-
Common reasons for backup and imaging failures
ISSUE 16.18.0 • 2019-05-20
 The AskWoody Plus Newsletter
The AskWoody Plus Newsletter
In this issue
LANGALIST: Common reasons for backup and imaging failures
BEST OF THE LOUNGE: Back by popular request: Interesting discussions in the forums
PATCH WATCH: Got XP? Got a patch!
BEST UTILITIES: Freeware Spotlight — SwiftSearch
WEB SECURITY: Secure website accounts with Microsoft’s Authenticator app
LANGALIST
Common reasons for backup and imaging failures
By Fred Langa
Sometimes, when a backup or system image fails, all you have to go on is a generic and not very useful “cannot find the file specified” error message.
Those problems often stem from one of five common causes discussed below — including some odd issues with a Windows shadow-copy service.
Why won’t her backups complete?AskWoody reader Jacquie is trying to find out why her files won’t back up, but a vague message is making it difficult to find the answer.
- “For the past several days, my laptop has not been able to fully back up my files. I get the error message:
‘Backup encountered a problem while backing up file C:\Users\[user]\Downloads\Incident Report 3-11-2019. Error:(The system cannot find the file specified. (0x80070002))’
“I’ve used a system repair disk, and I tried to do a repair install, but nothing works. Help!”
There are multiple reasons for a “0x80070002/system cannot find the file specified” backup error. One of the most common is a problem with the shadow copies used by most good backup and imaging tools.
A shadow copy is a temporary snapshot of the drive that’s being backed up. In Windows, the shadow copy is created by a built-in, low-level system service called Volume Shadow Copy Service (VSS).
Here’s the thing: The actual backup or image is made from the shadow copy rather than from your actual, live files.
This kind of indirect backup has two major benefits.
First, it improves the quality of the backup or image because Windows’ low-level VSS is part of the operating system itself. Acting as a kind of master conductor of disk operations, VSS can ensure all files are frozen into the shadow copy at essentially the same moment. (That’s why it’s called a “snapshot.”)
This way, if the backup process takes minutes, tens of minutes, or even hours, all files in the backup will be from the same moment — when the shadow copy was triggered.
And that leads to the second major benefit: You can continue to use your PC while a shadow-copy backup is in progress. Any changes you make to the live files on your disk won’t affect the hidden, read-only shadow copy that’s actually being backed up. (Those changes to live files will have to wait for the next backup, when they’ll be swept up by the VSS into a new shadow copy.)
This process works fine most of the time — VSS has been around since Windows XP — but, clearly, things can and do go wrong, as Jacquie can attest.
One common problem: VSS gets confused by symbolic links (or “symlinks”; Microsoft info), hard links, and junctions (MS info).
Those terms may sound unfamiliar, but symlinks, hardlinks, and junctions are standard Windows technologies. They’re implemented by users, developers, and software to stitch together files and folders from different physical or electronic locations into a single, virtual container.
Even if you’ve never knowingly used ’em, symlinks are probably active on your system right now. For example, Windows’ built-in Libraries (MS info) are based on symlinks. (To see Win10’s symlink-based Libraries, open File Explorer and click View/Navigation Pane/Show Libraries, as shown in Figure 1.)
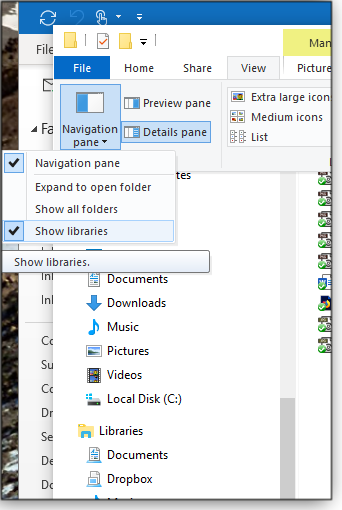
Figure 1. Although hidden by default, Windows’ symlink-based Libraries are still present and active in Windows 10.VSS usually works fine with system-defined symlinks (such as those in the default Libraries), but user- or third party–created symlinks can cause trouble. If VSS encounters a broken or malformed symlink (or hard link, or junction), you’ll get one of those 0x80070002 “cannot find the file specified” errors.
So, if you or any of your software has added symbolic links in Windows Library or elsewhere, make sure they’re working properly. Once you correct or delete any malfunctioning symlinks, VSS (and subsequent shadow copy–based backups or images) should work OK.
If that’s not the problem, there are at least four other somewhat common causes for a VSS file-not-found error:
- 1) Not enough space: If your disk is nearly full, there might not be enough space to create a temporary shadow copy. To see how much space your system needs for its shadow copies, open an admin-level command window and type vssadmin list shadowstorage at the prompt. Click Enter and see what’s listed for the Maximum Shadow Copy Storage space (see Figure 2).

Figure 2: The administrative command vssadmin list shadowstorage will show you how much space your shadow copies need — and what they’re actually using. - 2) Disk errors: Common disk errors can mess up a shadow copy. Chkdsk may be able to help (MS info).
- 3) Dual Booting: Using the Grub2 bootloader in a Windows/Linux dual-boot setup can confuse VSS. (Yet another reason why I personally dislike dual-boot setups.)
- 4) Communication issues: Disconnects, drop-outs, or interruptions when copying from/to an external drive or networked location might cause errors.
And, believe it or not, there are still other causes, too.
It’s clearly a complex topic. But with just a bit of luck, something in the info above might trigger an “aha!” that leads you to a solution.
If not, here are some of the best online resources I could find for additional help:
- Microsoft: Backup fails with error code 0x80070002 — SOLVED
- Microsoft: Error code 0x8100002F and or error code 0x80070002 when you back up files in Windows 7
- Superuser.com: Windows Backup fails with 0x80070002: “The system cannot find the file specified”
- Easus.com: How to Fix Error Code 0x80070002 in Windows Update
- Diskgenius.com: Fix Issues Related To Error Code 0x80070002
Send your questions and topic suggestions to Fred at fred@askwoody.com. Feedback on this article is always welcome in the AskWoody Lounge! Fred Langa has been writing about tech — and, specifically, about personal computing — for as long as there have been PCs. And he is one of the founding members of the original Windows Secrets newsletter. Check out Langa.com for all Fred’s current projects.
Best of the Lounge
Back by popular request: Interesting discussions in the forumsLongtime Windows Secrets readers will remember the weekly Lounge Life column. Here’s the new AskWoody version — in a more readable format but with the same focus on discussions that might be of interest to many AskWoody Plus readers. Let us know what you think — in the Lounge, of course.
This week, we lead off with world traveler Susan Bradley’s post about lithium-ion batteries.
HARDWARE
Patch Lady — The battery problemBy Susan Bradley, AskWoody MVP
Batteries power many of our laptops and devices, but a faulty battery can lead to dangerous conditions.
It really doesn’t matter what brand of portable technology you’re taking out and about — MS Surface, Apple MacBook, HP, Lenovo, etc. — any lithium battery can develop problems. What are the danger signs, and what are your options? Check out Susan’s post and join the forum discussion.
Chromebook
Chromebooks will be gaining access to the ‘real computer’ Linux software
that works offline.
Windows 10
Microsoft is planning to add its own, custom-built Linux kernel to future releases of Windows 10. So should the Linux community be wary of “Extend, Embrace, Extinguish”?
Windows 7
Woody announced a new forum for Win7 users who refuse to give up on their favorite operating system. As forum admin PKCano explains, “Microsoft wants everyone off Win7 ASAP. But as a Win7 group, we intend to help others who don’t want to let go — and who want to keep safe and protected for as long as possible.”
If you’re not already a Lounge member, use the quick registration form to sign up for free.
Got XP? Got a patch! By Susan Bradley
By Susan BradleyMicrosoft surprised me once again — in a good way. The company proved that, when its customers are truly at risk, it’ll do what’s necessary to protect them.
No, not with dragons (à la Game of Thrones); rather, it actually released a patch for Windows XP and Server 2003. I’m amazed! The fix protects against a Remote Desktop Services vulnerability that can be exploited remotely and without user authentication. Other older versions of Windows — Win7, Server 2008, and Server 2008 R2 — are also threatened. Win8 and Win10 aren’t affected.
Still running one of these older systems? Read on! (And if you’re not, skip to the next item: Win10 updates.)
If you have a machine with XP or Server 2003, I sure hope you’re not accessing the Internet with it. On systems running Win7, Server 2008, or Server 2008 R2, you need to check whether you’re at risk. Specifically, if you have port 3389 open to the Internet, and you can access a remote PC merely by entering an IP address and your credentials into a Remote Desktop client, you’re highly vulnerable.
