-
Another patching debacle — how we got here
ISSUE 16.30.0 • 2019-08-26
 The AskWoody Plus Newsletter
The AskWoody Plus Newsletter
In this issue
WOODY’S WINDOWS WATCH: Another patching debacle — how we got here
BEST OF THE LOUNGE Keeping on top of the DejaBlue threat
LANGALIST: Spotting fakery in system specs
DROLL TALES: LABS: Can’t connect to the server
ON SECURITY: Options for secure remote access
SMALL BUSINESS COMPUTING: What does digital transformation mean for small business?
WOODY’S WINDOWS WATCH
Another patching debacle — how we got here
By Woody Leonhard
Frantic moves to fix this month’s Windows-update bugs highlight the dark underbelly of Microsoft’s patching strategy.
August patches have been flying around like salmon in Seattle’s Pike Place Market. Now that the major bugs are fixed — for the most part — it’s time to look at what happened and speculate on whether this type of debacle can be avoided in the future.
Here’s the short version of events.
August patches go out: On Patch Tuesday, Microsoft released its usual round of updates for all current versions of Windows — from Win7 onward. At the same time, we were warned to install the patches quickly, due to a just-announced security hole colloquially called DejaBlue (more info).
DejaBlue is a mean exploit in the BlueKeep mold. Both take advantage of a security hole in Microsoft’s Remote Desktop Services (RDS). And as with BlueKeep (patched in May), DejaBlue is “wormable” — once an infection takes hold, it can move from machine to unprotected machine.
Fortunately, there are no known infections in the wild that use either variant — at this time. However, it’s a given that they will appear, sooner or later.
So getting patched relatively quickly was a very good idea, especially if you used Microsoft’s remote-access service. And then we went down the rabbit hole.
VBA takes a hit: Two days after Patch Tuesday, Microsoft warned that all August Windows updates could cause failures with programs based on Visual Basic, Visual Basic for Applications, and VBScript. When using a VB/VBA application (many of you are, even if you don’t know it!), under certain circumstances the app will stop working and put up an inscrutable “invalid procedure call error” notice.
You had two choices:
- Protect your Windows system against DejaBlue.
- Reliably use your VB, VBA and VBScript programs.
It was an either/or decision; there was no middle ground.
Over on Twitter, @MalwareTechBlog (Marcus Hutchins, whom you may recognize as the guy who single-handedly shut down WannaCry) posted a legitimate — if somewhat naive — suggestion.
“I do wonder if the number of people who patch against major Windows vulnerabilities would increase if Microsoft provided an individual application patch for major vulnerabilities.
“Security patches alter lots of different Windows components, which can lead to all kinds of unforeseen system-breaking bugs. In cases like EternalBlue and BlueKeep, it might be nice to have an option to patch just the affected components.
“I’m not saying split patches up into individual components …. Just keep cumulative updates [and] offer a standalone patch for wormable vulnerabilities.”
The response from Microsoft employees was clear. Here’s one of many contrarian opinions:
“It increases the support cost a lot. Because now each [subsequent] patch has to take into account the combinations that may or may not have been installed before. It is horrible.”
The problem, of course, is that Microsoft is right. Grouping together patches — a process I called “the patchocalypse” (InfoWorld) when it arrived on the scene three years ago — is a Frankenstein-like solution to an intractable and congenital dilemma.
Back in the not-so-good old days, when we had only a few patches every month, both Microsoft and its customers could step through the minefields, picking and choosing what to fix and what to ignore. But as the volume of patches increased, that kind of granular specificity just wasn’t feasible any more. With the advent of Windows 10, Microsoft didn’t even try.
So now we’re left with monolithic, take-it-or-leave-it updates. And given the questionable quality of the patches we’re seeing these days, the issues just seem to get worse and worse. (I keep a log of patching problems over the past two years on Computerworld’s site.)
I’ve reported on Windows updating for years, and I can’t offer a solution. Keeping patches bundled isn’t viable. Breaking them apart isn’t viable, either. My best advice is one I’ve given many times: defer patching each month for at least 14 days — and let’s see what happens to Microsoft’s unpaid beta testers.
The best solution: Microsoft could just, you know, thoroughly test the patches before they’re released.
