-
Patch Lady: Tracking some post release issues
Update: Mark Berry has an excellent blog post about how to do a group policy update on the network as well a warning about not setting that value too soon!
 Susan here with early reports from the Tuesday releases (or Wednesday depending on your time zone). Normally we don’t start seeing issues until tomorrow but already we have a few issues bubbling up. This issue is actually expected and you’ll need to look for updates for any third party remote desktop software that may be impacted. The reason for this is a major change in the Credential security support provider. You’ll probably see this in the news talked about as the CredSSP issue. In the security portal the issue is called out here:
Susan here with early reports from the Tuesday releases (or Wednesday depending on your time zone). Normally we don’t start seeing issues until tomorrow but already we have a few issues bubbling up. This issue is actually expected and you’ll need to look for updates for any third party remote desktop software that may be impacted. The reason for this is a major change in the Credential security support provider. You’ll probably see this in the news talked about as the CredSSP issue. In the security portal the issue is called out here:To be fully protected against CVE-2018-0886, users must enable Group Policy settings on their systems and update their Remote Desktop clients. The Group Policy settings are disabled by default to prevent connectivity problems and users must follow the instructions documented HERE to be fully protected.
But I’ll be flat honest, I missed it upon first reviewing the security portal and didn’t realize the impact until later.
The issue impacts remote desktop protocol. If you’ve ever launched the remote desktop connection application on any of your Windows computers, you’ve used CredSSP in your use to remote into computers.
The flaw will be demonstrated next week at a BlackHat conference, but that said you can tell from the description that this will be difficult to exploit in a consumer setting:
Exploiting the flaw requires the attacker to wage a man-in-the-middle attack between the client and server in an RDP or WinRM session. He or she would need WiFi or physical access to the targeted network. A WiFi exploit could be set up using a key reinstallation attack such as KRACK, for example, according to the researchers. Other vectors are Address Resolution Protocol (ARP) poisoning and exploiting vulnerable network devices such as routers, to reach servers inside.
The security fix is actually going to be phased in over the next several months. This month (as per Microsoft) is phase one. All supported workstations and servers will get the update this month, next month in April, Microsoft will start phasing in error messages if you rdp from a patched client into an unpatched server and finally in May the registry setting to better protect servers from unpatched system will kick in.
Bleeping computer even has a video that the researchers have shared discussing the flaw and it’s impact. As is noted, attackers have to have a toe hold into your network before this can be successful, they would have to do a Man in the middle attack to intercept your rdp transmission. In a peer to peer network that would mean they’d have to have malicious code and be in your router. Given the complexity, time spent to craft the packets just so, this one is more in the “they really have to target you” and not in what I call “roadkill” variety of vulnerabilities.
It impacts ALL versions of supported windows, so for anyone in businesses still using Windows XP, and relying on remote desktop protocol, just be aware that this may impact interaction between the platforms as these adjustments roll out over the next several months.
Initially in March, they are rolling out the new protocol. Later in April they will make it so that an error message will occur when you attempt to remote from a patched machine to an unpatched machine, and then later in May (tentative at this time) the default will be to enforce that remoting from a patched machine to an unpatched machine will not work.
If you still need to go between patched and unpatched after May security updates come out, you’ll have to make a manual registry adjustment to lower the security of your system. Hopefully no one has to do that.
Consumer recommendations:
Actions needed: Patch [after we wait a bit just to make sure it’s all clear for any other issues]
I’ve not seen any side effects on Windows machines at this time. I’ve even patched a workstation and left another workstation unpatched to see if there was any issues. I personally saw none. I have seen reports of issues where after installing the update on the Windows based machine, folks couldn’t use the RDP client on a Mac to remote into the Windows machine. So on a consumer machines, if you only RDP between Windows machines you should be fine. For a mixed network with Macs or other non Windows machines that use RDP protocol, check with your vendors for updates.
In May the setting to set the protocol so that clients can’t fall back to using insecure versions of the CredSSP will kick in and thus there is no other action you need to do on standalone peer to peer networks other than to make sure that if you use RDP to remote into computers that all of your remoting still works after you apply the updates.
Mitigated 1
Client applications that use CredSSP will not be able to fall back to insecure versions. Services that use CredSSP will accept unpatched clients. Domain/Network recommendations:
If you are in a domain setting whereby you connect to a file server (not peer to peer), but something called a domain controller, here’s where the guidance differs as Microsoft recommends you roll these settings out now. You actually need to set registry keys or group policy settings to allow for the phase in of this update.
You can make the registry change/group policy in advance before you roll out the updates.

In a Windows 10 Pro – when you go into edit group policy you can see the setting there.
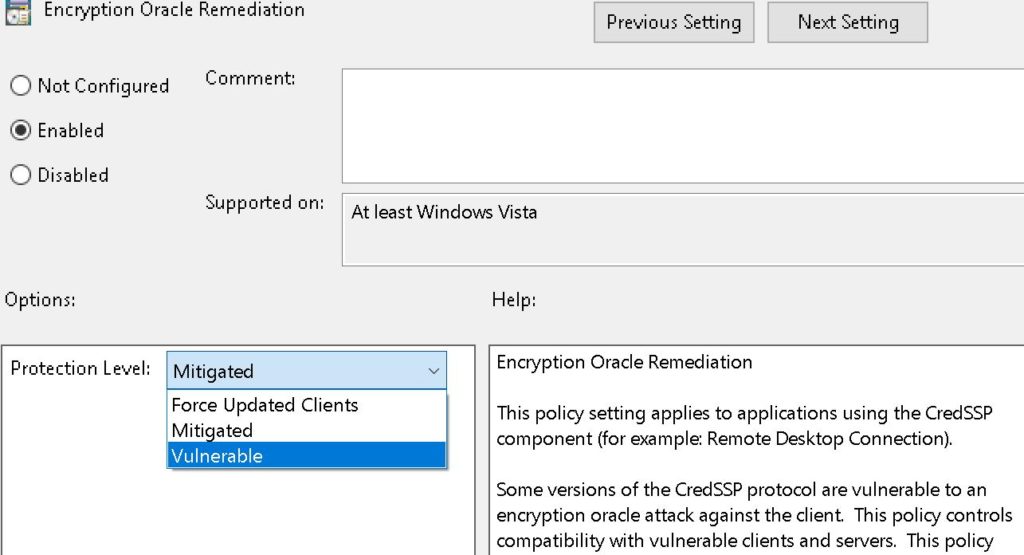
Double click to enable it and then set it to the value of Mitigated. “Mitigated” whereby “Client applications that use CredSSP will not be able to fall back to insecure versions” will be the default value in May.
Test. See if anything breaks. If it does, set it to vulnerable and then go see about getting an update to the RDP client that doesn’t work.
Microsoft has stated that
We recommend that administrators apply the policy and set it to “Force updated clients” or “Mitigated” on client and server computers as soon as possible. These changes will require a reboot of the affected systems.
Hopefully I’ve made this a bit more clearer? I’ll be working on updating the master patch listing for March and will post it Wednesday and will keep an eye out for any other issues along the way.


