We’re in for a hum-dinger of a Patch Tuesday today, with knowledgeable folks anticipating a big, scary new Windows exploit and a ‘Softie Captain Ameri
[See the full post at: January 2020 Patch Tuesday running commentary, from the skeptic’s corner]

|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
-
January 2020 Patch Tuesday running commentary, from the skeptic’s corner
Home » Forums » Newsletter and Homepage topics » January 2020 Patch Tuesday running commentary, from the skeptic’s corner
- This topic has 167 replies, 50 voices, and was last updated 5 years, 1 month ago.
AuthorTopicViewing 64 reply threadsAuthorReplies-
GoneToPlaid
AskWoody Lounger -
jabeattyauditor
AskWoody Lounger
-
le_clandestin
AskWoody Plus-
woody
Manager
anonymous
GuestJanuary 14, 2020 at 9:16 am #2084658From some of the articles running on Forbes there appears to be some scare tactics at play even regarding 7 and some wav sound file crypto reporting as well as the fact that Windows 7 is getting one last round of updates for Jan 14(today) before it’s all over.
Now for Windows 7 patches in Feb 2020 that’s when it’s really not getting any new security patches(For Consumers at least). I’m beginning to suspect that MS is embarrassed by missing that 1 Billion devices number goal that’s still to this day at around 900 million for 10. So those scare tactics is why there needs to be DEFCON3 or higher before I’ll even think about it.
That Sky Is Falling theme is definitely in play today at 7’s EOL but that’s still not going to help any 1 Billion devices goal from being met on 10. People are just not limited to only PCs/Laptops for any light computing needs so Phones/Tablets for video/browsing and other light computer needs sees more devices running Android and iOS filling that need.
anonymous
Guest-
warrenrumak
AskWoody Lounger -
abbodi86
AskWoody_MVP
-
Mr. Natural
AskWoody Lounger-
Mr. Natural
AskWoody Lounger
JCpharm
AskWoody PlusJanuary 14, 2020 at 10:52 am #2084710-
PKCano
Manager -
Mr. Natural
AskWoody Lounger
-
b
AskWoody_MVPJanuary 14, 2020 at 1:39 pm #2084831M$ should have an incentive i.e. (big fine) to make sure exploits of this level are not passed on to contractors and paying customers of their OS.
And Ford should be fined each time they have to recall a dangerous part. But they’re not.
-
DLivesInTexas
AskWoody Plus -
b
AskWoody_MVP -
DLivesInTexas
AskWoody PlusJanuary 16, 2020 at 1:18 pm #2085893Perhaps this apples-to-oranges comparison of Microsoft and Ford would be more appropriate if Ford refused to allow anyone to drive their cars unless they agree to an EULA that absolves Ford of any damage caused by the use of their product.
1 user thanked author for this post.
-
-
LoneWolf
AskWoody LoungerJanuary 14, 2020 at 11:29 am #2084725Until patch release and until analysis, I treat the prophecies of doom with exactly what they’re due.
We are SysAdmins.
We walk in the wiring closets no others will enter.
We stand on the bridge, and no malware may pass.
We engage in support, we do not retreat.
We live for the LAN.
We die for the LAN.4 users thanked author for this post.
techweenie
AskWoody LoungerJanuary 14, 2020 at 11:39 am #2084732After reading the article, I got the “boy who cried wolf” impression. Woody, it seems like you’re starting to become pacified to all the threats. Just because nothing has materialized with recent threats, doesn’t mean something won’t with each new one. I definitely agree we should wait to see if any bugs are introduced, but don’t start making us believe there’s no urgency until proven that there really is no urgency.
1 user thanked author for this post.
-
woody
ManagerJanuary 14, 2020 at 11:52 am #2084736Well, OK, but I’d put the shoe on the other foot.
Don’t patch until there’s a lot of evidence that you need to patch.
It’s a half-full/half-empty sort of thing. But given MS’s horrible track record with botched patches, I’d say the burden of proof is on MS.
Total of 23 users thanked author for this post. Here are last 20 listed.
-
bbearren
AskWoody MVPJanuary 14, 2020 at 12:49 pm #2084783For me, the evidence that there is a need to patch is the fact that a patch has been made available. I much prefer being the one who says, “Patches installed, no issues, no problems, no BSOD’s, no black screens” than the one who says, “Help! The hackers got my PC!”
As for “given MS’s horrible track record with botched patches, I’d say the burden of proof is on MS.” I’ve had no botched patches, and I have installed every patch that has been offered to my systems from Windows 7 all the way through Windows Version 1909 (OS Build 18.363.592).
In the event that I should one day become botched by a patch, I’m six minutes away from being un-botched.
Always create a fresh drive image before making system changes/Windows updates; you may need to start over!We all have our own reasons for doing the things that we do with our systems; we don't need anyone's approval, and we don't all have to do the same things.We were all once "Average Users". -
Cybertooth
AskWoody PlusJanuary 14, 2020 at 1:13 pm #2084809In the system where it took you six minutes to install the OS image, are you using an SSD, how large is the image, and how often do you make fresh images?
-
bbearren
AskWoody MVPJanuary 14, 2020 at 2:58 pm #2084889The PC is a dual boot with 6 drives, 4 of which are SSD’s (three 250GB, one 1TB), two are 1TB SSHD’s. The OS partition is 100GB, the image file is 38.3GB located on the 1TB SSD.
However, don’t be deceived by the “SSD’s”. I had similar performance (~six minute restoration) when I had four spinners in the box. The partition size is the primary contributor to the speed boost. I’ve been doing this for years and years.
Task Scheduler runs Image For Windows scripts for my OS partition, my Program Files partition and my Users partition (they’re all 100GB partitions) in the wee hours every Sunday morning while I sleep. Task Scheduler also runs a Robocopy batch file twice daily to copy my Documents folder to my OneDrive folder. There it’s synced through the cloud to my NAS OneDrive folder. That way, any data in between drive images is already saved in three separate locations.
I do the same for the B side of my dual boot.
Always create a fresh drive image before making system changes/Windows updates; you may need to start over!We all have our own reasons for doing the things that we do with our systems; we don't need anyone's approval, and we don't all have to do the same things.We were all once "Average Users".-
This reply was modified 5 years, 1 month ago by
bbearren.
-
This reply was modified 5 years, 1 month ago by
bbearren.
2 users thanked author for this post.
-
This reply was modified 5 years, 1 month ago by
-
-
-
Kranium
AskWoody LoungerJanuary 14, 2020 at 2:30 pm #2084866I, too, go by my own anecdotal evidence.
Group B for WIN7 w/ ESU, plus trying out Linux builds in dual boot.
2 users thanked author for this post.
-
woody
Manager
-
-
-
Schnarph
AskWoody LoungerJanuary 15, 2020 at 2:49 pm #2085414At the time of your post, my main PC was on 1809. I made 2 backups then upgraded to 1909, all patches and fully up to date. Everything seems to be running fine, actually a little better in some respects. However, if I let MS update my drivers this system will not function.
Being fully up to date on patches is one thing, but up to date with drivers is another. In my case and likely most cases this is the hardware manufacturers fault, but MS pushing those bad drivers is not acceptable.
Win7and10
AskWoody LoungerJanuary 14, 2020 at 11:56 am #2084739I have not installed the Windows 7 December 2019 Monthly Quality and Security Rollup yet for that reason. Somehow I can’t bring myself to do it knowing that I have to cancel the nag screen. Curious to see what happens on 1/15/20.
My Win 10 is totally patched.
Win 10 Home 22H2
-
This reply was modified 5 years, 1 month ago by
Win7and10.
-
Seff
AskWoody Plus -
PaulK
AskWoody Lounger -
Charlie
AskWoody PlusJanuary 14, 2020 at 2:43 pm #2084879I’ve got both of the EOSNotify and EOSNotify2 tasks disabled in Task Scheduler. It was not a big deal for me to disable them. EOSNotify2 has its start date shown as Jan. 15, 2020 at 12:00 pm. If by chance I do still see a Nag screen, I’ll go back and delete the tasks altogether, and maybe even move the EOSNotify.exe program in System32 to the Recycle Bin.
Being 20 something in the 70's was far more fun than being 70 something in the insane 20's -
Win7and10
AskWoody LoungerJanuary 14, 2020 at 2:51 pm #2084884Did the same, went right to the task scheduler and disabled the TWO EOS Notify tasks after the installation of the December KB 4530734 ROLLUP. Found them under SETUP in the TASK SCHEDULER and also checked the active tasks and EOS NOTIFY is no longer in the active tasks. Tomorrow evening will sign on to see if the task is really gone. From what I can see it appears so! Let us know and thanks!
Win 10 Home 22H2
-
This reply was modified 5 years, 1 month ago by
Win7and10.
1 user thanked author for this post.
-
This reply was modified 5 years, 1 month ago by
-
jabeattyauditor
AskWoody LoungerJanuary 14, 2020 at 12:12 pm #2084751The January patches are now listed in the Microsoft Update Catalog:
https://www.catalog.update.microsoft.com/Search.aspx?q=2020-01
1 user thanked author for this post.
Seff
AskWoody PlusJanuary 14, 2020 at 12:24 pm #2084758I should really have put a bet on at the local bookmakers, predicting that there would be a doomsday threat on EOL day for Windows 7 – it was totally predictable, whether real or imagined. Yes we have to take such things seriously, but that doesn’t mean we have to panic.
2 users thanked author for this post.
anonymous
GuestJanuary 14, 2020 at 12:24 pm #2084755I am using Windows 7 and just received 4 updates: KB4535102 Security and Quality Rollup, KB4534310 Security Monthly Quality Rollup, KB4503548 .NET Framework 4.8 and KB890830 Malicious Software Removal Tool. I only have beginner computer skills so I will watch this site to see what the verdict is on whether I should install, but am wondering if they will be available for installation after today?
-
PKCano
Manager -
Seff
AskWoody PlusJanuary 14, 2020 at 12:37 pm #2084776Agreed. The important thing to note is that Microsoft aren’t immediately withdrawing existing patches, they just aren’t routinely releasing any new ones – although the likelihood is that they will respond to any real nightmare scenario as they will have patches available in those circumstances for paying business customers and will be under enormous pressure to extend them to everyone given the high residual usage of Windows 7 – as they have done previously with XP patches long after EOL.
-
Cybertooth
AskWoody PlusJanuary 14, 2020 at 12:35 pm #2084771We can confidently state that this month’s updates will still be available for installation after today. For one thing, not everyone (not even those caught in the Windows 10 matrix) installs the month’s patches on the same day that they’re released; taking down patches the day after release would cut off untold millions of users. And for another, patches for End of Support versions of Windows such as XP and Vista are still available today, and if you were to install these old operating systems new this afternoon, the patches for them would still show up in Windows Updates.
At some point, that will no longer be the case–for example, you can’t download updates for Windows 98 any more. But if history is any indication, Windows 7 updates will remain available for years.
PKCano
ManagerJanuary 14, 2020 at 12:26 pm #2084761Group B Security-only Updates and the IE11 Cumulative Update have been updated for January 2020 on AKB2000003.
There is a new SSU for Win7. KB4536952 32-bit ot 64-bit
The documentation for the SSU DOES NOT mention the ESU or say it is just for the ESU.-
Microfix
AskWoody MVP -
PKCano
Manager -
abbodi86
AskWoody_MVPJanuary 14, 2020 at 3:12 pm #2084893When did they ever list the real changes? 🙂
BTW, both Monthly Rollup KB4534310 and Security Only KB4534314 contain updated WUA client, which they didn’t mention in the articles
on another hand, ESU licenses are updated to officially support these editions:
Enterprise,EnterpriseE,EnterpriseN,Professional,ProfessionalE,ProfessionalN,Ultimate,UltimateE,UltimateN1 user thanked author for this post.
-
-
-
Charlie
AskWoody Plus -
AmbularD
AskWoody PlusJanuary 14, 2020 at 2:57 pm #2084888Purely speculation here, but MS did release some unplanned emergency patches for major threats for Windows XP after EOL. Maybe this SSU is intended to prepare for any such emergency patches for Windows 7.
i7-10700k - ASROCK Z590 Pro4 - 1TB 970 EVO Plus M.2 - DDR4 3200 x 32GB - GeForce RTX 3060 Ti FTW - Windows 10 Pro
-
abbodi86
AskWoody_MVP -
Charlie
AskWoody Plus -
PKCano
Manager -
Charlie
AskWoody Plus -
PKCano
Manager -
AmbularD
AskWoody PlusJanuary 14, 2020 at 3:48 pm #2084916I’m aware, I just mean, perhaps the purpose of the SSU is to make certain that the machine will be able to receive and install any future emergency patches which might be issued.
i7-10700k - ASROCK Z590 Pro4 - 1TB 970 EVO Plus M.2 - DDR4 3200 x 32GB - GeForce RTX 3060 Ti FTW - Windows 10 Pro
1 user thanked author for this post.
-
abbodi86
AskWoody_MVP -
Charlie
AskWoody PlusJanuary 14, 2020 at 4:05 pm #2084934From Google:
Secure Hash Algorithms, also known as SHA, are a family of cryptographic functions designed to keep data secured. It works by transforming the data using a hash function: an algorithm that consists of bitwise operations, modular additions, and compression functions.
I must have misunderstood.
Being 20 something in the 70's was far more fun than being 70 something in the insane 20's1 user thanked author for this post.
-
jabeattyauditor
AskWoody LoungerJanuary 14, 2020 at 5:47 pm #2084964You didn’t completely misunderstand.
A recent SSU enabled the application of updates signed only with SHA-2; this update was made necessary by the cracking of SHA-1 and by Microsoft moving to SHA-2-only code signing.
So… to make a short story long, you had to apply the SSU to enable the more-securely-signed updates to make your system more secure.
🙂
1 user thanked author for this post.
-
Charlie
AskWoody PlusJanuary 15, 2020 at 12:13 pm #2085342Thank you, that’s exactly the way I understood it, I don’t understand why we’ve had SSU’s each and every month since Sept. and the headaches they’ve caused people as to what order, whether installed before or after the main updates, etc. Now we have another one for Jan.
Anyway, for the most part, we got through it, it’s not imperative that I understand everything, and as usual I’m very thankful for the information that I get from Woody and the crew here on this site.
🙂
Being 20 something in the 70's was far more fun than being 70 something in the insane 20's
-
-
bbearren
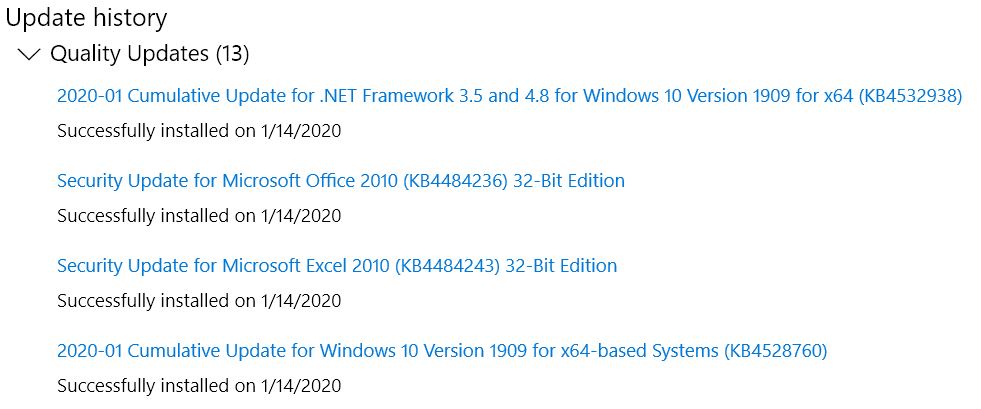
AskWoody MVPJanuary 14, 2020 at 12:33 pm #2084766Seeker/cannon fodder report:
KB4532938 Cumulative Update for .NET Framework 3.5 and 4.8 for Windows 10 Version 1909 for x64
KB4528760 Cumulative Update for Windows 10 Version 1909 for x64-based Systems
KB890830 Windows Malicious Software Removal Tool x64Restart required/accomplished. So far, so good.
Always create a fresh drive image before making system changes/Windows updates; you may need to start over!We all have our own reasons for doing the things that we do with our systems; we don't need anyone's approval, and we don't all have to do the same things.We were all once "Average Users".-
anonymous
Guest -
JCpharm
AskWoody PlusJanuary 14, 2020 at 1:41 pm #2084832KB4532938 Cumulative Update for .NET Framework 3.5 and 4.8 for Windows 10 Version 1909 for x64
KB4528760 Cumulative Update for Windows 10 Version 1909 for x64-based Systems
KB890830 Windows Malicious Software Removal Tool x64Same updates for me as well. Hiding for now.
Win10 Pro
-
This reply was modified 5 years, 1 month ago by
JCpharm.
-
This reply was modified 5 years, 1 month ago by
Alex5723
AskWoody PlusJanuary 14, 2020 at 12:43 pm #2084781We’re in for a hum-dinger of a Patch Tuesday today, with knowledgeable folks anticipating a big, scary new Windows exploit and a ‘Softie Captain Ameri
[See the full post at: January 2020 Patch Tuesday running commentary, from the skeptic’s corner]Martin Brinkmann has the full breakdown :
Lars220
AskWoody PlusJanuary 14, 2020 at 12:51 pm #2084788Reminder for Windows 7 users, the full screen notificaton starts tomorrow, from:
https://support.microsoft.com/en-us/help/4534310
January 14, 2020—KB4534310 (Monthly Rollup)
IMPORTANT Starting on January 15, 2020, a full-screen notification will appear that describes the risk of continuing to use Windows 7 Service Pack 1 after it reaches end of support on January 14, 2020. The notification will remain on the screen until you interact with it. This notification will only appear on the following editions of Windows 7 Service Pack 1:
5 users thanked author for this post.
anonymous
GuestJanuary 14, 2020 at 12:57 pm #2084791Read your guidance to turn off updates this morning in New Zealand where it’s already Wednesday and realize that I may be too late to protect myself [running Win8.1] –
From Windows Update in Control Panel
” ! Download and install updates (550.9 MB total)
3 important updates are available
4 optional updates are available”
I’m given the option to install updates, but it is clear as mud whether they’ve already been downloaded and need to be installed, or clicking to install will commence the download.I did turn off automatic updates. So, am I safe? Or have I been drafted to be a lab rat?
Thanks,
A7-
Microfix
AskWoody MVP -
anonymous
Guest
anonymous
GuestValter
AskWoody LoungerJanuary 14, 2020 at 1:13 pm #2084810“HTTPS connections” are impacted according to NSA advisory: https://media.defense.gov/2020/Jan/14/2002234275/-1/-1/0/CSA-WINDOWS-10-CRYPT-LIB-20190114.PDF
samak
AskWoody PlusJanuary 14, 2020 at 1:29 pm #2084820According to MS, the big, scary vulnerability only affects Windows 10 and Server, not W7 / 8
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-0601
Yay, Windows 10 , most secure Windows ever 😉
Windows 10 Home 22H2, Acer Aspire TC-1660 desktop + LibreOffice, non-techie
7 users thanked author for this post.
Win7and10
AskWoody LoungerJanuary 14, 2020 at 2:12 pm #2084858-
PKCano
Manager -
fernlady
AskWoody LoungerJanuary 14, 2020 at 2:36 pm #2084873I haven’t updated yet cause the updates won’t be available to me till tomorrow morning but I did find the EOSNotify and EOSNotify2 in task scheduler and I disabled both of them. Hope I didn’t kill my computer.
I just went back in to task scheduler to look at them again and they have disappeared from the lineup. oh oh
Windows 11 Pro
Version 23H2
OS build 22631.48901 user thanked author for this post.
-
krzemien
AskWoody Loungeranonymous
GuestJanuary 14, 2020 at 2:30 pm #2084863I’ve updated a number of non-critical/test or still disposable pre-production systems so far. 1809 & 1909 Win 10, LTSC 2019, Server 2016, and Server 2019. I have a few of my techs running it on their office PCs too because I like making them guinea pigs. No issues have come to light yet.
I plan to sit in a holding pattern like this waiting for issues to surface unless word comes out about active exploits.
OscarCP
MemberJanuary 14, 2020 at 2:32 pm #2084869There is nothing in gHacks about this vulnerability, at this time. (3:13 PM, EST) Only two garden variety CVEs, one about a remote desktop attack and one about an exploit that makes IE11 vulnerable to a phishing attack, where the user is bamboozled, as usual, to click something that should not be clicked.
However, the story so far, as I can ascertain it, is thus: at NSA they found this vulnerability and then alerted MS about it. Ms, on receiving the notice from the super-spooks, took quick action, and here we are.
As evidence for this story, there is this document, directly from Spook Central:
https://media.defense.gov/2020/Jan/14/2002234275/-1/-1/0/CSA-WINDOWS-10-CRYPT-LIB-20190114.PDF
Notice that, in the first two paragraphs it says that this CVE affects (only?) Windows 10 and Server 216/219:
“NSA has discovered a critical vulnerability (CVE-2020-0601) affecting Microsoft Windows cryptographic functionality. The certificate validation vulnerability allows an attacker to undermine how Windows verifies cryptographic trust and can enable remote code execution. The vulnerability affects Windows 10 and Windows Server 2016/2019 as well as applications that rely on Windows for trust functionality. Exploitation of the vulnerability allows attackers to defeat trusted network connections and deliver executable ode while appearing as legitimately trusted entities. Examples where validation of trust may be impacted include:
HTTPS connections
Signed files and emails
Signed executable code launched as user-mode processes
The vulnerability places Windows endpoints at risk to a broad range of exploitation vectors.
NSA assesses the vulnerability to be severe and that sophisticated cyber actors will understand the underlying flaw very quickly and, if exploited, would render the previously mentioned platforms as fundamentally vulnerable.”As to scaremongering and the Boy That Cried Wolf (too many times):
The boy cried “Wolf” around his village, a place and a time when wolves were a real problem, because they used to come in big packs and kill and eat its inhabitants. So crying “wolf” was serious business that got the boy a lot of attention. He liked that, and so he kept crying “wolf” with no real wolves in sight. After he did it three times, people decided to ignore him and stop wasting time following the alarms from a proven purveyor of fake alarms.
Until, one day, the wolves really came, they killed and ate everybody in the village, except for the boy and his family. Because Dad had kept, “just in case the boy was not lying, for a change”, his trusty MP-15 well greased, cleaned and loaded, set for “burst” firing (those were the days!) and always close at hand.
Moral of this story: Don’t worry about sudden, alarming news of fierce bugs out there to get people (even if the news come from people close to you, or usually trusted — not the same thing, obviously) but keep the patches handy. Don’t rush to install them, though, but wait — as usual — for indications that they are themselves bug-free, then install them.
And this being my last Patch Tuesday ever (as Win 7 is my last and only Windows for evermore), all I can say is: Wow! What a way to go!
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV3 users thanked author for this post.
-
b
AskWoody_MVP -
OscarCP
MemberJanuary 14, 2020 at 2:58 pm #2084890So now you know.
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV1 user thanked author for this post.
-
CraigS26
AskWoody Plus-
woody
Manager -
bbearren
AskWoody MVPJanuary 14, 2020 at 3:30 pm #2084908I forgot about that one (I don’t use Search) so I just checked. Still have to use Ctrl + V to paste in the search box, but search still works. It’s slow for me because I have indexing disabled, but it does indeed work.
Always create a fresh drive image before making system changes/Windows updates; you may need to start over!We all have our own reasons for doing the things that we do with our systems; we don't need anyone's approval, and we don't all have to do the same things.We were all once "Average Users". -
anonymous
Guest
-
Kranium
AskWoody LoungerJanuary 14, 2020 at 2:34 pm #2084872This vulnerability exists in Windows 7, too. It probably has been there since Windows 2000.
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-0601
Thus far, Win 7 is not on the list.
Group B for WIN7 w/ ESU, plus trying out Linux builds in dual boot.
-
warrenrumak
AskWoody LoungerJanuary 14, 2020 at 3:52 pm #2084922Shoot, you’re right. I was getting my lists crossed with the one security vulnerability actually marked as “critical” this month, which is the RDP vulnerability.
Someone’s going to need to explain to me why the certificate spoofing vulnerability has an “important” rating, not critical.
4 users thanked author for this post.
bbearren
AskWoody MVPJanuary 14, 2020 at 2:40 pm #2084876>>edited for clarity<<
The same updates were pushed to my Dell Latitude E5420. That is to say more specifically, when I logged in and went to All settings > Update & Security the announcement that there are updates available for download was at the top of the page, followed by the list of available downloads, and below that the prominent “Download” button. I had to click the button to initiate the download and update process. No issues with my laptop.
>>end of edit<<
The same updates are being restarted/installed on my NAS as I type this.
All is well. I haven’t updated the B side of my laptop yet, but I’ll get around to that one soon enough. Four out of five installations updated with no issues.
Always create a fresh drive image before making system changes/Windows updates; you may need to start over!We all have our own reasons for doing the things that we do with our systems; we don't need anyone's approval, and we don't all have to do the same things.We were all once "Average Users"._Reassigned Account
AskWoody LoungerJanuary 14, 2020 at 3:57 pm #2084926Windows so popular and no doubt full of old code that dates back to Windows NT. Microsoft will always be chasing these security holes. Not much difference between a Mac OS, or Linux they too have old code just waiting to be found. Except that those operating systems do not have nearly the numbers of potential exposed users as Windows does.
Ken Sims
AskWoody PlusJanuary 14, 2020 at 4:50 pm #2084944Write-up by the SANS Internet Storm Center about Patch Tuesday, especially CVE-2020-0601:
Microsoft Patch Tuesday for January 2020Their summary chart shows that Microsoft only rates CVE-2020-0601 as Important, not Critical.
