
-
OldBiddy
AskWoody Lounger
-
-
-
Tex265
AskWoody PlusAugust 13, 2019 at 8:02 pm #1907596I’m seeing the same thing as ? above with my Norton Security on Windows Pro SP1 x64.
Windows Update is now showing me 2019-08 KB4474419 (again) and the MSRT, but not KB4512506 (the real August Security Update).
Windows 10 Pro x64 v22H2 and Windows 7 Pro SP1 x64 (RIP)PKCano
ManagerAugust 14, 2019 at 4:34 am #1907722There is not urgency/need to install any of the August updates at this time. We are on DEFCON 2. WAIT!!
There is a conflict with Semantec/Norton EndPoint Protection and the updates signed with SHA-2 only. This affects both the Monthly Rollup and the Security-only Update. Until this is worked out, MS has a block in Windows Update on computers running this security software, so you will not see (and should not install manually) the August SQMR or SO.
anonymous
GuestAugust 13, 2019 at 1:49 pm #1907337? says;
peeked inside KB4512486 and did not see any telemetry
https://support.microsoft.com/en-in/help/4512486/windows-7-update-kb4512486
scroll down to “file information” and open it or save it…
now i’m wondering if i can apply it (later on) w\o breaking something\everything naving not applied the July SO?
-
anonymous
GuestAugust 14, 2019 at 3:22 am #1907659I recklessly installed KB4512486 and my Windows 7 laptop wound up reinstalling itself from scratch. Forgetting the full details of that patch including symptoms was rash on my part. I meant to get a new laptop considering my old one was on its metaphorical life support, but do hold off the update until Woody gives an “ok” on the Defcon.
ashfan212
AskWoody LoungerAugust 13, 2019 at 2:05 pm #1907346Windows 7 x64 Home Premium Group A, McAfee AV
I installed the SHA-2 update KB4474419 back in March. It appears that the August update to KB4474419 only applies to IA64 and not X64 based systems. Therefore, I am assuming that I will not need to reinstall this update.
What is unclear is whether I will even be offered this update. I would imagine that WU would only offer KB4474419 as an “exclusive” update. Therefore, if I am not offered the update, should I use the technique of hiding all of the other updates to see if KB4474419 appears as an “exclusive” update? Or is it preferable not to attempt to reinstall the update (even if replacing the March update version with the August update version does no harm) as the August update only applies to IA64 based systems according to the documentation?
-
PKCano
ManagerAugust 13, 2019 at 2:21 pm #1907356 -
ashfan212
AskWoody LoungerAugust 13, 2019 at 3:28 pm #1907375Hi PKCano,
I am not doubting your claim that KB4474419 is NOT exclusive; however, the documentation for KB4474419 indicates that installation of this update requires a reboot. Wouldn’t that mean that one should install this update by itself and then reboot before attempting to install any other offered updates? I would imagine that installing KB4474419 along with the August monthly rollup concurrently would cause the rollup installation to fail, even when KB4474419 is installed first by WU before attempting the installation of the August monthly rollup.
Perhaps this explains why the user Geekdom reported that the installation of the August monthly rollup KB4512506 failed to install on its first attempt, as that user indicated that KB4474419 was included in the set of updates that were received from WU.
As an aside, is there a convenient way to check whether an update is marked as exclusive?
-
This reply was modified 5 years, 8 months ago by
ashfan212.
-
This reply was modified 5 years, 8 months ago by
-
PKCano
ManagerAugust 13, 2019 at 3:44 pm #1907377KB4474419 is NOT exclusive. Many Win7 updates “require a reboot.”
I just installed, on my Win7 SP2, KB4512506 Rollup, KB4474419 SHA-2 v2, and KB890830 MSRT at the same time through Windows Update with no problems, no failures, no second reboot, no error messages. -
ashfan212
AskWoody LoungerAugust 13, 2019 at 4:10 pm #1907389 -
PKCano
ManagerAugust 13, 2019 at 5:32 pm #1907520Selected the important updates. – KB4512506 failed. – KB890830 installed. – KB4503548 installed.
KBKB4012215 is the installer for .NET 4.8 on Win7. It is not an update for the operating system. If I had to guess, I would suspect this for causing @geekdom ‘s problem. Just saying…
1 user thanked author for this post.
-
geekdom
AskWoody_MVPAugust 13, 2019 at 6:05 pm #1907550On the first pass, only the important updates were attempted.
On the second pass, the important update that failed and the optional update were installed.
On permanent hiatus {with backup and coffee}
offline▸ Win10Pro 2004.19041.572 x64 i3-3220 RAM8GB HDD Firefox83.0b3 WindowsDefender
offline▸ Acer TravelMate P215-52 RAM8GB Win11Pro 22H2.22621.1265 x64 i5-10210U SSD Firefox106.0 MicrosoftDefender
online▸ Win11Pro 22H2.22621.1992 x64 i5-9400 RAM16GB HDD Firefox116.0b3 MicrosoftDefender -
geekdom
AskWoody_MVPAugust 13, 2019 at 6:28 pm #1907561Reiterating:
First pass, selected the important updates.
– KB4512506 failed.
– KB890830 installed.
-KB4474419 installed.Optional
Second pass, selected important update that failed and optional update.
– KB4512506 installed.
– KB4503548 installed.There is an error in my beta test report. Could someone correct it?
On permanent hiatus {with backup and coffee}
offline▸ Win10Pro 2004.19041.572 x64 i3-3220 RAM8GB HDD Firefox83.0b3 WindowsDefender
offline▸ Acer TravelMate P215-52 RAM8GB Win11Pro 22H2.22621.1265 x64 i5-10210U SSD Firefox106.0 MicrosoftDefender
online▸ Win11Pro 22H2.22621.1992 x64 i5-9400 RAM16GB HDD Firefox116.0b3 MicrosoftDefender-
This reply was modified 5 years, 8 months ago by
geekdom.
-
This reply was modified 5 years, 8 months ago by
-
PKCano
Manager -
ashfan212
AskWoody LoungerAugust 13, 2019 at 6:05 pm #1907551Hi PKCano,
I had meant to say that KB4474419 is listed as a prerequisite to installing the August rollup KB4512506. That fact along with its required reboot caused me to inquire whether I should install KB4474419 separately prior to the installation of the August rollup. Anyway, that’s what I did and it seems to have worked. Thanks!
1 user thanked author for this post.
-
GoneToPlaid
AskWoody LoungerAugust 14, 2019 at 8:59 pm #1908096Maybe because you already had KB4474419 version 1 installed back in March? But yeah, it shouldn’t be exclusive as long as it is installed first, before other updates.
-
This reply was modified 5 years, 8 months ago by
GoneToPlaid. Reason: add more info
-
This reply was modified 5 years, 8 months ago by
-
-
-
GoneToPlaid
AskWoody LoungerAugust 13, 2019 at 4:17 pm #1907390Yes, install KB4474419 by itself and then reboot before installing any other updates.
2 users thanked author for this post.
-
anonymous
GuestAugust 13, 2019 at 2:15 pm #1907350According to Ghacks:
“Systems with Symantec or Norton software installed may block or delete Windows updates which causes Windows to stop working or fail to start. Upgrade block is in place. Symantec support article for the issue.”
But the Symantec support article says:
“Windows 7/Windows 2008 R2 updates that are only SHA-2 signed are not available with Symantec Endpoint Protection installed”
So no mention of Norton in the Symantec support article are they the same thing(Norton and Symantec Endpoint Protection).
I’m also waiting for any KB4512486(Aug 2019 Sec Only Update) telemetry vetting as well just because of what happened with the July 2019 Sec Only update for Windows 7.
-
woody
Manager -
anonymous
GuestAugust 14, 2019 at 2:19 pm #1907916But the Symantec support article says[Verbatim]:
“Windows 7/Windows 2008 R2 updates that are only SHA-2 signed are not available with Symantec Endpoint Protection installed”
And it’s the Press that’s Adding that Norton Branding so maybe that AKA needs to be clarified with Symantec. I’m running an ISP provided version of Norton Security Suite and there that Norton branding is on the product but in the quoted statement above on the Branding that is only “Symantec Endpoint Protection” so I assume that Symantec’s branding is correct. But clarification is certainly needed with the Press asking Symantec if that actually includes any products with that Norton name included in the product’s branding.
1 user thanked author for this post.
-
anonymous
GuestAugust 29, 2019 at 10:31 am #1925075I have a Windows 7 Asus laptop and was offered the August update. I went to the MS catalog and downloaded and installed the security only version. It bricked my laptop. On reboot, I looked and it was selecting and assigning partition drives or something and then went into the ASUS rescue procedure. Since it was going to erase my files and programs, I cancelled the operation, only to have the computer reboot and select partitions, etc. resulting in an endless loop of rebooting. After getting nowhere with Norton (I just kept getting transferred from one rep to another) for over 2.5 hours on the phone, I gave up. I pulled the drive from the laptop and hooked it to another computer, only to find that the laptop drive partitions were “unallocated”. How can I recover from this disaster? I’ve searched for answers but most say you need to get into a DOS prompt to fix. How? I cant even get past post. I’ve tried several different Windows 7 recovery disks and the laptop error says the Windows version is incompatible. I even tried an ASUS backup I had created (4 DVDs) and it appeared at first to be working, until the laptop rebooted again after the “recovery”. I’m not a technical guru…I need some help getting my system going again…or it the laptop now a brick?
