Using a Dell device? you may want to read this article:
Vulnerable Dell driver puts hundreds of millions of systems at risk
Five flaws in one
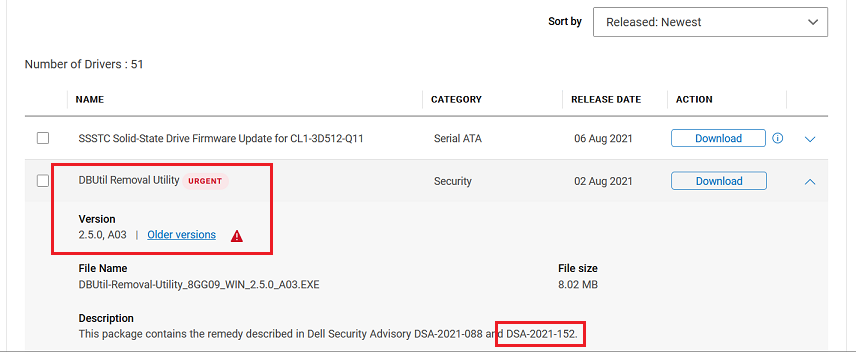
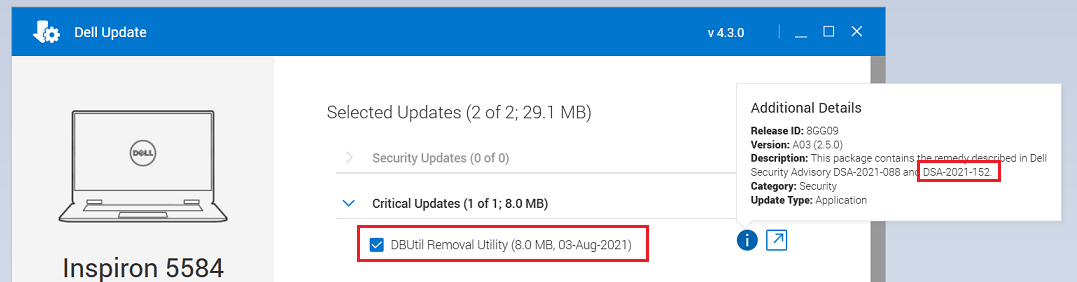
A collection of five flaws, collectively tracked as CVE-2021-21551, have been discovered in DBUtil, a driver from that Dell machines install and load during the BIOS update process and is unloaded at the next reboot.
and from the horses mouth
and keep an eye on your dell updates..