To check the status of port 3389, you (or another admin) need to sign in locally to the remote computer (e.g., the home or office machine you access over the Internet). Next, open a browser and head over to the ShieldsUP site. Once there, click the Proceed button for a scan of open ports. On the next page that pops up, enter 3389 into the Home section and click User Specified Custom Port Probe. You’ll get an immediate status report for that specific port (labeled Microsoft Remote Display Protocol).
If it’s open and you use a Remote Desktop client to access your computer over the Net, you need to patch the machine as soon as possible — and then reconsider how you connect into your system. On the other hand, if you don’t have Remote Desktop enabled, you’re not at risk. To check, go into the Control Panel, select System, and click Remote settings.
Having port 3389 open to the world has always been risky. A tool that’s been around for years — TSGrinder — lets attackers compromise systems through repeated attempts to sign in to machines with common passwords. So, again, even without this latest Remote Desktop Services vulnerability, it’s unwise to have port 3389 open to the Web.
So what makes this issue so horrific that we’re telling you to patch immediately? The exploit requires no user authentication or action. And if you have Remote Desktop Services running in Windows (possibly without knowing it), an attacker can access your system, install malicious apps, change or delete data, and create new accounts with admin rights!
If you’re running Windows XP SP3 x86, XP Pro SP2 x64, XP Embedded SP3, Server 2003 SP3 x86, Server 2003 x64, or Server 2003 R2, you need to manually download KB 4500331. Head over to Microsoft’s Update Catalog site, select the patch, pick the operating system you’re patching (see Figure 1), and then choose the preferred language. Next, open the downloaded file and run the updating app (Figure 2). If you manage to pick the wrong version, don’t worry — it won’t install, and you’ll get a notification. Finally, you will need to restart your system to have the fix take effect.
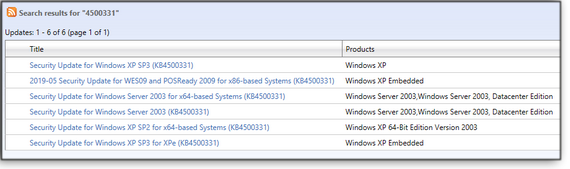
Figure 1. For XP and editions of Server 2003, KB 4500331 must be downloaded from the Microsoft Catalog site.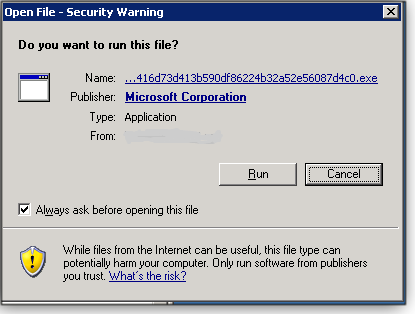
Figure 2. Launch the file downloaded from the MS Update Catalog to install KB 4500331.On Win7, Server 2008, and Server 2008 R2 systems, the patch will be automatically offered via Windows update.
 What to do: If you’re running XP or Win7 systems, you really need to install KB 4500331 as soon as possible — especially if you use Remote Desktop connections.A couple of odds and ends
What to do: If you’re running XP or Win7 systems, you really need to install KB 4500331 as soon as possible — especially if you use Remote Desktop connections.A couple of odds and endsWe were tracking an Internet issue that impacted all Windows versions. As originally noted in a Woody post, May’s patches sorta broke “https” on United Kingdom government websites. Not long after problem was revealed, Microsoft released a fix — but only for Win7 and Win8.1. Then, yesterday (May 19), Woody posted an update that Microsoft now has fixes for all versions of Windows. For example, you’ll see KB 4505056 for Version 1809 and KB 4505064 for Version 1803. Perhaps a tempest in a teapot?
More problems with antivirus apps. In the previous Patch Watch column, I discussed a flaw with April’s updates that hammered Win7 and Win8.1 systems running certain anti-malware products.
Most of the AV vendors posted updates for their products, but Sophos is, apparently, still not out of the woods. A post on the vendor’s community site reported system hangs on Win7 systems that had the May updates installed. Given the threats discussed at the top of the column, that leaves Win7/Sophos users in a quandary.
