Newsletter Archives
-
Avast fixes bug that made the June cumulative updates block many programs
Microsoft has officially acknowledged that Avast (one of my least-favorite Windows programs) has plugged a bug that caused many different Windows programs to fail to launch. Per the official Release Information Status page:
Error when attempting to open any Microsoft Office application
We have received reports that some users are unable to open apps after installing KB4557957, especially Microsoft Office apps. Affected users might also receive an error, such as, ‘Windows cannot find “c:\program files\microsoft office\root\office16\winword.exe” Make sure you typed the name correctly, and then try again.’
Affected platforms:
Client: Windows 10, version 2004; Windows 10, version 1909; Windows 10, version 1903
Server: Windows Server, version 2004; Windows Server, version 1909; Windows Server, version 1903Resolution: This issue has been resolved by Avast. This issue only affected devices with certain versions of Avast or AVG applications and was addressed with an update to their respective products. For more information on this, please see Avast’s forum post here. Note No update is needed for Windows or Microsoft Office to address this issue.
In fact, as Lawrence Abrams reports on BleepingComputer:
A component of the AVG/Avast security software causes Image File Execution Options registry entries to be created for various applications that would launch applications through a filter that points to C:\Program Files (x86)\AVAST Software\Avast Cleanup\autoreactivator.exe.
A recent update broke something in this filter that was causing the programs to not launch.
I know, I know. People love their antivirus programs. I continue to use, and recommend, Microsoft’s Windows Defender. It’s effective, reliable and free.
-
Reports of Windows Security (nee Microsoft Security Essentials) crashing after installing this morning’s definition updates
This is quite rare, in my experience, but it looks like we got a bad Windows Defender definition update this morning.
Poster Mike Reynard on the Microsoft Answers site says:
I’ve got an issue that’s come up today in Windows Security. On ‘virus and threat protection’ a notification shows: ‘The threat service has stopped. Restart it now.’ I have tried to do this but it does not work. Another message reads: ‘Unexpected error. Sorry, we ran into a problem. Please try again.’ This started happening after the following update: … Version: 1.313.1638.0… Released: 4/16/2020 4:53:09 AM
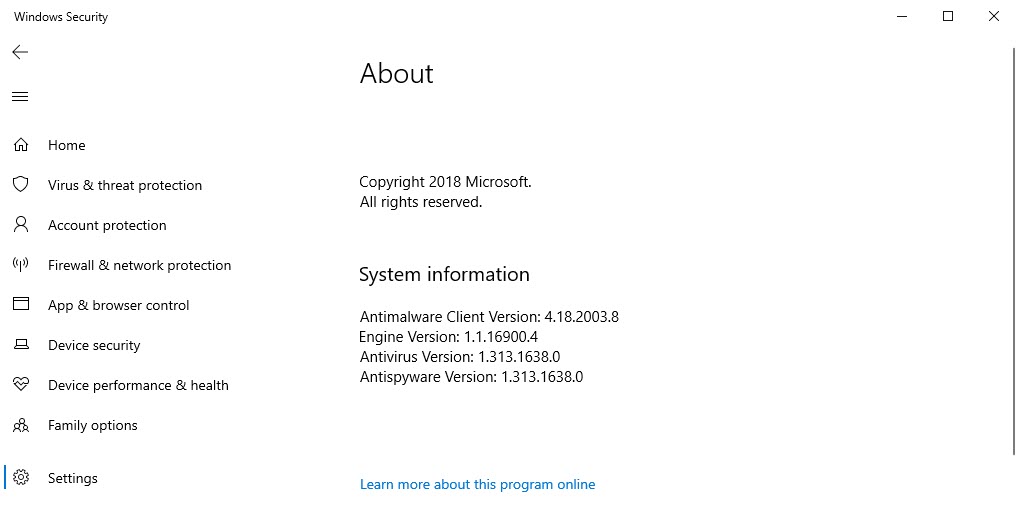
I’m running the same virus definition (screenshot above), and not seeing any problems, but there’s a similar complaint lodged on the Microsoft Answers forum by KevinThomas1. @Sumit, here on AskWoody, posted about it a couple of hours ago.
If you see a similar crash from Windows Security, could you let us know? Be sure to include your Antivirus Version value from the Windows Security About page. (Start > Settings > Update & Security > Windows Security > click “Open Windows Security” > at the lower left, Settings > About.)
UPDATE: Lawrence Abrams has a full rundown on BleepingComputer, showing crashes with Antivirus version 1.313.1666.0.
By the by: Microsoft’s branding of its antivirus software is so convoluted you need a scorecard. Several scorecards. As I understand it, Microsoft AntiSpyware became WinXP and Win7’s Microsoft Security Essentials. Then MSE became Windows Defender in Win8 (prior to that, “Windows Defender” was an antispyware program). After that, the product gained some features, shed a couple, and changed names to “Microsoft Defender” and “Windows Defender Antivirus” and “Windows Security” and “Son of Windows Microsoft Defender Security Antivirus.” Ok. I made the last one up.