1 user thanked author for this post.
-
b
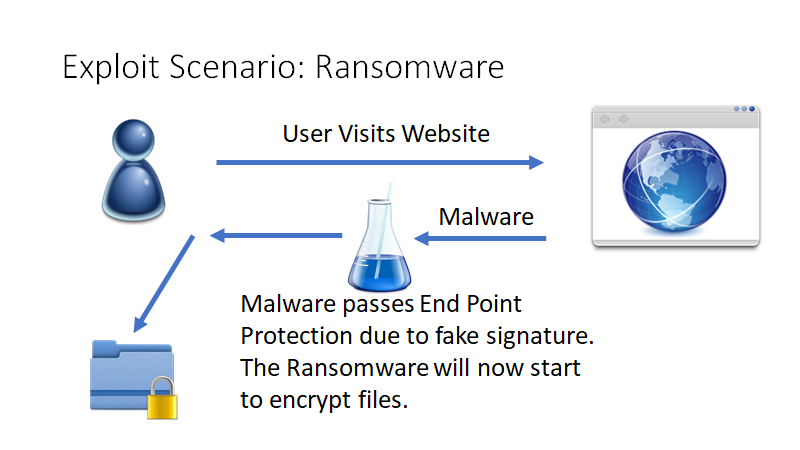
AskWoody_MVPJanuary 14, 2020 at 5:11 pm #2084945Phishing/ransomware appears to be the most likely attack vector for CVE-2020-0601:
How could this flaw be exploited? Let’s look at a quick sample scenario how this flaw could be used to trick a user to install malicious code:
1. The attacker sends an email to the user. The attacker can use this flaw to create a valid signature for the email indicating that it came from a trusted source (for example a vendor).
2. The user clicks on the link, and the attacker will redirect the request to a malicious website via a man in the middle attack. The attacker would be able to create a fake website with a TLS certificate that appears to be valid.
3. Malicious software will be downloaded from the site. The attacker will be able to create a valid code signing signature.
4. The user, or endpoint protection software on the user’s system, will consider the software harmless due to the (fake) signature identifying a trusted vendor as the author.
…
This flaw is likely going to affect a lot of third party software as well, not just software written by Microsoft. Any software calling the “CertGetCertificateChain()” function in Crypto API should be considered vulnerable, which for example includes Google Chrome and many others. -
OscarCP
MemberJanuary 14, 2020 at 8:28 pm #2085018In the (USA) National Security Agency (NSA) document I posted a link to in an earlier comment and also copied what I understood to be the most immediately informative text from the first and second paragraph, among other things it does say;
“Examples where validation of trust may be impacted include:
HTTPS connections
Signed files and emails
Signed executable code launched as user-mode processes
The vulnerability places Windows endpoints at risk to a broad range of exploitation vectors.“
So, I do wonder: what other kinds of attacks could there be, particularly for “consumer” users, such as many of us here, besides phishing and, or ransomware?
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV
-
abbodi86
AskWoody_MVPJanuary 14, 2020 at 5:50 pm #2084965While the blog post don’t mention it clearly, but .NET 4.8 got refreshed packages for all Windows versions, in addition to the Security Rollup
https://devblogs.microsoft.com/dotnet/net-framework-january-security-and-quality-rollup/
Ken Sims
AskWoody PlusJanuary 14, 2020 at 6:04 pm #2084976Here’s an article by Ars Technica where they recommend patching right away:
Patch Windows 10 and Server now because certificate validation is brokenOne paragraph from the article:
Microsoft has rated the update as “important” rather than critical. But in a blog post, Mechele Gruhn, the Principal Security Program Manager for Microsoft Security Response Center, explained that this was because “we have not seen it used in active attacks.”
Personally I’m not going to rush into patching. At the very least I want see credible reports of proof-of-concept exploits before expediting patching.
WildBill
AskWoody PlusJanuary 14, 2020 at 6:15 pm #2084982I know Java is bad news now but Just in Case… I noticed your Oracle link also went to the VMWare page. On http://www.oracle.com, I searched “Any updates for Java?”. The last SE Critical Patch Update Advisory was October 2012. SE 13 (JDK 13) was released October 2019. Guess we’re cool…
Bought a refurbished Windows 10 64-bit, currently updated to 22H2. Have broke the AC adapter cord going to the 8.1 machine, but before that, coaxed it into charging. Need to buy new adapter if wish to continue using it.
Wild Bill Rides Again...-
AJNorth
AskWoody PlusJanuary 15, 2020 at 1:26 pm #2085377Hello WB,
For those who are running the Java SE Runtime Environment (as am I, due to the requirement of one of my banks), then the JRE has been updated to version 8u241 (digitally signed on 2019.12.11):
https://www.oracle.com/technetwork/java/javase/downloads/jre8-downloads-2133155.html
Cheers,
AJN
2 users thanked author for this post.
Win7and10
AskWoody LoungerJanuary 14, 2020 at 6:57 pm #2084991Here’s what I received today:
WINDOWS 7
KB4535102 2020-01 Security Quality Rollup for .NET
KB4534310 2020-01 Security Monthly Quality Rollup
KB4503548 Microsoft NET Framework for Windows 7 for x 64
KB890830 Windows Malicious Software Removal Tool x 64 January 2020HID THEM ALL FOR NOW…..THEN…DRUM ROLL….
Received :
KB4536952 2020-01 Servicing Stack Update for Windows 7 for x 64 based systemsHID THAT AS WELL…..
Waiting for Defcon Safe…..QUESTION: I did not install the December 2109 .NET Security and Quality Rollup, it stated Recommended. Will that be an issue and would you install it before any of the January updates?
Thanks….Wonder Woman Cape in Place…. 🙂
Win 10 Home 22H2
-
PKCano
ManagerJanuary 14, 2020 at 7:14 pm #2084997KB4503548 Microsoft NET Framework 4.8 for Windows 7 for x 64 is the INSTALLER for .NET 4.8. We have not been recommending it for Win7. I would suggest leaving it hidden.
If December 2019 .NET Security and Quality Rollup is CHECKED, I would recommend installing it after you unhide it. If it is UNCHECKED, do not check it and it won’t get installed, But you should rehide it so you get the SSU KB4536952. All the checked updates in the queue can be installed at once, providing they have the DEFCON approval.
3 users thanked author for this post.
-
ryegrass
AskWoody Lounger -
Win7and10
AskWoody LoungerJanuary 14, 2020 at 9:42 pm #2085041Thanks PKano,
Will not install the 4.8 per your recommendation.
(KB4503548 Microsoft NET Framework 4.8 for Windows 7 for x 64 is the INSTALLER for .NET 4.8. We have not been recommending it for Win7. I would suggest leaving it hidden.)In regards to the December 2109 .NET Security and Quality Rollup, it stated Recommended, and it was checked on the initial WU in December. I hid it, and did not install, only the December 2019 Rollup. I have installed the .NET Security and Quality Rollups in the past as they were mostly all recommended.
Since WIN 7 is EOL, I presume I should UNHIDE it and install it before Defcon levels are approved for the January updates, correct?
Thanks again!
Win 10 Home 22H2
-
Paul T
AskWoody MVPJanuary 15, 2020 at 1:24 am #2085118Win7 EOL doesn’t make any difference.
You should have installed the December updates last week, but as we are now in the January patch cycle I would wait to see what is recommended before installing any updates.And you should have an image backup of your machine, as always.
cheers, Paul
-
-
-
Nibbled To Death By Ducks
AskWoody PlusJanuary 15, 2020 at 12:39 am #2085091KB4503548 Microsoft NET Framework 4.8 for Windows 7 for x 64 is the INSTALLER for .NET 4.8. We have not been recommending it for Win7. I would suggest leaving it hidden.
I don’t have 4.8 on my system per advice, will the .Net rollup KB4535102 just go ahead and update all .NET frameworks to 4.7 and not become upset there is no 4.8 on my system?
Win7 Pro SP1 64-bit, Dell Latitude E6330, Intel CORE i5 "Ivy Bridge", 12GB RAM, Group "0Patch", Multiple Air-Gapped backup drives in different locations. Linux Mint Greenhorn
--
"The more kinks you put in the plumbing, the easier it is to stop up the pipes." -Scotty -
PKCano
ManagerJanuary 15, 2020 at 4:18 am #2085156The Rollup is a bundle of independent patches for each separate version of .NET. If you do not have the version of .NET installed, the patch for that version is not applied. The Rollup installation manages patching only the individual version(s) you have installed.
1 user thanked author for this post.