 What to do: Weigh your options and risks before installing May updates.Windows 10 updates
What to do: Weigh your options and risks before installing May updates.Windows 10 updatesAs I posted on AskWoody.com, I was one of the folks who had their Win10 1809 system abruptly and unexpectedly reboot on May 3. The culprit was KB 4495667. A short time later, I stumbled across Microsoft’s acknowledgment of the issue — which also made me recall Microsoft’s promise of a “heads-up” page listing known problems with various releases. I think you’ll want to bookmark the update status page as a resource for patching issues. For example, we already know that May’s KB 449441 for Win10 1809, has the following quirks.
For businesses:
- Problems using the Preboot Execution Environment (PXE) to start a device from Windows Deployment Services
- File renaming issues on Cluster Shared volumes
For everyone:
- Problems printing from Edge (The workaround is to use another browser!)
- Some updates installed twice, each time with a reboot
I’ve not seen any serious issues yet, but it’s still early days.
May’s Win10 updates include:
The new Windows 10 1903 is already receiving “Retpoline protections” (more info) for the Spectre and Meltdown threats. And for all x64 versions of Windows, Microsoft introduced additional protections for a new subclass of speculative execution side-channel vulnerabilities, also known as Microarchitectural Data Sampling. Previously, these malware-protection enhancements were enabled by default on workstations, but not on servers. May’s updates are automatically enabled on all systems.
By now you should have installed the usual Flash Player update, as noted in a May 14 Adobe security bulletin. Microsoft also released the fix as KB 4497932.
In addition, you’ll see the following servicing-stack updates for all Win10 releases:
 What to do: Install the Flash Player update ASAP, but delay the installation of the rest for a couple of weeks.Windows 8.1/Server 2012 R2 updates
What to do: Install the Flash Player update ASAP, but delay the installation of the rest for a couple of weeks.Windows 8.1/Server 2012 R2 updatesMay patches for Win8.1 also included new protections against speculative execution side-channel vulnerabilities. The patches are:
 What to do: The usual drill: Install the Flash Player fix as soon as possible. There’s also no harm in installing the IE patch sooner rather than later. Put off the others to give Microsoft time to find and fix any significant patch problems.Windows 7 updates
What to do: The usual drill: Install the Flash Player fix as soon as possible. There’s also no harm in installing the IE patch sooner rather than later. Put off the others to give Microsoft time to find and fix any significant patch problems.Windows 7 updatesFor the reasons reported at the top, May’s Win7 updates should be installed immediately. They include:
Once you’ve installed May’s Win7 updates, scan for updates again. If you failed to install the critical SHA-2 patches last month, you should see them offered again — but only after you’ve installed the other updates. Look for KB 4474419 for SHA-2 support and KB 4490628 for the needed servicing stack update.
And if you have Adobe Flash Player install on your Win7 machine, head over to Adobe’s online About page for an update.
 What to do: May is a rare month — install Win7 and Server 2008 R2 patches as soon as possible.Windows Server 2012 updates
What to do: May is a rare month — install Win7 and Server 2008 R2 patches as soon as possible.Windows Server 2012 updatesThis month’s updates include:
 What to do: Test and apply these updates later in the month..NET updates
What to do: Test and apply these updates later in the month..NET updatesMicrosoft has issued the following .NET Framework security updates to combat a new denial-of-service threat:
- 4499406 for Win7 SP1 and Server 2008 R2 SP – .NET 3.5.1, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2, 4.8
- 4498961 for Win7 SP1 and Server 2008 R2 SP1 – .NET 3.5.1, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2, 4.8
- 4499407 for Server 2012 – .NET 3.5, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2, 4.8
- 4499408 for Windows 8.1, RT 8.1, and Server 2012 R2 – .NET 3.5, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2, 4.8
- 4498963 for Windows 8.1 and Server 2012 R2 – .NET 3.5, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2, 4.8
This is the first time we’ll see separate, cumulative .NET 4.8 security updates for the various Windows 10 releases. They include:
 What to do: Delay installing these .NET Framework updates.Office security updates
What to do: Delay installing these .NET Framework updates.Office security updatesMay has the usual mix of Office security fixes, feature enhancements, and Japanese-era bugs. The security patches, released May 14, focus primarily on a remote-code-execution vulnerability. The typical set of feature enhancements and non-security fixes was released May 7.