Questions? Comments? Thinly veiled prognostications of impending doom? Join the discussion about this article on the AskWoody Lounge. Bring your sense of humor. Eponymous factotum Woody Leonhard writes lots of books about Windows and Office, creates the Woody on Windows columns for Computerworld, and raises copious red flags in sporadic AskWoody Plus Alerts.
Best of the Lounge
Keeping on top of the DejaBlue threatFlaws in Windows’ Remote Desktop Services might be keeping some IT pros up at night. But our own MVP and security guru Susan Bradley sheds some much-needed light on the subject in a CIO podcast.
If you’re looking for help with alternatives to the related Remote Desktop Protocol (RDP), head over to a recent AskWoody post and click the podcast link. Susan shows Windows Pro users how to avoid using RDP — or having it used against them.
Staying Connected
AskWoody Lounger bmeacham was seeking help. His link to the Web kept dropping, and he couldn’t work out a solution. Fortunately, with lots of help from fellow Loungers, he thinks he’s found the fix.
TROUBLESHOOTING
Plus member Southieguy reported that VBScript no longer runs on his Windows 7 machine — apparently for the past several months. Could it be the August Win7 update? Or is it a conflict with his antivirus software?
RECYCLING WINDOWS
WSjsachs177 wants to know if all “cheap” copies of Windows are counterfeit. Lounge members voice their opinions, but WSjsachs177 doesn’t get the looked-for answer.
Maintenance
Lysdexic is finding it impossible to add and remove items in his context menus. Loungers offer suggestions; feel free to add your favorite solution.
TROUBLESHOOTING
Lounger DaveYVR tried running chkdsk on an external, 8TB drive that’s connected to his Win7 laptop. But the process took a l-o-n-g time to complete. Along the way, Dave wondered whether he should pull the plug on the drive and try again. Fellow Loungers offered suggestions — and welcomed the eventual good news.
Fun Stuff
Plus Member MrJimPhelps talks Ford Mustangs — specifically the 2019 Bullitt. That prompts a discussion about muscle-car competitors and fun versus practicality.
If you’re not already a Lounge member, use the quick registration form to sign up for free.
LANGALIST
Spotting fakery in system specs
By Fred Langa
We all assume that Windows’ built-in System Information and Device specifications applets are reporting a PC’s true specs.
And under normal circumstances they do; but, surprisingly, simple hacks can make those tools display totally bogus information.
Plus: What you should know about safely repurposing a former boot drive in a new machine.
Can he trust his PC’s reported specs?I bet there’s a fascinating backstory behind David M.‘s question:
- “Can someone fake the stats of a computer, so that when you open up the ‘device specifications’ it shows more CPU, RAM, and other specs than it actually has?
Yes, and it’s amazingly easily!
For example, as a test, I manually faked some hardware specs on my personal-use PC. It took all of about 60 seconds — and some of that time was reading the instructions. (I’d never done it before.)
Figures 1 and 2 are screen shots taken from my PC’s System Information and Device Specifications (Settings/System/About/) screens.
Check out the highlighted “Processor” item in each figure. Notice anything unusual?

Figure 1: Ahem. The “Intel Core i15” doesn’t exist — at least not yet; and no standard PC CPU can run anywhere near 9.80GHz.
Figure 2: This might look like legitimate processor data, but it’s utterly bogus — the result of an extremely simple hack.You might be shocked to know that it’s ridiculously easy to make a PC’s processor appear to be anything you want. Here’s how.
Open Windows’ registry editor (type regedit into the search box). With the editor open, look for the Computer heading in the left pane and then navigate to:
\HKEY_LOCAL_MACHINE\HARDWARE\DESCRIPTION\System\CentralProcessor
Next, click the Central Processor’s topmost category from the list — it’s usually “0” or “1.” In the right-hand pane (and as shown in Figure 3), right-click ProcessorNameString, select Modify, and type in whatever processor name you like into the Value data text-entry box. It can be literally any name that strikes your fancy. Click OK to save your changes.
With that one simple change, I created a completely bogus processor name — which Windows then displayed in hardware-spec screens, everywhere on my system.

Figure 3. Whatever text you enter as the value for ProcessorNameString will appear throughout Windows as your CPU’s current designation.If this looks like a serious issue, it’s not: the change is superficial and temporary. Plain-text strings entered into the registry — such as ProcessorNameString — are mostly used as inert, non-operational labels or descriptors. So they can usually be changed without messing up Windows or your apps. Moreover, any changes you make will be automatically corrected at the next reboot!
That’s one very simple example of potential fakery. Other methods include apps that pretend to probe your system (the screen may flash, for example) and then display bogus specs provided by the software. There are also fake hardware-identification apps that mimic the look and feel of legitimate apps.
You get the idea: If all you’re talking about is changing labels or displaying bogus specs, it’s actually rather easy to fool an unsuspecting person.
On the other hand, it’s very hard to fool an operating system or good diagnostic software — and for good reasons.
For a PC to function properly, the OS, drivers, and apps all have to know what hardware resources are actually available — and not what some arbitrary text strings in the registry might claim. Otherwise, you’d have mayhem.
Imagine, for example, if an OS tried to write data to a bank of RAM that doesn’t actually exist!
To truly deceive a fully functioning OS or hardware-probing app, you’d need an elaborate level of virtualization or hardware abstraction to mediate and translate between the claimed fake specs and the actual available hardware. I doubt the deception would survive any but the most cursory scrutinies.
And why on earth would you do that anyway? Again, I’d love to know the backstory behind David’s question!
So, yes, it’s easy to produce a faked data display that can fool a casual observer — at least for a short while. But no, it’s not at all easy to fool low-level software — or a savvy user!
If you suspect that something’s wrong with a hardware spec you’re seeing, reboot the PC, then install and run several different and freshly downloaded hardware-probing apps. The free and classic CPU-Z is a good example; AlternativeTo.net lists many others.
Odds are, apps like those will immediately see through any shenanigans and tell you what’s really inside the box!
Safely repurposing a former boot drive, in-placeWriting from San Diego, AskWoody subscriber DJTooley wonders if reusing an old, internal boot drive (with a drive letter already assigned) will mess up his new setup.
- “Good morning, Mr. Langa! Have followed you for at least 10+ years.
“When my previous tower PC died (video system problem), I plugged its hard drive into an empty drive bay in the new computer. I then successfully extracted all the info I wanted from the old drive.
“Here’s my question: Can I reformat that previous drive while it’s still installed in the new computer — with its already-assigned drive letter and backup-drive section letter — without destroying any information on the ‘new’ hard drive and backup drive sections?
“I have been very, very wary of just ‘doing it.’ Thanks for your response.”
You’ve already done the hard part!
You’ve successfully removed the drive from the old PC; installed, connected, and accessed it in the new system; and extracted the data you needed from it. You’re in excellent shape to proceed!
All that’s left is to verify that nothing’s using any software or files on the old drive. When you’re sure the drive is 100 percent passive, have at it — reformat, repartition, data-wipe, whatever! Your changes should have no effect on the other drives on the system.
If you’re not completely sure that the drive is unused, there’s an easy way to find out.
First, make a just-in-case backup. Next, power down the PC, open the case, and unplug (physically disconnect) the old drive’s power and data cables. Restart the PC and put it through all its paces with the old drive disconnected.
Check to see that everything still works OK with the drive deactivated — including any out-of-sight, automated software that might make non-obvious use of the drive (e.g., backups, File History, and so forth).
If you discover that something breaks or fails to run properly with the old drive deactivated, you can alter that task or app to work on a different drive.
When you’re sure the old drive isn’t actively being used for anything, you’re clear to reconnect and repurpose it in any way you wish.
If you leave the old drive in the new PC, connected to the same physical ports/interfaces, its post-reformat drive-letter assignment should stay the same as before. You can leave it as is or change it to any unassigned letter you wish.
Need a tool? There are many available for download. But this is an easy task, well within the capabilities of Windows’ built-in Disk Management tool. (See Figure 4.)
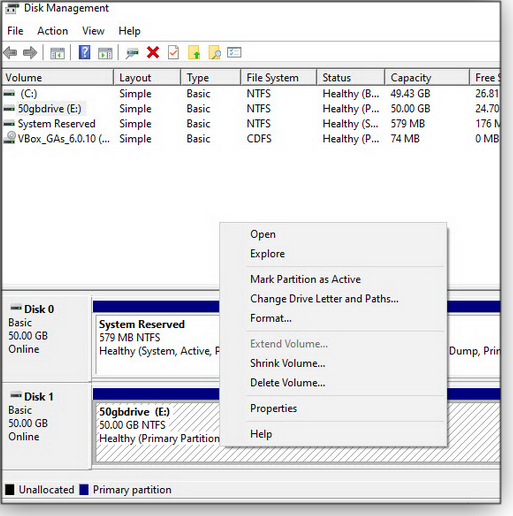
Figure 4. Right-click on any drive or partition in Windows’ built-in Disk Management tool to perform a variety of routine drive/partition alterations.So, sure: Once you’re certain nothing’s using the old drive, and you’re sure you don’t need any of its data, fire up the Disk Management app and have at it!
For more info, here’s official Microsoft support information on the Disk Management snap-in tool and its functions:
- Overview of Disk Management
- Help in Disk Management
- How to use the Disk Management Snap-in … (older info, but still applies)
Send your questions and topic suggestions to Fred at fred@askwoody.com. Feedback on this article is always welcome in the AskWoody Lounge! Fred Langa has been writing about tech — and, specifically, about personal computing — for as long as there have been PCs. And he is one of the founding members of the original Windows Secrets newsletter. Check out Langa.com for all Fred’s current projects.
DROLL TALES
LABSBy Aaron Uglum

On Security
Options for secure remote access
By Susan Bradley
Do you regularly use some form of Microsoft remote-access technology?
If so, you’re probably wondering how to manage the transition from on-premises to in-the-cloud versions.
But that’s putting the cart before the horse. It might be tempting to go straight to the cloud, but simply moving the tools you currently use to a cloud-based virtual machine can be the most expensive and least efficient way to change technologies. Before you jump to a cloud solution, you should first assess your actual remote-access needs.
If you’ve relied on Remote Web Workplace or Remote Web Access (RWA), included with Small Business Server, you have a couple of good remote-access options, going forward. (RWA provided an easy and secure path for anyone out of the office to link back into their on-site workstation.) But you (or your IT consultant) should start looking at those options soon, because support for Small Business Server 2011 ends this coming January (2020). Here are some considerations:
Local versus onlineTo start, do you really need to provide remote access to local workstations? In this era of cloud technologies, many small-business applications can be accessed directly through the Web. With QuickBooks Online, for example, you might not need access to a desktop-based copy.
You will, however, need to confirm that an online edition will fulfill your needs. Web-based apps are often less capable than their workstation siblings. You might be able to comfortably adapt your workflow — or not. Having worked with both versions of QuickBooks, I can assure you that — though they’re similar — there are some significant differences, too. In my experience, users tend to stick with the desktop edition when they’ve added inventory modules or other add-ins that increase the platform’s complexity.
On the other hand, QuickBooks Online may be a better fit if you don’t have regular access to a desktop or laptop. You can quickly sign in to your QuickBooks account via a tablet or smartphone. (I know of folks who claim they haven’t used a Windows PC in years — they rely exclusively on iPads and phones.) So there’s the classic compromise: features versus mobility.
More remote-access considerationsNext, how many people in the company really need remote access to their workstations? Do you have, say, a mobile sales force that numbers in the dozens? Or is remote access needed by just one or two employees? If it’s the latter, consider simpler and less expensive solutions such as single-user copies of GoToMyPC, LogMeIn, Splashtop, or TeamViewer.
Also, how important are features such as remote printing? For some workers, it might be critical — for others, the ability to print to PDF might be enough.
If your business uses an IT professional/consultant, give them a shout; they might have a solution for you via the tools they use to remotely control and manage your systems.
Local solutions for multiple usersIn settings with fairly broad remote-access needs, you may still want an on-premises, server-based solution — one based on the same underlying technology as Remote Web Access. For example, enable an RD Gateway (more info) on a newer Windows Server version and purchase a client-access license (CALs; more info) for each user that needs remote access.
This setup hides systems and their Remote Desktop Protocol (RDP) sessions from the Web, tucking them behind authentication and using the more-secure port 443 instead of port 3389. (The client machines using Remote Desktop Connection will also have to be configured for RD Gateway via the advanced options.)
A TurboFuture article has a good tutorial for setting up RD Gateway on Server 2016.
Microsoft has a new offering that includes remote-access services — Windows Virtual Desktop (WVD), on Azure. But it appears to be an enterprise solution — not suitable for typical small businesses. For example, your business-software vendors will have to support WVD, and I assume they’d rather promote their own solutions. Moreover, we still don’t know the price for WVD service.
