-
Tip for the weekend – scanning for Log4j vulnerabilities
I wrote about this the other day in the newsletter to check your computer for the Log4j2 vulnerability. So far the good news is that I’ve not seen active attacks in consumer computers, but I have seen vendors taking action to patch their software in business software. Now comes word that the Federal Trade Commission is reaching out to warn vendors to step up and ensure that their software is patched.
While I don’t see this as an issue for consumers, it’s still a concern for those of us in small businesses, as we don’t have the power to demand stuff from our vendors. For us, it is what it is.
I’ve found a tool that does a better job of identifying if your system has vulnerable code. It’s from Qualys and can be downloaded here.
You download the zip file, extract it. Now open up a command window, right mouse click to run as admin and leave it open. (watch the video for a demonstration)
Get yourself to where you downloaded the file (this is often the tricky part) and then run the command log4jscanner.exe
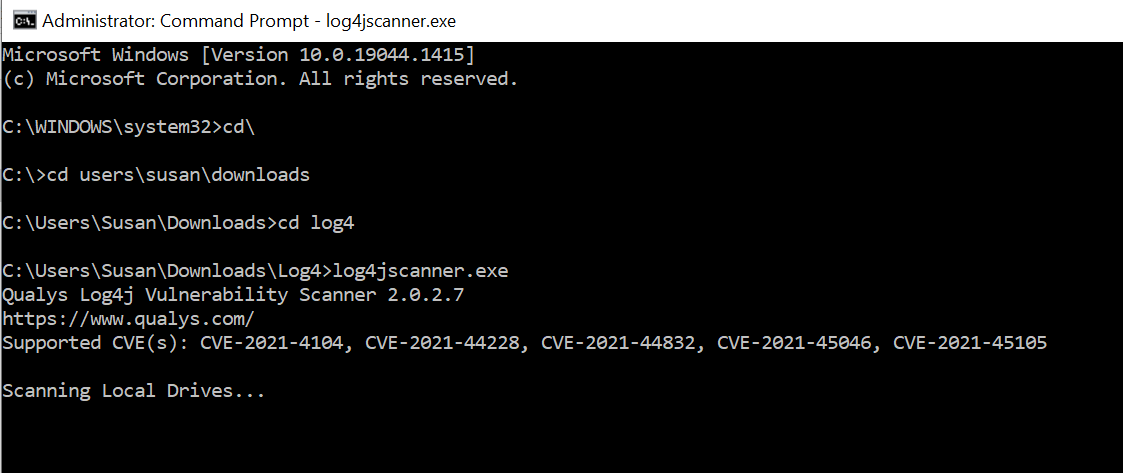
Now wait for it to scan your drives. This may take some time. On my laptop it found nothing on the drive. On my machine that I am typing this up from, it found some old files on my spare E drive. I can remove them with no issues. But on my office computers, it found files on some line of business vendor software that I use.
So now what? It’s active software so I can’t uninstall it. But keep in mind that the attacker has to get on to your system first, unlike the cloud vendors I don’t have the vulnerable software exposed directly to the web. So they have to get on my system first. And that means to me that they can nail me lots of OTHER ways first. So while I am going to reach out to my vendor, I’m not panicking. But it is interesting to see how the FTC is getting into the act of pushing our vendors to get better.
So if you are a small business tech person like me? Check your computers to see what vendors you need to push.