Security updates:
Office 2016
Office 2013
- 4464561 – Office
Office 2010
- 4464567 – Office
Feature updates and fixes
Office 2016
- 2920717 – Office; crashes with Korean proofing tools
- 4461441 – Office; synchronization error with OneNote
- 4461477 – Office; performance problem
- 4462113 – Visio; naming issue in Explorer
- 4462119 – Office, Japanese-era information
- 4464538 – Office; Japanese proofing fixes
- 4462243 – Office; Japanese era
- 4464532 – Skype for Business; various fixes
- 4464533 – PowerPoint; linking error with Excel
- 4464540 – Outlook; various fixes
- 4464541 – Project; various fixes
- 4464550 – Excel; crashes and other issues
- 4464552 – Office, OneNote synchronization
Office 2013
Office 2010
- 4464524 – Office; crashes and image blocking
 What to do: At this point, there are no reports of problems with these updates. Still, unless you need a specific fix, there’s no rush to install these Office updates.
What to do: At this point, there are no reports of problems with these updates. Still, unless you need a specific fix, there’s no rush to install these Office updates.Questions or comments? Feedback for this article is always welcome in the AskWoody Lounge! In real life, Susan Bradley is a Microsoft Security MVP and IT wrangler at a California accounting firm, where she manages a fleet of servers, virtual machines, workstations, iPhones, and other digital devices. She also does forensic investigations of computer systems for the firm.
Best Utilities
Freeware Spotlight — SwiftSearch By Deanna McElveen
By Deanna McElveenMy favorite freeware finds are the programs that make you say, “How can this be possible?”
SwiftSearch by “wfunction,” a developer on SourceForge, is one of those programs. Both the 32-bit and 64-bit versions are completely portable — just click the .exe file, and the program loads instantly.
You’ve undoubtedly used Windows’ or third-party search programs. They typically index everything, which can seemingly take forever. They can also be quite the resource hog: they’re constantly updating the index, forcing the hard drive to thrash away. It kind of defeats the purpose of fast searching, if you have a slower machine.
SwiftSearch does things completely differently. It bypasses the file system and goes straight for the hard drive’s file directory. It also supports path-based searches and regular expressions (see the program’s help file for simple cheat sheets on using these searches).
After SwiftSearch opens, you start by selecting a drive to search (see Figure 1). It must be a local drive — not one mapped to another computer or server. The reason? A mapped drive’s file directory isn’t on your computer, it’s on the remote machine.
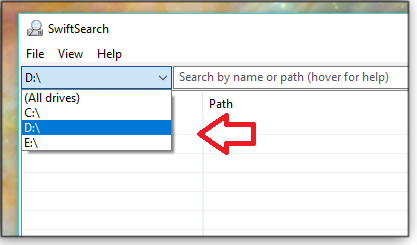
Figure 1. Start a SwiftSearch task by selecting a local drive.Once the drive has been selected, you can just enter something to search for — or narrow the search by selecting a particular folder (see Figure 2).
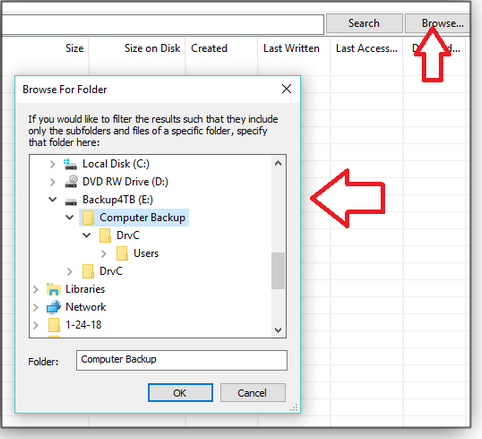
Figure 2. Use the Browse For Folder option to focus a search.SwiftSearch allows the use of an asterisk (“*“) for wild cards in the search string. For example, entering Users\**\* will find every file in the “Users” folder.
Figure 3 shows an example of a search that looks for all .zip files on my backup drive that are in the Computer Backup folder.
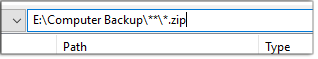
Figure 3. Looking for ZIP files in a specific folder on a backup drive.Once I’ve entered the search parameters, I hit the Search button. And this is where I say: “How’s this possible?” The program found nearly 300,000 ZIP files in under a second! (See Figure 4.)