(On the other hand, if you subscribe to Virtual Desktop on Azure, you’ll get extended security support for the soon-to-expire Windows 7 plus help transitioning to Windows 10. We’ll have to see whether Microsoft makes WVD financially feasible for small-to-medium businesses.)
Note: If you (or your IT consultant) are considering placing your line-of-business (LoB) apps in an Azure virtual machine and setting up remote desktops to access the data, it probably won’t work. The LoB software we’ve used for years was written to use traditional file-sharing methodologies. In other words, many of these applications need Server Message Block Version 1 (Wikipedia info) and other older technologies that aren’t supported in cloud offerings.
The clock is ticking down on Small Business Server 2011 and its built-in remote-access options. But you still have time to carefully assess our remote-access needs — taking into account complexity, legacy support, mobility, and cost — and implement the best solution for you. But start now!
Questions or comments? Feedback on this article is always welcome in the AskWoody Lounge! In real life, Susan Bradley is a Microsoft Security MVP and IT wrangler at a California accounting firm, where she manages a fleet of servers, virtual machines, workstations, iPhones, and other digital devices. She also does forensic investigations of computer systems for the firm.
SMALL BUSINESS COMPUTING
What does digital transformation mean for small business?
By Amy Babinchak
While attending a recent conference, I sat in on a session about digital transformation. But it proved disappointing — the speaker’s discussion was limited to moving local servers into a data center.
That’s not what digital transformation means. Digital transformation is about modernizing your business processes for better customer experiences and improving productivity. When boiled down to its essence, a digital makeover is about taking an old business and making it new again.
Any business that’s been around for a while has developed its own particular way of doing things. Employees get comfortable with those established practices and stick to them, often to the point of resisting any significant changes. But like the office carpeting, set practices get threadbare over time and need to be refreshed. Digital transformation is how that refreshing process gets done.
What’s driving the digital transformation?There’s a lot of buzz about digital transformation in the business press. Small-business owners might well ask, why? More specifically, what’s driving this need for businesses to modernize?
It’s the Internet, of course. The Web has now been around longer than many small businesses. But small-business owners are only now starting to understand the service aspect of the Net.
Today’s customers have well-developed expectations about their online experience. Most assume they can go online and at least place an order — or, if the business has an in-person sales process, that ordering will proceed from person to digital quickly and efficiently. Customers want to be able to go online and get the status of their purchase, to access information about their account, and to receive their purchase within a couple of days.
This change isn’t just about buying a product. Customers’ online expectations extend to many types of services — even legal and accounting. In short: They want a modern online delivery experience, regardless of whether it’s physical goods or services. They also want it fast, and they want it friendly.
Odds are, if your business isn’t relatively new, it needs a digital makeover in order to meet current customer expectations. And keep this in mind: if your competition hasn’t completed their digital transition, they very well might soon.
Here are some signs that your business needs a digital upgrade:
- You run on paper forms and everything goes into filing cabinets.
- Your website hasn’t changed in more than five years.
- Any mention of change makes your employees cringe.
- New software is looked upon with scorn.
- Your sales process still requires slow, manual steps. (Let’s see, where did my pen go?)
Starting from the insideI’ve mentioned that a digital transformation is all about the customer experience. But the above list is mostly about the internal functions of the business. In truth, a digital transformation begins from within.
Before you can present a modern online image to customers, you have to update and automate daily business processes. “Modern” is not providing an amazing online purchasing experience — then printing out the order and hand-delivering it to the piled-high inbox on someone’s desk. Customers won’t see that initial internal inefficiency, but they’ll certainly feel it later when the order process proceeds slowly offline.
On the service side, imagine the impression customers are left with when they, for example, schedule appointments online — then arrive at the business and are met by someone with an ancient CRT monitor and a stack of papers to fill out. Developing an attractive and intuitive external, digital experience while neglecting the back-end processes is putting the shopping cart in front of your old-mare processes.
Modernizing the paper trailAll businesses still have some level of paperwork — and as far as I can tell, they always will. But the more you rely on paper, the more you need that digital makeover. Papers end up in piles and sometimes get lost. Papers ask for duplicate information. Who isn’t annoyed when the receptionist at the doctor’s office hands you a clipboard of forms and a pen (usually out of ink) with a big plastic flower on top? And it seems that every form starts out by asking for your name and contact information.