-
Microfix
AskWoody MVP
-
-
-
Microfix
AskWoody MVPAugust 13, 2019 at 2:39 pm #1907358This kind of looks weird and out of place for Windows update KB4512508. Extract from: https://www.ghacks.net/2019/08/13/microsoft-windows-security-updates-august-2019-overview/
Fixed the MIT Kerberos realms issue that prevented devices from starting up or caused them to continue restarting.
Security updates to Windows App Platform and Frameworks, Windows Storage and Filesystems, Microsoft Scripting Engine, Windows Input and Composition, Windows Wireless Networking, Windows Cryptography, Windows Datacenter Networking, Windows Virtualization, Windows Storage and Filesystems, the Microsoft JET Database Engine, Windows Linux, Windows Kernel, Windows Server, Windows MSXML, Internet Explorer, and Microsoft Edge.my bolding never thought I’d see the day TBH
Windows - commercial by definition and now function...anonymous
GuestAugust 13, 2019 at 3:10 pm #1907371Possible new issue with August 2019 Updates on Win 7 Ultimate 32 bit.
Downloads & installs both the 2019-08 Secutity Monthly Quality Rollup… and 2019-08 Security Update for Windows 7… patches.
Reboots and starts to configure changes…. Then I get the following error:
“Failure Configuring Windows Updates, Reverting to” …blah blah blah
Reboots and reverts to previous patches. First time I ever got this error while updating.
Just to let y’all know…
-
PKCano
Manager -
anonymous
GuestAugust 13, 2019 at 4:20 pm #1907382Yo Boss,
Already had KB4490628 & KB4474419 patches before August 2019 updating. As I said, both August 2019 patches (KB3212646 & KB4012215) were downloaded & installed…BUT it fails when it reboots and tries to CONFIGURE them on the “Don’t turn off power” screen.
So there you have it…. BTW don’t have any Symantec s/w.
-
PKCano
ManagerAugust 13, 2019 at 4:39 pm #1907402Already had KB4490628 & KB4474419 patches before August 2019 updating. As I said, both August 2019 patches (KB3212646 & KB4012215) were downloaded & installed
KB3212646 is January 2017 Rollup
KB4012215 is March 2017 Rollup
These are not August 2019 patches. Are you trying to install these?
-
-
GoneToPlaid
AskWoody Lounger-
PKCano
Manager
anonymous
Guest-
PKCano
Manager -
anonymous
GuestAugust 13, 2019 at 4:44 pm #1907403? says: thank you PKC
this wasn’t up this a.m.:
-
EP
AskWoody_MVPSeptember 3, 2019 at 4:35 pm #1934620saw this post near the end of August:
https://blogs.windows.com/msedgedev/2019/08/30/update-removing-flash-microsoft-edge-internet-explorer/seems like MS plans to discontinue and eventually remove Flash for MS Edge & IE
1 user thanked author for this post.
-
woody
Manager
-
-
-
warrenrumak
AskWoody LoungerAugust 13, 2019 at 6:22 pm #1907559It’s a small thing, but it’s worth mentioning that the availability of .NET Framework 4.8 to versions of Windows prior to 1903 is going to be throttled over the coming weeks and months. Doing a “Check for Updates” will bypass the throttling, but otherwise it’s not going to show up right away for many people.
.NET 4.8 is already included with Windows 10 1903 so none of this applies there.
BTW, the main reason to install .NET 4.8 is that it improves startup time on a lot of .NET applications, in some cases by more than 20%.
Microfix
AskWoody MVPAugust 13, 2019 at 6:46 pm #1907565Windows 8.1 Pro x64 on HP Laptop
Installed SMQR KB4512488 via WU
System rebooted, allowed 10-15 mins to cease SSD activity.Scrutinised the following for any changes prior to re-connecting online:
Event Viewer
Task Scheduler
Performance Monitor/ Data Collector Sets/ Event Trace Sessions
Performance Monitor/ Data Collector Sets/ Startup Event Trace Sessions
GP settingsResults = no changes
Configuration Notes:
Diagtrack removed early 2018 and hasn’t returned.
MRT disabled from downloading.
uPNP disabled
Windows Defender Antivirus Security Intelligence Update 1.299.1918.0SFC /verifyonly displayed:
WU review of update history
So far so good on win8.1 🙂
EDIT: Also updated a Haswell Desktop and Ivybridge Laptop again no issues with either. device.
Windows - commercial by definition and now function...GoneToPlaid
AskWoody LoungerAugust 13, 2019 at 8:19 pm #1907607Windows 7 Group B computers. I am now fully patched through August. Note that there is a bug in the Windows Update manual installer. Once updates are installed and if you click the Restart button in the Windows Update window, your computer might hang when shutting down and while trying to close the Windows Update program. I first noticed this bug starting last month, and the results are bogus errors being recorded in Event Viewer. The errors state that the Windows Update(s) were not successfully installed, when in fact they were.
So until MS gets this bug fixed…
If you want to reboot after installing one or more Windows 7 updates, click Cancel when you are asked to reboot your computer. Doing so causes the Windows Update manual installer to close. Then reboot your computer by going to Start and then Restart. You might want to use this procedure for the time being, even when installing updates via Windows Update.
E Pericoloso Sporgersi
AskWoody LoungerAugust 13, 2019 at 11:17 pm #1907640JAP (*)
Remember me, the vanilla computer guy?
On my request Microsoft installed the August update for 1903 on Wednesday 14 August @ 01:30 UTC+2.Again I found no issue, not a single one.

How very boring!
* Just Another Patch.
1 Desktop Win 11
1 Laptop Win 10
Both tweaked to look, behave and feel like Windows 95
(except for the marine blue desktop, rgb(0, 3, 98)-
This reply was modified 5 years, 8 months ago by
E Pericoloso Sporgersi.
-
kiwisolutionz
AskWoody LoungerAugust 17, 2019 at 4:29 pm #1910727Exactly the same for one of my 3 LAPTOPS – W10 Pro_build: 18362_19h1_Release:190318.1202. My only error with the 1st 1903 update was that I forgot to disable Winaero for WUpdate, so it crashed on reboot because of my faux pas! So I disabled-repeated install to succeed, I must say folks; this is a stable build from the 1st days of W10’s arrival; what a nightmare that was. this version is just humming along without issues (touch Woody) thank you for all your work team, never thought i’d upgrade from W7 Ultimate 64bit. I have one more laptop to upgrade (my bizzo one), so until I save all my data near EOL – then finally move over to W10. If things turn to custard later…guess it’s gunna be Linux (!)
If there is magic on this earth ... it's in the water.
anonymous
GuestAugust 14, 2019 at 4:54 am #1907723Windows 7 Home Premium x64, Avast AV
First installed:
– KB890830
– KB4512506
– KB4474419System rebooted twice.
Then I installed KB4503548 and after that reboot I got the NET Language Pack offered, so I installed that one as well.
No problems and no telemetry re-enabled.
anonymous
Guestanonymous
GuestSeff
AskWoody PlusAugust 14, 2019 at 6:36 am #1907745According to Microsoft’s description, the current revision for KB4474419 includes “Further hardening of infrastructure files that are used by the Windows Update and Microsoft Update client”.
Is it just me being cynical, or does that wording sound suspiciously like another move towards “encouraging” Windows 7 users to upgrade to Windows 10?
Has anyone been able to establish what “further hardening of infrastructure files” actually means?
-
abbodi86
AskWoody_MVPAugust 14, 2019 at 7:04 am #1907756How’s that is an upgrade move? it’s actually a discouraging move (i.e. we are securing Windows Update)
by the way, the v2 release for x64 and x86 does not have any new files or changed ones, only the digital signature security categories are updated
-
Seff
AskWoody Plus
-
anonymous
GuestAugust 14, 2019 at 8:34 am #1907773WARNING!!!
looks like updates KB4512486 AND KB4512506 kills Windows 7 with nvme SSD drives. two out of ~100 pc’s won’t boot with these updates installed, and only these two has nvme SSD as boot drives.
tried to remove both and install separately – it’s enough one of these patches to kill Windows 7 machine.
2 users thanked author for this post.
-
woody
ManagerAugust 14, 2019 at 10:06 am #1907826Did you install the Monthly Rollup (KB 4512506) using Windows Update, or did you install it manually?
Can anyone else reproduce? I don’t see any confirmation online. Yet.
My Seven Semper Fi machine has spinning platters…..
-
slkj00
AskWoody PlusAugust 15, 2019 at 1:42 pm #1908433Looks like others are having problems with Win7 not booting after the update:
-
kiwisolutionz
AskWoody LoungerAugust 17, 2019 at 4:57 pm #1910738KB4512506 is not installed on my Crucial 250 SSD Drive,W7 Ultimate 64bit laptop (F-Secure AntiVirus) but: I found I have KB4474419 (The fix for kb4512506) installed; I cannot recall how this is so other than to say I may have spotted the advice on here earlier and just rolled with it at the time? The system is fine with no glitches that are noticeable at this point. hope this helps team, cheers all ; >)
If there is magic on this earth ... it's in the water.
-
PKCano
ManagerAugust 17, 2019 at 5:16 pm #1910740KB4474419 is the the patch for SHA-2 hashing. There have been two versions, the first v.1 was released 3/11 , and v.2 released on 8/12. SHA-2 has become mandatory for Windows Update beginning in August 2019. Win7 also requires Servicing Stack KB4490628.