Figure 4. The results of my sample search show just how fast SwiftSearch works.No more going for coffee while Windows tries to find something. There are plenty of other tools in SwiftSearch to explore, from the way the program displays searches (Figure 5) to different ways to get really focused results (Figure 6).
Figure 5. Add gridlines to the search display.
Figure 6. Look for more advanced search tools under the Help tab.The program will run on any version of Windows that has an NTFS file system. Don’t worry: your computer most likely uses NTFS, and the program will tell you if it doesn’t.
SwiftSearch is free. Download either the 32bit or 64bit version from the OlderGeeks.com website and give it a whirl.
Questions or comments? Feedback for this article is always welcome in the AskWoody Lounge! Deanna and Randy McElveen are celebrating 20 years in the computer business, seven years running OlderGeeks.com and 26 years of putting up with each other. Their computer store is in a small town in the Missouri Ozarks. Believing that happy customers are always the best advertisement, they hope to do it for another 20 years.
WEB SECURITY
Secure your website accounts with Microsoft’s Authenticator By Lance Whitney
By Lance WhitneyUsing two-factor authentication can significantly boost your security on sensitive websites.
Microsoft’s Authenticator app helps you sign in to Microsoft websites more securely — and to some third-party sites, too. Here’s how.
You most likely use a Microsoft Account to sign in to Windows and also to access various Microsoft sites and services. Securing that account with alternative forms of authentication — such as PIN, fingerprint, and two-factor verification — adds extra levels of convenience and security. That’s an important consideration in these days of phishing attacks, hacked corporate websites, and other digital mayhem.
Undoubtedly, at one time or another, you’ve been asked to use your smartphone as yet another form of authentication — typically in the form of one-time, text message–based PINs. Authenticator is Microsoft’s phone-based verification system, and it’s available for iOS, Apple Watch, and Android devices.
When you sign in to a Microsoft site, one of the options is to use the Authenticator app. Click the option, and a notification pops up on your phone with a selection of numbers. Press the one that’s displayed on the site, and you’re quickly and easily verified. The app can also be combined with traditional forms of authentication for more secure, two-factor verification.
Authenticator can also be added as an option for two-factor verification with non-Microsoft websites and accounts. You can, for example, use it with Google, Facebook, Amazon, and other sites that support authenticator apps.
To start using Authenticator, download it from the App Store for your iPhone or iPad, or from Google Play for Android devices. For the most part, the app works the same on either platform.
Next, open the app on your device. In iOS, you may be asked whether you want Authenticator to send you notifications. Allow them — that’ll let you respond to sign-in messages without having to open the app. Again, there are slight variations between iOS and Android, but the next major steps are these:
Add your first account — I recommend starting with your Microsoft account because that’s probably what you’ll access most often with the app. Tap the add account button (a “+” sign for iOS or three dots for Android) and choose whether your Microsoft account is personal, for work, or for school (see Figure 1, left panel). Enter your ID (username, phone number, or Skype name; Figure 1, center panel) and, on the next screen, tap in your password. You may be asked to verify your identity, which you can do via text or email (Figure 1, right panel).
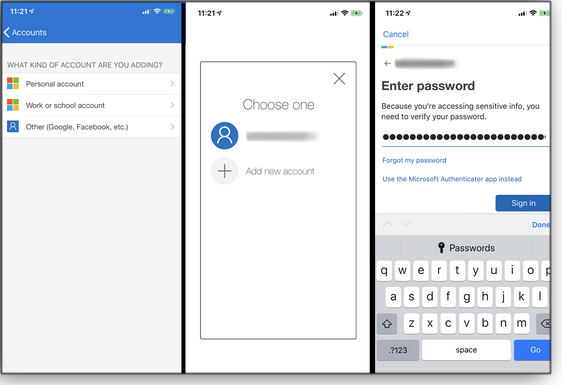
Figure 1. Creating a new account in Microsoft’s Authenticator takes just three simple steps: selecting the account type, entering a specific account, and verifying it with a password.Now, let’s try the app in action. Browse to a Microsoft website, such as the page for managing your MS account. Click the Sign in button and enter your email address if needed. Click Next. At the password window, click the link to Use the Microsoft Authenticator app instead (see Figure 2).

