-
There’s a working Proof of Concept for the “ChainOfFools” CVE-2020-0601 Crypto API bug — but it isn’t as bad as you think
Long story short, Yolan Ronmailler has posted a working Proof of Concept for NSA’s CVE-2020-0601 Crypt32 bug. The code is available on Github.
There’s no question the code works — but it has a prerequisite. In order to get bitten by the security hole, you have to first visit a specific site. That site will load a security certificate that’s instrumental in making the PoC code work.
That severely limits the threat, eh?
Here’s how Ronmailler puts it:
In the end, please keep in mind that such a vulnerability is not at risk of being exploited by script kiddies or ransomware. While it is still a big problem because it could have allowed a Man-in-the-Middle attack against any website, you would need to face an adversary that owns the network on which you operate, which is possible for nation-state adversaries, but less so for a script kiddie. This is why we are releasing this PoC, the exploitability of this vulnerability is not good enough to lead to a sudden ransomware threat (unlike the one we had with Wannacry). This is also probably why the NSA decided not to weaponize their finding, but to rather disclose it: for them it is best to have the USA patched rather than to keep it and take the risk of it being used against the USA, as the attack surface is so vast.
Which ties up many loose ends.
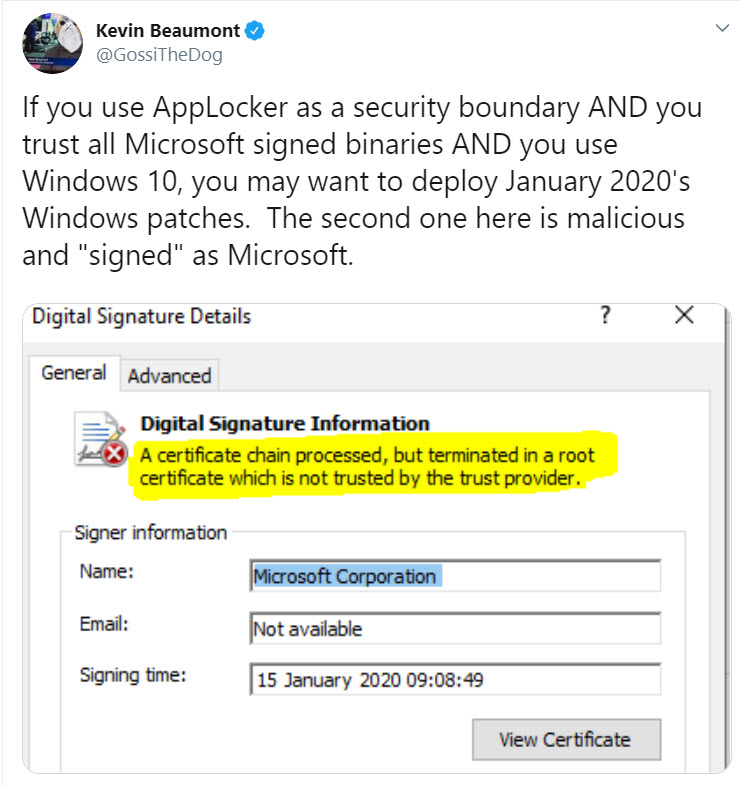
Looks like Kevin Beaumont is right: There’s certainly a security hole here, but it would be very difficult to turn it into a widespread attack. In order for it to work, the victim first has to visit a site that has a clean copy of the certificate that the attacker has subverted, and then visit the site with the subverted certificate. Unless the attacker has full control over your network, the chances of that happening are slim indeed.
(Saleem Rashid showed yesterday that the clean-before-dirty approach is a requirement for the Chrome browser, but Chrome throws a NET::ERR_CERTIFICATE_TRANSPARENCY_REQUIRED. Firefox isn’t vulnerable.)
As I said in the Computerworld article, it’s a long way from a third-degree polynomial to working ransomware.
We’re still at MS-DEFCON 2.
UPDATE: Kevin Beaumont has a revised recommendation: