… Do you have Drive Encryption in the left panel at Settings | Update & Security?…
Hi WCHS:
Just to clarify, the category shown in your image at Settings | Update & Security is Device Encryption (i.e., not Drive Encryption). See TheWindowsClub article Difference Between Device Encryption and BitLocker.
I do not have a category at Settings | Update & Security called Device Encryption on my Win 10 Pro machine. According to the MS support article Device Encryption in Windows, if your device doesn’t support BitLocker (e.g., if you have Win 10 Home), you may be able to use Windows Device Encryption instead at Settings | Update & Security | Device Encryption if you meet certain system requirements. Similar information is posted in the MS support article Turn On Device Encryption.
I deliberately enabled BitLocker during my initial OOBE setup when I first purchased my Win 10 Pro laptop (BitLocker has since been disabled) and I always managed BitLocker from Control Panel | System and Security | BitLocker Drive Encryption.
I don’t know if it’s relevant but my Inspiron 5584 / Win 10 Pro v21H2 laptop does not support Modern Standby (S0 Low Power Idle).
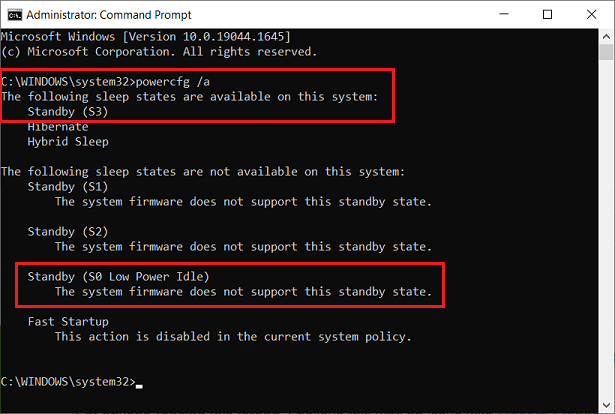
———–
Dell Inspiron 5584 * 64-bit Win 10 Pro v21H2 build 19044.1889 * Firefox v104.0.1 * Microsoft Defender v4.18.2205.7-1.1.19500.2 * Malwarebytes Premium v4.5.14.210-1.0.1751 * Macrium Reflect Free v8.0.6867