Not only can digital records be located and retrieved quickly, they can also be referenced and collated so customers are not forced to give the same information over and over again.
Today’s digital forms are easy to create, and once your staff becomes comfortable building and using electronic forms, they’ll find ways to automate other tasks.
As small-business consultants, our most common request from management is to automate the hiring process — more specifically, to develop a process that notifies everyone in the company of a new hire. The managers we talk to are tired of running around in a panic, locating a desk, a computer, insurance forms, payroll forms, a cell phone, a hard hat, etc., all because they just found out that someone new is starting work — today! (It doesn’t give that new hire a great first-day experience, either.)
Putting on our Microsoft 365–consultant hats, we solve this problem with a digital workflow process — typically combining the applications Forms, Flow, and sometimes Excel and SharePoint, too.
Building staff confidenceJust as it’s not enough to buy a pretty website and ignore the back end, it’s also inefficient — even destructive — to purchase new software and not invest in thorough staff training. Lots of businesses, small and large, have acquired expensive cloud applications — only to complain that they didn’t get their money’s worth. Why? Mostly because the staff had had inadequate training and did not use the new features. To these business owners, new software is just an expense — not an investment in the future of the company.
Just knowing how to use a mouse and type on a keyboard is no longer sufficient. Training gives employees the confidence to approach software with interest and curiosity — and possibly find new ways to improve business processes. That kind of innovation adds to the bottom line, too.
Not all changes will be big. In fact, most of them will be small. But taken together, they’ll add up into the final digital transformation of the business. For example, I recently found a spreadsheet attached to an outdated business process. The process required that tabs in the spreadsheet be separated into their own files, once the monthly data-collection process was complete. That task took about two hours. By automating the separation process, we reduced the time to around 15 minutes — a small but ultimately significant change. If you’ve always done something one way, it’s likely that there’s now a better, more efficient way to do it.
And the cost for making digital transitions can be relatively low. Saving three hours of a lower-salaried employee’s time (less than hour for a mid-level employee) each month can pay for an entire Microsoft 365 infrastructure.
I have a saying: If your IT investment isn’t making you money, you’re doing it wrong. When we look at aged business processes, finding that missing money is easy.
Developing digital-makeover teamsAnother aspect of a digital transformation is enhancing ad-hoc teams. In a typical business, short-term, informal teams come together to work on a particular task. For example, we see this often in distribution and sales organizations. The people on the front line need people behind the scenes, and an informal team comes together to get the deal done, the service delivered, or the project completed. The team then disbands to focus on the next big thing.
We commonly see two team-related failures in old-style business practices: no teams of any kind, or formal and static teams that don’t always have the right people for a particular project. Either can result in a less-than-positive customer experience.
Effective businesses let employees build teams as needed, and managers provide the software tools that will make those teams productive.
One of my clients recently redesigned their office to have small meeting rooms to accommodate ad-hoc teams. Previously, they had one large conference room that was always reserved for management meetings — or it was used for departmental gatherings, where information was delivered in a top-down style. The new “huddle rooms” enabled small, quick meetings by temporary teams.
We have helped enhance these smaller, short-term teams by implementing Microsoft Teams within Microsoft 365. Employee training allows companies to build and tear down ad-hoc groups as necessary, while IT ensures that important data gets backed up and secured, and also manages more permanent teams.
Leading the transitionIn order to modernize paper, give confidence to employees, and develop teams, companies need leaders who will champion the digital transformation. If it’s not the CEO or president, then it should be someone close to that level: someone who has the authority to freely work across all departments and present a consistent message about the coming changes — and who can reward departments and individuals for embracing the makeover.
Digital-transformation leaders need to be early technology adopters and advocates in order to inspire those around them. Most important, implementing a successful internal digital transformation will naturally be reflected on the outside, too.
Questions or comments? Feedback on this article is always welcome in the AskWoody Lounge! Amy Babinchak is the owner of three IT-related businesses: Harbor Computer Services, Third Tier, and Sell My MSP. She has been working in the IT field with small and medium businesses for more than 20 years. She’s also a Microsoft MVP and has received numerous leadership awards.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2019 AskWoody LLC, All rights reserved.