Figure 2. At the password sign-in window, click the link that takes you to the Authenticator-based sign-in page.The next window will prompt you to check your phone for an approval notification (Figure 3, right panel). You should immediately receive the notification on your phone, via the Authenticator app. Tap Approve (Figure 3, left panel). You might then be asked to verify your identity on your phone via Face ID, fingerprint recognition, or PIN. You’re now signed in to the website.

Figure 3. Selecting the Authenticator option on your PC (right panel) sends a request for sign-in approval on your phone (left panel).Now, let’s try the app with a non-Microsoft site. The catch here is that you won’t receive a notification; you must open the app to grab an authentication code. Note that for third-party sites such as Facebook, Google, and Amazon, Authenticator doesn’t make sign-in easier — it just adds two-factor verification for better security.
First, browse to the site you want to add. Let’s use Facebook for this example. On your PC, sign in to Facebook with your standard username and password. Click on the down arrow on the right side of the toolbar and select Settings. Next, select Security and Login in the left column and then click the Edit button for Use two-factor authentication (see Figure 4).
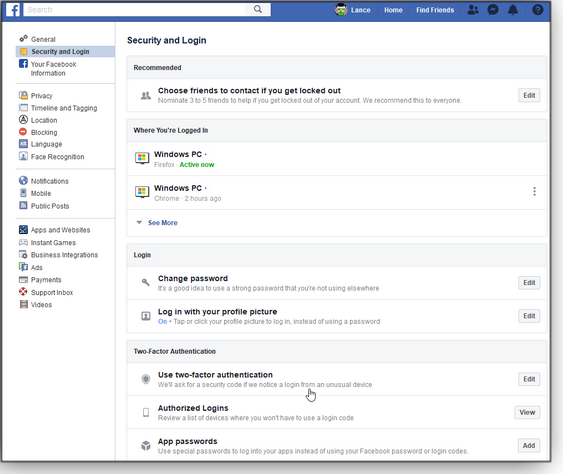
Figure 4. To set up Authenticator sign-ins for Facebook requires enabling two-factor authentication.Click the Get Started button, then check the radio button for Authentication App. Now, back on your phone, open the Microsoft Authenticator app. Tap the “+” or three-dot icon and select the option to Add account. At the next screen, tap the option for Other (Google, Facebook, etc.). Aim your phone’s camera at the QR code displayed on your PC (see Figure 5). Click Next. The app then displays a six-digit code for Facebook. Type the code into the appropriate field on the Facebook page. Click Verify and then Finish. The app is now set up for Facebook.
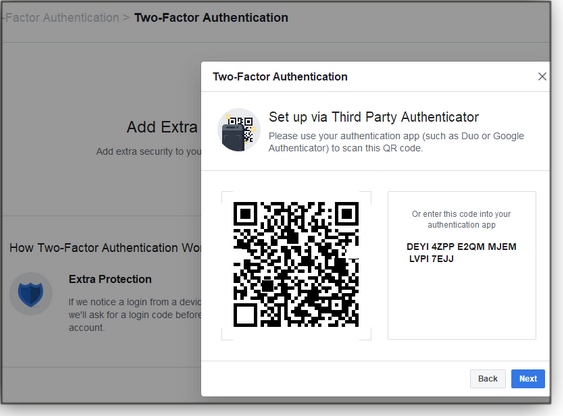
Figure 5. Authenticator can add two-factor verification for non-Microsoft sites. Setup requires scanning a QR code with your phone.To test it, sign in to Facebook on a different computer or device. Open the Microsoft Authenticator app and, on your PC, enter the six-digit code displayed for Facebook. After verification, you can choose the option Save Browser to avoid entering the code on that device in the future.
You can add other sites such as Google, Twitter, LinkedIn, and Amazon. The process is the same; you just need to find the setting for two-factor authentication for each site.
Finally, Apple Watch owners can also use the Microsoft Authenticator, though the app supports only Microsoft websites. For non-Microsoft sites, you’ll still need to use your phone or tablet to authenticate the sign-in. To learn more, check out the Microsoft Authenticator app FAQ.
Questions or comments? Feedback on this article is always welcome in the AskWoody Lounge! Lance Whitney is a freelance technology reporter and former IT professional. He’s written for CNET, TechRepublic, PC Magazine, and other publications. He’s authored a book on Windows and another about LinkedIn.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2019 AskWoody LLC, All rights reserved.
- “For the past several days, my laptop has not been able to fully back up my files. I get the error message:


