Ask you to give them remote access to your computer — which lets them access all information stored on it, and on any network connected to it
Newsletter Archives
-
31 days of Paranoia – day 31
First off a bit of Halloween humor seen on a twitter post… someone was saying they were dressing up as “Outlook”. Their costume was to wrap themselves up in a translucent shower curtain with a sign that said “Not Responding!”.
I think we all can relate to that.
So as I’m here at the front door (dressed up like Supreme Court Justice Ruth Bader Ginsburg I might add) waiting for the trick-or-treaters let’s end our 31 days of paranoia with one more post of resources:
Places to go to get help – especially for Windows issues.
First off – and above all – this site. Specifically the Forums on this site. There is nothing that helps better than someone else saying “gee I don’t see that here”… or “yes, I’ve had that EXACT same issue and here’s how I fixed it!”. When you have no other machine to compare to, you tend to get a bit paranoid thinking that attackers are making your machine freak out when it might just be… well… patching or anti virus scanning or something third party making it freak out.
Next I’d recommend something that makes me shiver… and not just because it’s Halloween and I’m listening to the Amazon Halloween playlist (It’s playing Michael Jackson’s thriller right now). Twitter. Yup Twitter. I am lately finding that you can get one on one help when you direct it to a corporate or official twitter account. There is a list (it might be a bit outdated) of official twitter aliases, and their official support alias for Microsoft is https://twitter.com/microsofthelps
You can direct message them and get communication back. The reason it makes me shiver is I find that twitter is too narrow of a channel and the knowledge or solution doesn’t often get exposed like it does in a forum venue.
If you are an IT pro kind of person, I’m finding that Microsoft employees respond pretty good on the Techcommunity venue.
Also make sure you have at least SOMETHING that can get to google. The best way to fix a Windows machine is a working computer or device and a search engine. There are so many times I’ve fixed something scrolling around a page on my iPhone.
Now just so you don’t think I’m going to end the 31 days of paranoia in a happy spot here are some parting trends to worry about:
Crypto mining attacks are trending. The bad guys get on your machine and use the excess CPU to coin bitcoin. So they don’t want to steal your credit card data, they want to use your computer to make their own money.
Smaller more targeted phishing is on the rise.
Attackers that set up Office 365 relay rules and then hide the fact that they’ve taken over your email box.
And with that we close this month of paranoia. Going forward I’ll still throw in a paranoid post or two…. just not as often as one a day.
-
Patch Lady – 31 days of Paranoia – Day 25
How many times has this happened to you? You get a call and the person on the other end of the phone says you have a problem with your [computer, iPhone, apple device, technology]. They usually say that your device is alerting them that it is full of viruses.
Their goal? To either get on your machine or get your credit card from you and then steal money from you. As noted on this FTC page,
The scammers may then


Try to enroll you in a worthless computer maintenance or warranty program

Install malware that gives them access to your computer and sensitive data, like user names and passwords

Ask for credit card information so they can bill you for phony services or services available elsewhere for free

Try to sell you software or repair services that are worthless or available elsewhere for free

Direct you to websites and ask you to enter credit card, bank account, and other personal information
How many of you try to play along and keep the scammers online? I know some folks that purposely keep a virtual machine around and let scammers log into that and pretend to be really really dumb in regards to technology to keep the scammers online as much as possible. I have often dragged them along for a time and then finally asked them if they feel right scamming people. They promptly hang up.
If you’ve let them on your system, make sure you scan your system with an antivirus program. Cancel credit cards if you gave them any financial information.
But just know that Microsoft never calls you, unless you’ve called them first.
-
Patch Lady – 31 days of Paranoia – Day 22
We come to our 22nd day of paranoia and today is about a topic that is near and dear to many of you….. end user license agreements. Those statements that vendors provide that we all click through and most of us don’t understand them, nor read them like we should. The electronic foundation recaps most of the terminology that we miss, but there’s another end user license agreement issue that we often overlook. One where the terms change and we don’t realize that it has changed:
For example… let’s look at the Windows 10 end user license agreement.