-
Nibbled To Death By Ducks
AskWoody PlusJanuary 16, 2020 at 12:16 am #2085632Thanks, PKCano. I thought that was the way of things, just needed to double-check; this flu has really smacked me hard, and am a little fuzzy around the edges. (Got my shot too.) 🙁
Win7 Pro SP1 64-bit, Dell Latitude E6330, Intel CORE i5 "Ivy Bridge", 12GB RAM, Group "0Patch", Multiple Air-Gapped backup drives in different locations. Linux Mint Greenhorn
--
"The more kinks you put in the plumbing, the easier it is to stop up the pipes." -Scotty
-
-
RetiredGeek
AskWoody PlusJanuary 14, 2020 at 9:35 pm #2085034Hey Y’all,
Here’s what I got today on my Test machine (Seeker)!
-
RetiredGeek
AskWoody PlusJanuary 17, 2020 at 8:10 am #2086214Hey Y’all,
Now 3 days in on my Test machine w/o issue. I’ve also decided to install on my main desktop and am 2 days in with that and also no problemo! HTH 😎
1 user thanked author for this post.
-
RetiredGeek
AskWoody PlusJanuary 19, 2020 at 8:26 pm #2087367Hey Y’all,
I said I’d keep you updated so here it is. Over the last two days I’ve noticed that my machine will no longer wake from sleep. This used to take a light tap on the power button but this now restarts the machine!
So I decided to restore my C: partition from my Macrium Reflect backup on my H: drive (3rd physical drive {SSD} in the machine. Guess what the Reflect rescue media only recognizes the firs 2 drives C: & G:, although when booted into Windows it sees them. The really funny part is it sees them for purposes of backup but not restore and it happens in V6 & V7.
Well back to the topic, I copied the backup file to the G: drive and restored it successfully and the machine once again behaves like it used to. So there is something in the cumulative updates causing the problem.
In the process of trouble shooting this problem I also noticed that options for turning off Fast Start are no longer in the Power Options menus in 1909.
HTH 😎
1 user thanked author for this post.
-
b
AskWoody_MVPJanuary 19, 2020 at 8:46 pm #2087376In the process of trouble shooting this problem I also noticed that options for turning off Fast Start are no longer in the Power Options menus in 1909.
It’s still there in the usual place: Turn On or Off Fast Startup in Windows 10
-
Ken Sims
AskWoody PlusJanuary 14, 2020 at 9:54 pm #2085043An article from Brian Krebs about Patch Tuesday:
Patch Tuesday, January 2020 EditionHe doesn’t make an explicit recommendation about how quickly to apply patches, but he does say (in reference to CVE-2020-0601):
Both Green and White said it likely will be a matter of hours or days before security researchers and/or bad guys work out ways to exploit this bug, given the stakes involved. Indeed, already this evening KrebsOnSecurity has seen indications that people are teasing out such methods, which will likely be posted publicly online soon.
… which is kind of an implied recommendation to patch fairly quickly.
anonymous
Guestanonymous
GuestNibbled To Death By Ducks
AskWoody PlusJanuary 15, 2020 at 12:26 am #2085089Just checked and saw:
2020-01 Security and Quality Rollup for .NET Framework 3.5.1, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2, 4.8 for Windows 7 and Server 2008 R2 for x64 (KB4535102)
2020-01 Security Monthly Quality Rollup for Windows 7 for x64-based Systems (KB4534310)
Windows Malicious Software Removal Tool x64 – January 2020 (KB890830)
<hr />
All labelled “Important”, installed none. Sitting in foxhole for now. Relieved to see that only Win 10 is affected by The Big Whambo.
—
(Sidenote: “Sometimes being a version back from the latest OS is a good thing,” we said in Ye Olde Days of Windows….remembering ME, 2000, Vista, 8.0,…DOS was fairly well behaved by the last version… 6.22?…(chuckle)_oh, the fond memories of debugging ’til 4 AM sessions…)
Thanks to all the Lighthouses on here who keep us off the rocks!
—
Win7 Pro SP1 64-bit, Dell Latitude E6330, Intel CORE i5 "Ivy Bridge", 12GB RAM, Group "0Patch", Multiple Air-Gapped backup drives in different locations. Linux Mint Greenhorn
--
"The more kinks you put in the plumbing, the easier it is to stop up the pipes." -ScottyPerthMike
AskWoody PlusJanuary 15, 2020 at 12:57 am #2085101Australian govt is recommending patching all three issues right away, jumping on the hype wagon.
No matter where you go, there you are.
-
doriel
AskWoody LoungerJanuary 15, 2020 at 5:29 am #2085170Czech goverment… Czech government just does not have a clue what is going on. Honestly I checked our National Center of Cyber Security web and the last update is dated to 9.12.2019 🙂 No politics here, but you get my point.
NCKBDell Latitude 3420, Intel Core i7 @ 2.8 GHz, 16GB RAM, W10 22H2 Enterprise
HAL3000, AMD Athlon 200GE @ 3,4 GHz, 8GB RAM, Fedora 29
PRUSA i3 MK3S+
1 user thanked author for this post.
Alex5723
AskWoody PlusJanuary 15, 2020 at 1:23 am #2085116In the event that I should one day become botched by a patch, I’m six minutes away from being un-botched.
How many of the 2 billion Windows users would you guess are ‘six minutes away from being un-botched’ ? I would say ~20%
How many will pay hundred$$ in order to fix their botched Windows PCs after an Windows Update ?
I would say ~80%-
bbearren
AskWoody MVPJanuary 17, 2020 at 9:05 am #2086224How many of the 2 billion Windows users would you guess are ‘six minutes away from being un-botched’ ? I would say ~20% How many will pay hundred$$ in order to fix their botched Windows PCs after an Windows Update ? I would say ~80%
And there’s the rub. Instead of spending time and effort month after month after month trying to dodge updates, setting up a conscientious, regular drive image regimen is a once-and-done procedure. It is no more complex (perhaps less so) than going through various settings in the registry, group policy, etc. to postpone updates.
Any drive imaging software that supports command line input can be setup in Task Scheduler to perform in the background and create drive images regularly.
As for how many will pay hundreds of $$$ in order to fix their botched Windows PCs, in view of the complete absence of any evidence of a pandemic of botched PCs by Windows updates, that percentage is most certainly not ~80%. It’s far more likely to be >0.01%. If the recent CVE-2020-0601 vulnerability made such a splash in the news, one might think that hundreds of millions of PCs suddenly being borked by a Windows update would prompt a few articles.
As I posted here, it’s just not that big an issue for ordinary home users with home networks. The sky is not falling.
Always create a fresh drive image before making system changes/Windows updates; you may need to start over!We all have our own reasons for doing the things that we do with our systems; we don't need anyone's approval, and we don't all have to do the same things.We were all once "Average Users".
Kranium
AskWoody LoungerJanuary 15, 2020 at 4:51 am #2085163So, here we are, the last regular Patch Tuesday for Windows 7.
I’m not gonna lie – this is enjoyably interesting. :]
Group B for WIN7 w/ ESU, plus trying out Linux builds in dual boot.
1 user thanked author for this post.
Barry
AskWoody LoungerJanuary 15, 2020 at 5:12 am #2085167I just noticed a oddity from yesterdays Updates. Yesterday afternoon i downloaded and installed KB4528760 the CU for 1909. It seemed to and showed that it installed just fine and there were no problems.
This morning i hit checked for updates and it offered KB7528760 again. While it was downloading i checked the version # and it was 18363.535 after the CU was installed the second time the version was 18363.592.
I am not sure if the CU actually failed or it was something else. Just thought i would throw this out there.
Barry
Windows 11 v23H2-
PKCano
ManagerJanuary 15, 2020 at 5:32 am #2085171I’m going to venture a guess.
The SSU is not in the list of patches to be installed, but it downloads and installs with the CU. I believe it presents itself in the Update History as the update as well as the CU doing this. If you look in the Installed Updates, you will see it listed as two separate updates with two different KB numbers.Supposedly, the update mechanism installs the SSU first, then the CU. This may be what you are seeing with what appears to be a second install. The Build number doesn’t change until the installation completes after the second reboot.
2 users thanked author for this post.
-
Barry
AskWoody LoungerJanuary 15, 2020 at 10:37 am #2085282I’m going to venture a guess.
The SSU is not in the list of patches to be installed, but it downloads and installs with the CU. I believe it presents itself in the Update History as the update as well as the CU doing this. If you look in the Installed Updates, you will see it listed as two separate updates with two different KB numbers.Supposedly, the update mechanism installs the SSU first, then the CU. This may be what you are seeing with what appears to be a second install. The Build number doesn’t change until the installation completes after the second reboot.
