-
Mind boggled: The Meltdown/Spectre microcode patches
I just read a tweetstorm from @Karl_F1_Fan to @Crysta that has my head swimming. Here’s what he says:
Hi Crysta,
Your quotes to Microsoft articles are right but things have developed over time. First they asked to set the bitmask for meltdown and Spectre 2 to
FeatureSettingsOverride 1
FeatureSettingsOverrideMask 3for intel clients and servers + the QualityCompat flag
The qualitycompatflag was removed with a patch in March for both clients and servers. Then Microsoft advised the same registry mask for Intel but for AMD it was
FeatureSettingsOverride 64
FeatureSettingsOverrideMask 3(I won’t handle disable flags here for easiness.)
With the appearance of Spectre NG the flags changed again for both AMD and Intel to
FeatureSettingsOverride 8
FeatureSettingsOverrideMask 3which Microsoft is falsely or incompletely advising now in the L1TF article. If a user is setting 1/3 it will DISABLE protection CVE-2018-3639 [speculative store bypass] also it will disable AMD protections.
Meltdown, Spectre 2 / 3, 3a / 4 / L1TF need microcode updates or the seperate updates deployed for Windows 10 in August 2018 + 2018-08 CUs. In addition Microsoft choose that only servers need the registry keys to enable protection. I would advise all customers to apply them.
The current situation is unbearable for average sys admins and there is too much confusion.
IMHO Microsoft should roll out all microcode updates for any OS and enable protection by default without any registry keys it is much easier to understand how to disable it.
The current situation is that only @Dell really cares to bring out BIOS updates for ANY systems back to 2009 whilst other OEMs don’t give a ****.. no matter if we are talking about enterprise or home.
@ASUS there are no microcodes for all systems, as Intel provided. @HP is not updating their site accordingly so the theme sites indicate updates are missing or pending, while being partially available on the product site. We better don’t talk about lack of support from @Acer Lenovo or Medion etc. Without Win10 we would have no protection at all
Based on a variety of 70 client pcs and servers of various OEMS / vendors only 18 received all BIOS microcode updates. 6 had too old Intel / AMD CPUs, more than 21 are only patches because Microsoft rolled out (optional) Microcode Updates. Others unprotected due to old Windows Client / Server version.
How’s that for the very definition of falling into the briar patch?
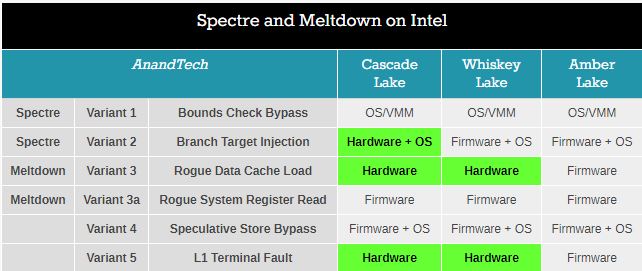
UPDATE: I just followed a link from @teroalhonen to a discussion on Anandtech of the new Intel processors and how they fare with Meltdown and Spectre. Clearly, whoever put together this slide didn’t have a clue.
I sympathize. If Anandtech can’t get it right, what chance do we mortals have? Whotta mess.
ANOTHER UPDATE: ‘Softie Jorge Lopez (@J0RGEL0P3Z) posted a few hours ago:
The 0 / 3 combo enables CVEs 2017-5715 and CVE 2017-5754. The 8 / 3 combo enables Speculative Store Bypass (SSB) protection (CVE 2018-3639) *and* -5715/-5754. L1TF kernel protection requires only for 5754 to be on (so either 0 or 8 works for L1TF). Will see about making clearer
— Jorge Lopez (@cybericua) August 31, 2018