Right now, for those of us who don’t pay extra for Microsoft security, the politically correct names are “Windows Defender Security Center” for the suite of protection products and “Windows Defender Antivirus” for the antivirus component. But inside Windows, the product is known as “Windows Security” (see screenshot) and “Antivirus” is an engine in Windows Security.
Got that?
-
Born: Broadcom botches the Symantec migration
So Broadcom bought Symantec for $ 10 billion. Symantec becomes NortonLifeLock, another excellent example of wasted name recognition.
As part of the transition, today, Broadcom abruptly cut off all links to the old Symantec site. People, uh, aren’t happy. Apparently they’re even having trouble buying new licenses for the old Symantec software.
Günter Born has a rundown, which relies heavily on Catalin Cimpanu’s reporting. You’d think with a $10 billion budget they’d do a bit better.
-
Avast, caught selling users’ private data, will shut down the division that’s selling the data
So what do you do when your company’s caught selling the surfing data from its “Free” antivirus product?
You shut down the division that sells the data, of course.
Charlie Osborne on ZDNet:
Avast is winding down its subsidiary Jumpshot following an explosive investigation into the sale of user data to third parties that may pose a risk to consumer privacy.
On Thursday, the antivirus vendor said the unit will no longer have access to user information harvested from users of Avast products and services will eventually be fully terminated…
Jumpshot reportedly has access to information from over 100 million devices; or rather, once did.
-
Enormous trove of Avast-gathered data being sold
Joseph Cox at Vice/Motherboard just published an eye-opener:
Leaked Documents Expose the Secretive Market for Your Web Browsing Data
An Avast antivirus subsidiary sells ‘Every search. Every click. Every buy. On every site.’ Its clients have included Home Depot, Google, Microsoft, Pepsi, and McKinsey.
Our report relies on leaked user data, contracts, and other company documents that show the sale of this data is both highly sensitive and is in many cases supposed to remain confidential between the company selling the data and the clients purchasing it.
Looks like PCMag.com joined in the investigation.
Are you using Avast Free?
-
Born, BleepingComputer: Malwarebytes fixes AdwCleaner, removing a DLL hijacking vulnerability
Günter Born is at it again. This time he found a DLL hijacking vulnerability in Malwarebytes’ AdwCleaner 8.
If Windows shows unwanted programs or displaying unwanted ads after installing software possible adware has been involved. In order to clean the system of this unwanted programs, the tool Malwarebytes AdwCleaner may be used (its free for private use)…
When AdwCleaner runs with administrative permissions, the code from the loaded DLL files is also executed as a process with administrative permissions. Normally this works well, because Windows does not find the DLL files in the folder of the program and then searches in the Windows folders. But if a malware knows that a tool has a DLL hijacking vulnerability for certain DLLs, it only needs to store a file with the same name in the folder containing the application.
Born notified Malwarebytes on Dec. 10 and they sent him a beta copy of a new version. That version also had a major DLL hijacking problem. Ultimately, Malwarebytes released a smarter version 8.0.1 without the security hole on Wednesday.
There’s a detailed explanation of the vulnerability and its resolution in this Lawrence Abrams post on BleepingComputer.
-
Microsoft blinks: MS Security Essentials will be supported after Win7 hits end-of-life next month

At least, that was the promise.
Nobody’s fixed the official documentation yet.
Details in Computerworld Woody on Windows.
-
Avast snooping gets called out by Firefox
And for good reason.
Martin Brinkmann reports:
If you search for Avast or AVG on the official Mozilla Add-ons website, you may notice that no results by these companies are returned. Neither Avast Online Security or SafePrice… are returned by the Store currently even though these extensions exist. It appears that Mozilla removed these extensions from its Store.
He goes on to quote a security researcher (the creator of AdBlock Plus) who determined two months ago that Avast snoops like crazy:
The data collected here goes far beyond merely exposing the sites that you visit and your search history. Tracking tab and window identifiers as well as your actions allows Avast to create a nearly precise reconstruction of your browsing behavior: how many tabs do you have open, what websites do you visit and when, how much time do you spend reading/watching the contents, what do you click there and when do you switch to another tab. All that is connected to a number of attributes allowing Avast to recognize you reliably, even a unique user identifier.
Back in August, @satrow observed:
They’ve been interfering with browser HTTPS connections for almost 5 years now.
Seems like the chickens have come home to roost.
Brinkmann says Avast extensions are still available in Chrome – but I can’t find any.
(By the by… Avast owns AVG. Avast bought a majority stake in AVG more than three years ago. The products are similar, but not identical. Wouldn’t surprise me a bit if AVG were up to similar shenanigans.)