I believe you are correct. I looked at installed updates and it did not show 4528760 on 1/14 only on 1/15
Barry
Windows 11 v23H2
-
anonymous
GuestJanuary 15, 2020 at 6:49 am #2085198. . . not forgetting the EOL of Windows Server 2008.
I’ve been updating a Vista-32 machine with WS2008 x86 updates, since the end of Vista.
15.01.2020. Probably, the last day to trawl through the Security Update Summary, .Net Framework, Sevice Stack etc. Manually loading the updates.
JOB DONE !CraigS26
AskWoody PlusJanuary 15, 2020 at 6:55 am #2085200Another 1909 WU without issues (Jan CU, MSRT, Net Frmwk 4.8, Svc Stack). Images were ready. 18363.592
Are you encountering the File Explorer Search bug?
No, although with an SSD/HDD combo an SSD article led me to Turn OFF Search Indexing, IF THAT matters / Cortana Never Active …. Just did a test search & all remains well.
W10 Pro 22H2 / Hm-Stdnt Ofce '16 C2R / Macrium Pd vX / GP=2 + FtrU=Semi-Annual + Feature Defer = 1 + QU = 0
OscarCP
MemberJanuary 15, 2020 at 7:45 am #2085210According to this, the vulnerability under discussion, that is centered on the crypt32.dll, has been around for quite a while in Windows. At least from the early 2000s, it would seem:
https://docs.microsoft.com/en-us/windows/win32/seccrypto/crypt32-dll-versions
This has some interesting implications that each one of us can figure out by thinking about it.
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AVfernlady
AskWoody LoungerJanuary 15, 2020 at 8:23 am #2085222Updates that came in this morning:
Security and Quality Rollup for .NET Framework 3.5.1, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2, 4.8 for Windows 7 SP1 and Windows Server 2008 R2 SP1 (KB4535102)
2020-01 Security Monthly Quality Rollup for Windows 7 for x64-based Systems (KB4534310)
Windows Malicious Software Removal Tool x64 – January 2020 (KB890830)
All Checked and hiddenServicing stack update for Windows 7 SP1 and Server 2008 R2 SP1 (KB 4536952)
Unchecked and hiddenChecked for updates again
Microsoft .NET Framework 4.8 for Windows 7 forx64 (KB4503548)
Unchecked and hiddenWindows 11 Pro
Version 23H2
OS build 22631.48901 user thanked author for this post.
-
Win7and10
AskWoody LoungerJanuary 15, 2020 at 8:31 am #2085227I received the same, however, all were checked, so I hid them all.
From what has been said, the .NET Framework 4.8 is recommended and not important.
Did you install last month’s .NET Security and Quality Rollup? Mine was recommended.
Installed everything but that one as yet for December 2019 Updates.
All of this month were checked and now HIDDEN.Win 10 Home 22H2
-
fernlady
AskWoody Lounger -
PKCano
ManagerJanuary 15, 2020 at 8:51 am #2085235The .NET Rollups should be installed if they are CHECKED.
Microsoft .NET Framework 4.8 for Windows 7 KB4503548 is the .NET 4.8 Installer.
If you have the earlier version of .NET 4.8 installed, AND KB4503548 is checked, you should install it.
If you don’t already have .NET 4.8 installed, it is not recommended for Win7. You shoud keep it hidden.
-
Win7and10
AskWoody Lounger-
Moonbear
AskWoody Lounger -
Charlie
AskWoody PlusJanuary 16, 2020 at 2:38 pm #2085935So far the EOSNotify disabling appears to be working. I haven’t seen any nag screen or pop up warning yesterday the 15th, or today.
Being 20 something in the 70's was far more fun than being 70 something in the insane 20's
anonymous
GuestKen Sims
AskWoody PlusJanuary 15, 2020 at 3:51 pm #2085446More from the SANS Internet Storm Center:
One quote:
Which operating systems are affected?
Only Windows 10 and Windows Server 2016 and 2019 are affected. Windows 7 is not affected. There was some confusion about this because Windows 7 is no longer officially supported after this patch release. But the January 14th patch Tuesday did cover Windows 7. The affected library, crypt32.dll (CryptoAPI), is present in older versions of Windows, including Windows 7. But not all versions of this library are affected. Out of support versions of Windows 10, like Windows 10 1709, are likely vulnerable, and you should upgrade to Windows 10 1809, the current “long term support” version.
The video referenced in the article can be viewed on YouTube:
SPECIAL WEBCAST: What you need to know about the Crypt32.dll / CryptoAPI Flawgeekdom
AskWoody_MVPJanuary 15, 2020 at 4:21 pm #2085461I’m holding off on the Windows 10 machine as I just got it stabilized. The user profile was corrupt and had to be rebuilt. Let’s give it a few days.
Windows 7 machine needs to be connected for a look-see on updates.
On permanent hiatus {with backup and coffee}
offline▸ Win10Pro 2004.19041.572 x64 i3-3220 RAM8GB HDD Firefox83.0b3 WindowsDefender
offline▸ Acer TravelMate P215-52 RAM8GB Win11Pro 22H2.22621.1265 x64 i5-10210U SSD Firefox106.0 MicrosoftDefender
online▸ Win11Pro 22H2.22621.1992 x64 i5-9400 RAM16GB HDD Firefox116.0b3 MicrosoftDefenderKen Sims
AskWoody PlusJanuary 15, 2020 at 11:20 pm #2085623More from the SANS Internet Storm Center:
CVE-2020-0601 Followup
One quote:
Which operating systems are affected?
Only Windows 10 and Windows Server 2016 and 2019 are affected. Windows 7 is not affected. There was some confusion about this because Windows 7 is no longer officially supported after this patch release. But the January 14th patch Tuesday did cover Windows 7. The affected library, crypt32.dll (CryptoAPI), is present in older versions of Windows, including Windows 7. But not all versions of this library are affected. Out of support versions of Windows 10, like Windows 10 1709, are likely vulnerable, and you should upgrade to Windows 10 1809, the current “long term support” version.
The video referenced in the article can be viewed on YouTube:
SPECIAL WEBCAST: What you need to know about the Crypt32.dll / CryptoAPI FlawSANS has updated CVE-2020-0601 Followup including the statement: UPDATE: An Exploit has been made public!
I’m not going to apply updates yet, but I’m definitely going to continue monitoring information from SANS and others.
Ken Sims
AskWoody PlusJanuary 15, 2020 at 11:29 pm #2085626A new article from Ars Technica:
Critical Windows 10 vulnerability used to Rickroll the NSA and GithubFirst two paragraphs:
Less than a day after Microsoft disclosed one of the most critical Windows vulnerabilities ever, a security researcher has demonstrated how attackers can exploit it to cryptographically impersonate any website or server on the Internet.
Researcher Saleem Rashid on Wednesday tweeted images of the video “Never Gonna Give You Up,” by 1980s heartthrob Rick Astley, playing on Github.com and NSA.gov. The digital sleight of hand is known as Rickrolling and is often used as a humorous and benign way to demonstrate serious security flaws. In this case, Rashid’s exploit causes both the Edge and Chrome browsers to spoof the HTTPS verified websites of Github and the National Security Agency. Brave and other Chrome derivatives, as well as Internet Explorer, are also likely to fall to the same trick. (There’s no indication Firefox is affected.)
-
woody
ManagerJanuary 16, 2020 at 5:07 am #2085699Yawn. Gotta get back to bed…
-
Ken Sims
AskWoody PlusJanuary 16, 2020 at 2:47 pm #2085941The article was mentioned, with a few sentences quoted, in this article on Threatpost:
PoC Exploits Published For Microsoft Crypto BugThreatpost is for cybersecurity professionals, which I am not. But I am a cybersecurity hobbyist so I read a number of sites meant for security professionals.
-
Ken Sims
AskWoody PlusJanuary 16, 2020 at 3:14 pm #2085948Note that while some of the articles that I link to are meant for security professionals (e.g. SANS), some of them are meant for the general public (e.g. Ars Technica) on websites that may or may not be primarily focused on cybersecurity (Ars Technica is not).
1 user thanked author for this post.
-
-
bsfinkel
AskWoody LoungerJanuary 16, 2020 at 1:58 pm #2085915Windows 7 January patches: KB4535102 .NET
KB4534310 Win 7I had not installed them Tuesday (I only installed MRT). This morning I powered down to install a new SSD disk on which I will install Win 10. But Windows Update had these two checked, so they auto-installed prior to the power down. Then I rebooted in safe mode to check to see if the SSD was OK, and Windows did its normal “chkdsk c:” and other things (because it took more than 12 minutes). But in safe mode Windows does not tell me what it is doing, as it displays the driver names that it has loaded before safe mode starts. Then I rebooted into regular mode. I checked the EventVwr, and it showed that the two patches had been installed, and a reboot was required. Then I saw that the two patches had failed with code 80070643. Widows update now shows me only KB4536952 2020-01 Servicing Stack Update Win 7. I have no idea what that 80070643 error code means. I looked at one thread (via Google), and it was obvious that all the “those knowledgeable” who were responding had no idea what the error code signified. Would I get that error code if my reboot after the patch installation was not a reboot into full Windows 7? Many years ago I would patch Win 7, then reboot into XP to patch, and then reboot into Win 7; back then the Win 7 patches would not complete installation because I had rebooted into XP.