The fix for KB4512506, which broke VB6, VBA and VBScript, is KB4517297, which was issued for Catalog download on 8/16.
-
anonymous
GuestAugust 21, 2019 at 9:07 am #1913668Boss, just so I’m clear, do we need to install KB4517297 from Microsoft Catalog before attempting to install KB4512506?
I am on WIN7x64 with latest versions of KB4474419 and KB4490628 already installed.
In either case, I’m holding off installing KB4512506 and KB4503548 as per current DEFCON-2. Thank you for all the support and expert advice you give people on askwoody.com
1 user thanked author for this post.
-
PKCano
ManagerAugust 21, 2019 at 9:06 am #1913695Boss, just so I’m clear, do we need to install KB4517297 from Microsoft Catalog before attempting to install KB4512506?
When you install KB4512506 it will break VB6, VBA and VBScript. If none of your programs are affected, you can stop there, b/c the fix will be in the Sept. Rollup. If you ARE affected, you can EITHER install KB4517297 (which is basically an SO with the fix) OR the 2019-08 Preview Rollup. I would recommend the former.
I’m holding off installing KB4512506 and KB4503548 as per current DEFCON-2
Good for you for waiting. When the time comes, I would recommend hiding KB4503548 (the installed for .NET 4.8 on Win7) for a while. If none of your programs require the latest version of .NET, it can wait for a while (several months, even).
Remember: We’re still on DEFCON 2
-
-
-
anonymous
GuestAugust 18, 2019 at 1:43 pm #1911415I have one machine too that got BSOD 0x0000007B INACCESSIBLE_BOOT_DEVICE after installing KB4512506, it uses a Samsung 960 EVO NVMe SSD.
I tried to use the latest Samsung NVMe driver instead of the Microsoft one bundled in KB2990941 but it did not help.
The fix described in KB2839011 for uninstalling a patch from the WinPE environment did work fine, as did restoring a previous recovery point.
What is strange is I have another workstation with a Samsung SM961 NVMe SSD that I held off to update until today when I could do a full backup but it went through without any issues!
-
anonymous
GuestAugust 24, 2019 at 10:47 am #1918113I have one machine too that got BSOD 0x0000007B INACCESSIBLE_BOOT_DEVICE after installing KB4512506, it uses a Samsung 960 EVO NVMe SSD.
I tried to use the latest Samsung NVMe driver instead of the Microsoft one bundled in KB2990941 but it did not help.
The fix described in KB2839011 for uninstalling a patch from the WinPE environment did work fine, as did restoring a previous recovery point.
What is strange is I have another workstation with a Samsung SM961 NVMe SSD that I held off to update until today when I could do a full backup but it went through without any issues!
I have realized the problem is not with NVMe SSD drives, it is with UEFI boot mode, which is a requirement for NVMe but can be used with any other drive as well.
Now I know why the second machine accepted the patch without issues: it had the “Win7 post SP1 rollup” patch KB3125574 applied.
Contained in this rollup is the recommended update KB3133977 for Bitlocker.
That patch is what works as a workaround for the problem: if you have it installed the system can then accept this months patch Tuesday patches: KB4512486 or KB4512506.
Microsoft has updated the patch notes for the latter with that info too, however they have done nothing to stop PC’s being bricked by the update still, as KB3133977 is still only listed as a recommended update!1 user thanked author for this post.
Tex265
AskWoody PlusAugust 14, 2019 at 9:30 am #1907802From Norton Community Forum:
Re: Is it safe to install August 2019 Windows 7 update??
Posted: 13-Aug-2019 | 3:56PM • Edited: 13-Aug-2019 | 3:59PM • PermalinkI’m running Norton Security v. 22.18.0.213 on Win 7 SP-1 Pro x64.
Windows Update informed me that KB4474419 was available. I installed it, and my computer works fine.
This update, however, is not the problem. The problem is apparently with KB4512506 — Monthly Rollup and KB4512486 — Security-only update. Even after installing KB4474419, MS Updates didn’t offer me either or the problematic ones.
The Symantic Enterprise KB article only indicates that the problem is with Enterprise Endpoint Solutions; it doesn’t mention any of the Norton products at all.
The answers provided to this Forum Thread are not at all clear except for this: “Defer the update until Norton has an official statement AND it clearly states a patch is available BEFORE attempting to install those updates at a later time.”
This should be in big red letters at the at the head of this Forum. I’m sure lots of Norton users around the world are wondering what’s going on with the August MS updates.
I’m wondering out loud how Norton intends to distribute its official statement and clearly state that a patch is available to address this specific issue.
And
As outlined in 2019 SHA-2 Code Signing Support requirement for Windows and WSUS, Microsoft will release an update to Windows 7 SP1 on August 13th, where the Microsoft Windows Updates are now SHA-2 signed instead of SHA-1 signed.
We have identified the potential for a negative interaction between Norton and the changes explained within the Microsoft KB. Symantec and Microsoft worked together to only allow the update to be visible to versions of Norton that offer full support for Windows 7 Updates that are solely SHA-2 signed.
We will release a Norton patch in the coming days to support the installation of updates that are only SHA-2 signed.
We don’t expect much impact. We can recommend that the customers click on ‘Always Allow’ when there is an alert, thereby allowing the Microsoft applications to function seamlessly.
We will be posting about this issue on the public forums, if we see large impact.
We already have an Enterprise KB article for this issue.Norton Forums Global Community Administrator | Symantec Corporation
EDIT to remove HTML. Please use the “Text” tab in the entry box when you copy/paste.
Windows 10 Pro x64 v22H2 and Windows 7 Pro SP1 x64 (RIP)1 user thanked author for this post.
-
kiwisolutionz
AskWoody LoungerAugust 17, 2019 at 5:28 pm #1910746
carpintero
AskWoody Lounger-
anonymous
GuestAugust 14, 2019 at 1:42 pm #1907885? says:
hi, carpintero i’m hoping to have one of the on-site scholars look at this. i read the project zero page on it and it seems fairly important:
https://googleprojectzero.blogspot.com/2019/08/down-rabbit-hole.html
from the demos it looks like it only takes seconds to obtain system control but hey, i’m no computer scientist!
1 user thanked author for this post.
WildBill
AskWoody PlusAugust 14, 2019 at 2:15 pm #1907915This isn’t “fake news” (quite), since the CVE-2019-1181 & CVE-2019-1182 vulnerabilities have been documented. Yet I haven’t see such an over-the-top media reaction since before Y2K. From CNN: https://www.cnn.com/2019/08/14/tech/windows-10-microsoft-security-update-trnd/index.html
Notice the headline: Microsoft urges Windows 10 users to update immediately
As Simon Pope said in the M$ blog post, there are a lot more Windows OS’s affected than just Win10. CNN states in the 1st paragraph: ‘Microsoft is warning Windows 10 users to update their operating system immediately because of two “critical” vulnerabilities.’ Again, it’s not just Win10. Here’s a CNN quote that is definitely #FakeNews:
‘There are “potentially hundreds of millions of vulnerable computers,” Simon Pope, Microsoft’s director of Incident Response, wrote in a blog post Tuesday.’ Search the blog post & you will NOT find the words “potentially hundreds of millions” blah, blah, etc. Sounds like one of CNN’s political reporters is moonlighting in the Business section… or it’s someone reminiscing about the Y2K panic. This final quote is not quite true:
“Other operating systems, such as Windows XP, are not affected.” WinXP isn’t, but see above, as well as the blog post. Could M$ have paid someone at CNN to start a panic among Win10 users & click “Check for updates”? Or was the Business reporter just bored?!
Bought a refurbished Windows 10 64-bit, currently updated to 22H2. Have broke the AC adapter cord going to the 8.1 machine, but before that, coaxed it into charging. Need to buy new adapter if wish to continue using it.
Wild Bill Rides Again...1 user thanked author for this post.
-
Susan Bradley
ManagerAugust 14, 2019 at 2:56 pm #1907946Gordon on Forbes is notoriously over the top. As you say there is a kernel of truth and then the rest is OMG the sky is falling the sky is falling!!!!!
Just like before you have to have RDP open and listening and most of us
- do not have it turned on or
- do not have it open directly to the web
Susan Bradley Patch Lady/Prudent patcher
-
Alex5723
AskWoody PlusAugust 15, 2019 at 2:38 pm #1908458someone reminiscing about the Y2K panic
What Y2K panic ? I worked for 2 months, many times for 36 hours with no sleep, updating banking software for Y2K, which was a real threat to our banking systems and clients.
Y2K was real.-
This reply was modified 5 years, 8 months ago by
Alex5723.
1 user thanked author for this post.
-
This reply was modified 5 years, 8 months ago by
-
WildBill
AskWoody PlusAugust 15, 2019 at 6:03 pm #1908524It was… for those started with less than a year to go. For those who took care of business in 1998 or earlier, the rest were panicking. BTW, I was with a company who verified software to make sure they were Y2K compliant with less than 60 days to go.
Bought a refurbished Windows 10 64-bit, currently updated to 22H2. Have broke the AC adapter cord going to the 8.1 machine, but before that, coaxed it into charging. Need to buy new adapter if wish to continue using it.
Wild Bill Rides Again...
-
rockandroller
AskWoody LoungerAugust 14, 2019 at 2:33 pm #1907922Well, I got burned – my 2008R2 primary domain controller would not boot after the updates yesterday. The other two 2008R2 servers here were not harmed by the updates. Our BDC is actually running 2008 standard, and it survived the updates unscathed (Well at least, it was able to boot afterwards…)
Shout-out to Veaam for saving my bacon once again ( rolled the PDC back to Sunday’s image)… now have to figure out ‘which patch was the killer..”
1 user thanked author for this post.
-
PKCano
Manager -
rockandroller
AskWoody LoungerAugust 14, 2019 at 2:57 pm #1907948The “crash-and-burn’ auto update was installing these three…
the MS ‘security intelligence’ ( AV definitions)
the 4512506 quality rollup
the 4474419 security patch
( in that order)
After restoring from image backup, I tried installing the AV defs – they went in fine. Then I tried installing just 4474419 BY ITSELF. And that has rebooted OK!!
Right now I am downloading the 4512506, with crossed fingers…
The server in question is a bone-stock 2008 R2 Standard, fully updated with all non-optional updates (to date!) just running DNS and DC role, and nothing else. We have a gateway appliance that provides DHCP…
PS: differences from our other 2008 R2 servers :
its a physical machine ( the others are Hyper-V VMs) – and it’s running the DC role ( the others are file server and DB servers, respectively… )
-
This reply was modified 5 years, 8 months ago by
rockandroller.
-
This reply was modified 5 years, 8 months ago by
rockandroller.
-
This reply was modified 5 years, 8 months ago by
-
NetDef
AskWoody_MVPAugust 14, 2019 at 3:09 pm #1907958Any chance that domain controller (the one that would not boot after KB4512506) was running Symantec AV?
I upgraded two SBS 2011 machines last night, both are in VM containers on a 2012 R2 Core host. Both took the August 2019 updates fine with no problems and no loss on their RDP Gateway service. Two separate companies/clients.
(Note, SBS 2011 runs Server 2008 R2 as their kernal.)
~ Group "Weekend" ~
-
-
rockandroller
AskWoody LoungerAugust 14, 2019 at 3:16 pm #1907964No symantec anything on our 2008R2 DC . Furthermore…
Just confirmed : KB4512506 IS THE KILLAH! Fails the reboot, after applying that patch.
This after the KB4474419 was successfully applied, and successfully rebooted.
Interestingly (or not) as it was “applying”, it got to 30% and then appeared to abruptly jump to the reboot stage (and subsequently failed).
ROLLING BACK to the previous backup… disabling the updates till they get this fixed
-
GoneToPlaid
AskWoody LoungerAugust 14, 2019 at 9:05 pm #1908099Yet was anything Symantec ever installed? I ask because some low level drivers might have been left behind when uninstalling any free trials which came with the computer. Long story, yet I believe that some AV manufacturers deliberately leave low level drivers behind in order to mess with the proper functionality of subsequently installed competing AV products. To get rid of any such remaining low level drivers, one has run download and run the AV manufacturer’s full removal tool.
1 user thanked author for this post.
anonymous
GuestAugust 14, 2019 at 3:48 pm #1907972I had an issue with a couple of 2008R2 Vm’s today failing when trying to install KB4512506, other patches installed fine.
Bit more digging and I noticed on the problem VM’s that KB4490628 (March Servicing stack update) was not installed on them. Installed that and tried installing KB4512506 again, installed fine, rebooted with no issues.
Don’t know if the above might help?
1 user thanked author for this post.
-
rockandroller
AskWoody Lounger
Geo
AskWoody Plus-
anonymous
GuestAugust 15, 2019 at 10:22 am #1908356Hello Geo, while I totally agree that not installing a .NET is a good idea, especially if you do NOT use any .Net for programs, I would ask you to investigate the Security Only (SO) .NETs offered.
Windows 7 comes with .NET 3.5.1. Whenever there is a SO for that offered it may be good to install it. It is up to you.
Again I say, if you do not need the higher numbered .NETs, then refuse them – unless you need them for a program you are using.
-
Geo
AskWoody Plus
-
ek
AskWoody LoungerAugust 14, 2019 at 4:33 pm #1907987CTF vulnerability (CVE-2019-1162) is scary.
What is vulnerable? Oh, just everything that contains text.
http://www.zdnet.com/article/vulnerability-in-microsoft-ctf-protocol-goes-back-to-windows-xp/Yes, catastrophically bad and profoundly dangerous.
I read Ormandy’s (project zero) blog post ( https://googleprojectzero.blogspot.com/2019/08/down-rabbit-hole.html ). I consider it priority reading for anyone concerned about Windows security. Advance warning: expect a lot of face-palming and hand-wringing while you read it.
The vulnerability is so bad – and seemingly so hopelessly entrenched throughout Windows – I don’t see how MS can ever truly fix it completely. Especially with their current ‘dev teams. It’s present in all versions of Windows from XP to Win 10. So it’s been there for 20 years and just now discovered. Ug!
-
anonymous
Guest -
ek
AskWoody LoungerAugust 15, 2019 at 12:08 am #1908157? says:
thank you, ek
did you see in the video’s and in the code how quickly and easily windows can be compromised? i have always disabled cftmon.exe from XP on up, so do you think that would slow down the cracking procedure?
Yes, I watched the video and shook my head in dismay. MS ignored re-designing CTF to make it secure for 20 years. I’m pretty sure at least some of their internals/kernel team knew about the mess. I’m speculating that big changes to CTF internals would be messy and likely break a lot of stuff, so they punted.
I don’t think disabling ctfmon will help. Anyone can craft their own executable that leverages the CTF “API”. This is one of those vulnerabilities that’s yet another great “tool” for malware and phishing.
-
anonymous
GuestAugust 15, 2019 at 4:10 am #1908188? says:
thank you ek for the explanation! so this “new,” Window’s vulnerability can be described as just another one of many “potential” attack avenues not (currently) being exploited? and the real and present danger is using Window’s updates or Windows at all?
1 user thanked author for this post.
-
-
anonymous
GuestAugust 14, 2019 at 4:48 pm #1907989Hi everyone,
Thanks for all the great feedback and advice over time. A priceless resource!!
I usually wait to install monthly security updates (and usually under Group B), but given the reported critical issues with the August update and recent issues I’ve had with security-only updates, I went ahead with the full roll-up.
As others mentioned, there seemed to be an issue with the installation and configuration. In contrast to what I usually do when an install “gets stuck” (shut down, reboot, uninstall, and try re-installing), I let this one go ahead without my intervention. After three automatic reboots (which made be nervous, for sure!) and configurations (the first two were stuck at 15% and 30% completed), the update and configuration finally went through smoothly.
It’s probably not how this update is supposed to run, but I thought I’d toss out my experience.
I also installed KB4474419 (which looks like a retread from March(?)) that consistently previously failed to install, and the .NET Framework update (KB4507240) before attempting the monthly (August) security update.
My system is Windows 7, 64-bit. Just a regular person 🙂
I will add to others’ frustration in having to go through this muckity-muck every month (and often more frequently) with MS–argh!!
Emily
1 user thanked author for this post.
EP
AskWoody_MVPAugust 14, 2019 at 6:54 pm #1908051hi woody.
check out these recent blogs from Born’s Tech & Windows World site:
https://borncity.com/win/2019/08/14/symantec-norton-blocks-windows-updates-sha-2/
noted about the problems with the Aug. 2019 Win7 updates and Symantec/Norton
https://borncity.com/win/2019/08/14/windows-updates-kb4512506-kb4512486-drops-error-0x80092004/
yup. either KB4512506 or KB4512486 fails to install or complete because the KB4490628 update was missing or not installed. really best for Win7 users to sit back and wait, which is what I’m currently doing; I won’t patch any of the few Win7 machines I have until things get sorted out for several days (but I have already installed both KB4474419 and KB4490628 updates way back in March 2019)
-
This reply was modified 5 years, 8 months ago by
EP.
-
geekdom
AskWoody_MVPAugust 14, 2019 at 7:02 pm #1908055The updates really aren’t playing nice this time.
Just wait to patch.
On permanent hiatus {with backup and coffee}
offline▸ Win10Pro 2004.19041.572 x64 i3-3220 RAM8GB HDD Firefox83.0b3 WindowsDefender
offline▸ Acer TravelMate P215-52 RAM8GB Win11Pro 22H2.22621.1265 x64 i5-10210U SSD Firefox106.0 MicrosoftDefender
online▸ Win11Pro 22H2.22621.1992 x64 i5-9400 RAM16GB HDD Firefox116.0b3 MicrosoftDefender-
This reply was modified 5 years, 8 months ago by
geekdom.
-
This reply was modified 5 years, 8 months ago by
tbsky
AskWoody LoungerAugust 14, 2019 at 9:03 pm #1908098KB4474419
now my wsus server has two KB4474419 updates. one from March (already approved and installed fine on testing environment). one from August. normally with same KB, the two updates should have revisions, and the latter revision will obsolete previous revision. but KB4474419 is special.
I don’t know how to deal with it. should I approve both March and August KB4474419? or I can just approved the August, abandon the March?
-
PKCano
ManagerAugust 15, 2019 at 6:12 am #1908229You should approve both.
The August KB4474419 v2 has changes from the March version.
But the MS pages for the August version say it does not replace the March version:Update replacement information
This update doesn’t replace a previously released update.
5 users thanked author for this post.
WSMRCS
AskWoody LoungerAugust 14, 2019 at 10:20 pm #1908147KB4512506 won’t install on Win7 x64
Apparently I am not the only one having this problem:
https://www.dslreports.com/forum/r32478603-Microsoft-August-2019-Security-UpdatesWhile it clearly says on the KB4512506 page that KB4474419 is a prerequisite, it’s also clear from the Update History that it tried to install KB4512506 first. Standalone installer wouldn’t work. Uninstalling and reinstalling KB4474419 didn’t help, either
rockandroller
AskWoody LoungerAugust 15, 2019 at 10:18 am #1908358In my case, the March 2019 servicing stack was already installed 🙁
This has been a real anomaly… I fell into the trap of complacency (always installing the ‘security patches’) since Windows updates have been mostly harmless for the last year or so. And I have only wasted all this time troubleshooting because the patch is marked “security” and these was all this hype about this latest critical vulnerability.
NINE HOURS of after-hours overtime wasted researching this issue and trying all the various patch application permutations, and I have restored our domain controller from its backup about five times now. To add insult to injury, the rather blasé word from ‘Microsoft Contingent Staff’ is that that so-called “security patch” can just be ignored until NEXT MONTH ( see https://social.technet.microsoft.com/Forums/windowsserver/en-US/c3feaf46-f5e5-4e78-a1b8-888eada3d6d6/patch-tuesday-08132019-windows-update-killed-our-2008r2-pdc-will-not-boot?forum=winservergen )
PKCano
ManagerAugust 15, 2019 at 12:27 pm #1908403I have installed August updates on these test machines:
+ 3 Win7 (one is 32-bit) KB4512596 SQMR, KB4474419 v2 SHA-2, and MSRT. (all had KB4474419 v1 SHA-2 and KB4490628 SSU previously installed)
+ 4 Win8.1 (one is 32-bit) KB4512488 SQMR and MSRT.I have used Windows Update on all, installing all patches at once. Have had no problems with any of them.
Notice: I am not installing KB4503548, the .NET 4.8 installer on any of my Win7/Win8.1 computers.
-
AJNorth
AskWoody Plus -
PKCano
ManagerAugust 15, 2019 at 1:19 pm #1908424In the past (history speaks on the side of caution) the initial release of a .NET version on Win7 (in particular) and Win8.1 has been problematic. Reference the initial version of .NET 4.7 on Win7 as an example. So, just like DEFCON says, I wait. That is the main reason.
Better safe than Microsofed.And, I don’t really have any need for it since I am not running programs that use/need .NET 4.8
-
abbodi86
AskWoody_MVPAugust 15, 2019 at 1:30 pm #1908428The newly published .NET 4.8 packages are actually refreshed with latest fixes (including security fixes from July)
for Win7, it’s handled via separate bundled patch KB4503575
for other systems, the MSU/CAB packages themselves are updated-
This reply was modified 5 years, 8 months ago by
abbodi86.
1 user thanked author for this post.
-
This reply was modified 5 years, 8 months ago by
-
EP
AskWoody_MVPAugust 15, 2019 at 5:55 pm #1908522for Win8.1, .NET 4.8 for 8.1 is KB4486105
https://www.catalog.update.microsoft.com/Search.aspx?q=4486105
also updated w/ July 2019 security fixes1 user thanked author for this post.
-
-
-
-
Microfix
AskWoody MVP
ek
AskWoody LoungerAugust 15, 2019 at 1:32 pm #1908430? says:
thank you ek for the explanation! so this “new,” Window’s vulnerability can be described as just another one of many “potential” attack avenues not (currently) being exploited? and the real and present danger is using Window’s updates or Windows at all?
Short answer to your 1st sentence: yes. But this vulnerability is very different than the processor side channel vulnerabilities like Spectre – which are (generally) computationally expensive to leverage (ie: complex and relatively slow). CTF is easy & fast to exploit to gain admin privs.
On your 2nd sentence: Well, if I made a statement like that I would be half serious.
I’ve been using Linux the majority of the time for years now.
I still run Windows 7 on some systems, but in doing so I follow these practices:
- MS updates are now often as risky as malware. So, I recently stopped patching. Prior to that, I always kept the systems up to date.
- The systems are behind a secure router with inbound/outbound rules set.
- I periodically inspect system activity (process, disk, network, etc.).
- I use a commercial Antivirus app and also do manual Defender scans.
- I use a local DNS server/filter and DNS services (like Quad9 and OpenDNS) to block risky/unwanted hosts/domains.
- The Windows systems never access the internet and especially: I avoid running a web browser of any sort on them. But if I absolutely have to, I use Firefox with a number of security/privacy addons (eg: noscript, privacy badger, UBlock, containers, etc.).
- I never store any sort of important documents on a Windows system anymore.
- The systems are never “always on”. I boot them when I need to use Windows and shut them down when done.
- Software/application wise: the systems are “frozen”. I don’t & won’t install any new Windows software (other than, maaaaybe, updates).
- I disable a number of unneeded Windows services and block telemetry.
So, yes, that’s a lot compromises & hoops to jump through just so I can (occasionally) use a a handful of Windows based apps I’m reluctant to abandon. Not sure how much longer I’ll be willing to put up with it.
4 users thanked author for this post.
-
anonymous
GuestAugust 15, 2019 at 2:01 pm #1908440? says:
again, many thanks ek for taking the time to reply and even more thanks for Woody, PKCano, abbodi86, and all the rest of the crew here for allowing me to vent my windows frustrations here and burn up precious airtime. all i really wanted to do is to finish out my windows 7 days in peace and then spin down quietly in January, but i know all to well that “you can’t always get what you want…”
1 user thanked author for this post.
VVet69
AskWoody PlusAugust 15, 2019 at 1:48 pm #1908437Also included in the August patches, specifically KB4512508, is a fix to a monstrous 20 year old security hole in Windows. There is a very good write up with a link to the research that uncovered the hole here: https://arstechnica.com/information-technology/2019/08/a-look-at-the-windows-10-exploit-google-zero-disclosed-this-week/
-
ek
AskWoody LoungerAugust 15, 2019 at 3:14 pm #1908468I’m doubtful that the fixes/mitigations in the update will plug all the CTF attack vectors. A few, maybe. All, unlikely.
CTF is just too entwined in the OS and probably requires a relatively long duration dev effort to re-engineer it (or rip it out) without breaking too much stuff. I don’t see this happening for Win 7 or 8/8.1. Win 10, maybe.
-
Geo
AskWoody PlusAugust 16, 2019 at 11:50 am #1908850Also included in the August patches, specifically KB4512508, is a fix to a monstrous 20 year old security hole in Windows. There is a very good write up with a link to the research that uncovered the hole here: https://arstechnica.com/information-technology/2019/08/a-look-at-the-windows-10-exploit-google-zero-disclosed-this-week/
Researcher details decades-old design flaws in Microsoft’s CTF protocol
tbsky
AskWoody LoungerAugust 16, 2019 at 9:26 am #1908802approved both March and August kb4474419. and do some testing:
1. client with March installed will install August just fine.
2. client without kb4474419 will be offered both and install both.
3. client with August installed can not install March and will not be offered March after reboot.
test both wsus and windows update online, the results are the same.
so it seems March kb4474419 should be abandoned. the relationship between March and August seems like revisions, like many telemetry hotfixes. but I don’t know why they co-exist.
-
PKCano
Manager -
GoneToPlaid
AskWoody LoungerAugust 16, 2019 at 10:08 am #1908816Thank you for performing this testing. Technically, the August V2 KB4474419 does supersede the March V1 KB4474419. I take it that after you installed the August V2, the attempt to install the March V1 resulted in a message that “This update is not applicable for your computer”? If so, that message clearly indicates that the V2 update has superseded the V1 update. This would not be the first time that Microsoft forgot to mention that a given update supersedes a previous update.
Supposedly the only change in the V2 update was to add a missing file to support Itanium processors. Without that file, computers with Itanium processors would black screen on bootup.
tbsky
AskWoody LoungerAugust 17, 2019 at 7:31 am #1910150Microsoft had many mistakes in wsus superseded relationships. many times I found wrong superseded patches. these kind of errors can be found easily when you compare the client scan result from wsus and on line update.
I didn’t try to find patches which should be superseded but not. they are hard to find. KB4474419 is very important or I think I won’t notice the duplicate.
but normally windows on line update is correct when wsus is wrong. the KB4474419 duplicate both at wsus and windows on line update. it is very strange to me.
-
This reply was modified 5 years, 8 months ago by
tbsky.
tbsky
AskWoody LoungerAugust 17, 2019 at 10:17 am #1910244kb4486153 (dotnet 4.8) is another strange thing.
we have windows 10 1809 LTSC. but kb4486153 for windows 1809 didn’t fit with LTSC. other hotfix for windows 1809 also fit 1809 LTSC, but not this one.
check https://www.catalog.update.microsoft.com/Search.aspx?q=kb4486153
I found Win10 1809 LTSC x64 share the same file with windows 2019. and there are another hotfix for 32bit 1809 LTSC.
so we have many kb4486153 for 1809:
for 2019 and 64bit 1809 ltsc (not in wsus)
for 32bit 1809 ltsc (not in wsus)
for normal 1809 64bit (in wsus)
for normal 1809 32bit (in wsus)
dot4.8 for win7/2008R2 just has 32bit/64bit version and share the same language pack.
I don’t understand what microsoft is doing with win10.
geekdom
AskWoody_MVPAugust 17, 2019 at 5:34 pm #1910747August 17, 2019—KB4512514 (Preview of Monthly Rollup)
https://support.microsoft.com/en-us/help/4512514/windows-7-update-kb4512514The above preview just showed in the Windows Update queue as an optional update.
On permanent hiatus {with backup and coffee}
offline▸ Win10Pro 2004.19041.572 x64 i3-3220 RAM8GB HDD Firefox83.0b3 WindowsDefender
offline▸ Acer TravelMate P215-52 RAM8GB Win11Pro 22H2.22621.1265 x64 i5-10210U SSD Firefox106.0 MicrosoftDefender
online▸ Win11Pro 22H2.22621.1992 x64 i5-9400 RAM16GB HDD Firefox116.0b3 MicrosoftDefender-
This reply was modified 5 years, 8 months ago by
geekdom.
2 users thanked author for this post.
-
WildBill
AskWoody PlusAugust 17, 2019 at 6:02 pm #1910772Here’s the Win8.1 version (also Optional):
2019-08 Preview of Monthly Quality Rollup for Windows 8.1 for x64-based Systems (KB4512478)
https://support.microsoft.com/en-us/help/4512478/windows-8-1-update-kb4512478
Bought a refurbished Windows 10 64-bit, currently updated to 22H2. Have broke the AC adapter cord going to the 8.1 machine, but before that, coaxed it into charging. Need to buy new adapter if wish to continue using it.
Wild Bill Rides Again...1 user thanked author for this post.
anonymous
GuestAugust 18, 2019 at 1:00 am #1911184Have several 64-bit Win 7 Pro machines that history shows successful installation of KB4512506 followed by KB4474419
Have at least 1 64-bit Win 7 Pro machine that was on automatic update, applying the 2 patches + KB890830, and upon reboot, not possible to boot -> Error 0xc000225 Black screen – unable to boot anything off hard drive (SATA SSD). Pulled the drive & ran chkdsk – everything OK. Unable to boot to HP recovery partition either.
Boots to HP recovery from USB, but unable to repair startup.
I had made a pure Microsoft Recovery CD -> bootable USB using Backup/Create System Restore Disk, and with this, I was able to UEFI boot the USB, and run startup repair successfully. Machine booted normally. Applied KB4474419/ reboot successfully. Then tried KB4512506, and again neutered the machine/ same Error 0xc0000225. But, again able to recover with pure MS Startup Repair (not the one in HP’s recovery image).
Seeing other reports of this from various sites
Windows Boot Manager Windows failed to start. A recent hardware or software change might be the cause. To fix the problem: 1. Insert your Windows installation disc and restart your computer. 2. Choose your language settings, and then click "Next". 3. Click "Repair your computer". If you do not have this disc, contact your system administrator or computer manufacturer for assistance. Status: 0xc0000225 Info: The boot selection failed because a required device is inaccessible. ======= Startup Repair - Name: System boot log diagnosis Result: Completed successfully. Error code = 0x0 Boot manager generic failure 0xc0000225 Root cause found: Boot manager failed to find OS loader. Repair action: File repair Result: Failed. Error code = 0xa Repair action: Boot configuration data store repair Result: Failed. Error code = 0x490 Repair action: System Restore Result: Completed successfully. Error code = 0x0
2 users thanked author for this post.
-
OscarCP
MemberAugust 18, 2019 at 1:17 am #1911195Anonymous: Do you know for sure, by now, which of the patches caused the problem? From your entry, it looks as it might have been KB4512506, the Monthly S&Q rollup. Anyone has heard of a problem with the Windows 7 Security Only patch?
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV -
anonymous
GuestAugust 18, 2019 at 4:24 am #1911211On window 7 machines with black screen of death after KB4512506 or the security only version of the patch I found removing all drives except c drive (operating system) drive and then booting up worked find. Then add the removed drives back and all should be ok if its what I ran into.
For some reason its scrambling the drive letters (identifiers) of the drives. Booting up with just the single drive straightens it out.
No clue why but it worked.
Crowz
3 users thanked author for this post.
-
gborn
AskWoody_MVPAugust 23, 2019 at 3:54 pm #1916994Concering boot error 0xc0000225 – it seems to me, that the SHA-2 thing is causing this error – Windows 7 can’t read the digital signature of files, after installing KB4512506.
So try to install the Bitlocker-Fix KB3133977, that also helps with Stop error 0xc0000428. I got confirmation from German readers that it helped.
But be careful an ASUS board, because this patch prevents a boot. The KB-article for KB3133977 contains more details.
Ex Microsoft Windows (Insider) MVP, Microsoft Answers Community Moderator, Blogger, Book author
https://www.borncity.com/win/
IT Manager Geek
AskWoody PlusAugust 18, 2019 at 6:05 am #1911220Morning all and after reading the commentary I certainly appreciate seeing your responses / questions. And what a ha ha, after Woody mention at the beginning of August that it should be a quiet month. As I say many times to my users, IT never sleeps.
Myself, will not wait till the end of the month as usual, and plan to start 2012 / 2016 Server updates next weekend. Though we’ll see what bugs come up between now and then before i finalize my decision.
A metaphor I’m telling my users who happen to catch the media’s reporting the “sky is falling, apply August patches NOW”, is as follows:
“Bluekeep and its siblings are like the boogie man, not sure if they exist now, so we’ll wait till Microsoft gets things figured out and then we’ll patch before Bluekeep turns into Godzilla.”.
This is the PG version, I have a non-PG version for those that appreciate the spice.
Take care,
IT Manager Geek
2 users thanked author for this post.
geekdom
AskWoody_MVPAugust 18, 2019 at 8:36 am #1911341Could there be a summary of all errors or borks to date?
On permanent hiatus {with backup and coffee}
offline▸ Win10Pro 2004.19041.572 x64 i3-3220 RAM8GB HDD Firefox83.0b3 WindowsDefender
offline▸ Acer TravelMate P215-52 RAM8GB Win11Pro 22H2.22621.1265 x64 i5-10210U SSD Firefox106.0 MicrosoftDefender
online▸ Win11Pro 22H2.22621.1992 x64 i5-9400 RAM16GB HDD Firefox116.0b3 MicrosoftDefender-
woody
Manager
anonymous
GuestAugust 18, 2019 at 5:07 pm #1911479Win 7 Pro X64 machine with Black Screen of Death – re-tried the August security only update – can’t boot – then tried the suggestion above of removing all but C: drive (machine in question had 2 drives, both SATA SSDs) – did not help.
Have another almost identical machine, except it has even more hard drives, including nvme, and SATA SSDs, where the Aug update worked – but this machine is multi-boot, first boot device being Linux, with a default to Windows 10 and Windows 10’s default is Windows 7…
abbodi86
AskWoody_MVPAugust 18, 2019 at 9:46 pm #1911536The 2019 SHA-2 Code Signing Support requirement for Windows and WSUS article is updated with more info for Windows 7
while it’s not listed as prerequisite, but the FAQ section now suggest to include update KB3133977 for new installations of Windows 7
those who have failed installations for already running Windows 7 OS can try the suggestion, particulary the last one (i.e. install KB3133977, reboot, run bcdboot.exe)
-
anonymous
GuestAugust 18, 2019 at 10:50 pm #1911549 -
abbodi86
AskWoody_MVP -
EP
AskWoody_MVP -
anonymous
Guest -
PKCano
ManagerAugust 26, 2019 at 9:04 am #1920739KB3125574 is a convenience Rollup meant for quick updaating from a clean install instead of having to install a lot of individual updates.
All you need at this point is the individual patch KB3133977 which was one of the updates contained in KB3125574.1 user thanked author for this post.
-
anonymous
Guest
-
-
-
geekdom
AskWoody_MVPAugust 20, 2019 at 12:10 pm #1913246This optional update just appeared in the Windows Update queue:
Preview of Quality Rollup for .NET Framework 3.5.1, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2, 4.8 for Windows 7 SP1 and Windows Server 2008 R2 SP1 (KB4512193)
https://support.microsoft.com/en-us/help/4512193/august-20-2019-kb4512193On permanent hiatus {with backup and coffee}
offline▸ Win10Pro 2004.19041.572 x64 i3-3220 RAM8GB HDD Firefox83.0b3 WindowsDefender
offline▸ Acer TravelMate P215-52 RAM8GB Win11Pro 22H2.22621.1265 x64 i5-10210U SSD Firefox106.0 MicrosoftDefender
online▸ Win11Pro 22H2.22621.1992 x64 i5-9400 RAM16GB HDD Firefox116.0b3 MicrosoftDefender1 user thanked author for this post.
-
WildBill
AskWoody PlusAugust 20, 2019 at 2:26 pm #1913314Here’s the Win8.1 version that appeared in my Windows Update queue:
Preview of Quality Rollup for .NET Framework 3.5, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2, 4.8 for Windows 8.1, RT 8.1, and Windows Server 2012 R2 (KB4512195) https://support.microsoft.com/en-us/help/4512195/august-20-2019-kb4512195
Capt. Obvious passes on that this is a Preview, and Optional at that. Easy to skip…Bought a refurbished Windows 10 64-bit, currently updated to 22H2. Have broke the AC adapter cord going to the 8.1 machine, but before that, coaxed it into charging. Need to buy new adapter if wish to continue using it.
Wild Bill Rides Again...-
This reply was modified 5 years, 8 months ago by
WildBill. Reason: Remove HTML
-
This reply was modified 5 years, 8 months ago by
rockandroller
AskWoody LoungerAugust 20, 2019 at 1:40 pm #1913293zero2dash
AskWoody LoungerAugust 20, 2019 at 3:31 pm #1913338-
EP
AskWoody_MVPAugust 20, 2019 at 5:27 pm #1913374no issues on 1903 with the Aug 2019 patches for you, zero2dash (not even encountering any VBA/VB6/VBScript problems?)
I’m skipping the KB4512508 update for 1903 – I won’t install that patch on my friend’s PC running Win10 pro v1903 and will wait for the next update coming near the end of August that should fix some of the issues found with KB4512508.
-
This reply was modified 5 years, 8 months ago by
EP.
1 user thanked author for this post.
-
This reply was modified 5 years, 8 months ago by
-
zero2dash
AskWoody Lounger
-
fpefpe
AskWoody Plusanonymous
Guest-
PKCano
Manager
anonymous
Guestrockandroller
AskWoody LoungerAugust 21, 2019 at 10:09 am #1913803Microsoft Technet forum moderator has posted this:
Hi,
It is confirmed as a known issue of Aug updates. If you skipped install the 2019 7B updates prior to installing 2019 8B updates OR fresh installed Win7 / W2K8 R2 then directly installed 2019 8B, the issue could be caused.
The current resolution is to uninstall those updates and keep them uninstalled until the next action plan.
If there is any update on this issue, I will post here ASAP.
Thanks for your understanding.
Best regards,
Yilia
anonymous
GuestAugust 21, 2019 at 4:38 pm #1914102I did some testing last night for my organization. I had a Server 2008 r2 VM go into a recovery mode I can’t get it out of after installing the August patches and rebooting. It boots directly into the recovery mode. Luckily, it’s not a server we use, so no big deal. I’m not going to waste time trying to fix it. I’m going to try to delay these as long as possible.
geekdom
AskWoody_MVPAugust 22, 2019 at 1:46 pm #1915139Are Patch Tuesday updates tested prior to release on systems that have installed third-party software?
On permanent hiatus {with backup and coffee}
offline▸ Win10Pro 2004.19041.572 x64 i3-3220 RAM8GB HDD Firefox83.0b3 WindowsDefender
offline▸ Acer TravelMate P215-52 RAM8GB Win11Pro 22H2.22621.1265 x64 i5-10210U SSD Firefox106.0 MicrosoftDefender
online▸ Win11Pro 22H2.22621.1992 x64 i5-9400 RAM16GB HDD Firefox116.0b3 MicrosoftDefender-
Alex5723
AskWoody PlusAugust 22, 2019 at 1:57 pm #1915158Are Patch Tuesday updates tested prior to release on systems that have installed third-party software?
There is no QA team at Microsoft any more, so no tests are done, and judging from the last 4 years no data is shared with 3rd party hardware and software vendors either.
-
geekdom
AskWoody_MVPAugust 23, 2019 at 9:13 am #1916677Two interesting Microsoft statistics would be:
– testing performed in-house on software modifications and patches.
– turnover rate of Microsoft employees assigned to software testing.On permanent hiatus {with backup and coffee}
offline▸ Win10Pro 2004.19041.572 x64 i3-3220 RAM8GB HDD Firefox83.0b3 WindowsDefender
offline▸ Acer TravelMate P215-52 RAM8GB Win11Pro 22H2.22621.1265 x64 i5-10210U SSD Firefox106.0 MicrosoftDefender
online▸ Win11Pro 22H2.22621.1992 x64 i5-9400 RAM16GB HDD Firefox116.0b3 MicrosoftDefender-
This reply was modified 5 years, 8 months ago by
geekdom.
1 user thanked author for this post.
-
This reply was modified 5 years, 8 months ago by
-
Razz
AskWoody PlusAugust 23, 2019 at 1:12 pm #1916891Are Patch Tuesday updates tested prior to release on systems that have installed third-party software?
There is no QA team at Microsoft any more, so no tests are done, and judging from the last 4 years no data is shared with 3rd party hardware and software vendors either.
Just out of interest how do you know that Microsoft don’t have a QA team?
Sounds absurd, although nothing would surprise me.
ASUS GL702VS 24GB RAM Intel Core i7 64 bit Win 10 Home 22H2 OS Build 19045.3693
Windows Feature Experience Pack 1000.19053.1000.0
Not Win 11 eligible. -
Alex5723
AskWoody PlusAugust 23, 2019 at 1:42 pm #1916909Are Patch Tuesday updates tested prior to release on systems that have installed third-party software?
There is no QA team at Microsoft any more, so no tests are done, and judging from the last 4 years no data is shared with 3rd party hardware and software vendors either.
Just out of interest how do you know that Microsoft don’t have a QA team?
Sounds absurd, although nothing would surprise me.
Microsoft fired it’s QA team in 2015.
Microsoft claims 10 million ‘fans’ help it test Windows 10, but it’s sure got a funny definition of that word
And since Microsoft fired a significant percentage of the QA team that used to be responsible for finding and fixing these bugs, it’s not catching them internally the way it used to.
-
samak
AskWoody Plus
-
-
-
Razz
AskWoody PlusAugust 23, 2019 at 9:28 am #1916682Thanks for the post on this topic. I have noticed that
2019-08 Security Monthly Quality Rollup for Windows 7 for x64-based Systems (KB4512506)
keeps popping up as an important update in this latest batch, and while it has now been uploaded successfully 8 times it is still there for upload.
Today the McAfee Vulnerability scanner is highlighting it as an issue now too.
Any idea what is going on with this and how to rectify?
Thanks
ASUS GL702VS 24GB RAM Intel Core i7 64 bit Win 10 Home 22H2 OS Build 19045.3693
Windows Feature Experience Pack 1000.19053.1000.0
Not Win 11 eligible.1 user thanked author for this post.
-
PKCano
Manager -
Razz
AskWoody PlusAugust 23, 2019 at 10:42 am #1916796Thanks for your reply. My Update history has *628 successfully installed 8/14, and *419 successfully installed 8/18 after multiple failed attempts 8/17 & 8/15.
*506 was successfully installed before *419, if that has any relevance.
screen shot attached for ref.
ASUS GL702VS 24GB RAM Intel Core i7 64 bit Win 10 Home 22H2 OS Build 19045.3693
Windows Feature Experience Pack 1000.19053.1000.0
Not Win 11 eligible.
-
anonymous
Guest-
geekdom
AskWoody_MVPAugust 24, 2019 at 8:22 am #1918001We are at MS-DEFCON 2 (posted at the top) and it is not yet safer to patch. Reports are still coming in — and most describe difficulties in either installation or system operations.
When MS-DEFCON 3 is posted, it will be advisable to patch with caution.
MS-DEFCON System is here:
https://www.askwoody.com/ms-defcon-system/On permanent hiatus {with backup and coffee}
offline▸ Win10Pro 2004.19041.572 x64 i3-3220 RAM8GB HDD Firefox83.0b3 WindowsDefender
offline▸ Acer TravelMate P215-52 RAM8GB Win11Pro 22H2.22621.1265 x64 i5-10210U SSD Firefox106.0 MicrosoftDefender
online▸ Win11Pro 22H2.22621.1992 x64 i5-9400 RAM16GB HDD Firefox116.0b3 MicrosoftDefender -
WildBill
AskWoody PlusAugust 24, 2019 at 10:44 am #1918123As @geekdom & many others attest, there’s a reason Woody developed the MS-DEFCON system. When it’s at 1 or 2, you’re risking a Lot of Pains in the Butt by patching early. 3 & above, it becomes safer… at least slightly. Patient Patching is a Virtue…
Bought a refurbished Windows 10 64-bit, currently updated to 22H2. Have broke the AC adapter cord going to the 8.1 machine, but before that, coaxed it into charging. Need to buy new adapter if wish to continue using it.
Wild Bill Rides Again... -
Charlie
AskWoody Plus
-
GeoffB
AskWoody PlusSeptember 2, 2019 at 1:05 am #1931804I have a simple question about the August patches. I am Win 7 x64 Group A.
I realise we are at DEFCON 2 and I don’t intend to patch until the rating is relaxed to DEFCON 3 or better. I installed the March version of KB 4474419 back in April and I note there is now an updated August version of this patch. Do I have to uninstall the March version of KB 4474419 prior to downloading/installing the updated August version?
Appreciate your advice on this.
regards
GeoffB
-
anonymous
GuestSeptember 2, 2019 at 1:53 am #1931847? says;
short answer, don’t uninstall the March version and then install the august version.
long answer:
scroll down to “Current Status,” quote #2.
#1 and #3 speak to the other required components (KB4490628) and (KB3133977)
1 user thanked author for this post.
-
EP
AskWoody_MVP
-
LHiggins
AskWoody PlusSeptember 7, 2019 at 7:52 am #1941273Question – a bit late though…
I am just now preparing my Win 7 computers for the Defcon 3 updates, and I find that I don’t seem to have KB3133977 on one of them. Should I go ahead and download that separately before any others? No idea why I don’t have it – I have 5 others within that March 2016 timeframe, but not that one. Also – no KB3125574.
