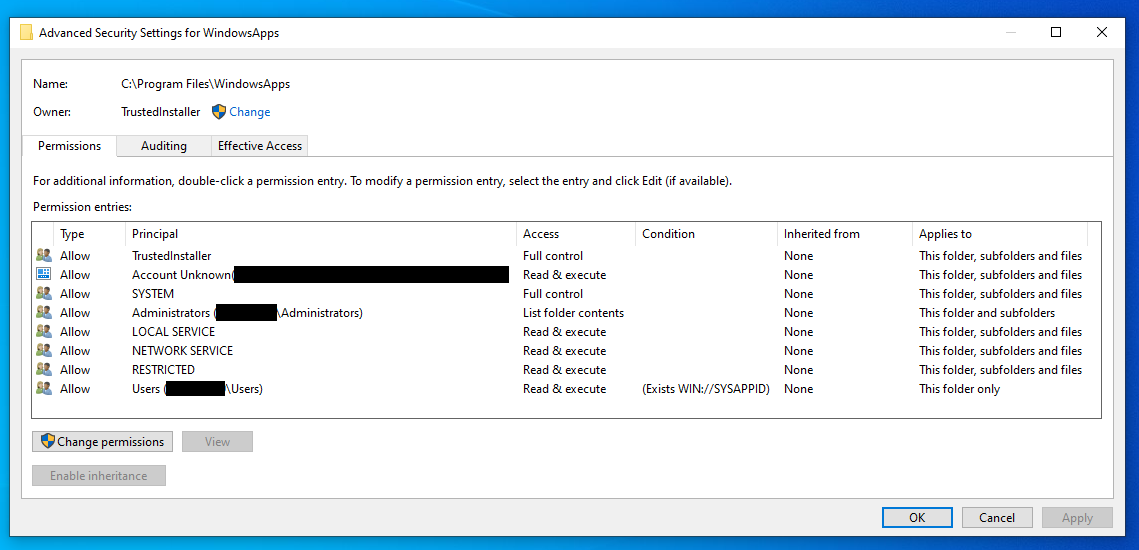
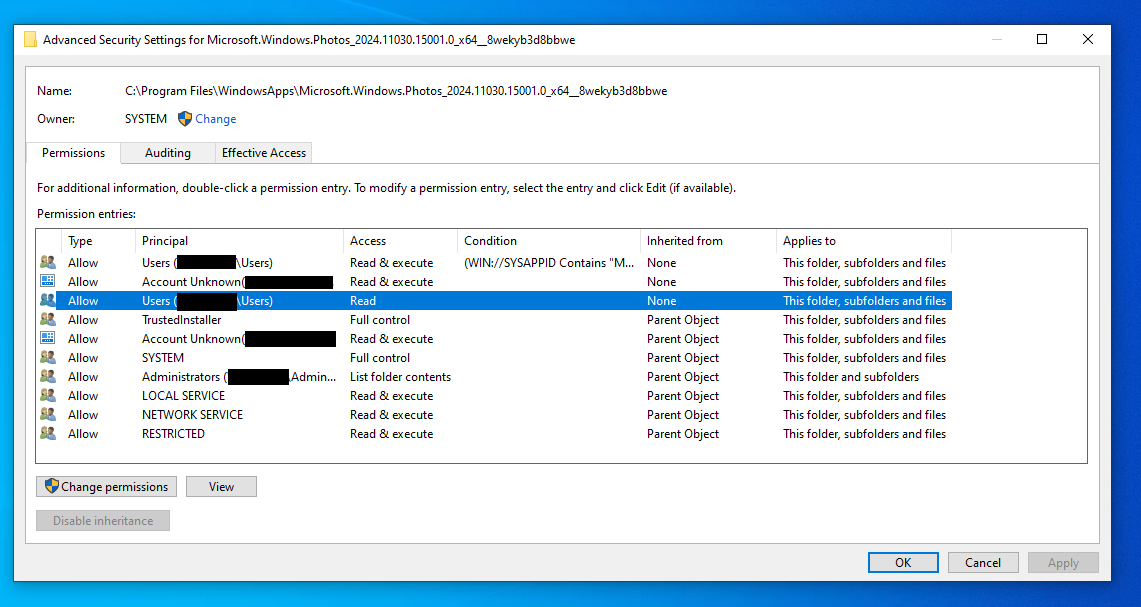
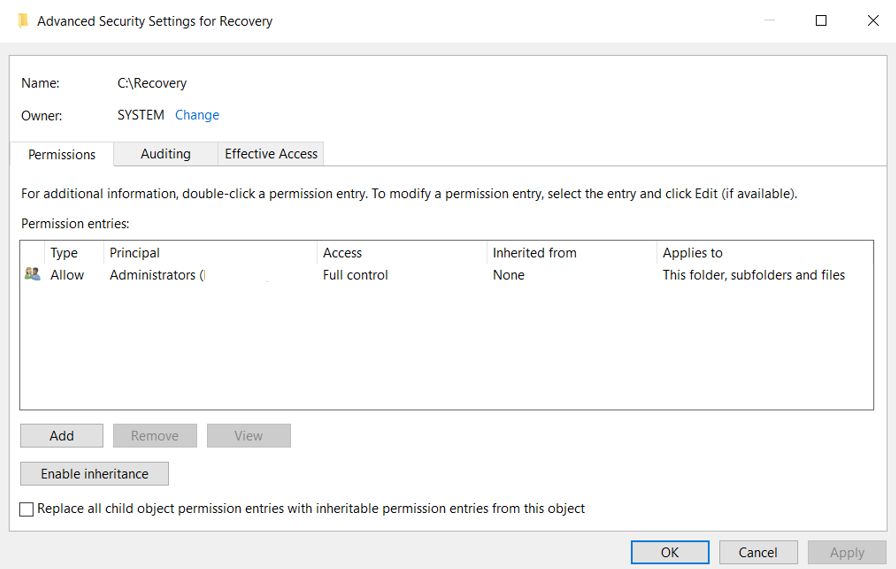
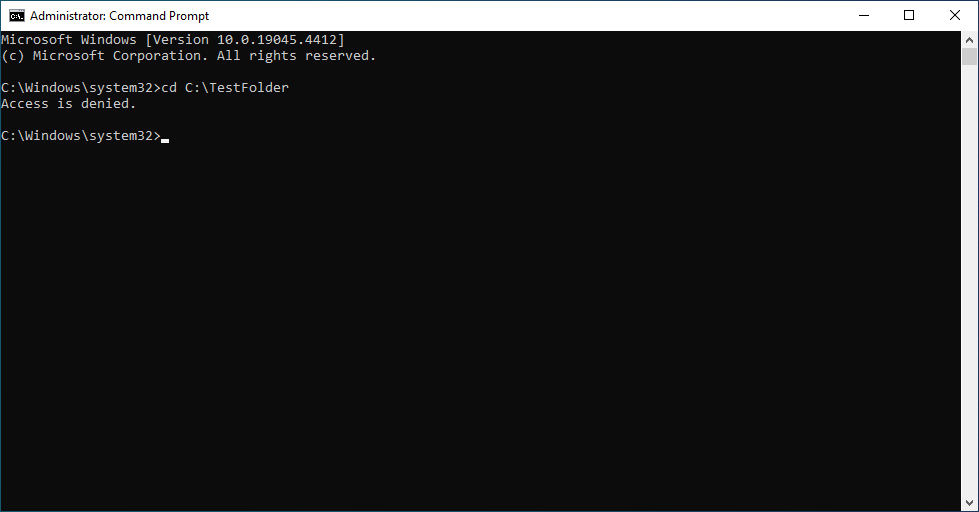
There are folders and files in Windows that a user with administrative privileges is denied access to. This is a safety feature to keep a user from accidentally deleting a file that is necessary for Windows or some app to function. Malware and even well known software makers will use the security settings in a denied access folder to keep a user from deleting their software. There are situations where an informed user needs to access a denied access folder or file.
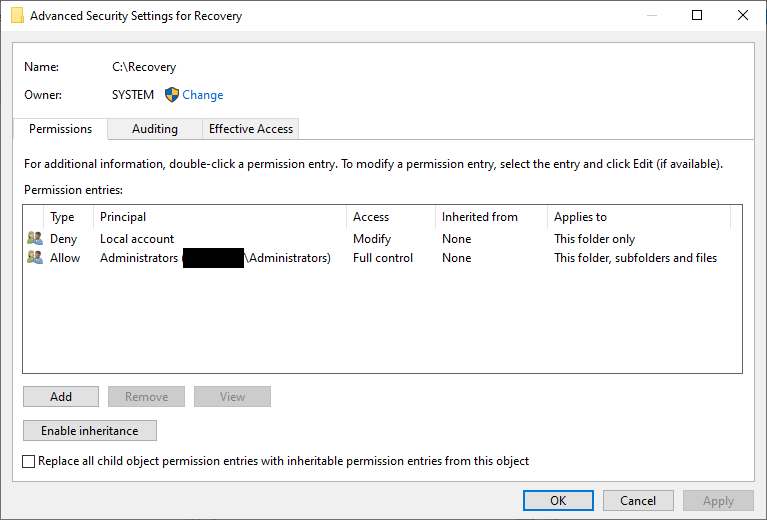
The typical method involves changing ownership to the user, then adding that user to the security settings for that folder/file, and modifying the security settings to allow that user access. This can be quite involved just to look into a denied folder.
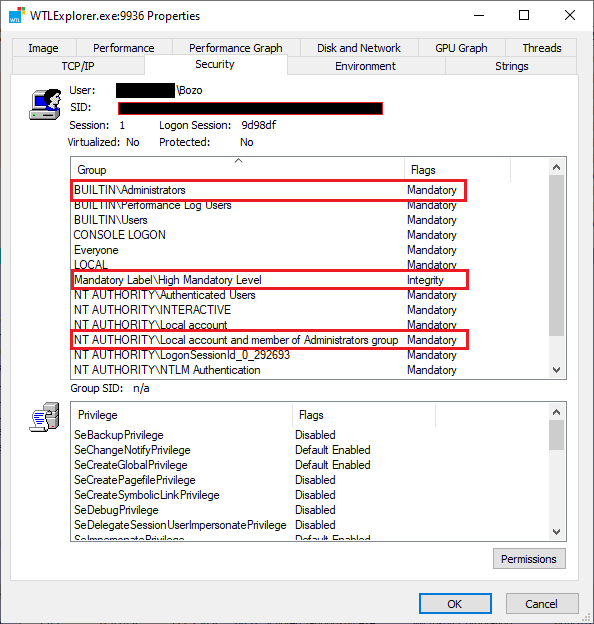
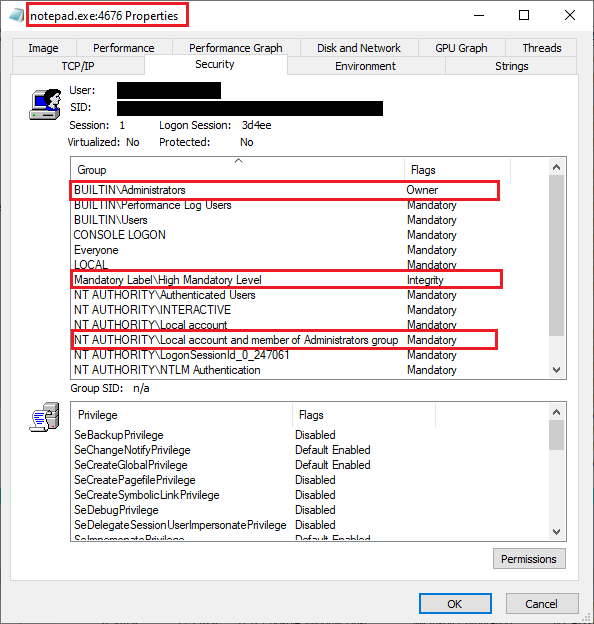
The Administrator’s account in Windows has security settings beyond those of a user account that was created as an “Administrator”. Many of these folders and files that deny access to that user will allow access in the Administrator account.
Thus a user can set up the Administrator account, switch to that Administrator account and view the folder or file that was denied in the user account. No ownership or security settings need to be changed.
This is not 100%. Some folder/files will allow the Administrator’s account to delete it. There will be folders and files that the Administrator account can view, but are not allowed control of (aka: cannot delete). There are folders and files that even the Administrator account cannot access. These are usually files that are protected and should be left alone.
There are other uses for the Administrator account.
For those that wish to set up and use their Administrator account, the attached PDF has detailed instructions.
HTH, Dana:))