I know that I will not see the two failed patches again (if indeed they did not install) until I install the SSU update. Is the SSU update safe, or is it too soon to know if the SSU patch is OK to install?
1 user thanked author for this post.
Win7and10
AskWoody LoungerJanuary 16, 2020 at 2:09 pm #2085920Here is what I received for Windows 7 2020-01 on 1/14/2020
Security and Quality Rollup for .NET Framework 3.5.1, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2, 4.8 for Windows 7 SP1 and Windows Server 2008 R2 SP1 (KB4535102) – are there issues with this Rollup? This is labeled as Recommended and not Important.
2020-01 Security Monthly Quality Rollup for Windows 7 for x64-based Systems (KB4534310)
Windows Malicious Software Removal Tool x64 – January 2020 (KB890830)
All HiddenMicrosoft .NET Framework 4.8 for Windows 7 forx64 (KB4503548)
Hidden and do not plan to install on Windows 7.Windows update automatically checked again and the following appeared:
Servicing stack update for Windows 7 SP1 and Server 2008 R2 SP1 (KB 4536952)
HiddenThis leads me to the question of last month. The SSU appeared AFTER all the updates were HIDDEN, therefore, when the all clear is given, will the updates install first or the SSU?
NOTE: KB 45330905 .NET Security and Quality Rollup for December 2019 was not installed as yet as some have reported issues with the .NET rollup. When I do install, it will be before the other January Patches. Has anyone had issues with the .NET Security Rollups? Also, if I skip this December rollup will I be OK with just the final January Rollup? This is labeled as Recommended and not Important.
Thanks….
Win 10 Home 22H2
-
This reply was modified 5 years, 1 month ago by
Win7and10.
-
PKCano
Manager -
Win7and10
AskWoody LoungerJanuary 16, 2020 at 5:34 pm #2085988PKCano,
Would you still install the KB 45330905 .NET Security and Quality Rollup for December 2019 or just wait and install all the January updates when we are given the all clear since they are cummulative?
All of my .NET Security and Quality Rollups come in RECOMMENDED, which are to me important. 🙂
Win 10 Home 22H2
-
PKCano
Manager -
Win7and10
AskWoody LoungerJanuary 16, 2020 at 9:05 pm #2086069Can’t recall if the .NET Security and Quality Rollup for December 2019 KB4533095 was checked, however, I have installed these Rollups in the past, so I presume it WAS checked and presume it should be installed. Didn’t know if this one had caused a problem with anyone, thanks.
Win 10 Home 22H2
-
-
-
Ken Sims
AskWoody PlusJanuary 16, 2020 at 4:40 pm #2085967New article from the SANS Internet Storm Center:
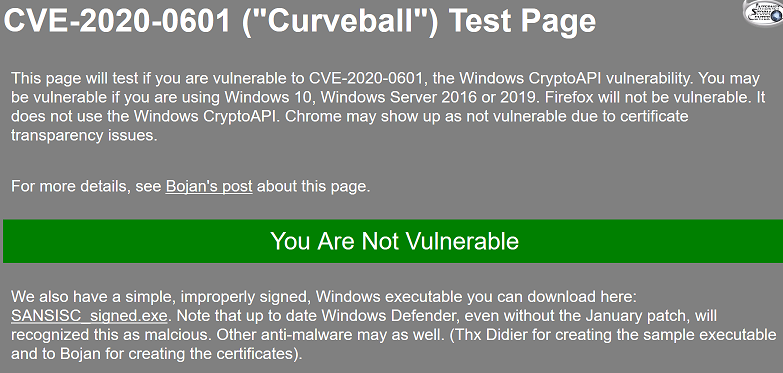
Summing up CVE-2020-0601, or the Let?s Decrypt vulnerabilityOf special interest, you can go to https://curveballtest.com/ to test if your browser is vulnerable to CVE-2020-0601.
On my unpatched system, Firefox (my default browser) is not vulnerable and Microsoft Edge is vulnerable.
3 users thanked author for this post.
anonymous
GuestJanuary 16, 2020 at 5:56 pm #2085989For what it’s worth – This is installed network wide without any apparent issues.
All Win10 PCs, varied mix of 1803 (ok, just one of them), 1809, 1903, 1909, LTSC 2016, LTSC 2019. Office 2016 ISO, Office 2019, Office 365.
Server 2016 & 2019 running domain controllers, file/print servers, SQL, Exchange 2016, SCCM CB, DPM 2019, IIS sites, RD Web, Terminal Server.
anonymous
GuestJanuary 16, 2020 at 7:21 pm #2086035I am running Windows 10 version 1903. Thru my neglect, Version 1909 was downloaded, but I have paused any more downloading or installing until February. Is there a method to download the new patches without installing the already downloaded Windows version 1909?
Thank you for your assistance.
-
PKCano
ManagerJanuary 16, 2020 at 7:26 pm #2086044We need to know if you are running Win10 Home or Win10 Pro.
But normally, when Win10 downloads the install is automatic. To be certain which version of Win10 you have, in the Searchbox, type “winver” (without the quotes) and press Enter. Let us know what version and Build is installed. The Build will look like 1838x.xxx
-
anonymous
GuestJanuary 16, 2020 at 7:55 pm #2086049Edition: Windows 10 Home
Version: 1903
OS build: 18362.535
I just ran the link from the previous post on this forum (https://curveballtest.com/) and it showed that I am vulnerable to CVE-2020-0601. Does this mean I should install all updates now?
Once again, thank you for all your help.
-
PKCano
Manager
-
-
anonymous
GuestJanuary 16, 2020 at 8:01 pm #2086048Windows Defender No Longer Updates Unless Windows Update Service Enabled
I thought that I would post this to the forum as I discovered this today. Normally my first activity on my machine (a Windows 8.1 64-bit system) is to update the Windows Defender virus definitions each morning. This has worked flawlessly for years with the Windows Update service disabled. By design Microsoft designed Windows Defender to be independent of Windows Update allowing defender files to be downloaded regardless of the state of the windows update service. On patch Tuesday(1/14/20) I launched windows update and installed the patch Security Intelligence Update for Windows Defender Antivirus (kb2267602) Version 1.307.2344.0 along with the Windows Malicious Software Removal Tool x64 – January 2020 (KB890830) the 2 most benign patches of the 4 important patches listed for Jan.
A day later I went to run Windows Defender, pressed the update button and no updates were found. Another day went by and the same thing happened. This morning I decided to investigate. I enabled the windows update service then opened Windows Defender and pressed update files. The data files downloaded and installed successfully. It would seem that this update broke the independence of the Windows Defender Service making it now dependent on windows update to run. Is this a nudge on Microsoft’s part to keep the Windows Update service perpetually enabled so they can force anything (including a covert win 10 upgrade) upon us holdouts? Admittedly this issue is minor; one can just enable and disable windows update before launching windows defender, but that is an extra 30 seconds I would rather not take. Any ideas on how to re-establish Windows Defenders’ independence?
DriftyDonN
AskWoody LoungerJanuary 16, 2020 at 8:56 pm #2086066New article from the SANS Internet Storm Center:
Summing up CVE-2020-0601, or the Let?s Decrypt vulnerabilityOf special interest, you can go to https://curveballtest.com/ to test if your browser is vulnerable to CVE-2020-0601.
On my unpatched system, Firefox (my default browser) is not vulnerable and Microsoft Edge is vulnerable.
I am using Firefox 72.0.1
(https://curveballtest.com/ tells me in big letters I am vulnerable. In smaller letters it says Firefox is NOT vulnerable. So…yea or nay, yin or yang? Any ideas?
Thank you.
DriftyDonN
Win10 ver 1903 build 18362.535, paused updates til 17Feb
-
This reply was modified 5 years, 1 month ago by
DriftyDonN. Reason: win version added
-
DrBonzo
AskWoody Plus
Ken Sims
AskWoody PlusJanuary 16, 2020 at 9:57 pm #2086086I’m running essentially the same thing:
Windows 10 Pro, version 1903, build 18362.535, updates paused until Feb 15th, using Firefox (64-bit) version 72.0.1.
I get a green bar across the middle of the screen that says “You Are Not Vulnerable”.