I also wondered about this post which seems to indicate that on older computers – mine is about 10 years old now – that KB3133977 isn’t needed: https://www.askwoody.com/forums/topic/ms-defcon-3-time-to-get-the-august-2019-patches-installed/#post-1941268
Perhaps that is why I don’t have it?
Thanks for the clarification.
-
PKCano
Manager -
LHiggins
AskWoody PlusSeptember 7, 2019 at 8:51 am #1941309Thanks! So I guess it is better to install it to be on the safe side.
So – would I download it from here: https://support.microsoft.com/en-us/help/3133977/bitlocker-can-t-encrypt-drives-because-of-service-crashes-in-svchost-e
Will look into it later when this old computer is done with its latest backup – just in case!
Thanks!
-
Marvel Wars
AskWoody PlusSeptember 8, 2019 at 3:18 am #1942985-
PKCano
ManagerSeptember 8, 2019 at 4:41 am #1943068If you have an ASUS motherboard, you should read this first.
Otherwise, you are correct. Install 3133977, then Windows Update will install the others correctly.
-
Marvel Wars
AskWoody PlusSeptember 8, 2019 at 5:01 am #1943088My pc is very old, I don’t have an UEFI BIOS.
-
This reply was modified 5 years, 7 months ago by
Marvel Wars.
-
This reply was modified 5 years, 7 months ago by
-
Marvel Wars
AskWoody Plus -
PKCano
Manager -
Marvel Wars
AskWoody Plus -
PKCano
Manager -
Marvel Wars
AskWoody PlusSeptember 9, 2019 at 9:49 am #1945011I don’t understand, I clicked on the link.
There is a question from a Charlie and a Sinclair. They both have an asus motherboard but not an UEFI Bios.
Then there is an answer from you saying that for those who have an Asus motherboard they “Either
Make the modification in the BIOS so you can install KB3133977
OR
Not install KB3133977 and just install the August patch.
OR
Do not install either patch and wait for further instructions.”You don’t really talk about the EFI/UEFI Bios in your answer so since I don’t know how to make the modification in the BIOS I decided I would just install the august patch without the KB3133977.
I’m really sorry, is there something else that I should understand from this ?
-
PKCano
ManagerSeptember 9, 2019 at 10:09 am #1945030If you have an ASUS motherboard, you should read this first.
Otherwise, you are correct. Install 3133977, then Windows Update will install the others correctly.
-
anonymous
Guest -
PKCano
Manager -
Marvel Wars
AskWoody Plus
-
-
-
Aaron Corey
AskWoody LoungerSeptember 16, 2019 at 7:40 am #1952441After installing the August rollup (KB4512488) on Windows 8.1 64-bit, I’ve been noticing some odd USB device detection issues. Nothing catastrophic, but still annoying. For example:
My computer’s built-in memory card reader keeps getting re-detected after my computer has been running for awhile (30-60 minutes) resulting in the “device setup” dialog being displayed. The device setup dialog progress bar freezes and the dialog doesn’t go away unless I close it manually. The card reader still seems to work in spite of this, so it’s mainly a nuisance. It’s not unusual for my card reader to be re-detected occasionally (once every few boots), but this normally happens right after I log in, and the device setup dialog normally goes away quickly.
Sometimes USB thumb drives experience a similar issue, where the “device setup” progress bar seems to stop and the dialog stays there until I manually close it. Sometimes the device name shown on the device setup dialog doesn’t match the actual device, while other times the name does match. Thumb drives and external hard drives still seemed to work fine otherwise (I could transfer files to them via explorer).
At one point, some of my USB thumb drives would not display the the eject option when I clicked the Safely Remove Hardware icon in the notification area. It seemed to be device specific (i.e. some of my thumb drives would have the eject option while others would not, even though they the same brand). The name of the device and drive letter would be there, but without the eject option. The thumb drives still seemed to work fine otherwise. After I restarted the computer, this issue seemed to go away (for now).
Is anyone else seeing issues like this?
-
Aaron Corey
AskWoody LoungerSeptember 16, 2019 at 7:40 am #1952456My work PC also seems to be having the second issue described above – when I plug in a thumb drive, I get the device setup dialog, the progress bar stops and the dialog just stays there. The device setup dialog also seems to have a delayed reaction – instead of appearing as when the device is first plugged in, it appears a few minutes later.
This PC is also running Windows 8.1 64-bit. Instead of KB4512488, it has the preview of that update (KB4507463) that was released on July 16. I’m not sure why IT pushed the preview from July instead of the August rollup (considering they pushed it on August 23). On my home PC I don’t install the previews.
-
This reply was modified 5 years, 7 months ago by
Aaron Corey.
-
This reply was modified 5 years, 7 months ago by
-
anonymous
GuestSeptember 16, 2019 at 8:50 am #1952520I installed the August rollup (KB4512488) on Windows 8.1 64-bit on 09 September.
I have not seen the behaviour you describe. My SanDisk memory sticks are working just fine.
My Event Viewer shows this for 09 September:
Warning 123 Device Setup Manager
The DSM service was delayed by 96 seconds for a driver query/download/install on device ‘SWD\DAFUPNPPROVIDER\UUID:91A84487-ED43-403D-AAFB-10668407CF26’
But I have not seen that message since.
-
Aaron Corey
AskWoody LoungerSeptember 16, 2019 at 10:19 am #1952618I’ve been doing a bit more digging on this, and the installation of these update may be just a coincidence. I’m seeing 2 instances event #131 “metadata staging failed” on my work PC, both of which occurred this month. That event code jogged my memory, because I remember investigating a similar outbreak of those events that occurred several years ago. At the time, other people were also encountering these events, and most were blaming it on Microsoft’s metadata servers being mis-configured or malfunctioning. From what I gather, the metadata in question is mainly used in the “Devices and Printers” control panel applet to display unique device icons and other device-specific information. The last time this happened, Microsoft eventually fixed the issue on their server and the event 131’s stopped happening. So if my theory is correct, the hung “device setup” dialogs are just Windows attempting (and failing) to get that device metadata from Microsoft’s server. I’ll do some more digging on my home PC this evening to see if it’s having the same event 131 issues.
-
Viewing 56 reply threads -

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
CISA warns of increased breach risks following Oracle Cloud leak
by
Nibbled To Death By Ducks
1 hour, 14 minutes ago -
Outlook 2024 two sent from email addresses
by
Kathy Stevens
5 hours, 17 minutes ago -
Speeding up 11’s search
by
Susan Bradley
12 hours, 30 minutes ago -
HP Pavilion Will Not Wake Up After Being Idle for Longer Period
by
WSwalterwood44
11 hours, 49 minutes ago -
Make a Windows 11 Local Account Passwordless
by
Drcard:))
15 hours, 15 minutes ago -
Ubuntu 25.04 (Plucky Puffin)
by
Alex5723
22 hours, 49 minutes ago -
24H2 fixed??
by
CWBillow
12 hours, 18 minutes ago -
Uninstalr Updates
by
jv16
1 day, 3 hours ago -
Apple zero days for April
by
Susan Bradley
8 hours, 39 minutes ago -
CVE program gets last-minute funding from CISA – and maybe a new home
by
Nibbled To Death By Ducks
1 hour, 32 minutes ago -
Whistleblower describes DOGE IT dept rumpus at America’s labor watchdog
by
Nibbled To Death By Ducks
2 days, 2 hours ago -
Seeing BSOD’s on 24H2?
by
Susan Bradley
1 day, 9 hours ago -
TUT For Private Llama LLM, Local Installation and Isolated from the Internet.
by
bbearren
1 day, 17 hours ago -
Upgrade from Windows 10 to 11
by
Holdsworth8
2 days, 11 hours ago -
Microsoft : AI-powered deception: Emerging fraud threats and countermeasures
by
Alex5723
2 days, 14 hours ago -
0patch
by
WSjcgc50
1 day, 15 hours ago -
Devices might encounter blue screen exception with the recent Windows updates
by
Susan Bradley
2 days, 7 hours ago -
Windows 11 Insider Preview Build 22631.5261 (23H2) released to Release Preview
by
joep517
2 days, 17 hours ago -
Problem opening image attachments
by
RobertG
2 days, 18 hours ago -
advice for setting up a new windows computer
by
routtco1001
3 days, 9 hours ago -
It’s Identity Theft Day!
by
Susan Bradley
11 hours, 9 minutes ago -
Android 15 require minimum 32GB of storage
by
Alex5723
3 days, 14 hours ago -
Mac Mini 2018, iPhone 6s 2015 Are Now Vintage
by
Alex5723
3 days, 14 hours ago -
Hertz says hackers stole customer credit card and driver’s license data
by
Alex5723
3 days, 15 hours ago -
Firefox became sluggish
by
Rick Corbett
1 day, 7 hours ago -
Windows 10 Build 19045.5794 (22H2) to Release Preview Channel
by
joep517
3 days, 18 hours ago -
Windows 11 Insider Preview Build 22635.5235 (23H2) released to BETA
by
joep517
3 days, 19 hours ago -
A Funny Thing Happened on the Way to the Forum
by
bbearren
2 days, 16 hours ago -
Download speeds only 0.3Mbps after 24H2 upgrade on WiFi and Ethernet
by
John
3 hours, 22 minutes ago -
T-Mobile 5G Wireless Internet
by
WSmmi16
2 days, 17 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.