In Windows 10 the eula specifically says this:
Section 2 c (v):
use the software as server software, for commercial hosting, make the software available for simultaneous use by multiple users over a network, install the software on a server and allow users to access it remotely, or install the software on a device for use only by remote users;Windows 8.1 Pro the eula says this:
The software is not licensed to be used as server software or for commercial hosting, so you may not make the software available for simultaneous use by multiple users over a networkOne could argue that the eula specifically disallows the ability to set up a headless Windows 10 machine that one can remote into and use remotely.
Given that they have announced a Microsoft virtual desktop hosted on Azure, you can see that’s where they want the remote experience to be.
Bottom line, never assume that end user license agreements are static. They can be updated with newer terms. Keep reading ….and keep reading between the lines… as necessary.
-
If you got hit by the 1809 upgrade file deleting feature…
and you’ve tried using Recuva to get the files back…
Contact Microsoft directly:
https://twitter.com/donasarkar/status/1048612272287834112
“They have the tools to get you back to a good state.”
Like, maybe Hawaii?
If Microsoft does have a secret tool or two in their hip pockets, I’d sure like to hear about it/them.
-
Patch Lady – 1803 issues with peer to peer
A new “known issue” note was posted in the answers forum:
File Explorer may not detect other devices or perform file sharing on the local network when running Windows 10 version 1803
Justin posts:
Microsoft is aware of reports that devices running Windows 10 version 1803 cannot connect to other devices on their home network and is investigating the issue.
You can resolve this problem by setting some services to Automatic (Delayed Start) and restarting Windows:
- Press the Windows Key and R at the same time to bring up the Run dialog.
- Type services.msc in the Run dialog and press Enter.
- For each of the following services, locate the service in list, right-click the service and select Properties. Then set the Startup type to Automatic (Delayed Start) and select Apply.
- Computer Browser (Browser)
- Function Discovery Provider Host (FDPHost)
- Function Discovery Resource Publication (FDResPub)
- Network Connections (NetMan)
- UPnP Device Host (UPnPHost)
- Peer Name Resolution Protocol (PNRPSvc)
- Peer Networking Grouping (P2PSvc)
- Peer Networking Identity Manager (P2PIMSvc)
- Restart Windows.
-
Patch Lady – Quickbooks and emails
 I was posting up the master patch listing tonight and I spotted this KB and I know this impacted people recently:
I was posting up the master patch listing tonight and I spotted this KB and I know this impacted people recently:ISSUE
After updating Outlook to Monthly Channel Version 1805 (Build 9330.2087), external applications may crash when interacting with or sending email.
For example, you may get an “Outlook is not responding” error with Intuit QuickBooks. Possible solutions for that specific error can be tried via this Intuit QuickBooks Help article: Crash: Com Error in QuickBooks Desktop
STATUS: FIXED
This issue is fixed in Monthly Channel Version 1805 (Build 9330.2118) and higher. To get the latest update immediately, open Outlook and choose File > Office Account > Update Options > Update Now.
Microsoft made a service change for Outlook on June 11 2018 (3:45 PST) to mitigate instances of a crash that happens if you’re using a POP or IMAP account. Because of the way the service changes are implemented and also because the issue involves 3rd party interaction with Outlook, you may have to restart Outlook up to three times to ensure that the service change is applied. These restarts ensure that the service change is recognized, then downloaded, then applied successfully to your install of Outlook.
If anyone is seeing this on NON Click to run, let me know. But again this points out you need to move to the semi-annual non monthly version of Office 2016 as there are less issues.
-
Patch Lady – KB 4103718 no longer lists “investigation” note
 Remember that KB that was updated to showcase that Microsoft was investigating the networking issues?
Remember that KB that was updated to showcase that Microsoft was investigating the networking issues?https://support.microsoft.com/en-us/help/4103718/windows-7-update-kb4103718
This has been removed from this KB and appears to have been updated today to remove this note:
Microsoft is aware that some customers have reported that network drivers are intentionally uninstalled, then fail to reinstall after applying the May 8, 2018 update. This can result in the loss of network connectivity.
Microsoft is presently investigating and will provide a status update when the investigation is complete.
I haven’t seen as many reports in the last few days of networking issues, but I’m not sure if that’s due to folks holding off on updating. I can tell you on my several Windows 7 machines I have not seen an issue with networking.
As always, when you go to install, be prepared to roll back.
Updated note: My apologies if I didn’t make this clear: The patch had no change. All that happened was a documentation change where they removed the investigation note. However we have no final word on what happened. All I know is that in my personal testing/patching on my Windows 7 under my control none had issues with networking.
-
Patch Lady – KB4103718 /KB4103712 known issues
 As noted in https://support.microsoft.com/en-us/help/4103718/windows-7-update-kb4103718 and in https://support.microsoft.com/en-us/help/4103712
As noted in https://support.microsoft.com/en-us/help/4103718/windows-7-update-kb4103718 and in https://support.microsoft.com/en-us/help/4103712Microsoft is aware that some customers have reported that network drivers are intentionally uninstalled, then fail to reinstall after applying the May 8, 2018 update. This can result in the loss of network connectivity. Microsoft is presently investigating and will provide a status update when the investigation is complete. -
Surface Pro 4 gets a firmware/driver patch
Just saw an addition to the Surface pro 4 update history page.
Windows Update History Name Device Manager Name Surface – Human Interface Device – 2.0.313.0 Surface Digitizer Integration – Human Interface Device - 2.0.313.0 enables on-screen support for Surface Dial.
Surface – Firmware – 105.0.106.8 Surface Touch – Firmware - 105.0.106.8 enables on-screen support for Surface Dial and improves touch accuracy.
Surface – System – 2.0.2.0 Surface Dial Detection – System - 2.0.2.0 enables on-screen support for Surface Dial.
Surface – System – 1.0.821.0 Surface Touch Servicing ML – System - 1.0.821.0 enables on-screen support for Surface Dial and improves touch accuracy.
Care to bet that they didn’t solve the screen shake problem?
-
Patch Lady – Networking issues and KB 4088875
 As Woody pointed out earlier today there are some reports of networking issues after the install of this month’s Server 2008 r2 and Windows 7 patch. The issues are not widespread and they appear to be limited to two scenerios:
As Woody pointed out earlier today there are some reports of networking issues after the install of this month’s Server 2008 r2 and Windows 7 patch. The issues are not widespread and they appear to be limited to two scenerios:Scenerio 1 – VMware. As noted on a reddit post a new virtual Ethernet network card is installed/enabled after the update. The side effect has occurred before with other convenience rollups and a workaround was previously posted to this KB and a script is provided to fix the issue. It is not impacting all servers, it appears to be impacting virtual machines on VMware.
You can see more threads here.
Scenerio 2 – workstations. This one is a bit more fuzzy and not clear cut. I’ve seen reports where workstations with static IPs may be impacted with this update. There are definitely enough credible reports of chipsets being reset and losing their networking IP addresses.
Note that I’m seeing this more in businesses than in consumer/peer to peer settings.
On my Windows 7 (my old machine that we keep around for older programs), I’m seeing this update unchecked:
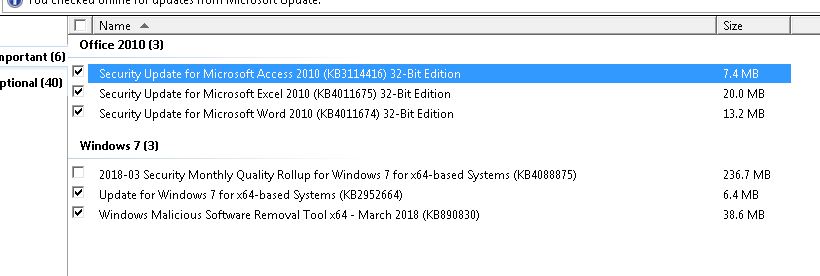
Which normally means that Microsoft is throttling the patch while they monitor issues.
What is honestly a bit more concerning is this documented side effect:
After installing this update, SMB servers may leak memory. Microsoft is working on a resolution and will provide an update in an upcoming release. If you run a file server, you may want to run tests and determine if you do see THIS side effect as that one may impact.
More on this as I see issues.
-
Revisited: How to update an old copy of Win7
 Credit: David Stanley, Nanaimo, Canada
Credit: David Stanley, Nanaimo, CanadaKevin Beaumont just tweeted:
https://twitter.com/GossiTheDog/status/965908161101271040
Barry Dorrans replied with a reference to this advice from @SwiftOnSecurity in April 2016:
[REVISED] If updating fresh Win7, first download these, install, and reboot to make update install faster:
KB3102810
KB3138612
KB3145739What struck me is how @SwiftOnSecurity’s advice (from April 2016) differs from our AskWoody advice (Feb. 2017, as amended) from @CanadianTech at AKB 3172605, basically:
3… download and install either one or two updates manually. In most cases only the first (KB3172605) of these is needed. If that produces a result that says the “update is not appropriate for your computer”, you need to first install the 2nd of these (KB3020369), then install the first (KB3172605).
Can anybody out there reconcile the differences? Which method is best?
I have a sneaky suspicion we’re going to see lots of Win7 (re-)installs this year.
-
Adobe Flash patch KB 4074595 pushed out the Windows Update chute
Doncha just love Flash?
A few hours ago, Microsoft pushed the first round of February 2018 patches. The KB 4074595 patch fixes two security holes in Adobe Flash Player, CVE-2018-4877 and CVE-2018-4878.
Microsoft has a few details in Security Advisory ADV180004.
Adobe’s Security Bulletin APSB18-03 says:
Adobe is aware of a report that an exploit for CVE-2018-4878 exists in the wild, and is being used in limited, targeted attacks against Windows users. These attacks leverage Office documents with embedded malicious Flash content distributed via email.
Adobe goes on to say it’s a remote code execution hole. Critical Priority 1. Impacts 28.0.0.137 and earlier versions (February 6, 2018). New version is 28.0.0.161.
Adobe’s version checker is here.
Microsoft’s patches are for Windows 8.1 and Win10, all versions. All of those versions need to have Internet Explorer (and, in the case of Win10, Edge) fixed to plug the holes in the embedded versions of Flash.
Adobe’s patches cover everything other than IE 11 and Edge. Chrome is fixed automatically, by default, when you re-start Chrome.
Liam Tung at ZDNet reports:
Researchers at Cisco Talos said hackers known as Group 123 were using the zero-day Flash flaw and Excel sheets to deliver the ROKRAT remote-administration tool.
Cisco researchers found Group 123’s Excel sheets contained an ActiveX object that was a malicious Flash file that downloaded ROKRAT from a compromised web server. Notably, it was the first time this group has been seen using a zero-day exploit, suggesting the targets were carefully selected and high value.
FireEye, which calls Group 123 TEMP.Reaper, said it had observed the group interacting with their command-and-control infrastructure from North Korean IP addresses. Most of the group’s targets were South Korean government, military and defense industry organizations, it said.
If you haven’t yet disabled Flash, now would be a very good time to do so. Chris Hoffman at How-to-Geek has detailed instructions. If you absolutely have to have Flash, restrict it to one browser — I use Chrome to do the dirty deed — and only use it manually, under duress.
If you can’t or won’t throttle Flash, get the update applied. Yet another Patch Wednesday.
Thx CAR, Günter Born.