It is only with Microsoft Edge that I get a red square in the middle of the screen that says “You Are Vulnerable”.
The only thing I can think of is if your configurations relating to certificate security have been changed. I believe there is a configuration to use the OS root store instead of the one in Firefox.
Looking in about:config, I see a configuration called security.enterprise_roots.enabled which is set to false. That if is set to true in your configuration, that could be the cause of the problem.
Or there could be some other certificate security setting causing the problem.
anotherwindowsuser
AskWoody Loungerbsfinkel
AskWoody LoungerJanuary 17, 2020 at 10:00 am #2086247Here is an update on my Windows 7 system. This morning I wanted to install the SSU patch, as someone above reported that it was safe to install. Windows Update no longer had the SSU update displayed, but it did have the Win 7 and .NET patches that had failed earlier in the week. It also had MSE pattern 1.307.2452.0, which had been installed at 12:30 yesterday. I have seen frequently that Windows Update wants me to install an MSE pattern update that already been installed. I have no idea if the second patch is an update to the first patch. I assume not, as if a bad MSE pattern patch were to be released, it would be fixed in the next pattern update,
I guess that I will not be able to install the SSU update until I have installed the two January patches.
One other item – MRT. What does this patch do besides replacing \windows\system32\mrt.exe and running it? When I run Windows Update, I get the message “creating a restore point”, and sometimes this message is frequently not changed when the actual patch installs. So I never know exactly when the patch is being installed. The MRT patch took about 1.5 hours from the time I selected it to the time it finished. I did not time this, as I was doing other things while the patch was being installed. I did look at the Task Manager a few times while the “restore point” message was being displayed, and mrt.exe had not yet started. So, I believe that the unneccessary restore point creation took over an hour.
anonymous
GuestWin7and10
AskWoody LoungerJanuary 17, 2020 at 4:48 pm #2086417Just a follow-up question, pardon my caution with Windows 7 x 64 SP1.
Can’t recall if the .NET Security and Quality Rollup for December 2019 KB4533095 was checked, however, I have installed these Rollups in the past, so I presume it WAS checked and presume it should be installed. Right now I have it hidden.
Didn’t know if this one had caused a problem with anyone as I have read that it took a long time to install??
We’re on the final countdown for the patches and have done well with them so far.
If no problems reported, will install over the weekend.
Thanks! 🙂
Win 10 Home 22H2
DriftyDonN
AskWoody LoungerJanuary 17, 2020 at 9:32 pm #2086489I’m running essentially the same thing:
Windows 10 Pro, version 1903, build 18362.535, updates paused until Feb 15th, using Firefox (64-bit) version 72.0.1.
I get a green bar across the middle of the screen that says “You Are Not Vulnerable”.
It is only with Microsoft Edge that I get a red square in the middle of the screen that says “You Are Vulnerable”.
The only thing I can think of is if your configurations relating to certificate security have been changed. I believe there is a configuration to use the OS root store instead of the one in Firefox.
Looking in about:config, I see a configuration called security.enterprise_roots.enabled which is set to false. That if is set to true in your configuration, that could be the cause of the problem.
Or there could be some other certificate security setting causing the problem.
This test page is for edge, IE, Chrome only…..SPECIFICALLY NOT FOR FIREFOX>
BTW< how do I change the value back again in firefox about:config? It seems to be locked.
(redfaced)
Drifty
-
Ken Sims
AskWoody PlusJanuary 17, 2020 at 11:09 pm #2086507In about:config, double-click a line to change the value.
If it’s a true/false value, double-clicking the line will toggle it.
If it’s some other kind of value, double-clicking the line will open up the value so that it can be changed.
If a line is bolded, the value has been changed. If not, it is the default. Changing a value back to the default will remove the bolding.
-
This reply was modified 5 years, 1 month ago by
Ken Sims.
1 user thanked author for this post.
-
This reply was modified 5 years, 1 month ago by
DriftyDonN
AskWoody LoungerJanuary 18, 2020 at 10:01 am #2086649In about:config, double-click a line to change the value.
If it’s a true/false value, double-clicking the line will toggle it.
If it’s some other kind of value, double-clicking the line will open up the value so that it can be changed.
If a line is bolded, the value has been changed. If not, it is the default. Changing a value back to the default will remove the bolding.
-
This reply was modified 5 years, 1 month ago by
Ken Sims.
security.<wbr />enterprise_roots.<wbr />enabled
This line has a padlock at the beginning(before “security…”) and the line is greyed out. The other lines are not. The value is set at “true” now…it was false.
Thanks for helping!
D
BTW, no response to double clicking, no real choice with right click(normal drop down menu)
-
This reply was modified 5 years, 1 month ago by
DriftyDonN.
-
Ken Sims
AskWoody PlusJanuary 18, 2020 at 1:15 pm #2086733I’m sorry, but I’ve never seen that and have no idea what would cause it. The only way that I can think of to fix it is to find the profile directory with the configurations, find the correct file, and manually edit it with a text editor.
1 user thanked author for this post.
DriftyDonN
AskWoody LoungerJanuary 18, 2020 at 7:46 pm #2086874I’m sorry, but I’ve never seen that and have no idea what would cause it. The only way that I can think of to fix it is to find the profile directory with the configurations, find the correct file, and manually edit it with a text editor.
I’m pretty sure Bitdefender has now gotten control over that particular setting. I have a newer acer w/ same win ver, FF, BD and that line is also padlocked on the newer machine. Curious it wasn’t when I checked earlier on the older machine….but BD had updated after I changed the setting. So now it’s “true”…..
Thanks
DriftyDonN
-
Ken Sims
AskWoody Plus
Viewing 64 reply threads -

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Windows 11 Insider Preview build 26120.3380 released to DEV and BETA
by
joep517
3 hours, 20 minutes ago -
Update Firefox to prevent add-ons issues from root certificate expiration
by
Alex5723
10 hours, 28 minutes ago -
Latest Firefox requires Password on start up
by
Gordski
5 hours, 3 minutes ago -
Resolved : AutoCAD 2022 might not open after updating to 24H2
by
Alex5723
23 hours, 16 minutes ago -
Missing api-ms-win-core-libraryloader-11-2-1.dll
by
IreneLinda
55 minutes ago -
How Much Daylight have YOU Saved?
by
Nibbled To Death By Ducks
1 hour, 2 minutes ago -
A brief history of Windows Settings
by
Simon Bisson
15 hours ago -
Thunderbolt is not just for monitors
by
Ben Myers
3 hours, 49 minutes ago -
Password Generators — Your first line of defense
by
Deanna McElveen
1 hour, 17 minutes ago -
AskWoody at the computer museum
by
Will Fastie
52 minutes ago -
Planning for the unexpected
by
Susan Bradley
2 hours, 2 minutes ago -
Which printer type is the better one to buy?
by
Bob99
1 day, 1 hour ago -
Upgrading the web server
by
Susan Bradley
23 hours, 26 minutes ago -
New Windows 11 24H2 Setup – Initial Win Update prevention settings?
by
Tex265
1 day, 18 hours ago -
Creating a Google account
by
DavidofIN
1 day, 17 hours ago -
Undocumented “backdoor” found in Bluetooth chip used by a billion devices
by
Alex5723
1 day, 23 hours ago -
Microsoft Considering AI Models to Replace OpenAI’s in Copilot
by
Alex5723
2 days, 10 hours ago -
AI *emergent misalignment*
by
Alex5723
2 days, 12 hours ago -
Windows 11 Disk Encryption/ Bitlocker/ Recovery Key
by
Tex265
19 hours, 58 minutes ago -
Trouble signing out and restarting
by
Tech Hiker
3 hours, 15 minutes ago -
Windows 7 MSE Manual Updating
by
Microfix
2 days, 20 hours ago -
Problem running LMC 22 flash drive
by
Charlie
1 day, 19 hours ago -
Outlook Email Problem
by
Lil88reb
1 day, 19 hours ago -
“Microsoft 365 Office All-in-One For Dummies, 3rd Edition FREE
by
Alex5723
2 days, 2 hours ago -
Cant use Office 2013 – Getting error message about Office 2013
by
SAAR
2 days, 19 hours ago -
Nearly 1 million Windows devices targeted in advanced “malvertising” spree
by
bbearren
2 days, 19 hours ago -
Windows 11 Insider Preview build 27808 released to Canary
by
joep517
3 days, 20 hours ago -
Windows 11 Insider Preview Build 22635.5025 (23H2) released to BETA
by
joep517
3 days, 20 hours ago -
Sysprep issue
by
Evit
3 days, 20 hours ago -
Android Security Bulletin—March 2025
by
Alex5723
3 days, 22 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.